Minio is a simple, fast, and AWS S3 compliant object store. Minio is designed to host unstructured data such as photos, videos, log files, backups. Minio also supports distributed mode, which provides the ability to connect multiple drives to objects on the same storage server, including those located on different machines.
The goal of this post is to configure minio so that each user can only work with his own bucket.
In general, Minio is suitable for the following cases:
- replication-free storage on top of a reliable file system with access via S3 (small and medium-sized storages located on NAS and SAN);
- replication-free storage on top of an untrusted file system with S3 access (for development and testing);
- Replication storage on a small group of servers in the same rack with S3 access (fail-safe storage with a failure domain equal to the rack).
On RedHat systems we connect the unofficial Minio repository.
yum -y install yum-plugin-copr
yum copr enable -y lkiesow/minio
yum install -y minio minio-mc
We generate and add to MINIO_ACCESS_KEY and MINIO_SECRET_KEY in /etc/minio/minio.conf.
# Custom username or access key of minimum 3 characters in length.
MINIO_ACCESS_KEY=
# Custom password or secret key of minimum 8 characters in length.
MINIO_SECRET_KEY=
If you will not use nginx before Minio, then you need to change.
--address 127.0.0.1:9000
on the
--address 0.0.0.0:9000
Launch Minio.
systemctl start minio
Create a connection to Minio called myminio.
minio-mc config host add myminio http://localhost:9000 MINIO_ACCESS_KEY
MINIO_SECRET_KEY
Create bucket user1bucket.
minio-mc mb myminio/user1bucket
bucket user2bucket.
minio-mc mb myminio/user2bucket
user1-policy.json.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:PutBucketPolicy",
"s3:GetBucketPolicy",
"s3:DeleteBucketPolicy",
"s3:ListAllMyBuckets",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::user1bucket"
],
"Sid": ""
},
{
"Action": [
"s3:AbortMultipartUpload",
"s3:DeleteObject",
"s3:GetObject",
"s3:ListMultipartUploadParts",
"s3:PutObject"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::user1bucket/*"
],
"Sid": ""
}
]
}
user2-policy.json.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:PutBucketPolicy",
"s3:GetBucketPolicy",
"s3:DeleteBucketPolicy",
"s3:ListAllMyBuckets",
"s3:ListBucket"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::user2bucket"
],
"Sid": ""
},
{
"Action": [
"s3:AbortMultipartUpload",
"s3:DeleteObject",
"s3:GetObject",
"s3:ListMultipartUploadParts",
"s3:PutObject"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::user2bucket/*"
],
"Sid": ""
}
]
}
user1 test12345.
minio-mc admin user add myminio user1 test12345
user2 test54321.
minio-mc admin user add myminio user2 test54321
Minio user1-policy user1-policy.json.
minio-mc admin policy add myminio user1-policy user1-policy.json
Minio user2-policy user2-policy.json.
minio-mc admin policy add myminio user2-policy user2-policy.json
user1-policy user1.
minio-mc admin policy set myminio user1-policy user=user1
user2-policy user2.
minio-mc admin policy set myminio user2-policy user=user2
minio-mc admin user list myminio
enabled user1 user1-policy
enabled user2 user2-policy
http://ip----minio:9000/minio/
Minio MINIO_ACCESS_KEY=user1. bucket user1bucket.
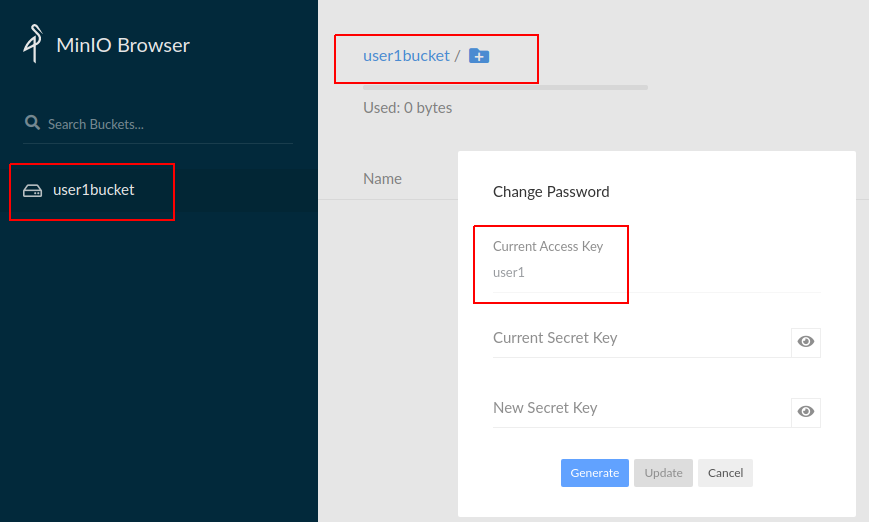
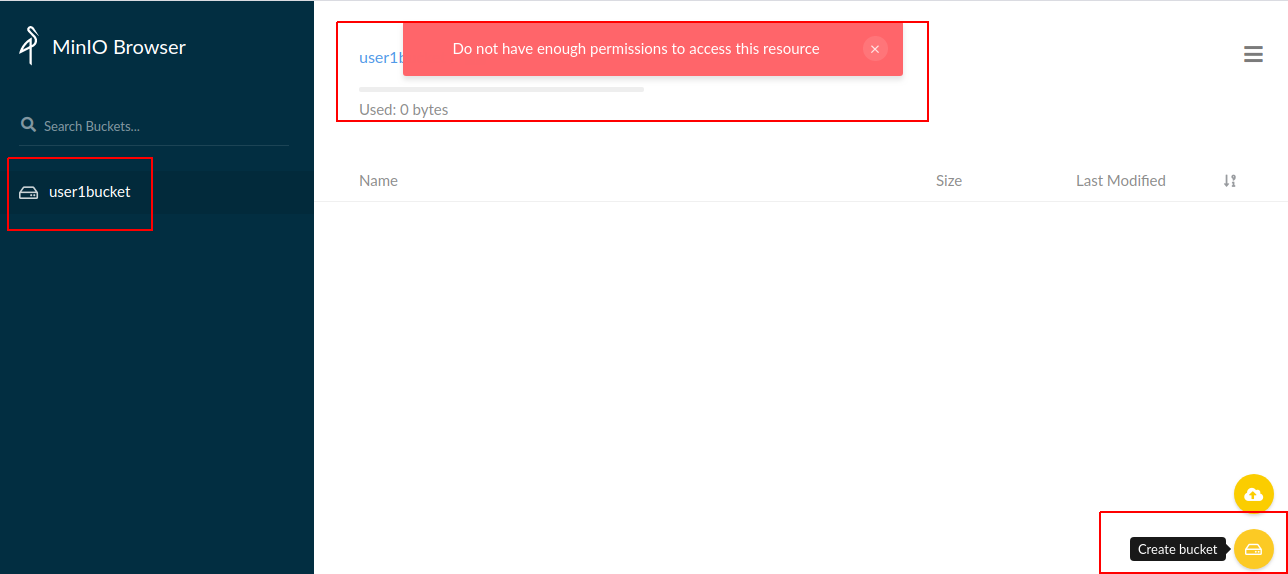
bucket , Action .
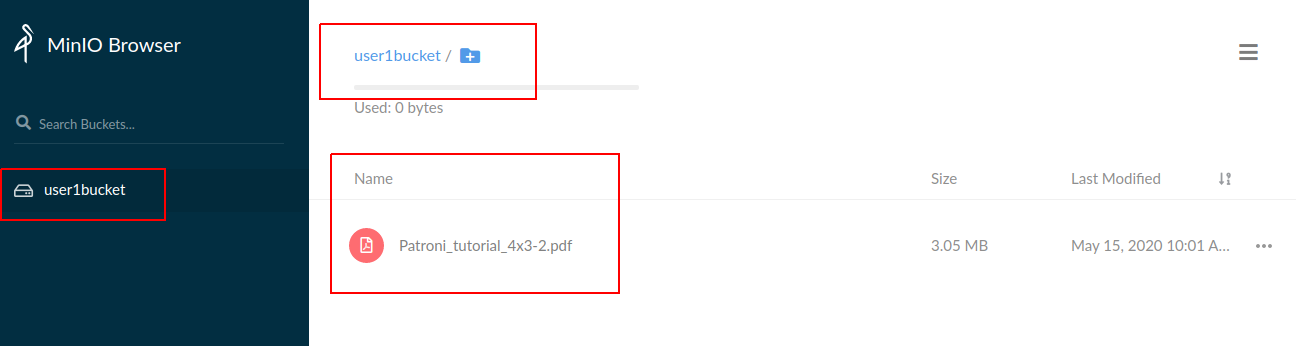
Create a file in bucket user1bucket.
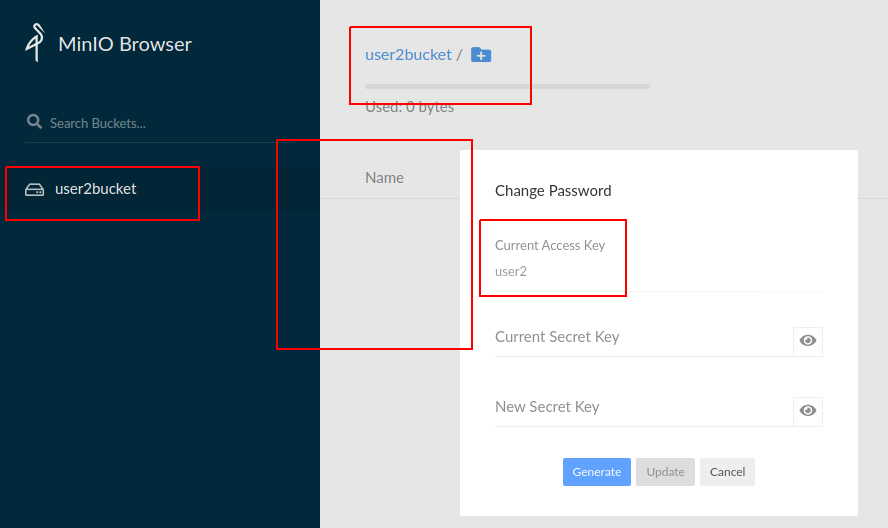
Connect to Minio under MINIO_ACCESS_KEY = user2. Bucket user2bucket is available for us.
And we see neither user1bucket nor files from user1bucket.
Created Telegram chat on Minio https://t.me/minio_s3_en