我经常读到这样一种观点,即在Internet上保持RDP(远程桌面协议)端口开放是非常不安全的,您不需要这样做。而且您需要通过VPN或仅从某些“白色” IP地址授予对RDP的访问权限。
我为小型公司管理多个Windows Server,其中的任务是为会计师提供对Windows Server的远程访问。这样的现代趋势是在家工作。很快,我意识到折磨VPN会计师是一项不感恩的任务,并且由于人们的IP地址是动态的,因此收集白名单的所有IP都将无法进行。
因此,我采用了最简单的方法-将RDP端口转发出去。现在,要进行访问,会计师需要运行RDP并输入主机名(包括端口),用户名和密码。
在本文中,我将分享我的经验(积极但不太好)和建议。
风险
打开RDP端口有什么风险?
1)未经授权访问敏感数据,
如果某人为RDP选择密码,他将能够获取您想要保密的数据:帐户状态,余额,客户数据等。
2)数据丢失,
例如由于加密病毒的操作而造成的数据丢失。
或攻击者有针对性的行动。
3)丢失工作站
工人需要工作,并且系统受到威胁,您需要重新安装/还原/配置。
4)本地网络的威胁
如果攻击者获得了Windows计算机的访问权限,则他可以从该计算机访问Internet上无法从外部访问的系统。例如锉球,网络打印机等。
我曾经遇到过Windows Server捕获到加密器的情况C:, NAS . NAS Synology, snapshots, NAS 5 , Windows Server .
Windows Servers Winlogbeat, ElasticSearch. Kibana , .
, .
:
a) RDP -.
RDP 3389, 443 — HTTPS. , , . :
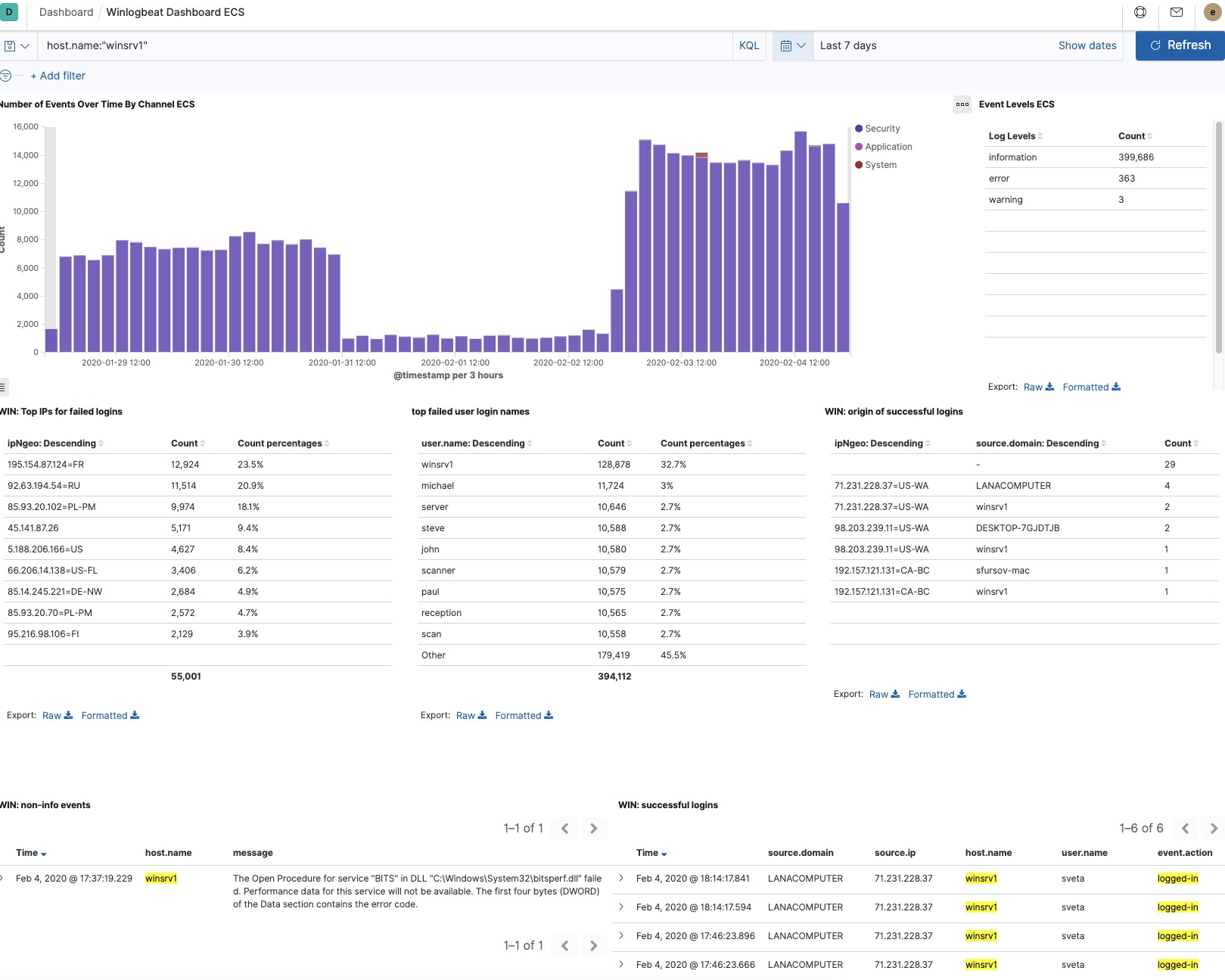
, 400 000 RDP.
, 55 001 IP ( IP ).
, fail2ban,
Update: , 443 — , (32000+), 443 , RDP — .
Update: , :
https://github.com/digitalruby/ipban
IPBan, :

IPBan2020-02-11 00:01:18.2517|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.228,, RDP, 1
2020-02-11 00:01:18.2686|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.228, Administrator, RDP, 2
2020-02-11 00:02:49.7098|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147,, RDP, 3
2020-02-11 00:02:49.7098|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147, Administrator, RDP, 4
2020-02-11 00:04:20.9878|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.184.20,, RDP, 5
2020-02-11 00:04:20.9878|WARN|DigitalRuby.IPBanCore.Logger|Banning ip address: 95.213.184.20, user name:, config black listed: False, count: 5, extra info:
2020-02-11 00:04:20.9878|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.184.20, Administrator, RDP, 5
2020-02-11 00:04:21.0040|WARN|DigitalRuby.IPBanCore.Logger|IP 95.213.184.20, Administrator, RDP ban pending.
2020-02-11 00:04:21.1237|WARN|DigitalRuby.IPBanCore.Logger|Updating firewall with 1 entries…
2020-02-11 00:05:36.6525|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.24,, RDP, 3
2020-02-11 00:05:36.6566|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.24, Administrator, RDP, 4
2020-02-11 00:07:22.4729|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 82.202.249.225, Administrator, RDP, 3
2020-02-11 00:07:22.4894|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 82.202.249.225,, RDP, 4
2020-02-11 00:08:53.1731|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 45.141.86.141,, RDP, 3
2020-02-11 00:08:53.1731|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 45.141.86.141, Administrator, RDP, 4
2020-02-11 00:09:23.4981|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 68.129.202.154,, RDP, 1
2020-02-11 00:09:23.5022|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 68.129.202.154, ADMINISTRATOR, RDP, 2
2020-02-11 00:10:39.0282|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147,, RDP, 5
2020-02-11 00:10:39.0336|WARN|DigitalRuby.IPBanCore.Logger|Banning ip address: 95.213.143.147, user name:, config black listed: False, count: 5, extra info:
2020-02-11 00:10:39.0336|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147, Administrator, RDP, 5
2020-02-11 00:10:39.0336|WARN|DigitalRuby.IPBanCore.Logger|IP 95.213.143.147, Administrator, RDP ban pending.
2020-02-11 00:10:39.1155|WARN|DigitalRuby.IPBanCore.Logger|Updating firewall with 1 entries…
2020-02-11 00:12:09.6470|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 82.202.249.225,, RDP, 5
2020-02-11 00:12:09.6470|WARN|DigitalRuby.IPBanCore.Logger|Banning ip address: 82.202.249.225, user name:, config black listed: False, count: 5, extra info:
b) username,
, .
: — , . : . , - : DESKTOP-DFTHD7C DFTHD7C:
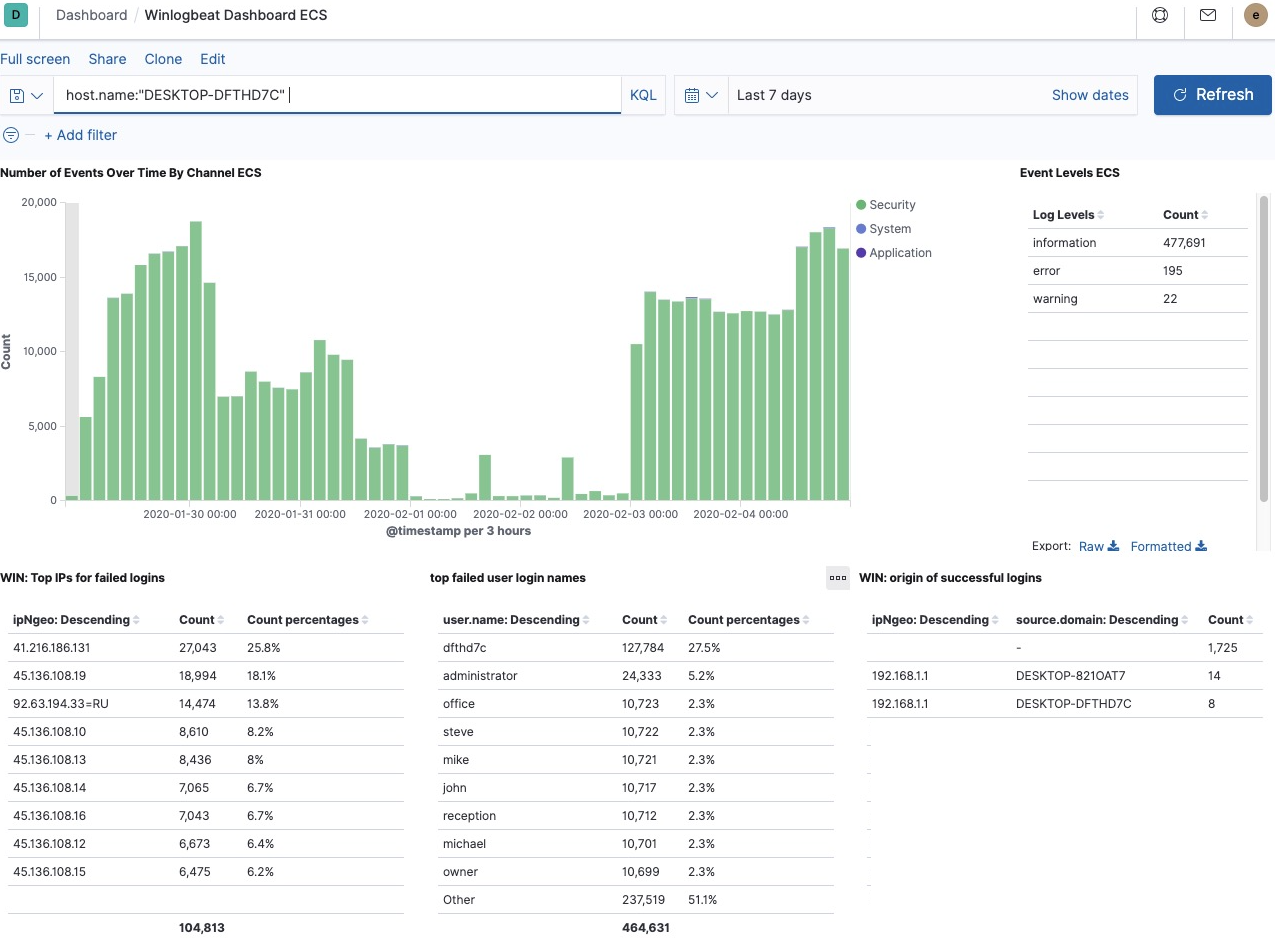
, DESKTOP-MARIA, MARIA.
, : , — "administrator". , Windows, .
- .https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/local-accounts#administrator-account
Administrator account
The default local Administrator account is a user account for the system administrator. Every computer has an Administrator account (SID S-1-5-domain-500, display name Administrator). The Administrator account is the first account that is created during the Windows installation.
The Administrator account has full control of the files, directories, services, and other resources on the local computer. The Administrator account can create other local users, assign user rights, and assign permissions. The Administrator account can take control of local resources at any time simply by changing the user rights and permissions.
The default Administrator account cannot be deleted or locked out, but it can be renamed or disabled.
: .
, Administrator Murmansk#9. , , , , — .
Administrator , ? !
:
, , Windows Server - - , .
, ?
, RDP, :
— .
, - IP - , IP ( ) PowerShell:
New-NetFirewallRule -Direction Inbound -DisplayName "fail2ban" -Name "fail2ban" -RemoteAddress ("185.143.0.0/16", "185.153.0.0/16", "193.188.0.0/16") -Action Block
Elastic, Winlogbeat Auditbeat, . SIEM (Security Information & Event Management) Kibana. , — Auditbeat Linux , SIEM .
:
奖励:50个用户的列表,这些用户最常用于通过RDP进行登录尝试