It is believed that 80% of emails in the world are spam. That is, e-mail messages that the recipient does not need at all (and this is sad). But, as if this weren’t enough, in the middle of spam there are often letters sent with malicious purposes: for example, to steal or delete data, or to extort.KDPV: As we know, in order for a letter to really harm computer systems, just delivering the letter to the recipient in most cases is not enough. Requires an “opponent prone to cooperation”, i.e. the user must independently perform actions that will lead to the execution of the intent of the attacker.Typically, such an action is to “open” the file attachment to the letter, that is, manually start processing the file with the corresponding handler program inside the user's operating system.Even more sadly, the assistant opponent is a very common bird, and our attacker spammer may well count on him.In short, our accountant opens an account, and there is not even an account at all, but a virus.Malicious letters, of course, have important differences. But hoping for user attention and awareness is a bad idea. Even bizarre concerts on the theme “do not open such a thing” with a salute and a solo vocal performance by the general (composition “Polymers”) are erased from the memory of an office worker over time.Of course, well-tuned systems will protect us from most of these attacks. But the key word is “from the majority”. No one will give a 100% guarantee; and if it comes to the user, then strengthening it, as one of the weakest places in the systems, is a good thing.In computer crime, technology and social engineering go hand in hand. The attacker realizes that it is difficult to pretend to whom the user trusts unconditionally, and therefore is forced to use other tactics: intimidation, coercion, imitate recognized authorities and / or use the corresponding false names - for example, send letters on behalf of government bodies and large companies.And, as the ancients teach us: if we cannot win, we must lead. Indeed, what are we worse than spammers? Yes, we are much better! Yes, and we have more opportunities. And the task itself will require the most minimal programming skills and will practically not affect existing systems.
As we know, in order for a letter to really harm computer systems, just delivering the letter to the recipient in most cases is not enough. Requires an “opponent prone to cooperation”, i.e. the user must independently perform actions that will lead to the execution of the intent of the attacker.Typically, such an action is to “open” the file attachment to the letter, that is, manually start processing the file with the corresponding handler program inside the user's operating system.Even more sadly, the assistant opponent is a very common bird, and our attacker spammer may well count on him.In short, our accountant opens an account, and there is not even an account at all, but a virus.Malicious letters, of course, have important differences. But hoping for user attention and awareness is a bad idea. Even bizarre concerts on the theme “do not open such a thing” with a salute and a solo vocal performance by the general (composition “Polymers”) are erased from the memory of an office worker over time.Of course, well-tuned systems will protect us from most of these attacks. But the key word is “from the majority”. No one will give a 100% guarantee; and if it comes to the user, then strengthening it, as one of the weakest places in the systems, is a good thing.In computer crime, technology and social engineering go hand in hand. The attacker realizes that it is difficult to pretend to whom the user trusts unconditionally, and therefore is forced to use other tactics: intimidation, coercion, imitate recognized authorities and / or use the corresponding false names - for example, send letters on behalf of government bodies and large companies.And, as the ancients teach us: if we cannot win, we must lead. Indeed, what are we worse than spammers? Yes, we are much better! Yes, and we have more opportunities. And the task itself will require the most minimal programming skills and will practically not affect existing systems.Disclaimer: author is not a spammer, spammer is not an author. The author is solely and exclusively on the good side.
The task is very simple:we will send our users letters similar to malicious ones. In the attachments to these letters we will attach documents where in capital letters we write “DO NOT OPEN DOCUMENTS FROM SUCH LETTERS. Be careful and careful. "Thus, our problem has the following conditions :Condition 1 . Letters should be different . If we send the same letter to everyone and every time, then this will not differ from ordinary reminders at meetings, to which users have immunity. We must stimulate the user with the system responsible for training. The following conditions follow from this:Condition 2 . Letters should be like real ones. It is possible, but inefficient, to send letters from Meat-Company LLP or Barack Obama. It makes sense to use the really existing (and different!) Names of organizations and bodies;Condition 3 . It is also important that the letters look a little strange . They should be somewhat dubious in order to arouse suspicion and the user and activate the learning system in the brain;Condition 4 . And with all this, letters should attract attention and provoke . Well, everything is simple, we don’t even need to invent anything: spammers have already done everything for us. “Penalties”, “Judicial decisions” and even just “Documents” in attachments, “Forfeits”, “Recalculations”, “Penalties” in the subject and many words “Urgent”, “Immediately”, “Obligatory”, “Pay” in the text - and it's in the hat.To implement this magic set you will need minimal programming skills and a boring evening. The author used Python 3 (because it was necessary to practice) and JS (to collect data directly from the browser console). But most of the code is easily implemented on native OS tools (bash, cmd), only with the encodings are tormented.In fairness, it should be noted that the idea itself does not belong to the author, but was spied on by one large international company. Nevertheless, the idea is so on the surface that, barely hearing, the author, shouting “why haven’t I done this before,” rushed to implement it.So, first of all, we need the parts from which we will compose the letter. Let's start with the From field - who will threaten our fearful users. Well, who: of course, banks, tax inspectorates, courts and all sorts of weird LLCs. At the same time, you can add templates for future auto-substitution, like PAO CmpNmF. See from.txtNow we need, in fact, the names. LLC Chamomile and Vector, as well as the endlessly repeating of some “Moscow court” is unlikely to cause a response in the souls.Fortunately, the Internet provides us with amazing opportunities to receive information. For example, a list of the current courts of the Russian Federation can be obtained with a simple JavaScript command directly in the browser console code like:for (let el of document.getElementById("mw-content-text").querySelectorAll("li")) {console.log(el.innerText;)}
So you can quickly very quickly gain an excellent base for our tasks (especially since the author has already done this for you :)). We will save in Plain text, the database for such a task is overkill. The project uses UTF-8 encoding with BOM, in case the most specific characters are used. See txt files with appropriate names.Next, you need to generate the correct (from the standard standard, but not necessarily existing) email address of the sender so that our letter is correctly displayed and correctly forwarded. For some of the titles, the author used fixed domains, for some, auto-generation from the name using a transliteration library, something like Vector LLC -> warning@ooovektor.ru. The name of the box is taken from the list in the code and is also intended to inspire awe: “vzyskanie”, “shtraf”, “dolg”, 'alarm'and other "zapros".Now - the subject of the letter.The subject must necessarily attract attention, otherwise the letter will go unnoticed. Give free rein to your internal scarecrow of accountants, and everything will turn out: “Closing account (s) ( CmpNm)”, “Chief accountant ( CmpNm)”, “Requirement (for CmpNm)” “Immediately pay (!!!)” and other pranks.See subj.txt. Add to taste, mix, do not shake.The text of the letter should be somewhat strange. We have already attracted the attention of the user, now our task is to raise suspicion. Therefore, trying at this point is completely useless. Let us take threatening phrases from spammers and we will combine them arbitrarily, 100% certainty will only hinder us. It will turn out nonsense like:() ( "")
See msg.txt. Additions are welcome.And finally, the attachment. The project currently provides for 3 types of investments: pdf, doc, docx. Files are copied from the samples without changing the content, the attachment file is given a name from the list (“Resolution”, “Judgment”, etc., see flnms.txt). For the first two types, the size is randomly generated by adding zeros to the end of the file. This does not work with docx (although after the recovery procedure, the Word file opens; LibreOffice, for example, opens the docx files without abuse, into which third-party files are added via the archiver interface).And we get such a miracle: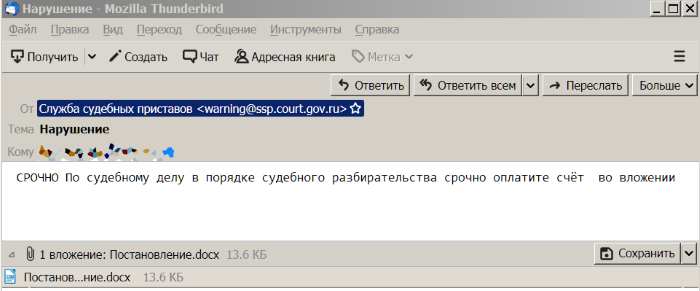 You can send:
You can send:gen_msg.py buh@oootest.ru
The code, of course, on the githubActually, that's all. Cases for an hour, and the benefits ... But the benefits will be. For the theory is dry, but the tree of life is lushly green - explanations do not reach, reminders are forgotten, and people learn skills only in practice. And we’d rather be better teachers than to restore everything from backups, right?