 I want to share some tips on setting up remote connection to workstations via RDP. I'll tell you how to upgrade the ancient RPC-HTTP to UDP, praise and scold Windows 10 and AVC, I will figure out a solution to several typical problems.We believe that Remote Desktop Gateway (RDGW) is used for connection, and workstations act as servers. Using RDGW is very convenient because the gateway becomes a common entry point for all clients. This makes it possible to better control access, keep records of connections and their duration. Even if the VPN allows you to connect to working machines directly, this is not the best option.RDGW is quick, easy to configure, and Let's Encrypt and win-acme easily solve the problem with a trusted certificate.There are three transport protocols over which the client can connect to the server:RPC-HTTP ( bad )HTTP ( better )HTTP + UDP ( excellent )By server we mean a working machine, by a client - home.The first thing to start with is to turn “bad” into “excellent”.
I want to share some tips on setting up remote connection to workstations via RDP. I'll tell you how to upgrade the ancient RPC-HTTP to UDP, praise and scold Windows 10 and AVC, I will figure out a solution to several typical problems.We believe that Remote Desktop Gateway (RDGW) is used for connection, and workstations act as servers. Using RDGW is very convenient because the gateway becomes a common entry point for all clients. This makes it possible to better control access, keep records of connections and their duration. Even if the VPN allows you to connect to working machines directly, this is not the best option.RDGW is quick, easy to configure, and Let's Encrypt and win-acme easily solve the problem with a trusted certificate.There are three transport protocols over which the client can connect to the server:RPC-HTTP ( bad )HTTP ( better )HTTP + UDP ( excellent )By server we mean a working machine, by a client - home.The first thing to start with is to turn “bad” into “excellent”.Upgrade RPC-HTTP to HTTP
Connection to a session using RPC-HTTP is easy to determine by the appearance of the connection strip. There is no connection quality icon (about it below), which means we are using the old RPC wrapped in TLS - this is very slow. The point, of course, is not only in the wrapper - the protocol itself changes with each release of the OS, codecs, image packing algorithms change. The fresher the protocol, the better.What to do?
There is no connection quality icon (about it below), which means we are using the old RPC wrapped in TLS - this is very slow. The point, of course, is not only in the wrapper - the protocol itself changes with each release of the OS, codecs, image packing algorithms change. The fresher the protocol, the better.What to do?Windows XP or Vista
In XP, you can raise the protocol from 5.1 to 7. The windowsxp-kb969084-x86.exe hotfix.In Vista, from 6 to 7. The hotfix has the same number, the windows6.0-kb969084-x64.msu or Windows6.0-KB969084-x86 files .msuBut RDP 7 does not work over HTTP and UDP. Only upgrade the client and server to Windows 7 and later will help.Windows 7First you need to upgrade the protocol to RDP 8.1, and then enable it. Support is added by updates that are grouped into a single download package:www.microsoft.com/en-US/download/details.aspx?id=40986Windows6.1-KB2574819-v2-x64.msuwindows6.1-kb2592687-x64.msuWindows6.1-KB2830477-x64.msuWindows6.1-KB2857650-x64.msuWindows6.1-KB2913751-x64.msu (replaced by kb2923545)windows6.1-kb2923545-x64.msuSo you get both the fresh mstsc.exe client and RDP 8.1 support for the server side of the OS.It was: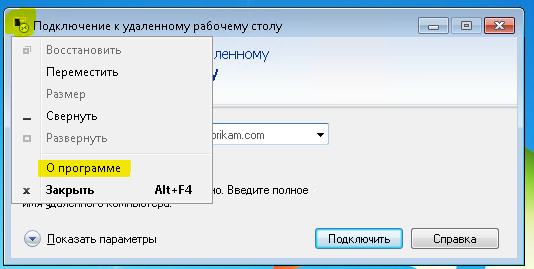
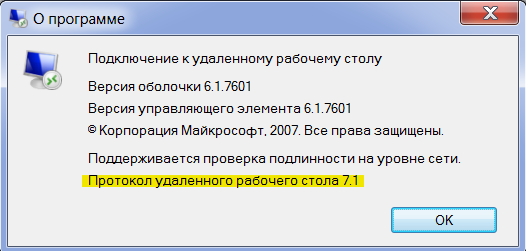 It became:
It became: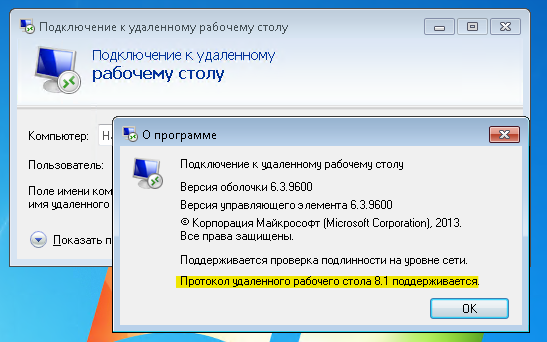 After that, the protocol must be turned on with the registry key (for this you can use the adm template bundled with Windows 7).
After that, the protocol must be turned on with the registry key (for this you can use the adm template bundled with Windows 7).[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services]
"fServerEnableRDP8"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows NT\Terminal Services]
"fServerEnableRDP8"=dword:00000001
Enable UDP transport support in Group Policy. We reboot the server with Windows 7. The same case when you may need to reboot twice - the value in the registry must be set before RDP is turned on, and Group Policy is applied later.If everything worked out, then when you connect to the server, a connection quality icon (like in a phone for a mobile network) will appear in the session bar:
We reboot the server with Windows 7. The same case when you may need to reboot twice - the value in the registry must be set before RDP is turned on, and Group Policy is applied later.If everything worked out, then when you connect to the server, a connection quality icon (like in a phone for a mobile network) will appear in the session bar: Windows 8 and newer Theprotocol works out of the box.
Windows 8 and newer Theprotocol works out of the box.Upgrade HTTP to HTTP + UDP
If your network is not prone to packet loss, UDP dramatically (for CAD - drastically) improves server responsiveness by using FEC to reduce retransmission, as well as switching packet delivery confirmation from the TCP / IP system stack to the RDP-UDP protocol level.One main control session via HTTP is connected from each client (a keyboard / mouse is also transmitted in this channel), plus one or more UDP sessions to transmit a picture or other virtual channels.We will only touch the tip of the iceberg. There are 3 different versions of the RDP-UDP protocol. In addition, UDP itself can operate in two modes: UDP-R (reliable) and UDP-L (lossy). Nothing just happens with Microsoft. But since nothing depends on us here, just keep in mind - the newer the operating system, the topic uses a more modern protocol.Outside, RDP-UDP is wrapped in Datagram Transport Layer Security (DTLS) RFC4347, as you can see by opening Wireshark.More details in the documents:[MS-RDPEMT]: Remote Desktop Protocol: Multitransport Extension[MS-RDPEUDP]: Remote Desktop Protocol: UDP Transport Extension[MS-RDPEUDP2]: Remote Desktop Protocol: UDP Transport Extension Version 2Where wrong, correct you are welcome.What do you need to enable UDP?RDP-UDP is supported starting from RDP 8.The udp / 3389 port must be open on the client. If you closed it with a local firewall, ACL on the switch or an external firewall - the port must be opened.For the Remote Desktop Gateway server to the tcp / 443 port, open udp / 3391.The port can be changed, here is how it is configured: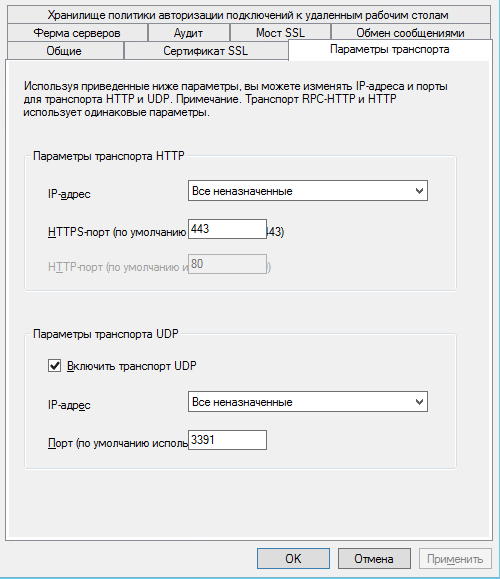 For Windows 7, NLA (Network Level Authentication) must be enabled.
For Windows 7, NLA (Network Level Authentication) must be enabled. Can be enabled in Group Policy
Can be enabled in Group Policy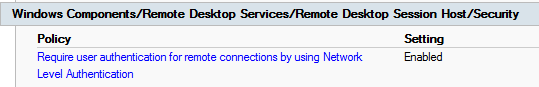 or through the registry
or through the registry[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp]
"SecurityLayer"=dword:00000001
What is the connection is not clear. But without NLA on 7-ke does not work, on more recent releases of NLA for work UDP is not required.After establishing a session over HTTP, the client and server try to negotiate a UDP connection. If there is packet loss or delay, then the UDP session will not start. The exact UDP negotiation failure algorithm is not fully understood.If everything is configured, then after connecting, click on the link quality button. The window will indicate that UDP is negotiated.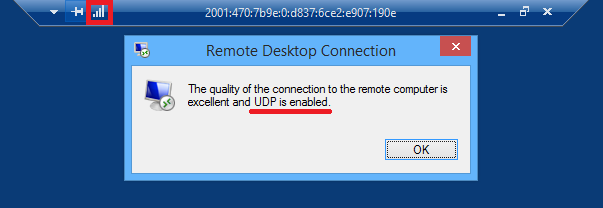 On the gateway, it looks like this:
On the gateway, it looks like this: Windows 10If you have Windows 10 both on the server and on the client, then this is the fastest and most problem-free option. Microsoft is actively finalizing RDP, and in the latest releases 10 you can count on a good speed. Colleagues could not detect the difference between Citrix and Windows 10 RDP in AutoCAD speed.There is a good article about the evolution of AVC-based RDP codecs in Windows 10Remote Desktop Protocol (RDP) 10 AVC / H.264 improvements in Windows 10 and Windows Server 2016 Technical PreviewMatching AVC with hardware encoding can be seen in the event log (see the article above for more details) ):
Windows 10If you have Windows 10 both on the server and on the client, then this is the fastest and most problem-free option. Microsoft is actively finalizing RDP, and in the latest releases 10 you can count on a good speed. Colleagues could not detect the difference between Citrix and Windows 10 RDP in AutoCAD speed.There is a good article about the evolution of AVC-based RDP codecs in Windows 10Remote Desktop Protocol (RDP) 10 AVC / H.264 improvements in Windows 10 and Windows Server 2016 Technical PreviewMatching AVC with hardware encoding can be seen in the event log (see the article above for more details) ):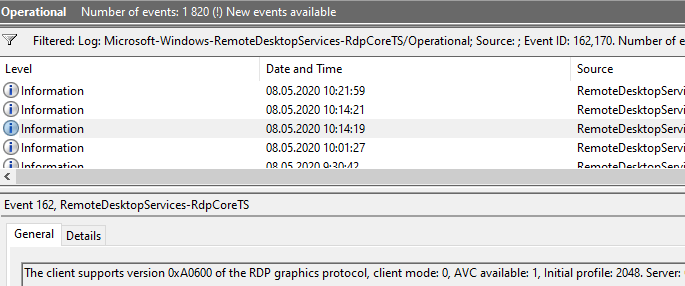
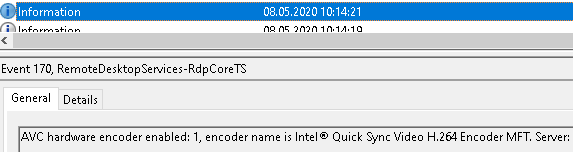 I note only that there is still a distortion problem even with h.264 4: 4: 4. It immediately catches your eye if you work in PowerShell ISE - the error text is displayed with unpleasant distortion. Moreover, everything is fine in the screenshot and in the photo. Magic.Also an indirect sign of the work of AVC are from time to time appearing green squares in the corners.AVC and hardware coding in fresh builds should work out of the box, but group policy is never superfluous:
I note only that there is still a distortion problem even with h.264 4: 4: 4. It immediately catches your eye if you work in PowerShell ISE - the error text is displayed with unpleasant distortion. Moreover, everything is fine in the screenshot and in the photo. Magic.Also an indirect sign of the work of AVC are from time to time appearing green squares in the corners.AVC and hardware coding in fresh builds should work out of the box, but group policy is never superfluous: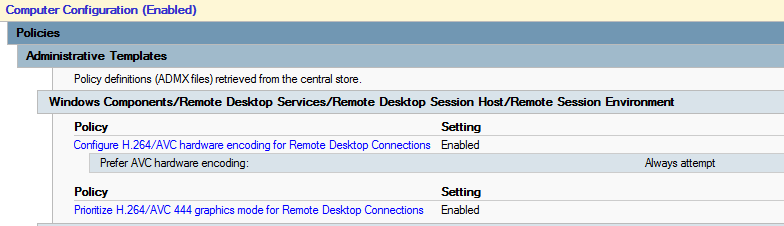 Given that AVC is hardware-encoded with a video card, updating video drivers is a good idea.
Given that AVC is hardware-encoded with a video card, updating video drivers is a good idea.About problems
XP and VistaIf the problem occurs on Windows XP or Vista, try updating the protocol to version 7 first (wrote at the beginning of the article). Be sure to enable CredSSP support. Microsoft has already deleted articles on the site, but the Internet remembers .If it doesn’t help, “the doctor speaks to the morgue, then to the morgue.” What the operating system has experienced over the past 15 years is better not to even think about it.NLASometimes it helps to disable NLA on the server. It did not work out the cause, the home cars are all different.NTLMSome clients attempt to log in using NTLMv1. The reasons are different, but you can fix it on the client like this:[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa]
"LmCompatibilityLevel"=dword:00000003
Reboot is required.If you are young and boldly afraid of nothing, then there is a more radical solution - disabling Channel Binding on the Remote Desktop GatewayHKLM\Software\Microsoft\Windows NT\CurrentVersion\TerminalServerGateway\Config\Core
Type: REG_DWORD
Name: EnforceChannelBinding
Value: 0 (Decimal)
You don’t have to do this. But we did. :-) For a client who insisted (no wrong, Insisted) that NTLMv1 on workstations he needed. I don’t know, maybe there servers on NT4 without SP are still in operation.Disabling RDP 8+ in Windows 10If all else fails and the ideas run out, you can use the undocumented key to downgrade the RDP protocol to version 7.[HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client]
"RDGClientTransport"=dword:00000001
I didn’t do it myself, and I don’t advise you. But to someone, they write that it helps.DrWebDr.Web SpIDerGate component may prohibit connection. In this case, an error is returned: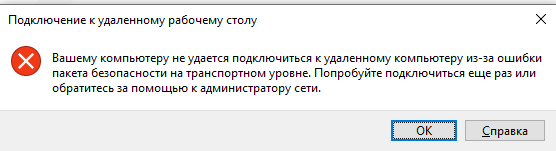 In Dr.Web statistics there will be an entry:
In Dr.Web statistics there will be an entry: In the comments on this article, a Dr.Web employee contacted me and our problem was resolved in the next update of the anti-virus databases.If you have the same error, it is best to contact support.As a temporary solution, you can add the URL of your RDGW to the exceptions:
In the comments on this article, a Dr.Web employee contacted me and our problem was resolved in the next update of the anti-virus databases.If you have the same error, it is best to contact support.As a temporary solution, you can add the URL of your RDGW to the exceptions: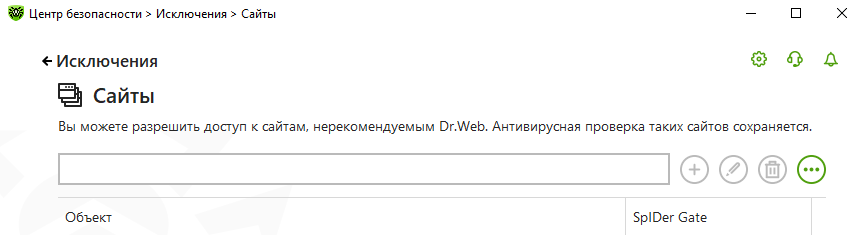 And only if it did not help to disable the SpIDer Gate component completely .System proxy Imet a decommissioned computer from some company where a local TMG was registered as a system proxy and the connection to RDGW did not work. This can be fixed like this:
And only if it did not help to disable the SpIDer Gate component completely .System proxy Imet a decommissioned computer from some company where a local TMG was registered as a system proxy and the connection to RDGW did not work. This can be fixed like this:netsh winhttp show proxy && netsh winhttp reset proxy
Switching keyboard layoutsSometimes extra layouts come. You can disable the layout forwarding from the client[HKLM\System\CurrentControlSet\Control\Keyboard Layout]
"IgnoreRemoteKeyboardLayout"=dword:00000001
DPI problemsScaling comes from the client machine, and if it costs 125% on a home laptop, it will be the same on a working machine. On servers, this can be turned off, but on workstations I could not find how. But the Windows 10 app store has a “modern” client .You can configure DPI in it: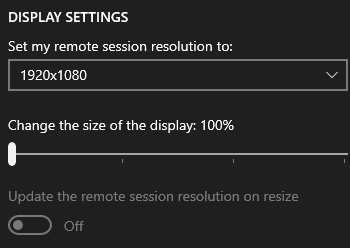
How to monitor a gateway with RDGW
There is a performance counter “TS Gateway \ Current Connections”, which is a bit buggy if there are no connections or the server has not rebooted for a long time. It shows exactly the number of connections, but as we remember, for HTTP + UDP there are at least two, and maybe more. Therefore, this is not a completely objective indicator of the number of employee connections.There is a WMI class Win32_TSGatewayConnection. Its contents correspond to what you see in the Monitoring section of the Remote Desktop Gateway.With it, the number of connections can be calculated more precisely:Get-WmiObject -class "Win32_TSGatewayConnection" -namespace "root\cimv2\TerminalServices"
|?{$_.transportprotocol -ne 2}|select username,connectedresource|sort username|Get-Unique -AsString| measure|select -ExpandProperty count
Just for fun there is a Remote Display Analyzer utility . The free version did not show me anything useful, but suddenly it will come in handy for someone.But what about fine tuning, tuning a few dozen session parameters?The Pareto principle is appropriate here: 20% of the efforts yield 80% of the result. If you are ready to invest your time in the remaining 20% of the result - excellent. Just keep in mind that when you read an article about setting up a protocol in Windows 7, you don’t know what protocol the author wrote about - 7, 8 or 8.1. When you read about Windows 10 without specifying a release, the problems are the same. For example, they write that in fresh builds of Windows 10, the AVC / h.264 codec has changed to RDPGFX_CODECID_AVC444 V2 , and in Windows Server 2016, RDPGFX_CODECID_AVC444 remains.Of all these tips, we use only two settings:- 16 bit color, you can read about it in the article MS RDP Performance / Bandwidth Usage
- Disabling font smoothing font smoothing: i: 0 in the article above or Performance Tuning Remote Desktop Session Hosts
I doubt that they give any tangible result.So we have come to the end of the article. I wanted to be shorter, but it turned out as always. I am glad if these tips help someone save time or improve the configuration of their infrastructure.