 I understand perfectly well that you got tired of the ubiquitous Mikrotik, but it is really interesting. In fact, the article was written with a delay of 4 months (support for SOCKS5 appeared in January 2020), but better late than never, especially since there is not much information about this and few people are aware.So let's get started!
I understand perfectly well that you got tired of the ubiquitous Mikrotik, but it is really interesting. In fact, the article was written with a delay of 4 months (support for SOCKS5 appeared in January 2020), but better late than never, especially since there is not much information about this and few people are aware.So let's get started!Background
Mikrotik is a very powerful tool that (IMHO) should be on the farm of any network engineer. Huge functionality and a set of tools, constantly replenished with each release. Changelog for RouterOS 6.47 (beta) noticed SOCKS5 support, which I personally had been waiting for several years (and many others, judging by the numerous “Feature Request” on forum.mikrotik.com ): Judging by one of the branches of the aforementioned forum , support for the built-in SOCKS5 server started with version 6.47beta19.
Judging by one of the branches of the aforementioned forum , support for the built-in SOCKS5 server started with version 6.47beta19.Customization
The setup, as always with MikroTik, is quite simple and fits into four lines.A virtual server with CHR (Cloud Hosted Router), updated to 6.47beta53, acted as a test subject.The beta prefix in the RouterOS version means that it is intended solely for testing and sending bug reports to support [at] mikrotik.com. I highly recommend not to rush to upgrade the hardware under load and wait for the Long-Term or at least Stable release. If you decide to upgrade, then read Changelog carefully to be aware of all the changes and possible problems.We configure the SOCKS5 server, select authorization by password (it is possible to make it open), 3327 is specified as the port (different from the standard 1080) so as not to get into the botnet scan lists:ip socks set enabled=yes version=5 port=3327 auth-method=password
Next, add the user:ip socks users add name=test_socks5 password=Str0nGP@SSw0RD
Create an exception rule in the firewall:ip firewall filter add chain=input protocol=tcp dst-port=3327 action=accept comment="SOCKS5 TCP"
And we move our rule before the rule of the "drop" type:ip firewall filter move [/ip firewall filter find comment="SOCKS5 TCP"] 0
Done! On our Mikrotik, a SOCKS5 proxy server has been raised.Check
Like any resident of the Russian Federation, having a proxy server in Europe, I immediately recall telegrams, and the functionality of the freshly configured SOCKS5 server was checked on it: Calls also work fine, despite the Free CHR version being limited to 1Mbps.Then it became interesting how POF (Passive OS Fingerprint) introduced by Mikrotik will look like (checked on WhatLeaks ):It can be seen that the system is defined as Linux, which is logical (because it is precisely its core that underlies ROS) and cannot but rejoice. Yes, it was possible to replace user-agent, but we have a slightly different task.At the same time, on Mikrotik itself, as it should be for a real server, statistics on connections and traffic are displayed:
Calls also work fine, despite the Free CHR version being limited to 1Mbps.Then it became interesting how POF (Passive OS Fingerprint) introduced by Mikrotik will look like (checked on WhatLeaks ):It can be seen that the system is defined as Linux, which is logical (because it is precisely its core that underlies ROS) and cannot but rejoice. Yes, it was possible to replace user-agent, but we have a slightly different task.At the same time, on Mikrotik itself, as it should be for a real server, statistics on connections and traffic are displayed: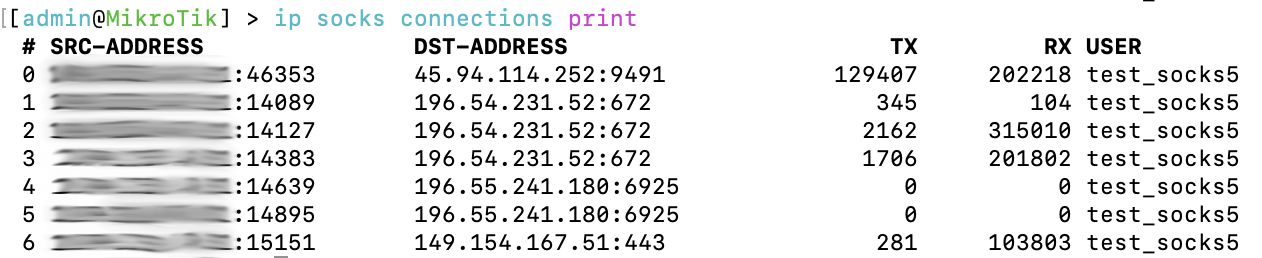
Conclusion
In fact, a lot is missing (for example, support for authentication via RADIUS), but I sincerely believe that this option will be further developed. It is important to note that this is still a router and its main task is traffic forwarding, and the rest of the “features” are more likely just nice. In any case, the realization that a piece of iron for $ 50 can do so much excites the imagination.That's all, thanks for watching :)