Hello everyone. Today we’ll look at an example where an attacker managed to bypass Windows Defender, but failed - a security guard. Yes, this is again about mimikatz. How, by launching mimikatz, to bypass Windows Defender, you can read here. And today, as I promised, consider something for the “blue” team. If it helps anyone at least, then it’s not in vain. So let's go.A lot has been written about the ELK stack (Elasticsearch, Logstash, Kibana) (including on the Habré), and today we will use it, or to be more precise, an ELK doped to our needs for threat hunting.The Hunting ELK, or HELK
The HELK diagram looks like this: Let's move on to the installation.As the server where HELK will be located, I chose, as the developer advises:
Let's move on to the installation.As the server where HELK will be located, I chose, as the developer advises:tomhunter@helk:~$ cat /etc/lsb-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=18.04
DISTRIB_CODENAME=bionic
DISTRIB_DESCRIPTION="Ubuntu 18.04.4 LTS"
Installation is simple and performed in 2 commands:git clone https://github.com/Cyb3rWard0g/HELK
tomhunter@helk:~/HELK/docker$ sudo ./helk_install.sh
Note: you may be asked to allocate more RAM for installation. I use 10 GB.
From the proposed installation options, I chose KAFKA + KSQL + ELK + NGNIX + ELASTALERT . And now just waiting. And, if we did everything right, we will see the cherished: With the server finished, let's prepare the client. It will be a Windows 10 machine. We need to install Sysmon on it.We also need a configuration file:
With the server finished, let's prepare the client. It will be a Windows 10 machine. We need to install Sysmon on it.We also need a configuration file: git clone https://github.com/olafhartong/sysmon-modular
Generate the config: . .\Merge-SysmonXml.ps1
Merge-AllSysmonXml -Path ( Get-ChildItem '[0-9]*\*.xml') -AsString | Out-File sysmonconfig.xml
Run: PS C:\Users\Tomhunter\Documents\sysmon-modular> .\Sysmon64.exe -i .\sysmonconfig.xml
We will also install winlogbeat , delete the winlogbeat.yml file and create a new one by copying raw.githubusercontent.com/Cyb3rWard0g/HELK/master/configs/winlogbeat/winlogbeat.yml into itNote: here we also need to change the IP address to the desired one (in my case hosts: ["192.168.31.97:9092"].
Install: PS C:\Users\Tomhunter\Desktop\winlogbeat-7.6.2-windows-x86_64> .\install-service-winlogbeat.ps1
Note: you need to enable the service by hand, or reboot the system.
Everything is ready, let's see what we get.We start mimikatz on Windows 10. And, having entered the cybana (in my case it is 192.168.31.97 , default credentials: helk: hunting) we see an alert. In its raw form, it looks like this:
And, having entered the cybana (in my case it is 192.168.31.97 , default credentials: helk: hunting) we see an alert. In its raw form, it looks like this: Alerts can be sent to yourself by e-mail, in slack, etc.But we are much more interested in how this works, let's understand.
Alerts can be sent to yourself by e-mail, in slack, etc.But we are much more interested in how this works, let's understand.Bit of theory
After starting mimikatz with Windows 10, the following message flies: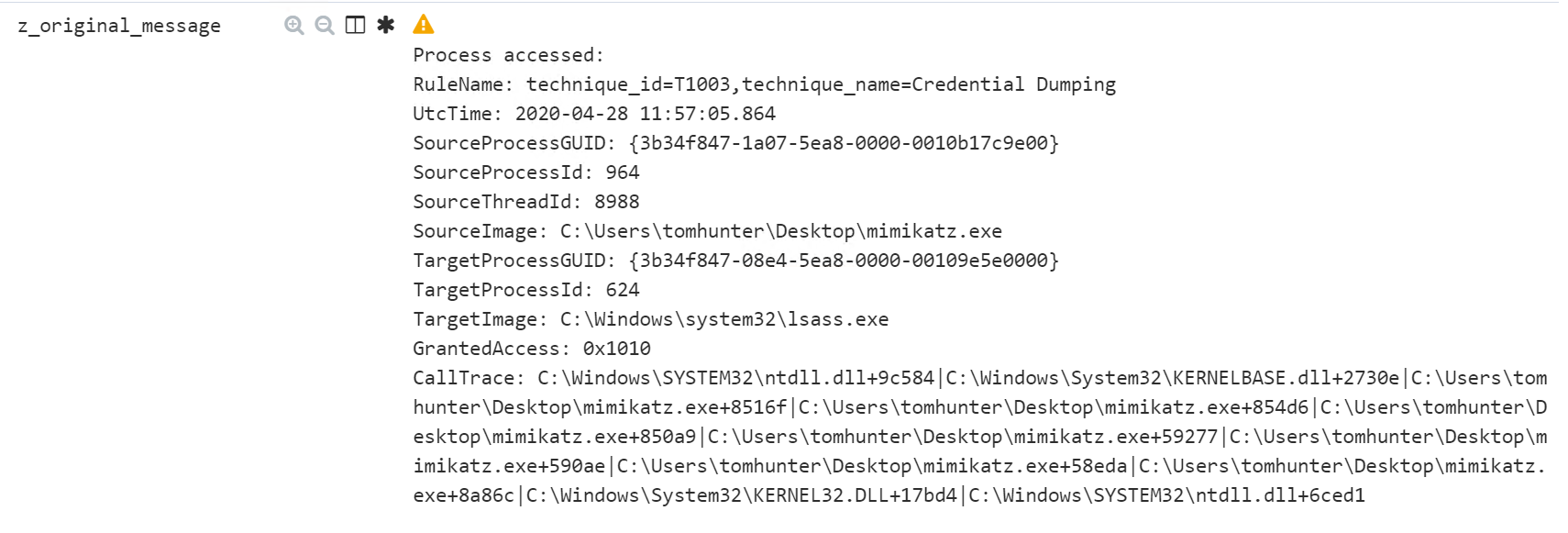 What is the rule that issued the alert that confused me? (spoiler: not the mimikatz.exe file name). Let's take a look at the rule itself:
What is the rule that issued the alert that confused me? (spoiler: not the mimikatz.exe file name). Let's take a look at the rule itself:sudo docker exec -it helk-elastalert bash
cat /opt/sigma/rules/windows/sysmon/sysmon_mimikatz_detection_lsass.yml
 EventID: 10. This is our ProcessAccess.TargetImage: C: \ windows \ system32 \ lsass.exe. This is good, but mimikatz is not the only one who turns to lsass.
EventID: 10. This is our ProcessAccess.TargetImage: C: \ windows \ system32 \ lsass.exe. This is good, but mimikatz is not the only one who turns to lsass. GrantedAccess: 0x1410 or 0x1010.And here everything falls into place. I explain.Let's take a look at the source code of mimikatz, namely, we are interested in the file kuhl_m_sekurlsa.c and the function kuhl_m_sekurlsa_acquireLSA ()
GrantedAccess: 0x1410 or 0x1010.And here everything falls into place. I explain.Let's take a look at the source code of mimikatz, namely, we are interested in the file kuhl_m_sekurlsa.c and the function kuhl_m_sekurlsa_acquireLSA () Turning to the Microsoft website, we see that
Turning to the Microsoft website, we see thatPROCESS_QUERY_LIMITED_INFORMATION (0x1000)
PROCESS_VM_READ (0x0010)
PROCESS_QUERY_INFORMATION (0x0400)
Using bitwise “OR” we get our Granted AccessNote: earlier in the sigma rule there was only 0x1410 detection, this is probably due to the fact that older versions of mimikatz made both requests (PROCESS_QUERY_INFORMATION and PROCESS_QUERY_LIMITED_INFORMATION), however, mimikatz passed with 0x1010, so you had to adjust the rule yourself. Now there is no such problem, and everything works out of the box.
Thus, if in the kiban we set the filterevent_id: 10 AND process_target_name: "* lsass.exe" AND process_granted_access: "0x1010", then we will only have our mimikatz.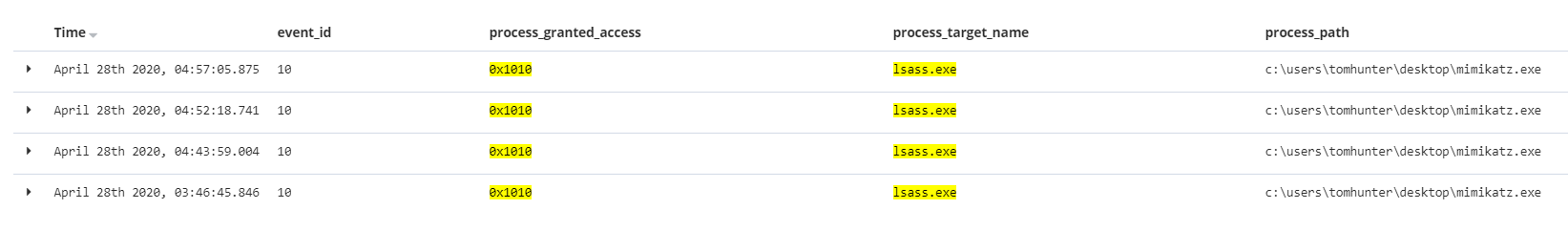 From the pleasant: there are rules for mimikatz_inmemory, mimikatz_trough_winrm, and even safetycatz (.NET version of mimikatz with its own chips).
From the pleasant: there are rules for mimikatz_inmemory, mimikatz_trough_winrm, and even safetycatz (.NET version of mimikatz with its own chips).What else can you do?
The rules, of course, are not limited to mimikatz, there are a lot of them. They are divided into categories application, cloud, compliance, linux, network, proxy, web and windows. Categories are divided into subcategories. For example, windows is divided into builtin, malware, other, powershell, process_creation, sysmon.And who knows, perhaps by including powershell logging in the GPO, you will receive alerts according to these rules: That seems to be all.
That seems to be all. Subscribe to the channel, like, click the bell.