本文的主要目的是展示oVirt集群上VyOS虚拟路由器的安装和配置,以组织内部和外部网络之间的L3级别的通信。
此外,本文还将解决与通过两个提供商设置Internet访问功能有关的问题,并提高Internet路由的容错能力。
介绍
基于前两篇文章:
到此时,我们已经创建了一个故障安全群集oVirt,该群集已连接了用于存储虚拟VM磁盘的存储系统。同时,所有网络设备和主机都切换到两个第二级Cisco C2960RX交换机的堆栈上,在其上以中继或静态模式配置相应的端口,并且将VLAN标识符与之关联。
, L2 VLAN'.
VLAN – «» , ( ). VLAN, , - , , , , .
(VLAN') , , OSI, - – . , , , .
– , , , , . , , .
– , .. - , , IP , .
VyOS 1.2.2, ( ), , , KVM.
VyOS – , VPN IPSec , WAN load balancing, VRRP, QoS, ..
VyOS Debian, CLI ( ), Juniper, , , .
GUI ( ) VyOS , Linux/Cisco/Juniper , , « » Debian, , CLI VyOS.
, GUI , Web GUI Vyatta, export, import VyOS — , , , - .
, , – VyOS User Guide, . Habr VyOS, :)
VyOS :
, rolling release VyOS 1.2.2, LTS VyOS 1.1.8.
( VyOS), :
BGP , , , .
, , . , :
IP , IP , , . , .
, :
- – VyOS1 VyOS2.
- CentOS 7 Quagga – Provider-1, Provider-2 Provider-3, .
- CentOS 7, .
, oVirt. , «» oVirt, – KVM, VMware, Hyper-V, .
L3 :
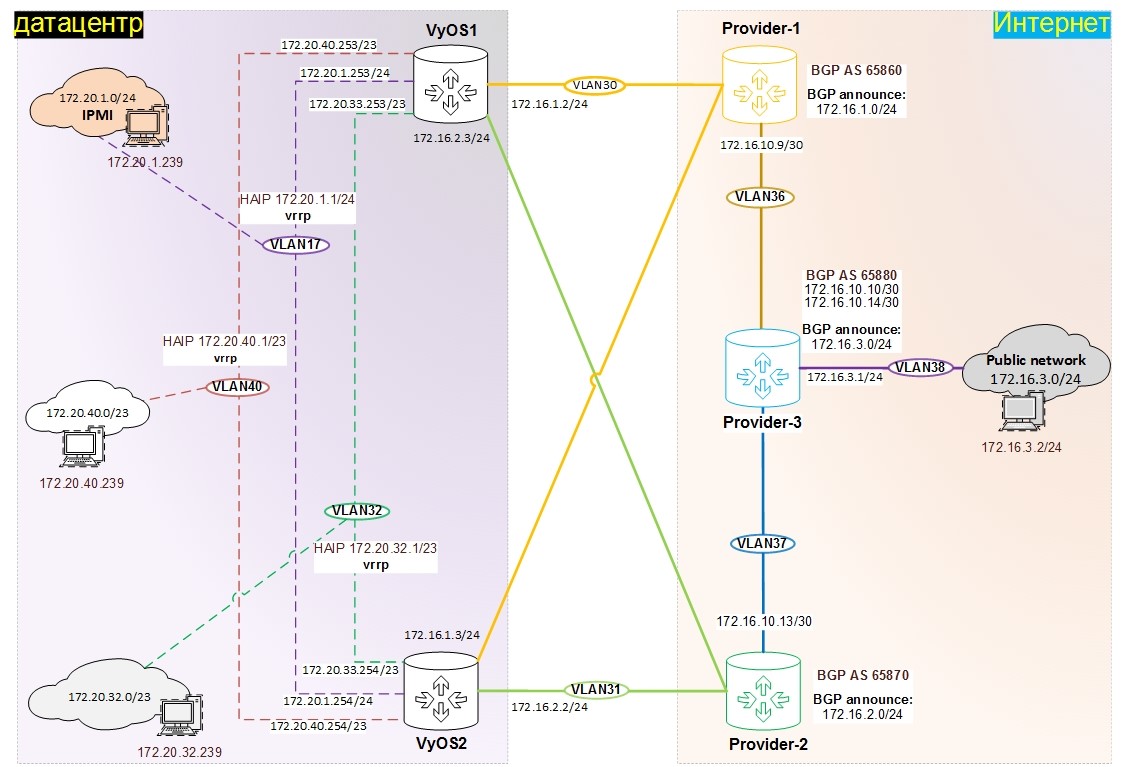
:
- «» 172.16.x.x, ,
- 172.20.x.x
, VLAN:
- VLAN17 – 172.20.1.0/24, (IPMI, management)
- VLAN30 – 172.16.1.0/24, «» , VyOS1, VyOS2 Provider-1
- VLAN31 – 172.16.2.0/24, «» , VyOS1, VyOS2 Provider-2
- VLAN32 – 172.20.32.0/23, – PROD
- VLAN36 – 172.16.10.8/30, «» P2P , Provider-1 Provider-3
- VLAN37 – 172.16.10.12/30, «» P2P , Provider-2 Provider-3
- VLAN38 – 172.16.3.0/24, «» ,
- VLAN40 – 172.20.40.0/23, – TEST
, BGP Provider-1, Provider-2 Provider-3, «» 172.16.1.0/24, 172.16.2.0/24 172.16.3.0/24
, :
.
, 9 oVirt:
- VyOS – 2 ., – rolling release
- Quagga – 3 ., – CentOS 7 x86/64 1810 Minimal ( )
- – 4 ., – CentOS 7 x86/64 1810 Minimal ( )
IP , oVirt.- test-17 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- VLAN17, IP – 172.20.1.239/24, Gateway – 172.20.1.1
- test-IM32 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- VLAN32, IP – 172.20.32.239/23, Gateway – 172.20.32.1
- test-IM40 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- VLAN40, IP – 172.20.40.239/23, Gateway – 172.20.40.1
- test-public – 1 Gb RAM, 1 CPU, 10 Gb HDD,
- VLAN38, IP – 172.16.3.2/24, Gateway – 172.16.3.1
- PROVIDER-1 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- VLAN30, IP – 172.16.1.1/24
- VLAN36, IP – 172.16.10.9/30
- PROVIDER-2 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- VLAN31, IP – 172.16.2.1/24
- VLAN37, IP – 172.16.10.13/30
- PROVIDER-3 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- VLAN36, IP – 172.16.10.10/30
- VLAN37, IP – 172.16.10.14/30
- VLAN38, IP – 172.16.3.1/24
- VyOS1 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- eth0: VLAN17, IP – 172.20.1.253/24
- eth1: VLAN30, IP – 172.16.1.2/24
- eth2: VLAN31, IP – 172.16.2.3/24
- eth3: VLAN32, IP – 172.20.33.253/23
- eth4: VLAN40, IP – 172.20.40.253/23
- VyOS2 – 1 Gb RAM, 1 CPU, 10 Gb HDD
- eth0: VLAN17, IP – 172.20.1.254/24
- eth1: VLAN30, IP – 172.16.1.3/24
- eth2: VLAN31, IP – 172.16.2.2/24
- eth3: VLAN32, IP – 172.20.33.254/23
- eth4: VLAN40, IP – 172.20.40.254/23
VLAN .
, :
1) oVirt, .
, . , :
2) Quagga, .
, , IP .
, .
, .
VyOS.
VyOS, FAQ.
VyOs oVirt:
- ISO rolling release
- oVirt
- ISO VyOS
- .
ISO, :
vyos@vyos:~$ install image
, CD , :
vyos@vyos:~$ reboot
VyOS: vyos / vyos
, ( oVirt), , , .
vyos@VyOS1:~$ sh system image
The system currently has the following image(s) installed:
1: 1.2-rolling-201909060337 (default boot) (running image)
vyos@VyOS1:~$ show version
Version: VyOS 1.2-rolling-201909060337
Built by: autobuild@vyos.net
Built on: Fri 06 Sep 2019 03:37 UTC
Build UUID: 8b5401ba-b2eb-45d9-b267-1e3c5cfba6d7
Build Commit ID: ad4c3805b7b9af
Architecture: x86_64
Boot via: installed image
System type: KVM guest
Hardware vendor: oVirt
Hardware model: oVirt Node
Hardware S/N: 4c4c4544-004a-5010-804e-cac04f4e5232
Hardware UUID: 0f6dcc5e-b60b-4a47-81cc-6885339aa695
Copyright: VyOS maintainers and contributors
( «configure terminal» Cisco), :
vyos@VyOS1:~$ configure
[edit]
vyos@VyOS1#
, .
:
show interfaces ethernet
show interfaces ethernet detail
show interfaces ethernet eth0
VyOS1VLAN17:
set interfaces ethernet eth0 address '172.20.1.253/24'
set interfaces ethernet eth0 description 'VLAN17'
IP :
delete interfaces ethernet eth0 address 172.20.1.253/24
VLAN30:
set interfaces ethernet eth1 address '172.16.1.2/24'
set interfaces ethernet eth1 description 'VLAN30'
VLAN31:
set interfaces ethernet eth2 address '172.16.2.3/24'
set interfaces ethernet eth2 description 'VLAN31'
VLAN32:
set interfaces ethernet eth3 address '172.20.33.253/23'
set interfaces ethernet eth3 description 'VLAN32'
VLAN40:
set interfaces ethernet eth4 address '172.20.40.253/23'
set interfaces ethernet eth4 description 'VLAN40'
VyOS2VLAN17:
set interfaces ethernet eth0 address '172.20.1.254/24'
set interfaces ethernet eth0 description 'VLAN17'
VLAN30:
set interfaces ethernet eth1 address '172.16.1.3/24'
set interfaces ethernet eth1 description 'VLAN30'
VLAN31:
set interfaces ethernet eth2 address '172.16.2.2/24'
set interfaces ethernet eth2 description 'VLAN31'
VLAN32:
set interfaces ethernet eth3 address '172.20.33.254/23'
set interfaces ethernet eth3 description 'VLAN32'
VLAN40:
set interfaces ethernet eth4 address '172.20.40.254/23'
set interfaces ethernet eth4 description 'VLAN40'
SSH
set service ssh port 22
DNS forwarder
set system name-server 1.1.1.1
set system name-server 8.8.8.8
set system host-name VyOS1
set system syslog global facility all level 'notice'
SSH
set system login user vyos authentication public-keys 'vyos' key "very_very_very_long_key"
set system login user vyos authentication public-keys 'vyos' type ssh-rsa
ntp
set system ntp server 0.pool.ntp.org
set system ntp server 1.pool.ntp.org
set system ntp server 2.pool.ntp.org
set system time-zone Europe/Moscow
date
SSH ( DNS )
edit service ssh disable-host-validation
,
commit
save
,
discard
, VyOS SSH, SSH .
, , VyOS, , :
, Zabbix, .
.
– Firewall.
VyOS netfilter.
VyOS :
- , (Per-Interface)
- (Zone Policy).
, .
– , 1 9999. , . , ; , .
:
- Accept – ,
- Drop – ,
- Reject – , «ICMP Port Unreachable».
, , :
- ( in)
FORWARD (netfilter), , VyOS. . - ( out)
FORWARD (netfilter), , . , VyOS, . . - ( local)
INPUT (netfilter), .. , VyOS, , 22 .
:
set firewall name OUTSIDE-IN default-action 'drop'
set firewall name OUTSIDE-IN rule 10 action 'allow'
set firewall name OUTSIDE-IN rule 10 state established 'enable'
set firewall name OUTSIDE-IN rule 10 state related 'enable'
1 – «OUTSIDE-IN» .
2 – (#10), , .
3 – , , .
4 – , , .
, :
set firewall name OUTSIDE-LOCAL default-action 'drop'
.
, :
set interfaces ethernet eth0 firewall in name 'OUTSIDE-IN'
set interfaces ethernet eth1 firewall local name 'OUTSIDE-LOCAL'
1 – «OUTSIDE-IN» eth0, .
2 – «OUTSIDE-LOCAL» eth1, , .
( , ).
, :
- , (established, related),
- ICMP echo-request (ping)
- DHCP
- DNS
- SSH 4 IP (management)
- SNMP (management)
set firewall group network-group NET-VLAN17 network '172.20.1.0/24'
set firewall group network-group NET-VLAN30 network '172.16.1.0/24'
set firewall group network-group NET-VLAN31 network '172.16.2.0/24'
set firewall group network-group NET-VLAN32 network '172.20.32.0/23'
set firewall group network-group NET-VLAN38 network '172.16.3.0/24'
set firewall group network-group NET-VLAN40 network '172.20.40.0/23'
set firewall group network-group NET-MANAGEMENT network '172.20.32.0/23'
set firewall group network-group NET-MANAGEMENT network '172.20.1.0/24'
- , , .
set firewall name LOCAL-VLAN30 default-action 'drop'
set firewall name LOCAL-VLAN30 rule 1010 action 'accept'
set firewall name LOCAL-VLAN30 rule 1010 state established 'enable'
set firewall name LOCAL-VLAN30 rule 1010 state related 'enable'
set firewall name LOCAL-VLAN30 rule 1011 action 'drop'
set firewall name LOCAL-VLAN30 rule 1011 state invalid 'enable'
set firewall name LOCAL-VLAN30 rule 1020 action 'accept'
set firewall name LOCAL-VLAN30 rule 1020 icmp type-name 'echo-request'
set firewall name LOCAL-VLAN30 rule 1020 protocol 'icmp'
set firewall name LOCAL-VLAN30 rule 1020 state new 'enable'
set firewall name LOCAL-VLAN30 rule 1030 action 'drop'
set firewall name LOCAL-VLAN30 rule 1030 destination port '22'
set firewall name LOCAL-VLAN30 rule 1030 protocol 'tcp'
set firewall name LOCAL-VLAN30 rule 1030 recent count '4'
set firewall name LOCAL-VLAN30 rule 1030 recent time '60'
set firewall name LOCAL-VLAN30 rule 1030 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN30 rule 1030 state new 'enable'
set firewall name LOCAL-VLAN30 rule 1040 action 'accept'
set firewall name LOCAL-VLAN30 rule 1040 destination port '22'
set firewall name LOCAL-VLAN30 rule 1040 protocol 'tcp'
set firewall name LOCAL-VLAN30 rule 1040 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN30 rule 1040 state new 'enable'
set firewall name LOCAL-VLAN31 default-action 'drop'
set firewall name LOCAL-VLAN31 rule 1010 action 'accept'
set firewall name LOCAL-VLAN31 rule 1010 state established 'enable'
set firewall name LOCAL-VLAN31 rule 1010 state related 'enable'
set firewall name LOCAL-VLAN31 rule 1011 action 'drop'
set firewall name LOCAL-VLAN31 rule 1011 state invalid 'enable'
set firewall name LOCAL-VLAN31 rule 1020 action 'accept'
set firewall name LOCAL-VLAN31 rule 1020 icmp type-name 'echo-request'
set firewall name LOCAL-VLAN31 rule 1020 protocol 'icmp'
set firewall name LOCAL-VLAN31 rule 1020 state new 'enable'
set firewall name LOCAL-VLAN31 rule 1030 action 'drop'
set firewall name LOCAL-VLAN31 rule 1030 destination port '22'
set firewall name LOCAL-VLAN31 rule 1030 protocol 'tcp'
set firewall name LOCAL-VLAN31 rule 1030 recent count '4'
set firewall name LOCAL-VLAN31 rule 1030 recent time '60'
set firewall name LOCAL-VLAN31 rule 1030 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN31 rule 1030 state new 'enable'
set firewall name LOCAL-VLAN31 rule 1040 action 'accept'
set firewall name LOCAL-VLAN31 rule 1040 destination port '22'
set firewall name LOCAL-VLAN31 rule 1040 protocol 'tcp'
set firewall name LOCAL-VLAN31 rule 1040 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN31 rule 1040 state new 'enable'
set firewall name LOCAL-VLAN17 default-action 'drop'
set firewall name LOCAL-VLAN17 rule 1001 action 'accept'
set firewall name LOCAL-VLAN17 rule 1001 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN17 rule 1010 action 'accept'
set firewall name LOCAL-VLAN17 rule 1010 state established 'enable'
set firewall name LOCAL-VLAN17 rule 1010 state related 'enable'
set firewall name LOCAL-VLAN17 rule 1011 action 'drop'
set firewall name LOCAL-VLAN17 rule 1011 state invalid 'enable'
set firewall name LOCAL-VLAN17 rule 1020 action 'accept'
set firewall name LOCAL-VLAN17 rule 1020 icmp type-name 'echo-request'
set firewall name LOCAL-VLAN17 rule 1020 protocol 'icmp'
set firewall name LOCAL-VLAN17 rule 1020 state new 'enable'
set firewall name LOCAL-VLAN17 rule 1040 action 'accept'
set firewall name LOCAL-VLAN17 rule 1040 destination port '53'
set firewall name LOCAL-VLAN17 rule 1040 protocol 'tcp_udp'
set firewall name LOCAL-VLAN17 rule 1040 state new 'enable'
set firewall name LOCAL-VLAN17 rule 1100 action 'drop'
set firewall name LOCAL-VLAN17 rule 1100 destination port '22'
set firewall name LOCAL-VLAN17 rule 1100 protocol 'tcp'
set firewall name LOCAL-VLAN17 rule 1100 recent count '4'
set firewall name LOCAL-VLAN17 rule 1100 recent time '60'
set firewall name LOCAL-VLAN17 rule 1100 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN17 rule 1100 state new 'enable'
set firewall name LOCAL-VLAN17 rule 1101 action 'accept'
set firewall name LOCAL-VLAN17 rule 1101 destination port '22'
set firewall name LOCAL-VLAN17 rule 1101 protocol 'tcp'
set firewall name LOCAL-VLAN17 rule 1101 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN17 rule 1101 state new 'enable'
set firewall name LOCAL-VLAN17 rule 1110 action 'accept'
set firewall name LOCAL-VLAN17 rule 1110 destination port '161'
set firewall name LOCAL-VLAN17 rule 1110 protocol 'udp'
set firewall name LOCAL-VLAN17 rule 1110 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN17 rule 1110 state new 'enable'
set firewall name LOCAL-VLAN32 default-action 'drop'
set firewall name LOCAL-VLAN32 rule 1010 action 'accept'
set firewall name LOCAL-VLAN32 rule 1010 state established 'enable'
set firewall name LOCAL-VLAN32 rule 1010 state related 'enable'
set firewall name LOCAL-VLAN32 rule 1011 action 'drop'
set firewall name LOCAL-VLAN32 rule 1011 state invalid 'enable'
set firewall name LOCAL-VLAN32 rule 1020 action 'accept'
set firewall name LOCAL-VLAN32 rule 1020 icmp type-name 'echo-request'
set firewall name LOCAL-VLAN32 rule 1020 protocol 'icmp'
set firewall name LOCAL-VLAN32 rule 1020 state new 'enable'
set firewall name LOCAL-VLAN32 rule 1030 action 'accept'
set firewall name LOCAL-VLAN32 rule 1030 destination port '67'
set firewall name LOCAL-VLAN32 rule 1030 protocol 'udp'
set firewall name LOCAL-VLAN32 rule 1030 state new 'enable'
set firewall name LOCAL-VLAN32 rule 1040 action 'accept'
set firewall name LOCAL-VLAN32 rule 1040 destination port '53'
set firewall name LOCAL-VLAN32 rule 1040 protocol 'tcp_udp'
set firewall name LOCAL-VLAN32 rule 1040 state new 'enable'
set firewall name LOCAL-VLAN32 rule 1100 action 'drop'
set firewall name LOCAL-VLAN32 rule 1100 destination port '22'
set firewall name LOCAL-VLAN32 rule 1100 protocol 'tcp'
set firewall name LOCAL-VLAN32 rule 1100 recent count '4'
set firewall name LOCAL-VLAN32 rule 1100 recent time '60'
set firewall name LOCAL-VLAN32 rule 1100 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN32 rule 1100 state new 'enable'
set firewall name LOCAL-VLAN32 rule 1101 action 'accept'
set firewall name LOCAL-VLAN32 rule 1101 destination port '22'
set firewall name LOCAL-VLAN32 rule 1101 protocol 'tcp'
set firewall name LOCAL-VLAN32 rule 1101 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN32 rule 1101 state new 'enable'
set firewall name LOCAL-VLAN32 rule 1110 action 'accept'
set firewall name LOCAL-VLAN32 rule 1110 destination port '161'
set firewall name LOCAL-VLAN32 rule 1110 protocol 'udp'
set firewall name LOCAL-VLAN32 rule 1110 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN32 rule 1110 state new 'enable'
set firewall name LOCAL-VLAN40 default-action 'drop'
set firewall name LOCAL-VLAN40 rule 1001 action 'accept'
set firewall name LOCAL-VLAN40 rule 1001 source group network-group 'NET-MANAGEMENT'
set firewall name LOCAL-VLAN40 rule 1010 action 'accept'
set firewall name LOCAL-VLAN40 rule 1010 state established 'enable'
set firewall name LOCAL-VLAN40 rule 1010 state related 'enable'
set firewall name LOCAL-VLAN40 rule 1011 action 'drop'
set firewall name LOCAL-VLAN40 rule 1011 state invalid 'enable'
set firewall name LOCAL-VLAN40 rule 1020 action 'accept'
set firewall name LOCAL-VLAN40 rule 1020 icmp type-name 'echo-request'
set firewall name LOCAL-VLAN40 rule 1020 protocol 'icmp'
set firewall name LOCAL-VLAN40 rule 1020 state new 'enable'
- VyOS1 VyOS2
set interfaces ethernet eth0 firewall local name 'LOCAL-VLAN17'
set interfaces ethernet eth1 firewall local name 'LOCAL-VLAN30'
set interfaces ethernet eth2 firewall local name 'LOCAL-VLAN31'
set interfaces ethernet eth3 firewall local name 'LOCAL-VLAN32'
set interfaces ethernet eth4 firewall local name 'LOCAL-VLAN40'
VLAN32 VLAN17 – , , , , (, ).
, VLAN30, VLAN31 VLAN40 , .
, , !
, , . (asymmetric routing), -, SPI (stateful packet inspection).
- VLAN32 VLAN17
set firewall name VLAN32-IN default-action 'drop'
set firewall name VLAN32-IN rule 1010 action 'accept'
set firewall name VLAN32-IN rule 1010 state established 'enable'
set firewall name VLAN32-IN rule 1010 state related 'enable'
set firewall name VLAN32-IN rule 1011 action 'drop'
set firewall name VLAN32-IN rule 1011 state invalid 'enable'
set firewall name VLAN32-IN rule 9000 action 'accept'
set firewall name VLAN32-IN rule 9000 source group network-group 'NET-VLAN32'
set firewall name VLAN32-IN rule 9000 state new 'enable'
set firewall name VLAN17-IN default-action 'drop'
set firewall name VLAN17-IN rule 1010 action 'accept'
set firewall name VLAN17-IN rule 1010 state established 'enable'
set firewall name VLAN17-IN rule 1010 state related 'enable'
set firewall name VLAN17-IN rule 1011 action 'drop'
set firewall name VLAN17-IN rule 1011 state invalid 'enable'
set firewall name VLAN17-IN rule 9000 action 'accept'
set firewall name VLAN17-IN rule 9000 source group network-group 'NET-VLAN17'
set firewall name VLAN17-IN rule 9000 state new 'enable'
- ,
set interfaces ethernet eth0 firewall in name 'VLAN17-IN'
set interfaces ethernet eth2 firewall in name 'VLAN32-IN'
- , VLAN32 VLAN17, .. .
set firewall name VLAN32-OUT default-action 'drop'
set firewall name VLAN32-OUT rule 1010 action 'accept'
set firewall name VLAN32-OUT rule 1010 state established 'enable'
set firewall name VLAN32-OUT rule 1010 state related 'enable'
set firewall name VLAN32-OUT rule 1011 action 'drop'
set firewall name VLAN32-OUT rule 1011 state invalid 'enable'
set firewall name VLAN32-OUT rule 1020 action 'accept'
set firewall name VLAN32-OUT rule 1020 icmp type-name 'echo-request'
set firewall name VLAN32-OUT rule 1020 protocol 'icmp'
set firewall name VLAN32-OUT rule 1020 state new 'enable'
set firewall name VLAN32-OUT rule 1100 action 'accept'
set firewall name VLAN32-OUT rule 1100 source group network-group 'NET-VLAN40'
set firewall name VLAN32-OUT rule 1100 state new 'enable'
set firewall name VLAN32-OUT rule 1110 action 'accept'
set firewall name VLAN32-OUT rule 1110 source group network-group 'NET-VLAN17'
set firewall name VLAN32-OUT rule 1110 state new 'enable'
set firewall name VLAN32-OUT rule 1120 action 'accept'
set firewall name VLAN32-OUT rule 1120 source group network-group 'NET-VLAN30'
set firewall name VLAN32-OUT rule 1120 state new 'enable'
set firewall name VLAN32-OUT rule 1130 action 'accept'
set firewall name VLAN32-OUT rule 1130 source group network-group 'NET-VLAN31'
set firewall name VLAN32-OUT rule 1130 state new 'enable'
set firewall name VLAN32-OUT rule 1140 action 'accept'
set firewall name VLAN32-OUT rule 1140 source group network-group 'NET-VLAN38'
set firewall name VLAN32-OUT rule 1140 state new 'enable'
set firewall name VLAN17-OUT default-action 'drop'
set firewall name VLAN17-OUT rule 1010 action 'accept'
set firewall name VLAN17-OUT rule 1010 state established 'enable'
set firewall name VLAN17-OUT rule 1010 state related 'enable'
set firewall name VLAN17-OUT rule 1011 action 'drop'
set firewall name VLAN17-OUT rule 1011 state invalid 'enable'
set firewall name VLAN17-OUT rule 1020 action 'accept'
set firewall name VLAN17-OUT rule 1020 icmp type-name 'echo-request'
set firewall name VLAN17-OUT rule 1020 protocol 'icmp'
set firewall name VLAN17-OUT rule 1020 state new 'enable'
set firewall name VLAN17-OUT rule 1100 action 'accept'
set firewall name VLAN17-OUT rule 1100 source group network-group 'NET-VLAN32'
set firewall name VLAN17-OUT rule 1100 state new 'enable'
- ,
set interfaces ethernet eth0 firewall out name 'VLAN17-OUT'
set interfaces ethernet eth3 firewall out name 'VLAN32-OUT'
, , , commit save.
VyOS- snmp
set firewall config-trap 'enable'
- , ( default drop)
set firewall name VLAN17-IN 'enable-default-log'
set firewall name VLAN17-OUT 'enable-default-log'
set firewall name VLAN32-IN 'enable-default-log'
set firewall name VLAN32-OUT 'enable-default-log'
- , , :
set firewall name VLAN17-LOCAL 'enable-default-log'
commit
exit
show log firewall name VLAN17-LOCAL
configure
delete firewall name VLAN17-LOCAL 'enable-default-log'
commit
- ,
set firewall all-ping 'enable'
set firewall broadcast-ping 'disable'
set firewall config-trap 'disable'
set firewall log-martians 'enable'
set firewall receive-redirects 'disable'
set firewall source-validation 'disable'
set firewall syn-cookies 'enable'
set firewall send-redirects 'enable'
set firewall ipv6-receive-redirects 'disable'
set firewall ipv6-src-route 'disable'
set firewall ip-src-route 'disable'
vrrp
– High availability (VRRP).
VyOS, .
vrrp, , IP — HAIP (Highly Available IP), . , - , . , HAIP () , .
- HAIP, keepalived, , , VyOS Linux, HAIP keepalived ( ). - , .
vrrp, IBM, Vyatta 5600 Brocade, , VyOS Vyatta ( 2012 Brocade).
HAIP, :VLAN17, HA VIP – 172.20.1.1/24
– 172.20.1.253/24
– 172.20.1.254/24
VLAN32, HA VIP – 172.20.32.1/23
– 172.20.33.253/23
– 172.20.33.254/23
VLAN40, HA VIP – 172.20.40.1/23
– 172.20.40.253/23
– 172.20.40.254/23
VyOS1 VyOS2set firewall name LOCAL-VLAN32 rule 1120 action 'accept'
set firewall name LOCAL-VLAN32 rule 1120 protocol 'vrrp'
set firewall name LOCAL-VLAN17 rule 1120 action 'accept'
set firewall name LOCAL-VLAN17 rule 1120 protocol 'vrrp'
set firewall name LOCAL-VLAN40 rule 1030 action 'accept'
set firewall name LOCAL-VLAN40 rule 1030 protocol 'vrrp'
vrrp VyOS1set high-availability vrrp group haip-1 vrid 17
set high-availability vrrp group haip-1 interface eth0
set high-availability vrrp group haip-1 virtual-address 172.20.1.1/24
set high-availability vrrp group haip-1 priority '200'
set high-availability vrrp group haip-1 authentication type 'plaintext-password'
set high-availability vrrp group haip-1 authentication password 'b65495f9'
set high-availability vrrp group haip-1 preempt 2
set high-availability vrrp group haip-1 advertise-interval '1'
set high-availability vrrp group haip-2 vrid 32
set high-availability vrrp group haip-2 interface eth3
set high-availability vrrp group haip-2 virtual-address 172.20.32.1/23
set high-availability vrrp group haip-2 priority '200'
set high-availability vrrp group haip-2 authentication type 'plaintext-password'
set high-availability vrrp group haip-2 authentication password 'b65495f9'
set high-availability vrrp group haip-2 preempt 2
set high-availability vrrp group haip-2 advertise-interval '1'
set high-availability vrrp group haip-3 vrid 40
set high-availability vrrp group haip-3 interface eth4
set high-availability vrrp group haip-3 virtual-address 172.20.40.1/23
set high-availability vrrp group haip-3 priority '200'
set high-availability vrrp group haip-3 authentication type 'plaintext-password'
set high-availability vrrp group haip-3 authentication password 'b65495f9'
set high-availability vrrp group haip-3 preempt 2
set high-availability vrrp group haip-3 advertise-interval '1'
commit
vrrp VyOS2set high-availability vrrp group haip-1 vrid 17
set high-availability vrrp group haip-1 interface eth0
set high-availability vrrp group haip-1 virtual-address 172.20.1.1/24
set high-availability vrrp group haip-1 priority '199'
set high-availability vrrp group haip-1 authentication type 'plaintext-password'
set high-availability vrrp group haip-1 authentication password 'b65495f9'
set high-availability vrrp group haip-1 preempt 2
set high-availability vrrp group haip-1 advertise-interval '1'
set high-availability vrrp group haip-2 vrid 32
set high-availability vrrp group haip-2 interface eth3
set high-availability vrrp group haip-2 virtual-address 172.20.32.1/23
set high-availability vrrp group haip-2 priority '199'
set high-availability vrrp group haip-2 authentication type 'plaintext-password'
set high-availability vrrp group haip-2 authentication password 'b65495f9'
set high-availability vrrp group haip-2 preempt 2
set high-availability vrrp group haip-2 advertise-interval '1'
set high-availability vrrp group haip-3 vrid 40
set high-availability vrrp group haip-3 interface eth4
set high-availability vrrp group haip-3 virtual-address 172.20.40.1/23
set high-availability vrrp group haip-3 priority '199'
set high-availability vrrp group haip-3 authentication type 'plaintext-password'
set high-availability vrrp group haip-3 authentication password 'b65495f9'
set high-availability vrrp group haip-3 preempt 2
set high-availability vrrp group haip-3 advertise-interval '1'
commit
vrrp:
run show vrrp statistics
run show vrrp detail
run show log all
vrrp:vyos@VyOS1# run show vrrp
Name Interface VRID State Last Transition
------ ----------- ------ ------- -----------------
haip-1 eth0 17 MASTER 13m48s
haip-2 eth3 32 MASTER 13m48s
haip-3 eth4 40 MASTER 13m48s
vyos@VyOS2# run show vrrp
Name Interface VRID State Last Transition
------ ----------- ------ ------- -----------------
haip-1 eth0 17 BACKUP 11m26s
haip-2 eth3 32 BACKUP 11m27s
haip-3 eth4 40 BACKUP 5m17s
vrrp- VyOS1
set high-availability vrrp group haip-1 disable
set high-availability vrrp group haip-2 disable
set high-availability vrrp group haip-3 disable
commit
run show vrrp
- test-17, test-IM3 test-IM40 , HAIP:
ping 172.20.32.239
ping 172.20.1.239
ping 172.20.40.239
- , VyOS1 vrrp :
delete high-availability vrrp group haip-1 disable
delete high-availability vrrp group haip-2 disable
delete high-availability vrrp group haip-3 disable
commit
run show vrrp
.
– WAN load balancing.
( ), , , .
- , , , , . , .
, ( ), : VLAN17, VLAN32 VLAN40.
IP «» () , , BGPv4 bgpd, Quagga.
Quagga , CLI, vtysh. CLI , Cisco, .
, «» () VyOS BGP , , . , VyOS BGP , , , CentOS Quagga.
Quagga BGP «» ()- Quagga:
yum install -y quagga
systemctl enable zebra && systemctl start zebra && systemctl status zebra
cp /usr/share/doc/quagga-0.99.22.4/bgpd.conf.sample /etc/quagga/bgpd.conf
systemctl start bgpd && systemctl enable bgpd && systemctl status bgpd
chmod -R 777 /etc/quagga/
vtysh
show running-config
config t
- BGP Provider-1
Provider-1# sh running-config
Building configuration...
Current configuration:
!
hostname Provider-1
log file /var/log/quagga/quagga.log
hostname bgpd
log stdout
!
password zebra
!
interface eth0
ipv6 nd suppress-ra
!
interface eth1
ipv6 nd suppress-ra
!
interface lo
!
router bgp 65860
bgp router-id 172.16.10.9
network 172.16.1.0/24
neighbor 172.16.10.10 remote-as 65880
neighbor 172.16.10.10 description "Provider-3"
neighbor 172.16.10.10 timers 30 90
neighbor 172.16.10.10 soft-reconfiguration inbound
!
ip forwarding
!
line vty
!
end
- BGP Provider-2
Provider-2# sh running-config
Building configuration...
Current configuration:
!
hostname Provider-2
log file /var/log/quagga/quagga.log
hostname bgpd
log stdout
!
password zebra
!
interface eth0
ipv6 nd suppress-ra
!
interface eth1
ipv6 nd suppress-ra
!
interface lo
!
router bgp 65870
bgp router-id 172.16.10.13
network 172.16.2.0/24
neighbor 172.16.10.14 remote-as 65880
neighbor 172.16.10.14 description "Provider-3"
neighbor 172.16.10.14 timers 30 90
neighbor 172.16.10.14 soft-reconfiguration inbound
!
ip forwarding
!
line vty
!
end
- BGP Provider-3
Provider-3# sh running-config
Building configuration...
Current configuration:
!
hostname Provider-3
log file /var/log/quagga/quagga.log
hostname bgpd
log stdout
!
password zebra
!
interface eth0
ipv6 nd suppress-ra
!
interface eth1
ipv6 nd suppress-ra
!
interface eth2
ipv6 nd suppress-ra
!
interface lo
!
router bgp 65880
bgp router-id 172.16.3.1
network 172.16.3.0/24
neighbor 172.16.10.9 remote-as 65860
neighbor 172.16.10.9 description "Provider-1"
neighbor 172.16.10.9 timers 30 90
neighbor 172.16.10.9 soft-reconfiguration inbound
neighbor 172.16.10.13 remote-as 65870
neighbor 172.16.10.13 description "Provider-2"
neighbor 172.16.10.13 timers 30 90
neighbor 172.16.10.13 soft-reconfiguration inbound
!
ip forwarding
!
line vty
!
end
BGP, iptables «» , .
, Provider-3 :
[root@Provider-3 ~]# ip route
169.254.0.0/16 dev eth0 scope link metric 1002
169.254.0.0/16 dev eth1 scope link metric 1003
169.254.0.0/16 dev eth2 scope link metric 1004
172.16.1.0/24 via 172.16.10.9 dev eth0 proto zebra
172.16.2.0/24 via 172.16.10.13 dev eth1 proto zebra
172.16.3.0/24 dev eth2 proto kernel scope link src 172.16.3.1
172.16.10.8/30 dev eth0 proto kernel scope link src 172.16.10.10
172.16.10.12/30 dev eth1 proto kernel scope link src 172.16.10.14
BGP 172.16.1.0/24 172.16.2.0/24, .
, Provider-1 Provider-2, 172.16.3.0/24 .
VyOS1 VyOS2 , VLAN17, 32, 40- Provider-1 Provider-2:
set protocols static route 0.0.0.0/0 next-hop 172.16.1.1
set protocols static route 0.0.0.0/0 next-hop 172.16.2.1
set load-balancing wan interface-health eth1 failure-count 3
set load-balancing wan interface-health eth1 nexthop 172.16.1.1
set load-balancing wan interface-health eth1 test 10 type ping
set load-balancing wan interface-health eth1 test 10 target 172.16.3.1
set load-balancing wan interface-health eth2 failure-count 3
set load-balancing wan interface-health eth2 nexthop 172.16.2.1
set load-balancing wan interface-health eth2 test 10 type ping
set load-balancing wan interface-health eth2 test 10 target 172.16.3.1
- :
set load-balancing wan rule 10 inbound-interface eth+
set load-balancing wan rule 10 destination address 172.20.40.0/23
set load-balancing wan rule 10 exclude
set load-balancing wan rule 20 inbound-interface eth+
set load-balancing wan rule 20 destination address 172.20.32.0/23
set load-balancing wan rule 20 exclude
set load-balancing wan rule 30 inbound-interface eth+
set load-balancing wan rule 30 destination address 172.20.1.0/24
set load-balancing wan rule 30 exclude
- , :
set load-balancing wan rule 1000 inbound-interface eth0
set load-balancing wan rule 1000 interface eth1
set load-balancing wan rule 1000 interface eth2
set load-balancing wan rule 1010 inbound-interface eth3
set load-balancing wan rule 1010 interface eth1
set load-balancing wan rule 1010 interface eth2
set load-balancing wan rule 1020 inbound-interface eth3
set load-balancing wan rule 1020 interface eth1
set load-balancing wan rule 1020 interface eth2
commit
:
eth+ ( ), .
:
show wan-load-balance
show wan-load-balance connection
:
restart wan-load-balance
,
- VLAN30 Provider-1
- bgpd Provider-1
- VLAN31 Provider-2
- bgpd Provider-2
- VyOS1
- VyOS1
- VyOS2
- VyOS2
, , :
- ping traceroute ,
- ping traceroute ,
- ssh , , http.
– , . , – .
NAT, , , ( ).
, - , , , , , c /27.
, , , PBR (policy-based routing) multipath routing. , ( , :)).
VyOS, – , , , .
, - , - IP /24, BGP .
, , . , , , .
, , , , :
, -, - . , .
, … , . , Veeam – oVirt/RHEV KVM, , (Veritas NetBackup, Acronis Cyber Backup, TrilioVault, Bacula Enterprise Edition, SEP, etc.), «» - , «» - OpenSource , .
, , Zabbix – , .
, , – , Cisco 3850, – . , .