Continuing the series of articles on organizing Remote-Access VPN access, I cannot but share the interesting experience of deploying a highly secure VPN configuration . A non-trivial task was thrown by one customer (there are inventors in Russian villages), but Challenge Accepted and creatively implemented. The result is an interesting concept with the following characteristics:
- Several protection factors against substitution of the terminal device (with tight binding to the user);
- Conformity assessment of the user's PC to the designated UDID of the authorized PC in the authentication database;
- With an MFA using the UDID of the PC from the certificate for secondary authentication through Cisco DUO (You can screw any SAML / Radius compatible) ;
- Multi-factor authentication:
- User certificate with field verification and secondary authentication for one of them;
- Login (immutable, taken from the certificate) and password;
- Assessing the status of the connecting host (Posture)
Used components of the solution:
- Cisco ASA (VPN Gateway);
- Cisco ISE (Authentication / Authorization / Accounting, Status Assessment, CA);
- Cisco DUO (Multifactor Authentication) (You can screw any SAML / Radius compatible) ;
- Cisco AnyConnect (Multipurpose Agent for Workstations and Mobile OS);
Let's start with customer requirements:
- The user must authenticate with the Login / Password to be able to download the AnyConnect client from the VPN gateway, all necessary AnyConnect modules should be automatically installed in accordance with the user policy;
- ( , – ), ( ).
- , , /, , Subject Name (CN) .
- , , , - . ( )
- ( ) ():
- Youtube (5 ).
-.
AnyConnect:
( ASDM) VPN Load-Balancing . , :
VPN :
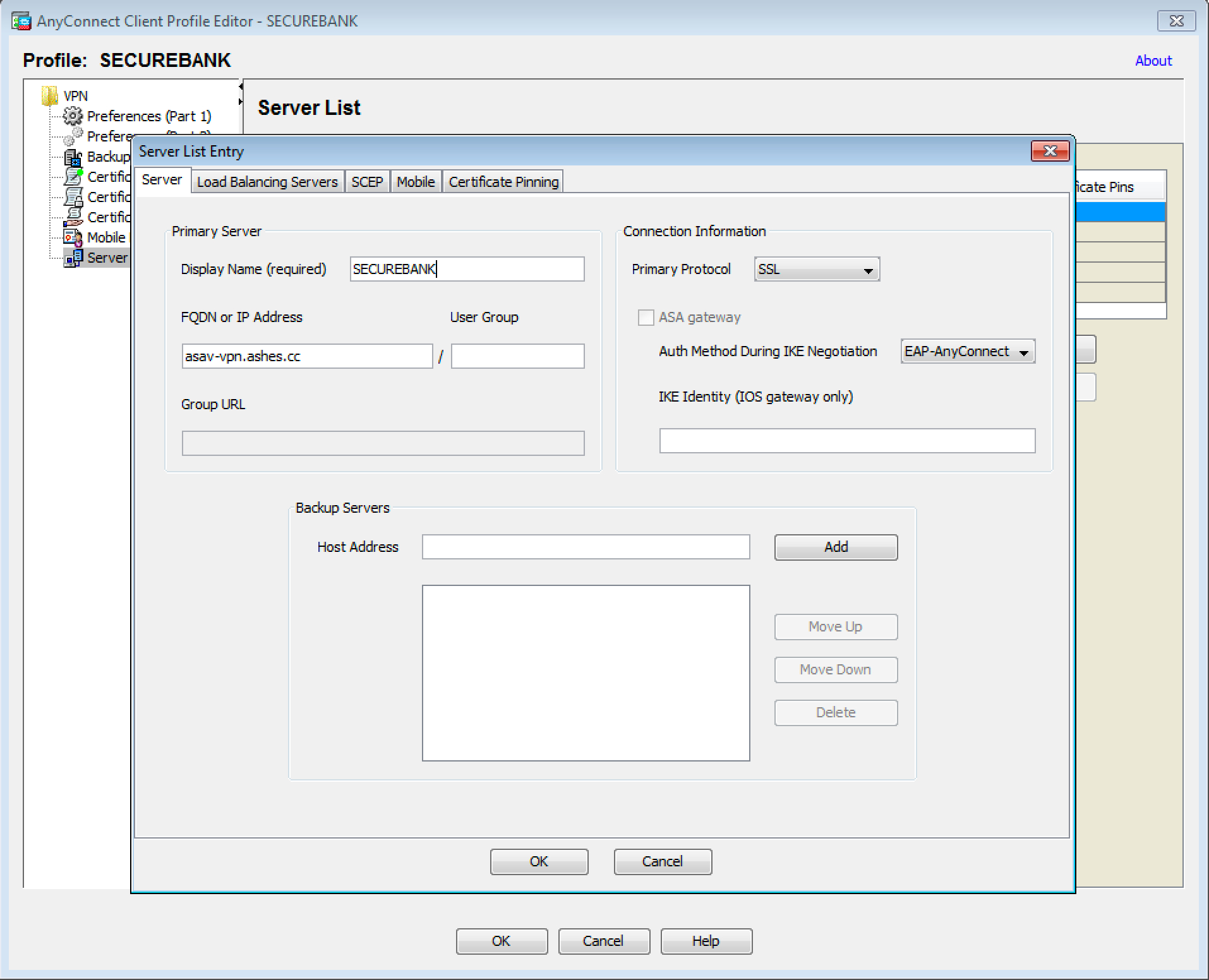
, , , , Initials (I), UDID ( , Cisco AnyConnect ).
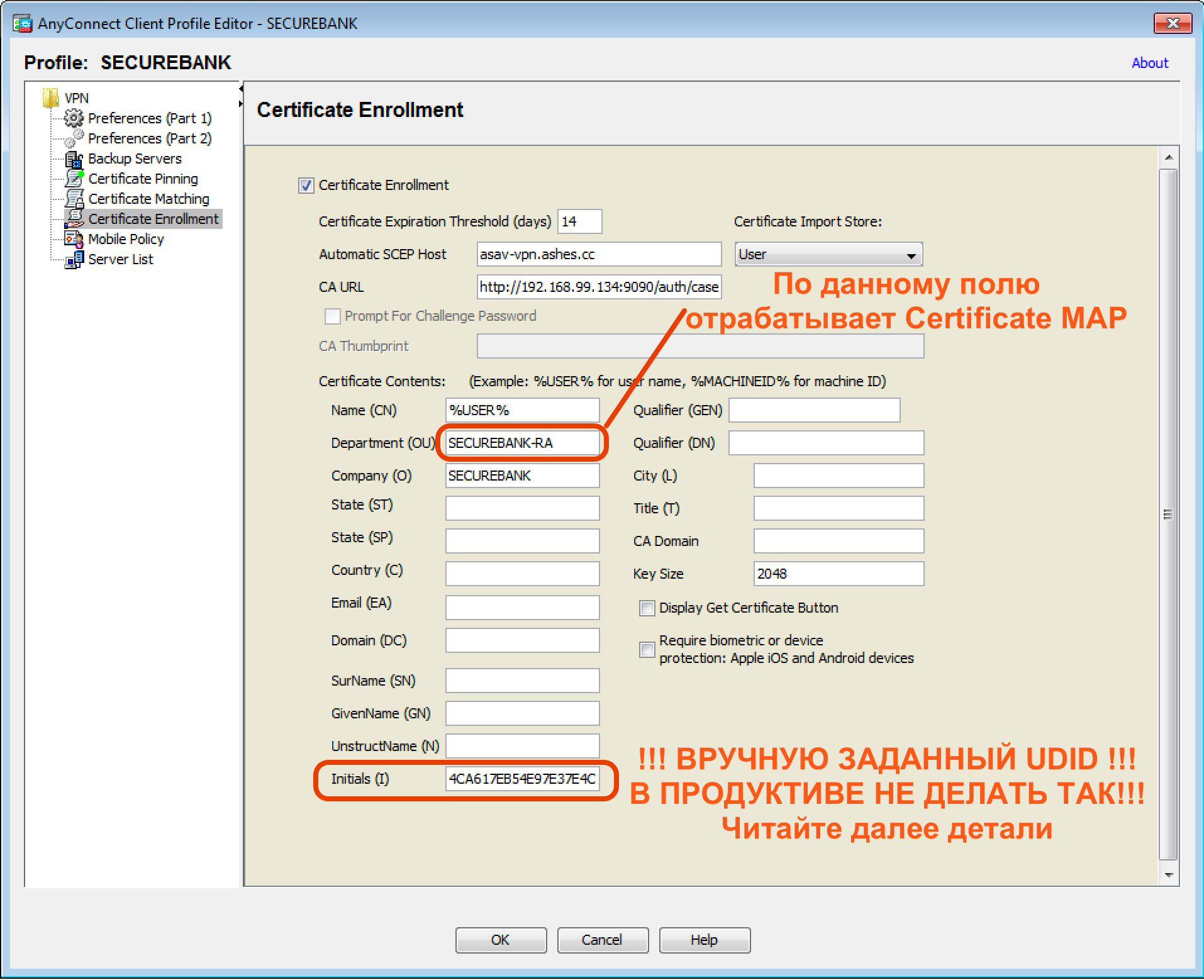
, , UDID Initials AnyConnect. , UDID , UDID . AnyConnect UDID , %USER%.
( ) UDID , - . ( =) ).
. Anyonnect UDID , , – . , UDID AnyConnect:
- Windows — SHA-256 DigitalProductID Machine SID
- OSX — SHA-256 PlatformUUID
- Linux — SHA-256 UUID root .
- Apple iOS — SHA-256 PlatformUUID
- Android –
Windows, UDID UDID, , AD ( Multiple Certificate).
Cisco ASA:
TrustPoint ISE CA , . Key-Chain , VPN Load-Balancing .
crypto ca trustpoint ISE-CA
enrollment terminal
crl configure
Tunnel-Group , . AnyConnect, . SECUREBANK-RA, SECURE-BANK-VPN, AnyConnect.
tunnel-group-map enable rules
!
crypto ca certificate map OU-Map 6
subject-name attr ou eq securebank-ra
!
webvpn
anyconnect profiles SECUREBANK disk0:/securebank.xml
certificate-group-map OU-Map 6 SECURE-BANK-VPN
!
. ISE DUO (Radius Proxy) MFA.
! CISCO ISE
aaa-server ISE protocol radius
authorize-only
interim-accounting-update periodic 24
dynamic-authorization
aaa-server ISE (inside) host 192.168.99.134
key *****
!
! DUO RADIUS PROXY
aaa-server DUO protocol radius
aaa-server DUO (inside) host 192.168.99.136
timeout 60
key *****
authentication-port 1812
accounting-port 1813
no mschapv2-capable
!
:
DefaultWEBVPNGroup AnyConnect VPN SCEP-Proxy ASA, , AC-Download, AnyConnect ( ..). ISE Posture Module.
SECURE-BANK-VPN , Certificate Map, . :
- secondary-authentication-server-group DUO # DUO (Radius Proxy)
- username-from-certificate CN # CN
- secondary-username-from-certificate I # DUO , Initials (I) .
- pre-fill-username client #
- secondary-pre-fill-username client hide use-common-password push # / DUO (sms/push/phone) –
!
access-list posture-redirect extended permit tcp any host 72.163.1.80
access-list posture-redirect extended deny ip any any
!
access-list VPN-Filter extended permit ip any any
!
ip local pool vpn-pool 192.168.100.33-192.168.100.63 mask 255.255.255.224
!
group-policy SECURE-BANK-VPN internal
group-policy SECURE-BANK-VPN attributes
dns-server value 192.168.99.155 192.168.99.130
vpn-filter value VPN-Filter
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelall
default-domain value ashes.cc
address-pools value vpn-pool
webvpn
anyconnect ssl dtls enable
anyconnect mtu 1300
anyconnect keep-installer installed
anyconnect ssl keepalive 20
anyconnect ssl rekey time none
anyconnect ssl rekey method ssl
anyconnect dpd-interval client 30
anyconnect dpd-interval gateway 30
anyconnect ssl compression lzs
anyconnect dtls compression lzs
anyconnect modules value iseposture
anyconnect profiles value SECUREBANK type user
!
group-policy AC-DOWNLOAD internal
group-policy AC-DOWNLOAD attributes
dns-server value 192.168.99.155 192.168.99.130
vpn-filter value VPN-Filter
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelall
default-domain value ashes.cc
address-pools value vpn-pool
scep-forwarding-url value http://ise.ashes.cc:9090/auth/caservice/pkiclient.exe
webvpn
anyconnect ssl dtls enable
anyconnect mtu 1300
anyconnect keep-installer installed
anyconnect ssl keepalive 20
anyconnect ssl rekey time none
anyconnect ssl rekey method ssl
anyconnect dpd-interval client 30
anyconnect dpd-interval gateway 30
anyconnect ssl compression lzs
anyconnect dtls compression lzs
anyconnect modules value iseposture
anyconnect profiles value SECUREBANK type user
!
tunnel-group DefaultWEBVPNGroup general-attributes
address-pool vpn-pool
authentication-server-group ISE
accounting-server-group ISE
default-group-policy AC-DOWNLOAD
scep-enrollment enable
tunnel-group DefaultWEBVPNGroup webvpn-attributes
authentication aaa certificate
!
tunnel-group SECURE-BANK-VPN type remote-access
tunnel-group SECURE-BANK-VPN general-attributes
address-pool vpn-pool
authentication-server-group ISE
secondary-authentication-server-group DUO
accounting-server-group ISE
default-group-policy SECURE-BANK-VPN
username-from-certificate CN
secondary-username-from-certificate I
tunnel-group SECURE-BANK-VPN webvpn-attributes
authentication aaa certificate
pre-fill-username client
secondary-pre-fill-username client hide use-common-password push
group-alias SECURE-BANK-VPN enable
dns-group ASHES-DNS
!
ISE:
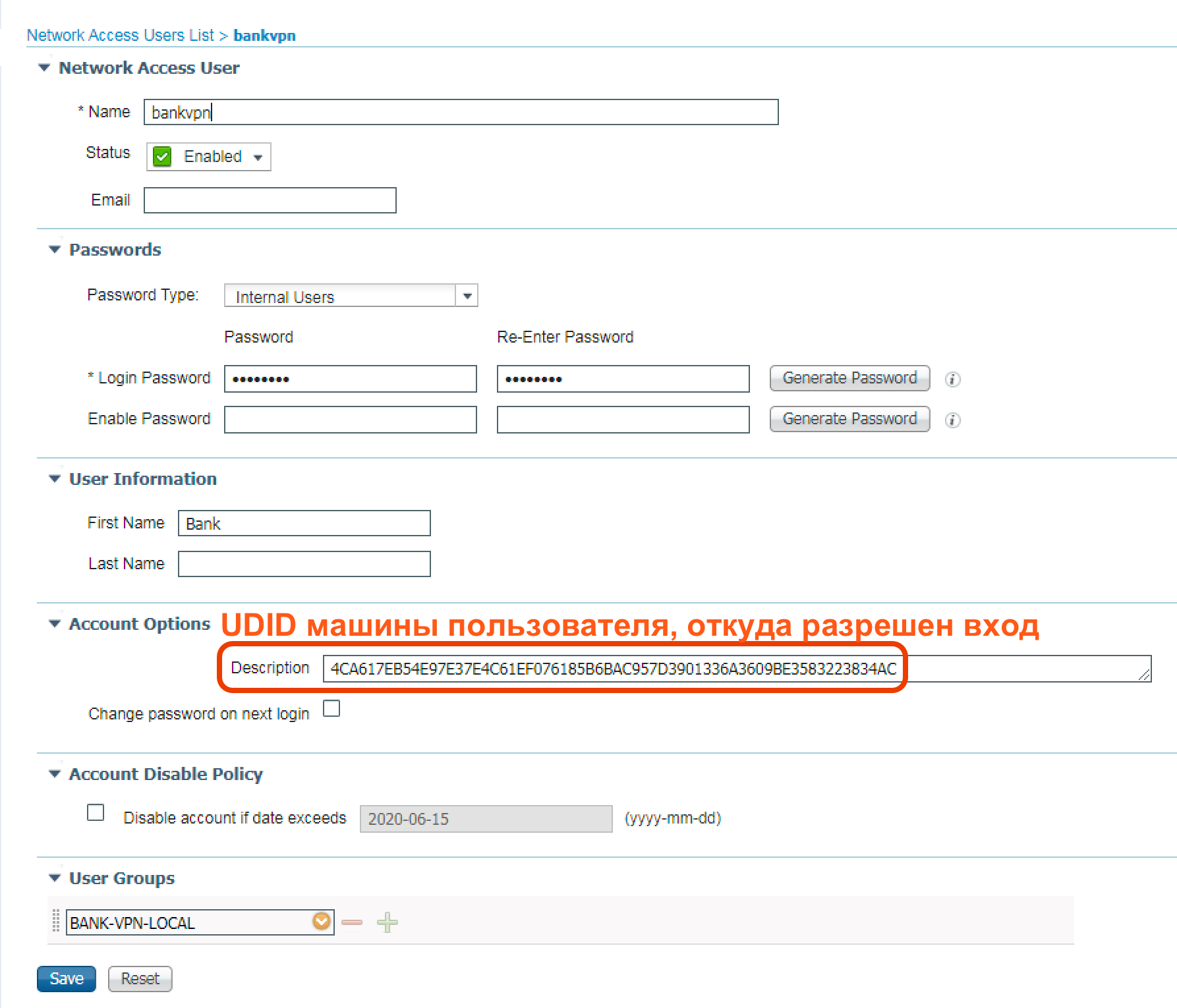
( AD/LDAP/ODBC ..), ISE description UDID VPN. ISE , , .
, :
- 1 — AnyConnect
- 2 — ( )/ + UDID
- 3 — Cisco DUO (MFA) UDID +
- 4 — :
- Compliant;
- UDID ( + ),
- Cisco DUO MFA;
- ;
- ;

UUID_VALIDATED, UDID Description , :
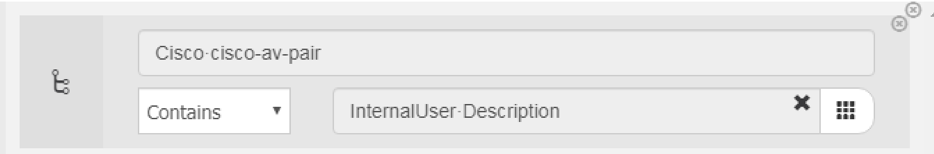
, 1,2,3 :

UDID AnyConnect ISE . , AnyConnect ACIDEX , UDID Cisco-AV-PAIR:
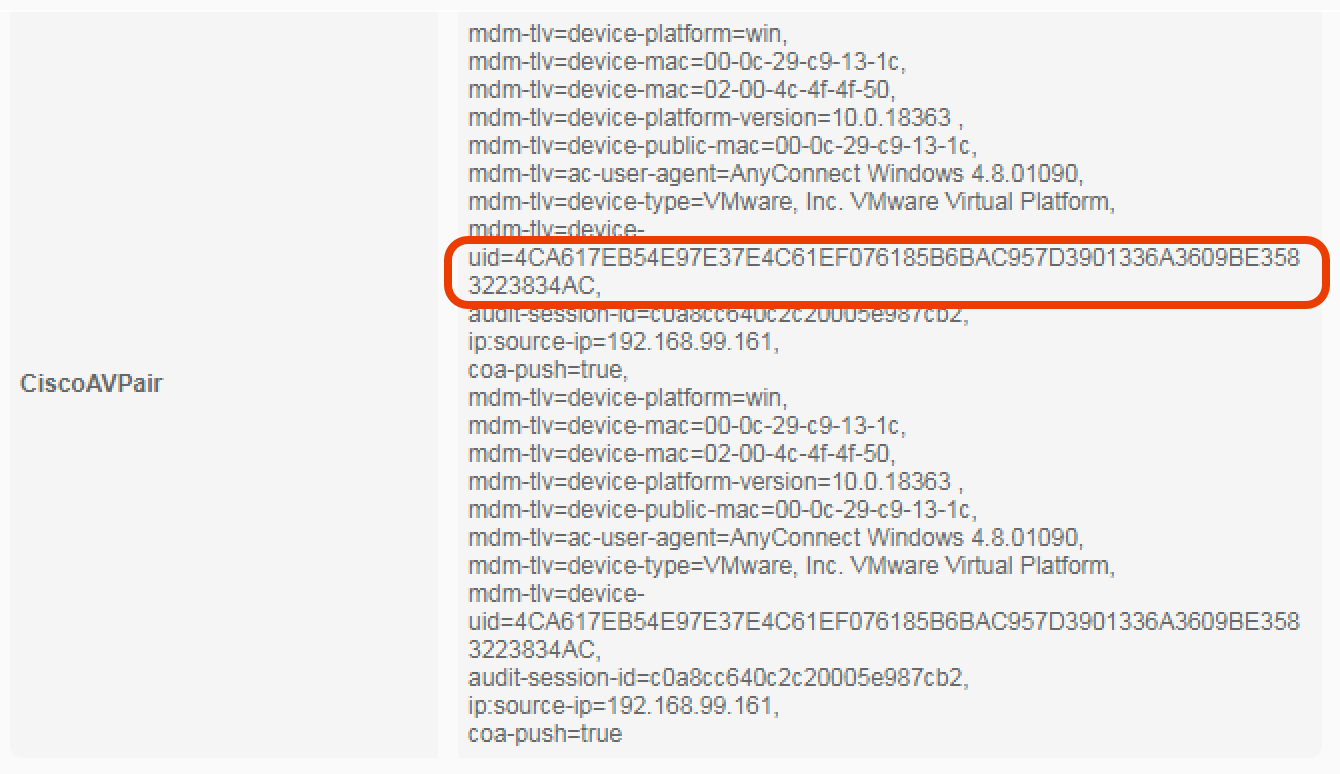
Initials (I), MFA Cisco DUO:
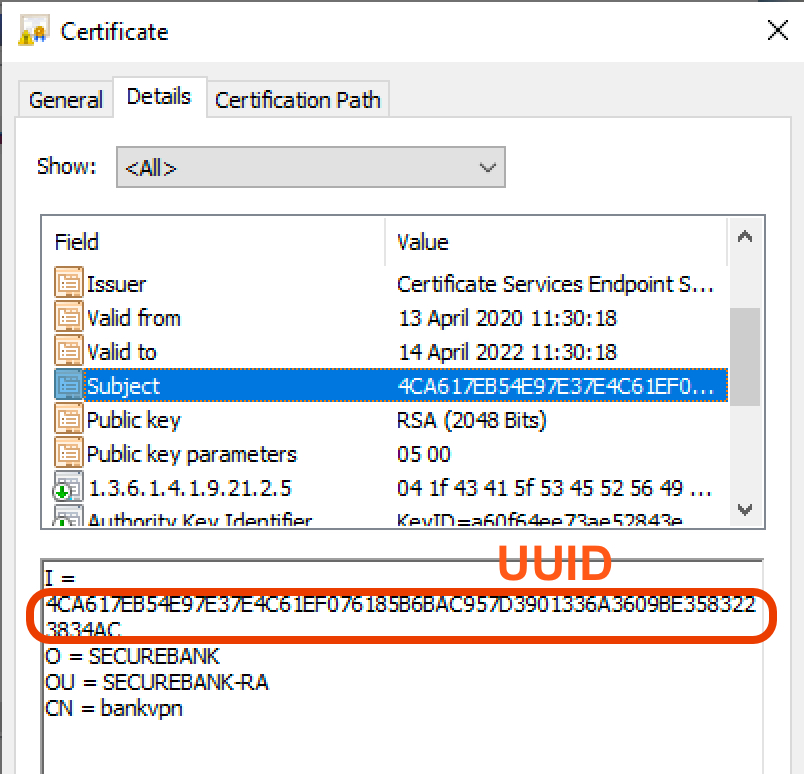
DUO Radius Proxy , UDID :
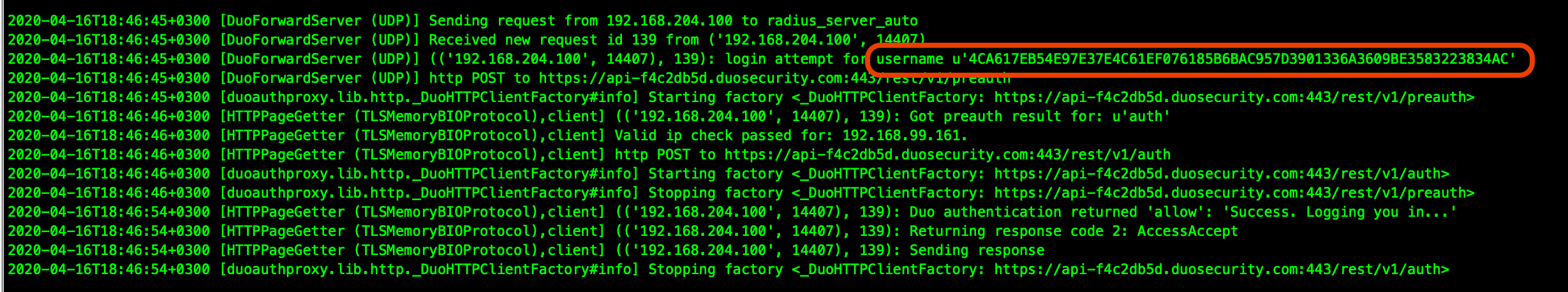
DUO :
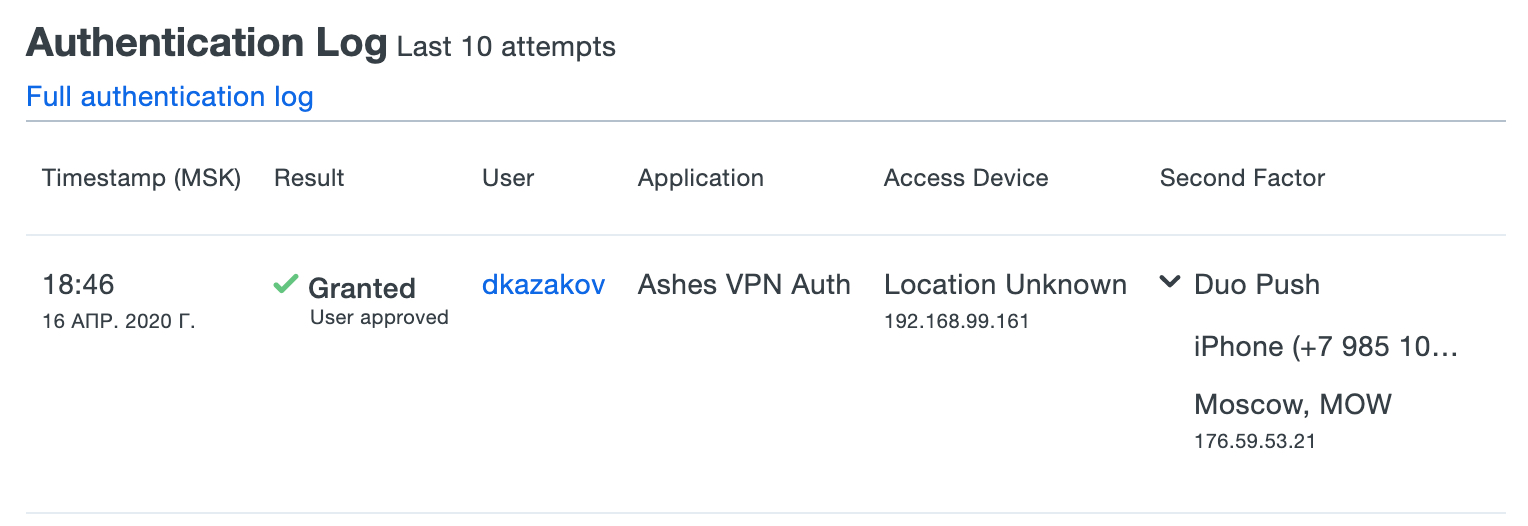
ALIAS, , UDID :
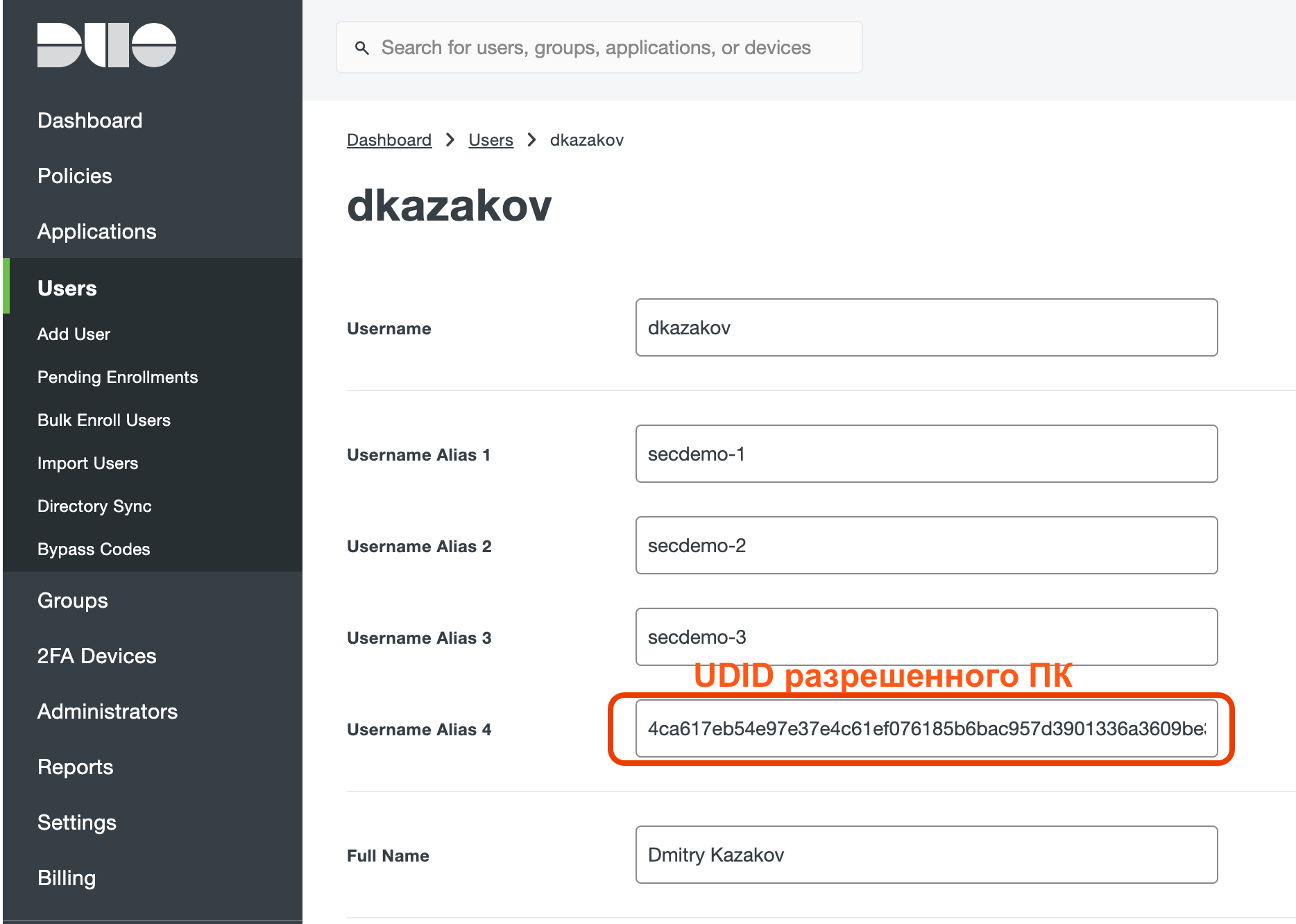
:
Cisco VPN: