在继续有关组织远程访问VPN访问的系列文章之后,我不得不分享部署高度安全的VPN配置的有趣经验。一位客户(俄罗斯村庄中有发明家)提出了一项艰巨的任务,但是挑战被接受并被创造性地实施。结果是一个有趣的概念,具有以下特征:
- 防止终端设备替换的几个保护因素(与用户紧密绑定);
- 用户的PC与认证数据库中授权PC的指定UDID的符合性评估;
- 使用通过证书通过PC的UDID通过Cisco DUO进行二次身份验证的MFA (您可以拧紧任何兼容的SAML / Radius);
- 多因素身份验证:
- 具有其中之一的现场验证和辅助身份验证的用户证书;
- 登录名(不可变,取自证书)和密码;
- 评估连接主机的状态(姿势)
解决方案的二手组件:
- 思科ASA(VPN网关);
- 思科ISE(身份验证/授权/计费,状态评估,CA);
- Cisco DUO(多因素身份验证)(您可以使用任何兼容SAML / Radius的方法);
- Cisco AnyConnect(工作站和移动操作系统的多用途代理);
让我们从客户需求开始:
- 用户必须使用登录名/密码进行身份验证才能从VPN网关下载AnyConnect客户端,所有必需的AnyConnect模块都应根据用户策略自动安装;
- ( , – ), ( ).
- , , /, , Subject Name (CN) .
- , , , - . ( )
- ( ) ():
- Youtube (5 ).
-.
AnyConnect:
( ASDM) VPN Load-Balancing . , :
VPN :
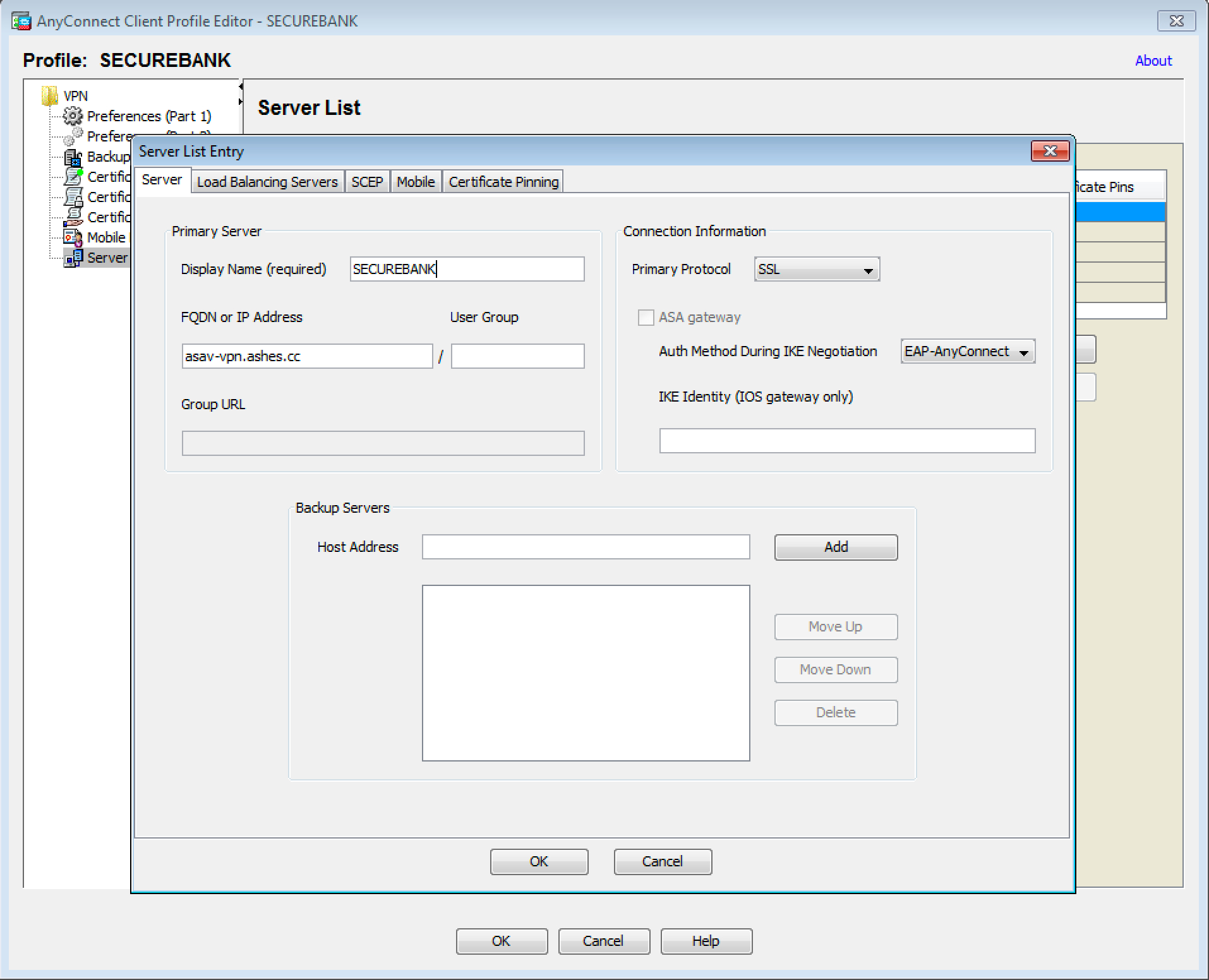
, , , , Initials (I), UDID ( , Cisco AnyConnect ).
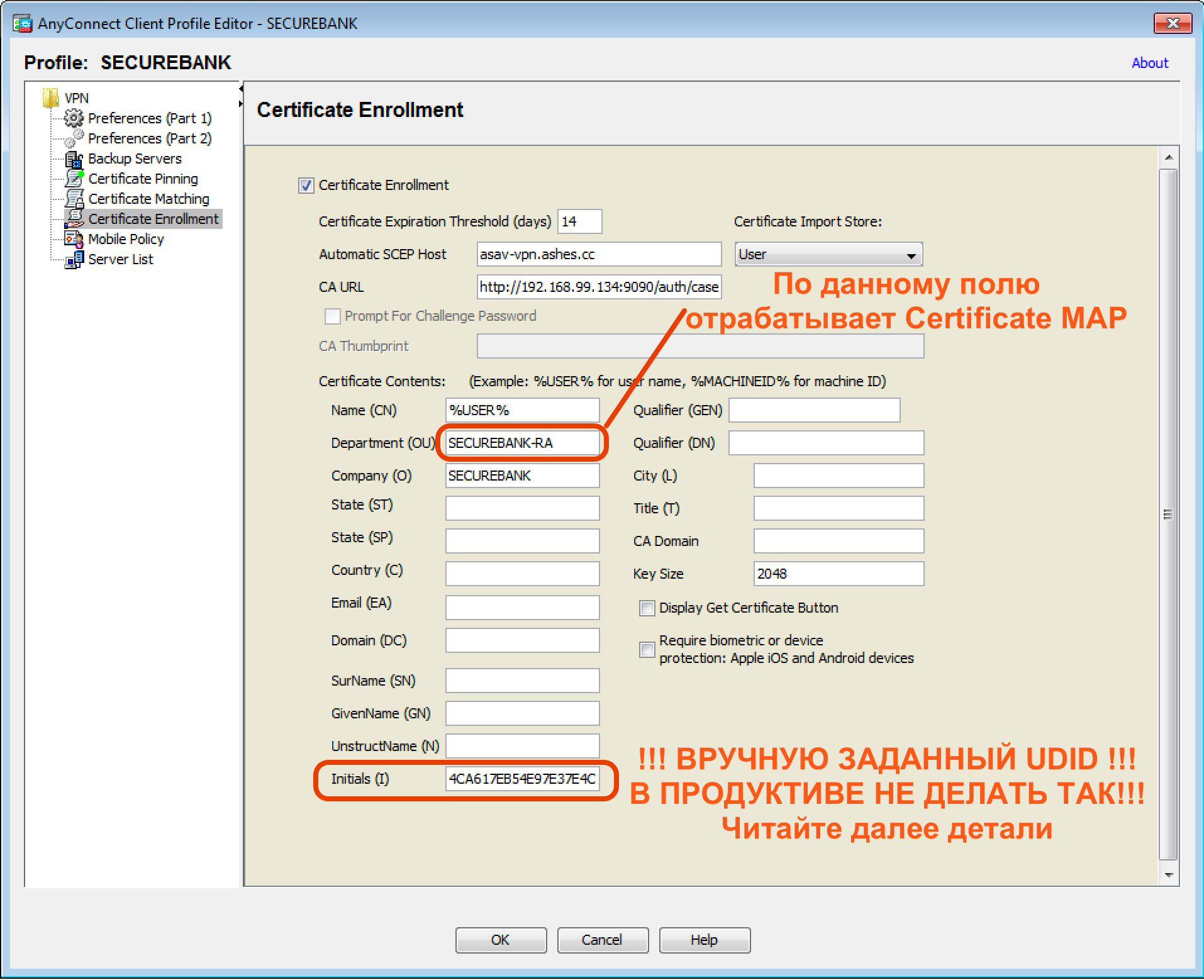
, , UDID Initials AnyConnect. , UDID , UDID . AnyConnect UDID , %USER%.
( ) UDID , - . ( =) ).
. Anyonnect UDID , , – . , UDID AnyConnect:
- Windows — SHA-256 DigitalProductID Machine SID
- OSX — SHA-256 PlatformUUID
- Linux — SHA-256 UUID root .
- Apple iOS — SHA-256 PlatformUUID
- Android –
Windows, UDID UDID, , AD ( Multiple Certificate).
Cisco ASA:
TrustPoint ISE CA , . Key-Chain , VPN Load-Balancing .
crypto ca trustpoint ISE-CA
enrollment terminal
crl configure
Tunnel-Group , . AnyConnect, . SECUREBANK-RA, SECURE-BANK-VPN, AnyConnect.
tunnel-group-map enable rules
!
crypto ca certificate map OU-Map 6
subject-name attr ou eq securebank-ra
!
webvpn
anyconnect profiles SECUREBANK disk0:/securebank.xml
certificate-group-map OU-Map 6 SECURE-BANK-VPN
!
. ISE DUO (Radius Proxy) MFA.
! CISCO ISE
aaa-server ISE protocol radius
authorize-only
interim-accounting-update periodic 24
dynamic-authorization
aaa-server ISE (inside) host 192.168.99.134
key *****
!
! DUO RADIUS PROXY
aaa-server DUO protocol radius
aaa-server DUO (inside) host 192.168.99.136
timeout 60
key *****
authentication-port 1812
accounting-port 1813
no mschapv2-capable
!
:
DefaultWEBVPNGroup AnyConnect VPN SCEP-Proxy ASA, , AC-Download, AnyConnect ( ..). ISE Posture Module.
SECURE-BANK-VPN , Certificate Map, . :
- secondary-authentication-server-group DUO # DUO (Radius Proxy)
- username-from-certificate CN # CN
- secondary-username-from-certificate I # DUO , Initials (I) .
- pre-fill-username client #
- secondary-pre-fill-username client hide use-common-password push # / DUO (sms/push/phone) –
!
access-list posture-redirect extended permit tcp any host 72.163.1.80
access-list posture-redirect extended deny ip any any
!
access-list VPN-Filter extended permit ip any any
!
ip local pool vpn-pool 192.168.100.33-192.168.100.63 mask 255.255.255.224
!
group-policy SECURE-BANK-VPN internal
group-policy SECURE-BANK-VPN attributes
dns-server value 192.168.99.155 192.168.99.130
vpn-filter value VPN-Filter
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelall
default-domain value ashes.cc
address-pools value vpn-pool
webvpn
anyconnect ssl dtls enable
anyconnect mtu 1300
anyconnect keep-installer installed
anyconnect ssl keepalive 20
anyconnect ssl rekey time none
anyconnect ssl rekey method ssl
anyconnect dpd-interval client 30
anyconnect dpd-interval gateway 30
anyconnect ssl compression lzs
anyconnect dtls compression lzs
anyconnect modules value iseposture
anyconnect profiles value SECUREBANK type user
!
group-policy AC-DOWNLOAD internal
group-policy AC-DOWNLOAD attributes
dns-server value 192.168.99.155 192.168.99.130
vpn-filter value VPN-Filter
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelall
default-domain value ashes.cc
address-pools value vpn-pool
scep-forwarding-url value http://ise.ashes.cc:9090/auth/caservice/pkiclient.exe
webvpn
anyconnect ssl dtls enable
anyconnect mtu 1300
anyconnect keep-installer installed
anyconnect ssl keepalive 20
anyconnect ssl rekey time none
anyconnect ssl rekey method ssl
anyconnect dpd-interval client 30
anyconnect dpd-interval gateway 30
anyconnect ssl compression lzs
anyconnect dtls compression lzs
anyconnect modules value iseposture
anyconnect profiles value SECUREBANK type user
!
tunnel-group DefaultWEBVPNGroup general-attributes
address-pool vpn-pool
authentication-server-group ISE
accounting-server-group ISE
default-group-policy AC-DOWNLOAD
scep-enrollment enable
tunnel-group DefaultWEBVPNGroup webvpn-attributes
authentication aaa certificate
!
tunnel-group SECURE-BANK-VPN type remote-access
tunnel-group SECURE-BANK-VPN general-attributes
address-pool vpn-pool
authentication-server-group ISE
secondary-authentication-server-group DUO
accounting-server-group ISE
default-group-policy SECURE-BANK-VPN
username-from-certificate CN
secondary-username-from-certificate I
tunnel-group SECURE-BANK-VPN webvpn-attributes
authentication aaa certificate
pre-fill-username client
secondary-pre-fill-username client hide use-common-password push
group-alias SECURE-BANK-VPN enable
dns-group ASHES-DNS
!
ISE:
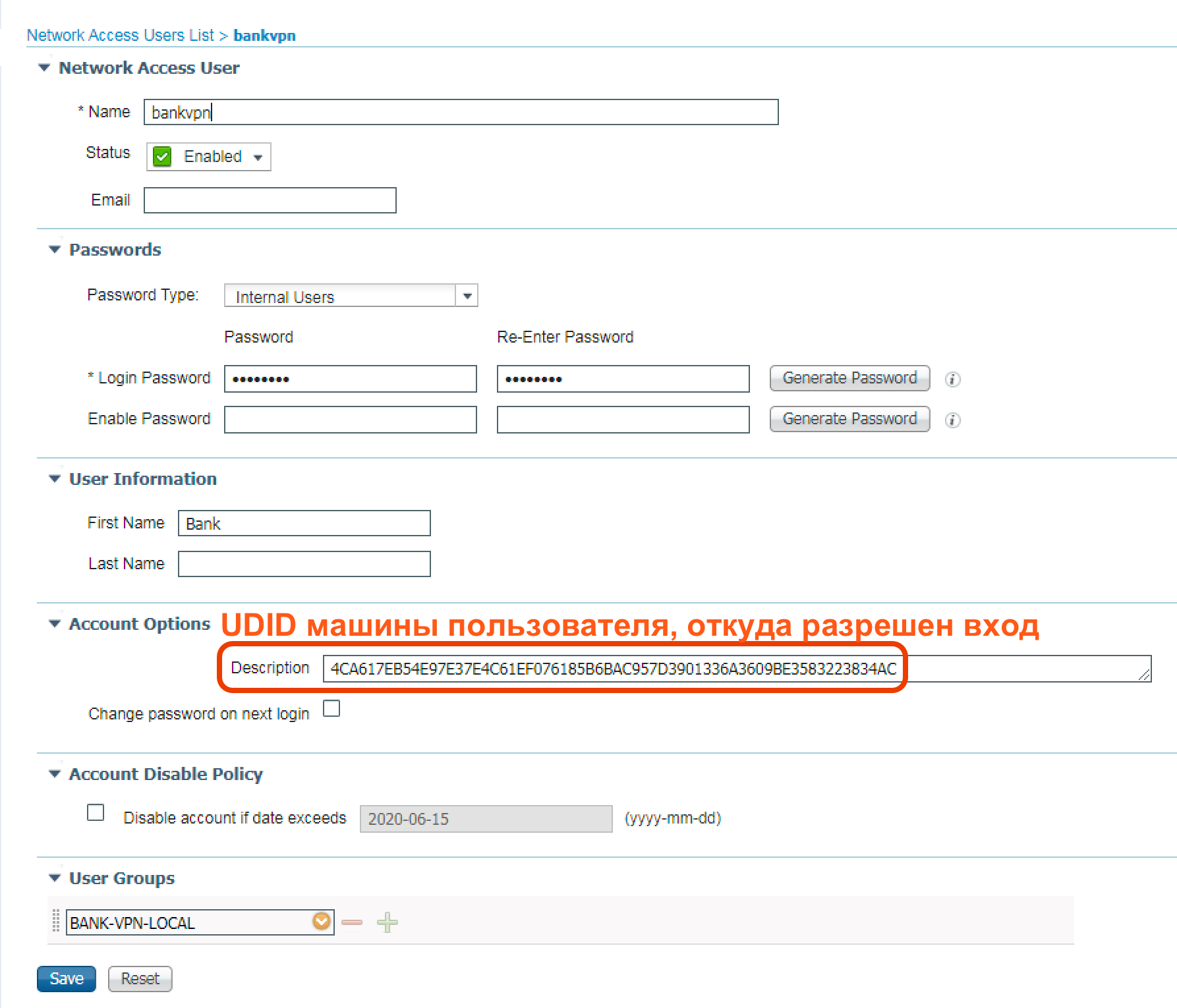
( AD/LDAP/ODBC ..), ISE description UDID VPN. ISE , , .
, :
- 1 — AnyConnect
- 2 — ( )/ + UDID
- 3 — Cisco DUO (MFA) UDID +
- 4 — :
- Compliant;
- UDID ( + ),
- Cisco DUO MFA;
- ;
- ;

UUID_VALIDATED, UDID Description , :
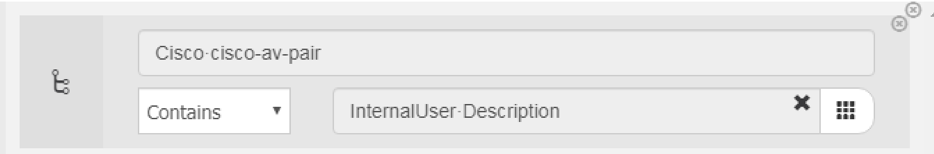
, 1,2,3 :

UDID AnyConnect ISE . , AnyConnect ACIDEX , UDID Cisco-AV-PAIR:
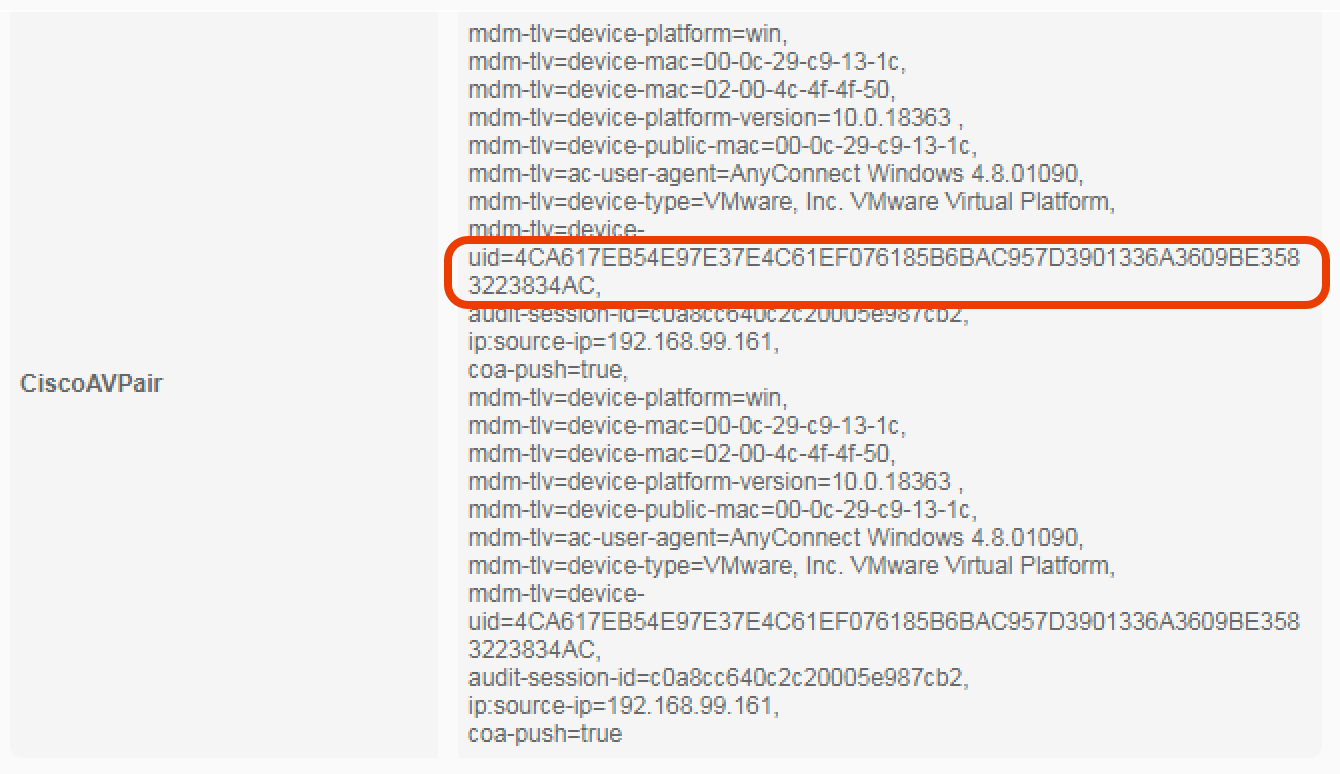
Initials (I), MFA Cisco DUO:
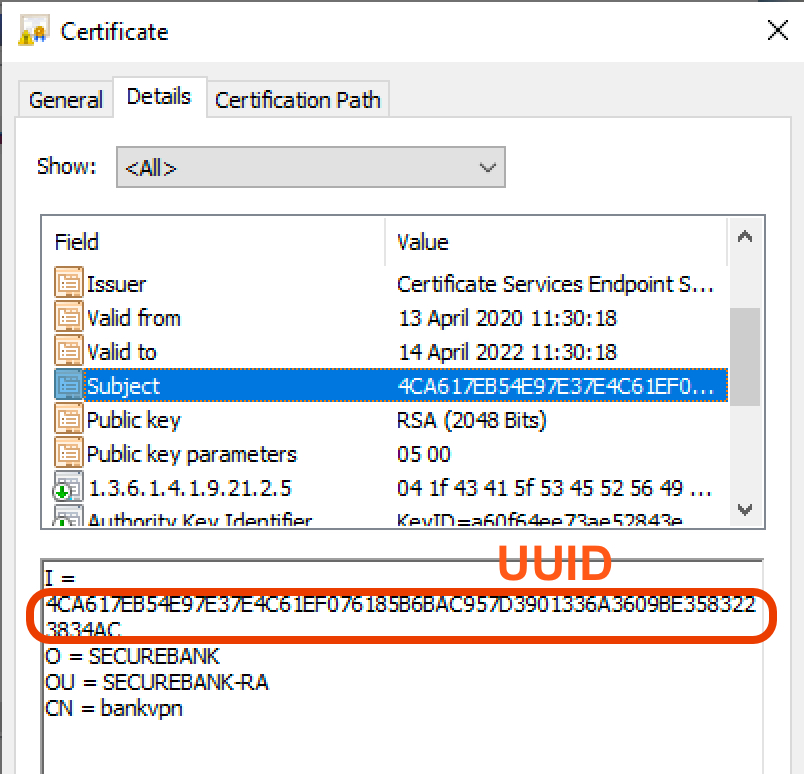
DUO Radius Proxy , UDID :
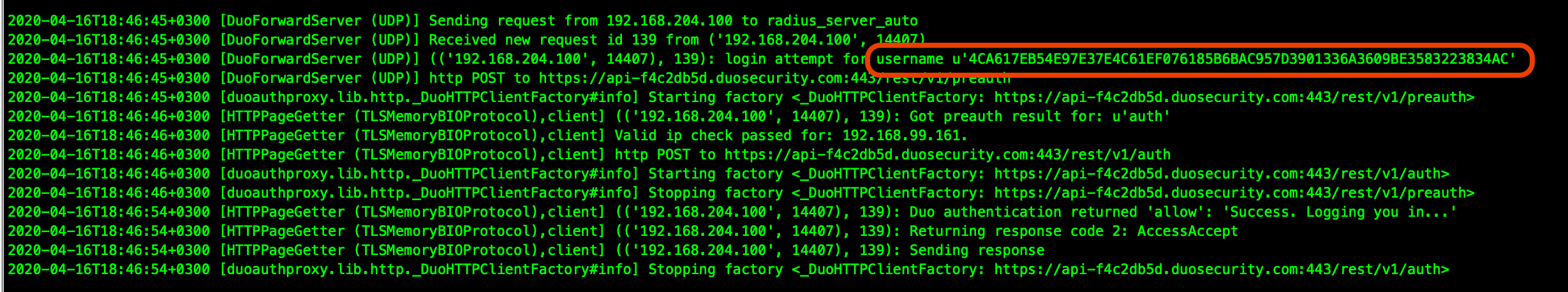
DUO :
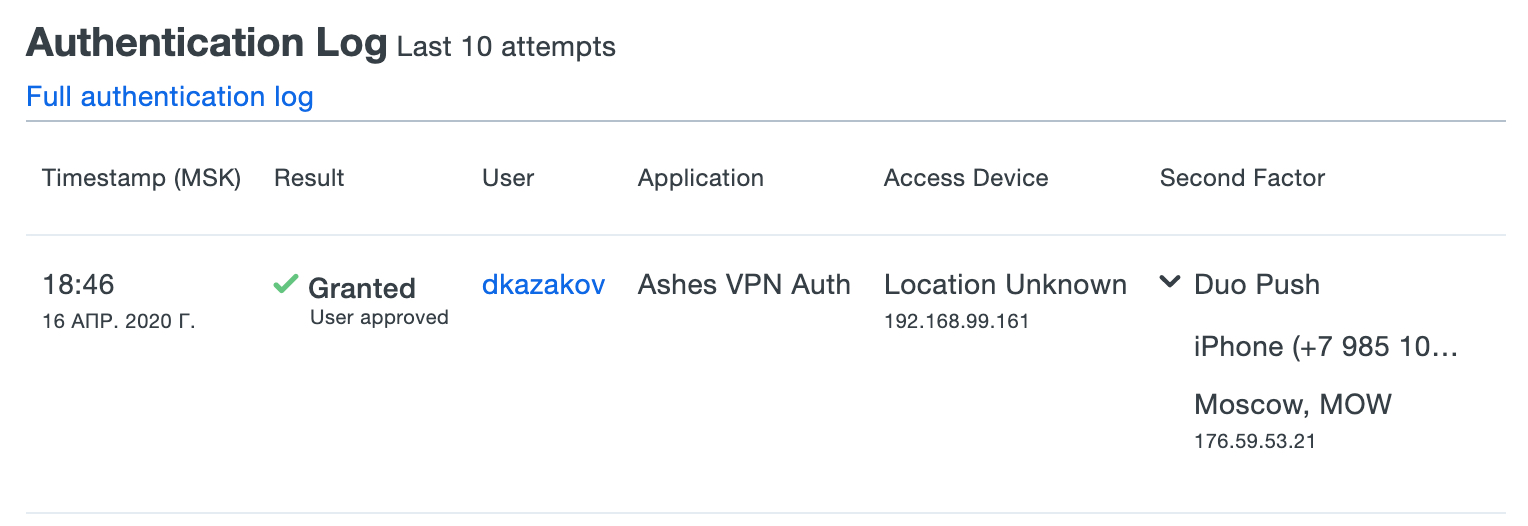
ALIAS, , UDID :
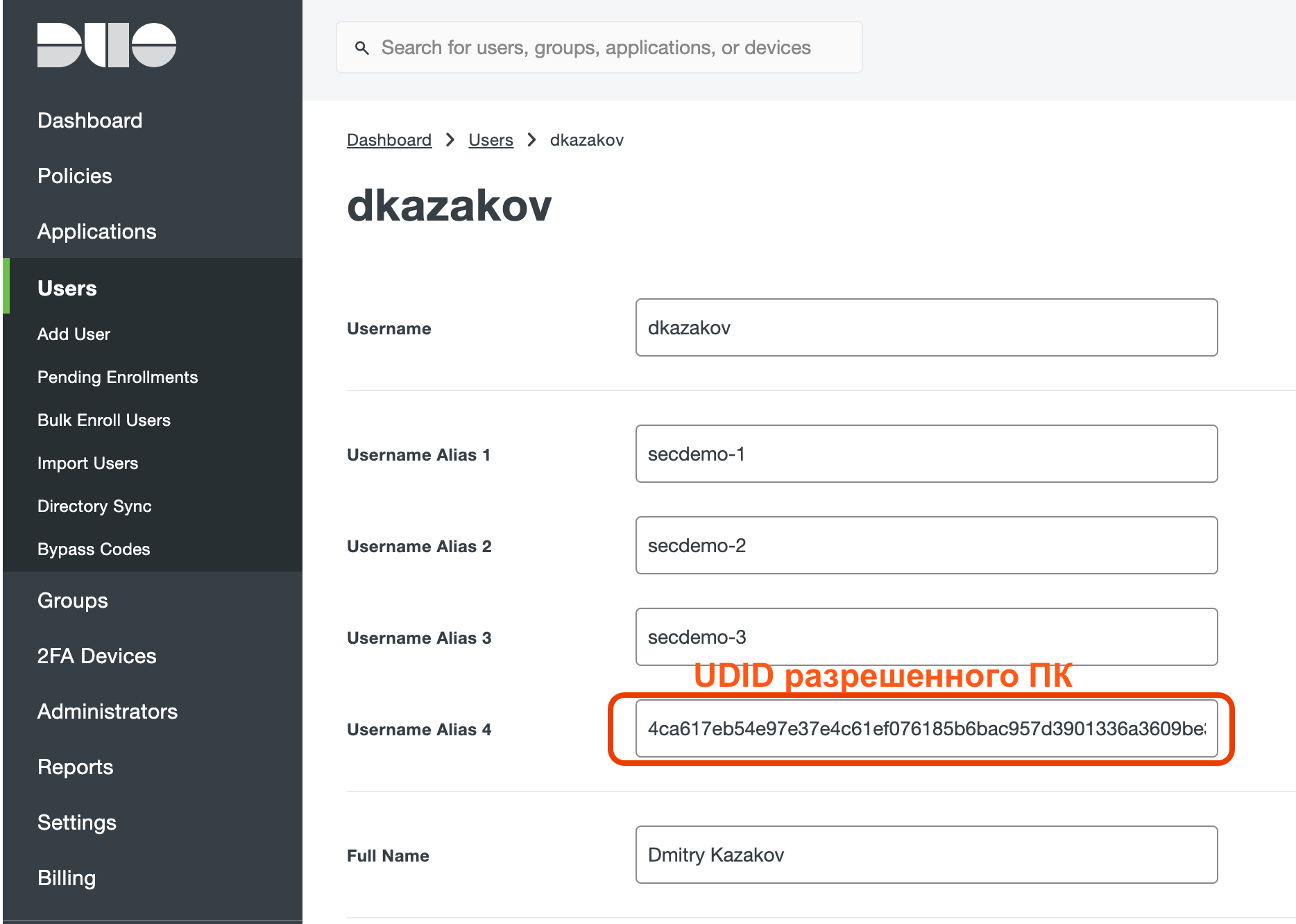
:
Cisco VPN: