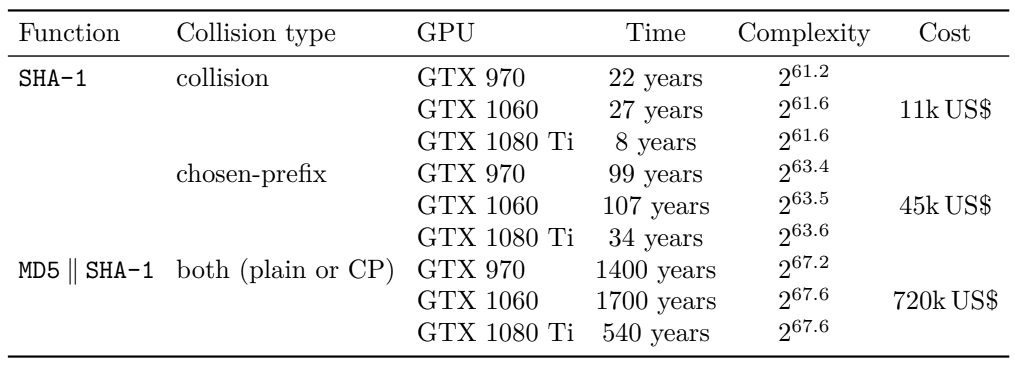
 The complexity of attacks on SHA-1. The price is based on the calculation of the rental price of one GTX 1060 at $ 35 / month.Much later than all the others, but the developers of the libraries for SSH decided to finally disable the outdated SHA-1 crypto function by default. Today, the selection of the server authentication key SHA-1, that is, a conflict with the selected prefix, on a rented GPU cluster will cost $ 45 thousand , as indicated in the table above. This makes the attack accessible not only for state intelligence services, but also for commercial clients.Disabling SHA-1 by default was simultaneously announced by the developers of the OpenSSH openSSH ( release notes ) and libssh ( code change )libraries.The Secure Hash Algorithm (SHA) was developed by the NSA in collaboration with NIST. The first version of SHA-0 was introduced in 1993, but soon the NSA withdrew this version, citing an error they discovered that was never disclosed.A fixed version of the NSA was published in 1995, it was called SHA-1.The SHA-1 (Secure Hash Algorithm 1) cryptographic hash function generates a 160-bit string called a hash digest. Theoretically, digests should be unique for each file, message, or other input to the function. As an input value, SHA-1 accepts a message no more thanbit, i.e. approximately 2 exabytes.It is clear that the range of digest values is smaller than the range of input values. But in practice, digest collisions should not be feasible, given the performance capabilities of existing computing resources. Unfortunately, SHA-1 no longer meets this criterion.In 2017, employees at Google and the Center for Mathematics and Computer Science in Amsterdam introduced the first way to generate collisions for SHA-1 .They published a proof: two PDF documents with different contents but the same digital signatures SHA-1.
The complexity of attacks on SHA-1. The price is based on the calculation of the rental price of one GTX 1060 at $ 35 / month.Much later than all the others, but the developers of the libraries for SSH decided to finally disable the outdated SHA-1 crypto function by default. Today, the selection of the server authentication key SHA-1, that is, a conflict with the selected prefix, on a rented GPU cluster will cost $ 45 thousand , as indicated in the table above. This makes the attack accessible not only for state intelligence services, but also for commercial clients.Disabling SHA-1 by default was simultaneously announced by the developers of the OpenSSH openSSH ( release notes ) and libssh ( code change )libraries.The Secure Hash Algorithm (SHA) was developed by the NSA in collaboration with NIST. The first version of SHA-0 was introduced in 1993, but soon the NSA withdrew this version, citing an error they discovered that was never disclosed.A fixed version of the NSA was published in 1995, it was called SHA-1.The SHA-1 (Secure Hash Algorithm 1) cryptographic hash function generates a 160-bit string called a hash digest. Theoretically, digests should be unique for each file, message, or other input to the function. As an input value, SHA-1 accepts a message no more thanbit, i.e. approximately 2 exabytes.It is clear that the range of digest values is smaller than the range of input values. But in practice, digest collisions should not be feasible, given the performance capabilities of existing computing resources. Unfortunately, SHA-1 no longer meets this criterion.In 2017, employees at Google and the Center for Mathematics and Computer Science in Amsterdam introduced the first way to generate collisions for SHA-1 .They published a proof: two PDF documents with different contents but the same digital signatures SHA-1. $ls -l sha*.pdf
-rw-r--r--@ 1 amichal staff 422435 Feb 23 10:01 shattered-1.pdf
-rw-r--r--@ 1 amichal staff 422435 Feb 23 10:14 shattered-2.pdf
$shasum -a 1 sha*.pdf
38762cf7f55934b34d179ae6a4c80cadccbb7f0a shattered-1.pdf
38762cf7f55934b34d179ae6a4c80cadccbb7f0a shattered-2.pdf
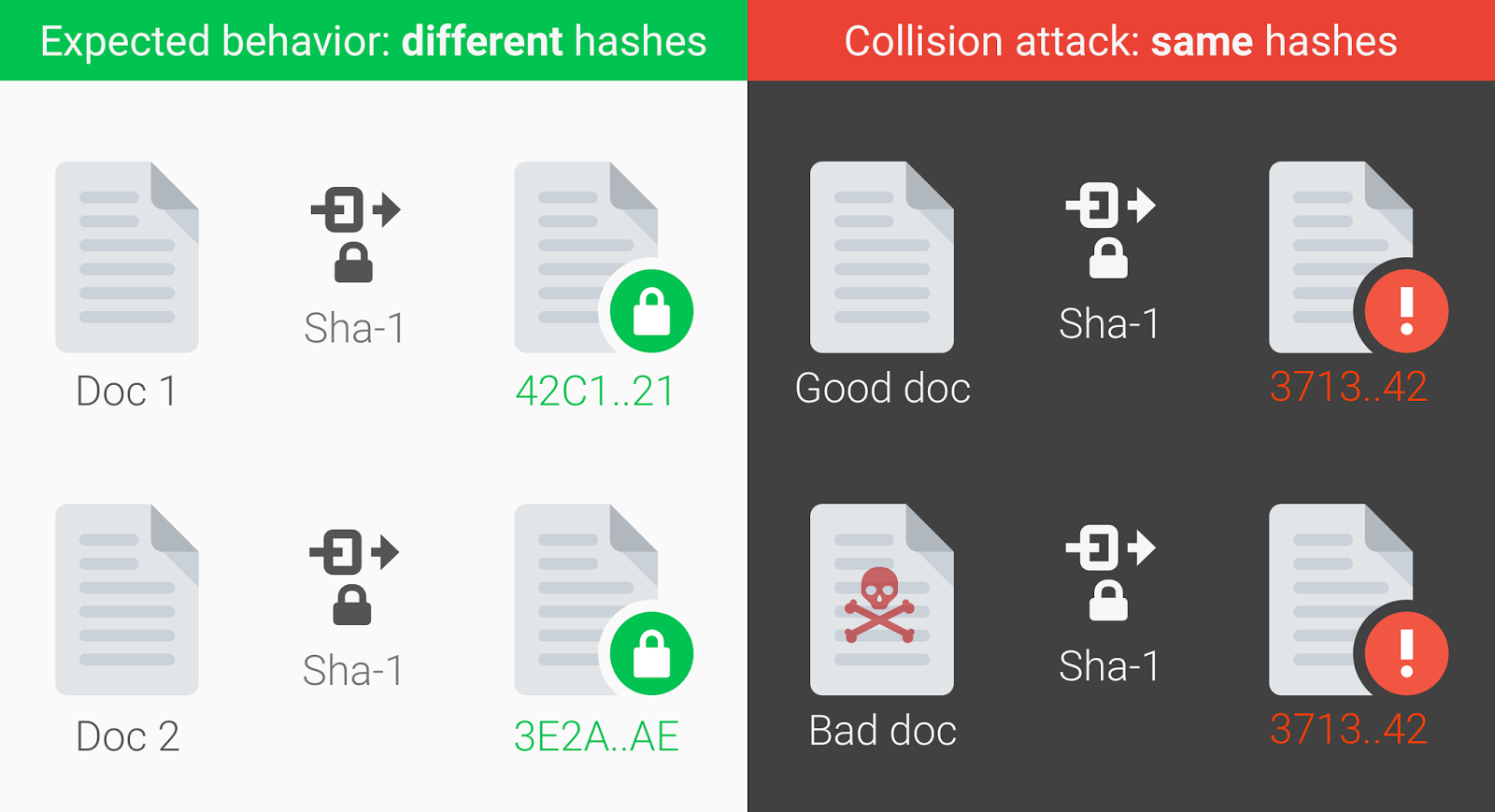 On the shattered.it website, you can check any file for whether it is included in the space of possible collisions. That is, is it possible to pick up another data set (file) with the same hash. The attack vector is clear: an attacker can replace a “good” file with his copy with a bookmark, a malicious macro or a trojan downloader. And this “bad” file will have the same hash or digital signature.In recent years, many programs and services have stopped using SHA-1 after researchers have shown practical ways to counterfeit digital signatures using SHA-1. The unanimous opinion of experts is that this algorithm is now not safe in almost all security contexts.Google has long expressed its distrust of SHA-1, especially as using this feature to sign TLS certificates. Back in 2014, the Chrome development team announced the phasing out of SHA-1.In 2017, researchers used the Google infrastructure to perform calculations and check theoretical calculations of how much the search for collision would take. Developers say this was one of the largest computing ever done by Google. In total, nine quintillion SHA-1 calculations were performed (9,223,372,036,854,775,808), which required 6,500 processor years in the first phase and 110 years of GPU in the second phase of the attack.Message blocks with the same SHA-1 hash
On the shattered.it website, you can check any file for whether it is included in the space of possible collisions. That is, is it possible to pick up another data set (file) with the same hash. The attack vector is clear: an attacker can replace a “good” file with his copy with a bookmark, a malicious macro or a trojan downloader. And this “bad” file will have the same hash or digital signature.In recent years, many programs and services have stopped using SHA-1 after researchers have shown practical ways to counterfeit digital signatures using SHA-1. The unanimous opinion of experts is that this algorithm is now not safe in almost all security contexts.Google has long expressed its distrust of SHA-1, especially as using this feature to sign TLS certificates. Back in 2014, the Chrome development team announced the phasing out of SHA-1.In 2017, researchers used the Google infrastructure to perform calculations and check theoretical calculations of how much the search for collision would take. Developers say this was one of the largest computing ever done by Google. In total, nine quintillion SHA-1 calculations were performed (9,223,372,036,854,775,808), which required 6,500 processor years in the first phase and 110 years of GPU in the second phase of the attack.Message blocks with the same SHA-1 hash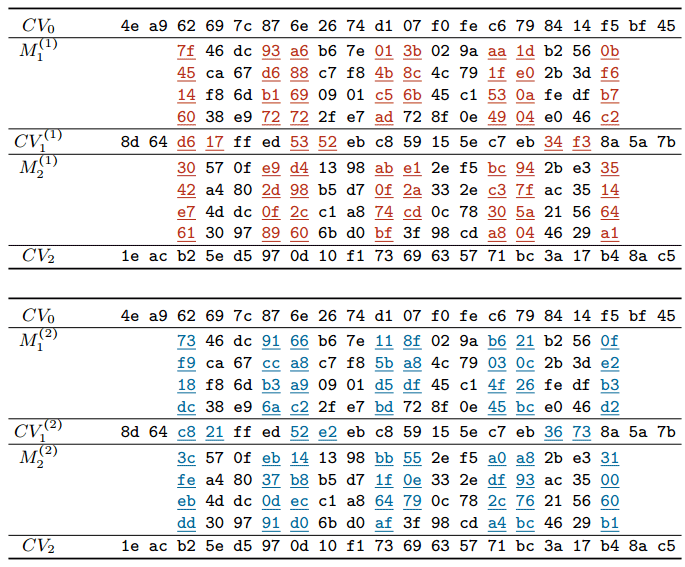 In 2019, researchers Gaetan Laurent and Thomas Peyrin demonstrated an attack on finding a conflict with a chosen-prefix, which makes practical sense for selecting specific PGP / GnuPG encryption keys. Finally, in January 2020, the authors managed to optimize the attack by an order of magnitude and reduce its theoretical cost to a commercially acceptable price (see table above and pdf ). To demonstrate, they created a pair of different PGP / GnuPG keys with the same SHA-1 certificates.As a defense against an attack on finding SHA-1 collisions, it is recommended to switch to better cryptographic hash functions SHA-256 and SHA-3.OpenSSH developers, who wrote in the notes for the latest release, cite this study from January 2020: “Now you can perform attacks with the selected prefix using the SHA-1 algorithm for less than 50 thousand US dollars. For this reason, in the near future we will disable the default ssh-rsa public key signing algorithm. Unfortunately, this algorithm is still widely used. Despite the existence of better alternatives, it has long remained the only public key signature algorithm defined by the original SSH RFC. ”Among the best alternatives, OpenSSH developers call the RFC8332 RSA SHA-2 algorithms (supported from OpenSSH 7.2 and already used by default if the server and client support it), ssh-ed25519 (supported from 6.5) and RFC5656 ECDSA (from version 5.7) .To verify that the server uses the weak SHA-1 algorithm when generating the public key for authentication, try connecting to it after removing the ssh-rsa algorithm from the list of allowed in ssh (1) :
In 2019, researchers Gaetan Laurent and Thomas Peyrin demonstrated an attack on finding a conflict with a chosen-prefix, which makes practical sense for selecting specific PGP / GnuPG encryption keys. Finally, in January 2020, the authors managed to optimize the attack by an order of magnitude and reduce its theoretical cost to a commercially acceptable price (see table above and pdf ). To demonstrate, they created a pair of different PGP / GnuPG keys with the same SHA-1 certificates.As a defense against an attack on finding SHA-1 collisions, it is recommended to switch to better cryptographic hash functions SHA-256 and SHA-3.OpenSSH developers, who wrote in the notes for the latest release, cite this study from January 2020: “Now you can perform attacks with the selected prefix using the SHA-1 algorithm for less than 50 thousand US dollars. For this reason, in the near future we will disable the default ssh-rsa public key signing algorithm. Unfortunately, this algorithm is still widely used. Despite the existence of better alternatives, it has long remained the only public key signature algorithm defined by the original SSH RFC. ”Among the best alternatives, OpenSSH developers call the RFC8332 RSA SHA-2 algorithms (supported from OpenSSH 7.2 and already used by default if the server and client support it), ssh-ed25519 (supported from 6.5) and RFC5656 ECDSA (from version 5.7) .To verify that the server uses the weak SHA-1 algorithm when generating the public key for authentication, try connecting to it after removing the ssh-rsa algorithm from the list of allowed in ssh (1) :ssh -oHostKeyAlgorithms=-ssh-rsa user@host
If the verification fails and other types of keys are not available, then the server software should be updated.In future versions of OpenSSH, the UpdateHostKeys option will be enabled by default, in which the client will automatically switch to the best algorithms. It can be activated manually.Apparently, the complete shutdown of SHA-1 will take a lot of time. Gaetan Laurent of the National Institute for Research in Informatics and Automation (France), one of the co-authors of the January study, does not expect OpenSSH developers to quickly do this: “When they completely disable SHA-1, it will be impossible to connect from the new version of OpenSSH to the device with the old SSH server, - writeshe. - Probably, before this they will take a series of gradual steps (with loud warnings). On the other hand, in embedded systems with SSH that have not been updated for many years, there are probably many security problems, so it might not be too bad to disrupt their work ... Anyway, I am quite pleased with this move, this exactly what we wanted to achieve :-) ”.After OpenSSH and libssh announced plans to disable SHA-1, the list of SHA-1 users became shorter, but did not disappear. The feature is still supported in the latest versions of the OpenSSL library, which many websites and Internet services use to implement HTTPS and other encryption protocols. The latest version of the GNU Collection compiler, released earlier this month, is digitally signed with the SHA-1 hash.Linus Torvaldssaidthat in Git repositories hash collisions do not pose a security risk. He explained that there is a big difference between using a cryptographic hash for digital signatures in encryption systems and for generating “content identification” in a system like Git. When all the data is in the public domain, then a real attack is almost impossible. The authors of the scientific work give an example of an attack on documents with the same prefix. This attack is successful because the prefix itself is “closed” inside the document, like a blob. If we have open source in the repository, then this is a completely different matter. It is hardly possible to make such a prefix from the source code (only from blob). In other words, to create an identical prefix and then generate code branches with the same SHA-1 hashes, you will have to inject some random data into the code, which will be noticed right away. Linus saysthat there are places where you can hide the data, butgit fsckalready catches such tricks. However, Linus has a plan to get away from using SHA-1 so that no one even has to convert their repositories.