Hanya beberapa hari yang lalu, sekelompok ilmuwan Cina menemukan kerentanan yang memungkinkan serangan DDoS dengan amplifikasi. Para penulis berhasil melakukan serangan dengan faktor 43.000! Serangan baru tidak hanya dapat menghabiskan sumber daya dari saluran keluar dari server web target, tetapi juga saluran dari node CDN. Rentan adalah 13 dari 13 penyedia CDN terbesar yang terbukti, termasuk Akamai, Fastly, dan Cloudflare. Di bawah cut, pertimbangkan mekanisme serangan dan langkah-langkah yang diusulkan oleh penulis.

, , Range-based Amplification ttack RangeAmp. CDN range request HTTP, - . — . , , Akamai ~15-30% - . RFC range request , CDN . .
13 CDN : Akamai, Alibaba Cloud, Azure, CDN77, CDNsun, Cloudflare, CloudFront, Fastly, G-Core Labs, Huawei Cloud, KeyCDN, StackPath Tencent Cloud.
- Linux c 2.4GHz CPU, 16G DDR 1000 Mbps .
- Apache/2.4.18 . CDN .
Range request
range request -. . , .
, Range. , . , . , Accept-Ranges "bytes".
range CDN - Range. :
- Laziness () — .
- Deletion () — .
- Expansion () — , .
CDN 2 3. , , , , .
, ? RFC7233 , range . , 4 13 CDN .
, — . .. , ! .
Deletion Expansion CDN , , CDN . . Range, CDN - . Small Byte Range Attack SBR RangeAmp. DDoS-, . , , , "" CDN, .., CDN .
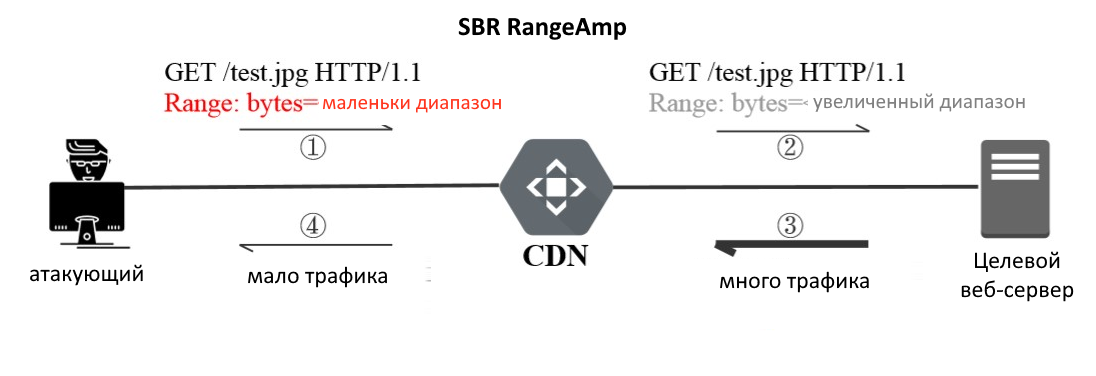
, . 25 MB Akamai 43000!
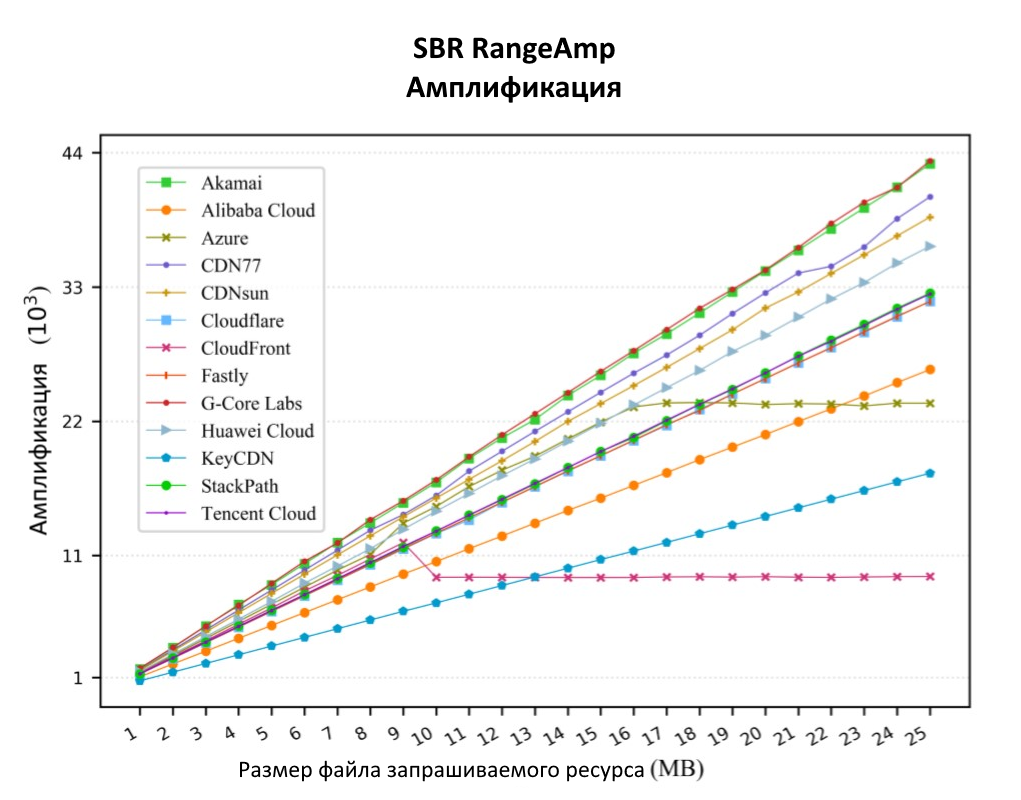
13 CDN : Akamai, Alibaba Cloud, Azure, CDN77, CDNsun, Cloudflare, CloudFront, Fastly, G-Core Labs, Huawei Cloud, KeyCDN, StackPath Tencent Cloud.
CDN
, . CDN, CDN , Frontend CDN FCDN. CDN, -, Backend CDN (. ).
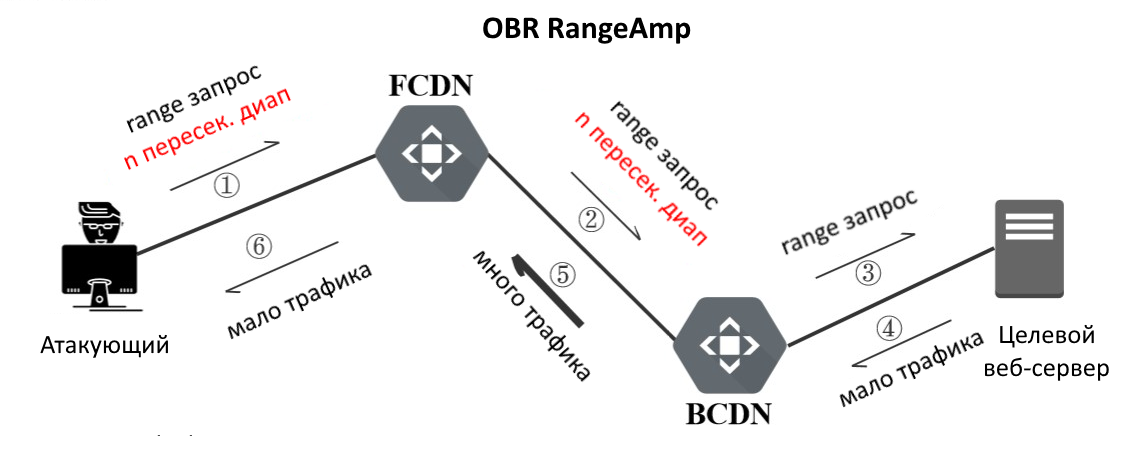
, :
- FCDN Laziness Range " ".
- BCDN , Range .
, n , BCDN n * ( ). , . TCP Receive Window, .
, , . .. Range.
, RFC , , 4 : CloudFlare, CDN77, CDNsun, StackPath. 1KB (, n — ):
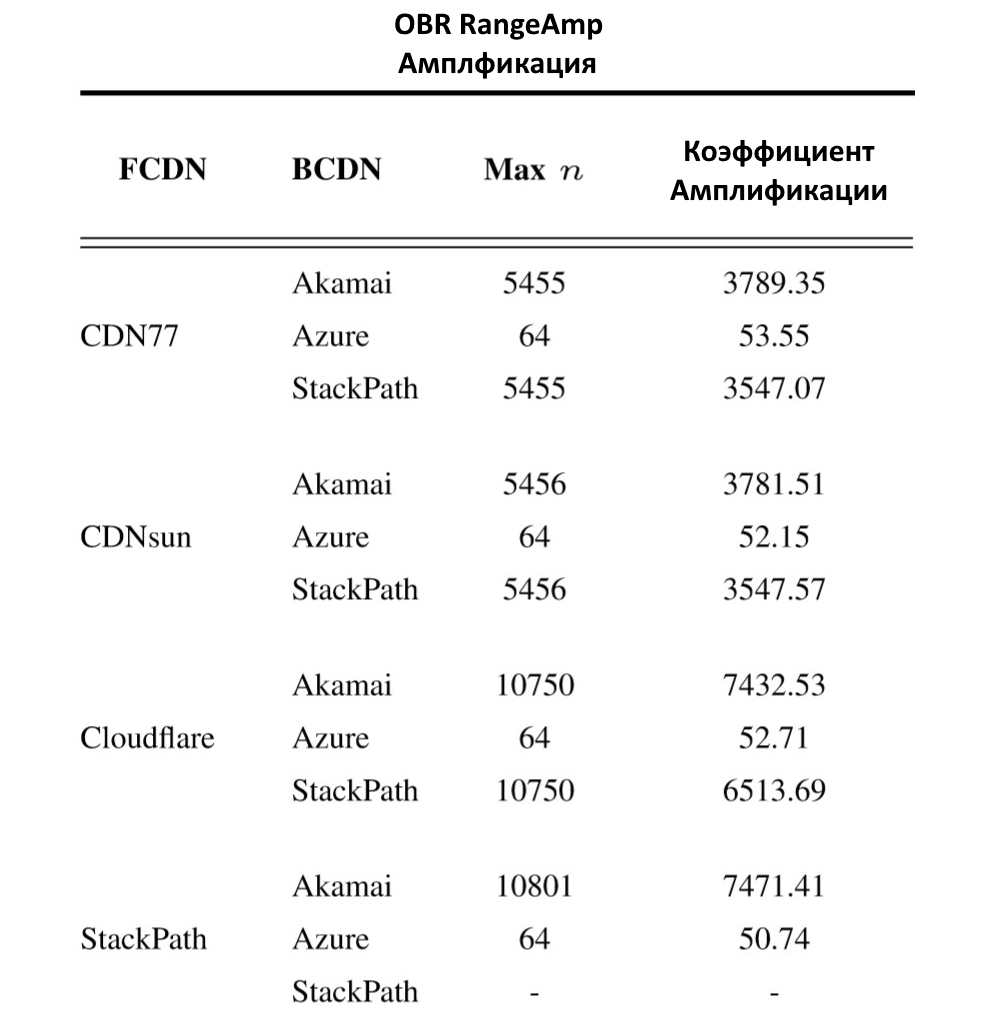
?
, . - (SBR RangeAmp), — CDN (OBR RangeAmp) HTTP/1.1, HTTP/2.
CDN RFC.
CDN :
- , , RFC7233 .
- Range Laziness , Expansion, .
Source:
CDN Backfired: Amplification Attacks Based on HTTP Range Requests, Weizhong Li, Kaiwen Shen, Run Guo, Baojun Liu, Jia Zhang, Haixin Duan, Shuang Hao, Xiarun Chen, Yao Wan.
.
P.S.
CloudFlare , , , .
"They thought that the SBR attack relies on constantly triggering a cache-miss and a customer can add a page rule to ignore query strings. But this does not solve the problem fundamentally. The malicious customers and some normal customers will not follow this suggestion. Unfortunately, they won’t implement our mitigation solutions because Cloudflare does not want to cache partial responses of certain resources."