 Imagine that in real life you received an envelope where the name of your old friend is written in the “Sender” field. Can you, without opening and reading the letter, say for sure - this is an envelope from your old friend or some intruder?This is the task facing mail servers - just looking at the envelope to determine if the sender is lying. To do this, the mail server refers to the mechanism that the Internet serves to confirm domain ownership - the DNS server.Previous < About ports and encryption in mail servers
Imagine that in real life you received an envelope where the name of your old friend is written in the “Sender” field. Can you, without opening and reading the letter, say for sure - this is an envelope from your old friend or some intruder?This is the task facing mail servers - just looking at the envelope to determine if the sender is lying. To do this, the mail server refers to the mechanism that the Internet serves to confirm domain ownership - the DNS server.Previous < About ports and encryption in mail servers Immediately make a reservation that by the "sender" field I do not mean the "from" field in the message itself, but the address of the sender server.
Immediately make a reservation that by the "sender" field I do not mean the "from" field in the message itself, but the address of the sender server. The mail server is very dependent on DNS. The only case when the mail server does not need a DNS server is when it is a local mail server that does not send or receive letters from other servers.
The mail server is very dependent on DNS. The only case when the mail server does not need a DNS server is when it is a local mail server that does not send or receive letters from other servers.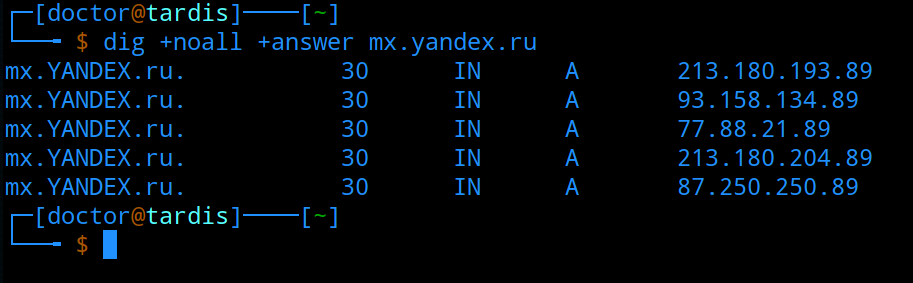 Now, let's decide on all the necessary DNS records for mail servers. Let's start with the “A” recordwhich translates the name into an IP address. By the way, A - from the word address. Common examples of names for mail servers are mx.example.org, mail.example.org, smtp.example.org. Several A records with the same name and different IP addresses will allow balancing traffic to different mail servers provided that round robin DNS is configured.
Now, let's decide on all the necessary DNS records for mail servers. Let's start with the “A” recordwhich translates the name into an IP address. By the way, A - from the word address. Common examples of names for mail servers are mx.example.org, mail.example.org, smtp.example.org. Several A records with the same name and different IP addresses will allow balancing traffic to different mail servers provided that round robin DNS is configured.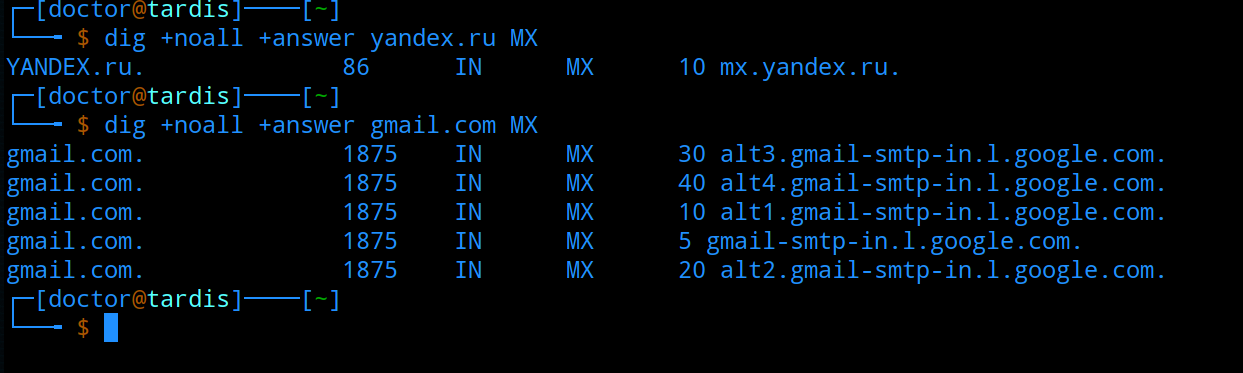 MX record- from the word e-mail messenger - it is necessary so that other mail servers can find out to which address the mail should be sent to the specified recipient domain. If you plan to use subdomains, for example, user@support.example.org, then for the subdomain you will need a separate MX record. Also, you can specify several MX records for one domain, pointing to different addresses and choosing priority. Say you want all mail to be sent to the mx1.example.org server by default, then give it priority closer to zero. The lower the priority of the server, the higher the number you assign to it. The maximum value is 65535, but usually priorities are set to 10, 20, 30, etc. Priorities can match, then either DNS balances these records, if configured on the DNS server, or the sender will use the first available server.
MX record- from the word e-mail messenger - it is necessary so that other mail servers can find out to which address the mail should be sent to the specified recipient domain. If you plan to use subdomains, for example, user@support.example.org, then for the subdomain you will need a separate MX record. Also, you can specify several MX records for one domain, pointing to different addresses and choosing priority. Say you want all mail to be sent to the mx1.example.org server by default, then give it priority closer to zero. The lower the priority of the server, the higher the number you assign to it. The maximum value is 65535, but usually priorities are set to 10, 20, 30, etc. Priorities can match, then either DNS balances these records, if configured on the DNS server, or the sender will use the first available server. PTR record is a reverse DNS record that translates an IP address into a name. The main objective of this entry for the mail server is to filter out most of the spam. This record allows you to determine the host name from which mail arrives. When receiving mail, the mail server makes two requests - to obtain a name by IP address and to obtain an IP address by the name of the sender. If the results match, then the sender server is who it claims to be. Unlike other records, such a record can only be created if you own or rent an IP address.
PTR record is a reverse DNS record that translates an IP address into a name. The main objective of this entry for the mail server is to filter out most of the spam. This record allows you to determine the host name from which mail arrives. When receiving mail, the mail server makes two requests - to obtain a name by IP address and to obtain an IP address by the name of the sender. If the results match, then the sender server is who it claims to be. Unlike other records, such a record can only be created if you own or rent an IP address. As a rule, services where you buy a domain name do not allow you to create a PTR record. If you rent VPS from cloud providers, some of them create PTR records for you. If you have your own local mail server, but the DNS provider acts as the DNS provider, then you can contact your Internet provider, which will give you an IP address so that the provider writes a PTR record for you. Without this entry, your outgoing messages are more likely to get spam on other mail servers.
As a rule, services where you buy a domain name do not allow you to create a PTR record. If you rent VPS from cloud providers, some of them create PTR records for you. If you have your own local mail server, but the DNS provider acts as the DNS provider, then you can contact your Internet provider, which will give you an IP address so that the provider writes a PTR record for you. Without this entry, your outgoing messages are more likely to get spam on other mail servers. SPF- A record that allows certain addresses to send a message from the specified domain, and says what to do if the message came from a different address. Suppose you, as a sender, declare that you only allow mail.example.org to send mail from the example.org domain. And if the message does not come from this address, but the example.org domain is specified in the sender field, then it is safe to reject this message as untrusted. In principle, the server recipients should check your SPF record and act according to what you set, but the recipient can ignore your “instructions” at will. An SPF record is needed to protect against spoofing attacks when an attacker pretends to be one of the sender's users.
SPF- A record that allows certain addresses to send a message from the specified domain, and says what to do if the message came from a different address. Suppose you, as a sender, declare that you only allow mail.example.org to send mail from the example.org domain. And if the message does not come from this address, but the example.org domain is specified in the sender field, then it is safe to reject this message as untrusted. In principle, the server recipients should check your SPF record and act according to what you set, but the recipient can ignore your “instructions” at will. An SPF record is needed to protect against spoofing attacks when an attacker pretends to be one of the sender's users.
v=spf1 -all
v=spf1 mx -all
v=spf1 a:mail.example.org ~all
When setting up an SPF record, you specify the version of SPF, and so far it is one - the first. Next, specify the addresses that are allowed to send messages from this domain. The addresses can be just an “mx” record - that is, those servers that you have listed in MX records. You can also register additional addresses using the options a - by A record, by ipv4 and ipv6 addresses, etc. After the allowed addresses, the all option is indicated for everything that did not fit your rule. You can advise the recipient to allow all messages from any addresses on your domain, prohibit, mark as inappropriate, but skip, or at the discretion of the recipient. The full syntax and all SPF options will be given as a link at the end.And although the SPF points to the addresses to whom it is allowed to send messages, there is a possibility of substitution of the message by someone in the middle. To prevent such attacks, there is another DNS entry. DKIM is a record that is used to confirm the sender using signatures that are added to each message. In short, your server adds a unique hash to outgoing messages, which can be decrypted using the public key from the corresponding DNS record. Even if someone substitutes a message, he will not be able to fake your digital signature. Thus, DKIM is also needed to protect against spoofing.But for DKIM, adding a DNS record is not enough; you also need to generate keys and configure your mail server to work with DKIM. To do this, the DKIM service rises on the mail server, and the mail service itself, before sending the message, sends messages through this service, which adds a digital signature. How to install and configure this I will consider another time, but this is full of material on the Internet.
DKIM is a record that is used to confirm the sender using signatures that are added to each message. In short, your server adds a unique hash to outgoing messages, which can be decrypted using the public key from the corresponding DNS record. Even if someone substitutes a message, he will not be able to fake your digital signature. Thus, DKIM is also needed to protect against spoofing.But for DKIM, adding a DNS record is not enough; you also need to generate keys and configure your mail server to work with DKIM. To do this, the DKIM service rises on the mail server, and the mail service itself, before sending the message, sends messages through this service, which adds a digital signature. How to install and configure this I will consider another time, but this is full of material on the Internet.
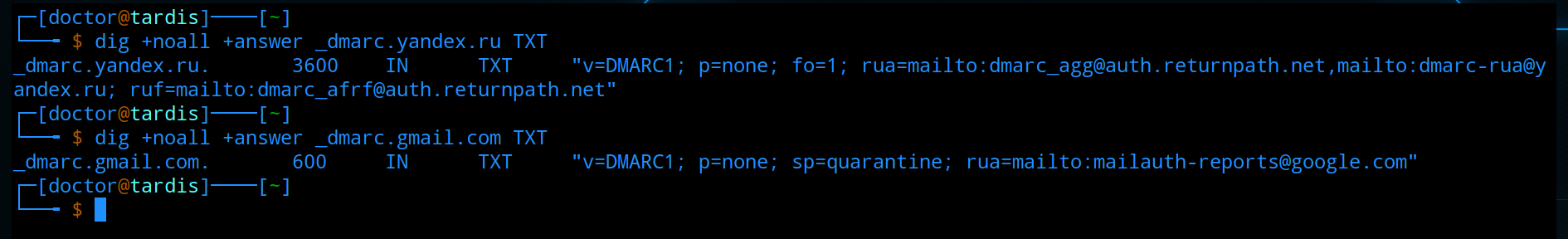 DMARC is a record that allows you to set policies based on SPF and DKIM checks. These policies, again, are needed by the recipient to know what to do with your letters.
DMARC is a record that allows you to set policies based on SPF and DKIM checks. These policies, again, are needed by the recipient to know what to do with your letters.
v=DMARC1; p=reject; pct=100; rua=mailto:admin@example.org
v=DMARC1; p=quarantine; pct=50; rua=mailto:admin@example.org
v=DMARC1; p=none; rua=mailto:admin@example.org
You can configure the recording so that the recipient ignores errors, quarantines failed messages, or rejects these messages altogether. Also, in the DMARC record, you specify the mailing address where the recipient servers will send statistics on messages from your mail servers, which will allow you to understand what is happening with outgoing messages, and also tighten the nuts slowly to prevent spoofing. Some services, say Gmail, also offer to add certain DNS records to confirm you as a domain administrator, which will allow you to better understand what is happening with messages from your domain for Gmail users. But these are special cases and vary depending on the service.
Some services, say Gmail, also offer to add certain DNS records to confirm you as a domain administrator, which will allow you to better understand what is happening with messages from your domain for Gmail users. But these are special cases and vary depending on the service. Forgot to mention. There are a couple of important tools online to check your settings.One of the most convenient tools is mail-tester . It's simple:1. Go to the site, copy the mailing address that the service gave you.2. Send a message to this address from your domain from any mailbox. It is desirable that the message is not empty, but contains some kind of text.3. Return to the site, click "Then check the rating."4. Check the result. The portal will check all possible settings, like DNS - the same SPF, DKIM and DMARC records, and will show if your server is blacklisted, etc. He will also give a recommendation if you have errors in the settings.5. If there were errors - correct and then send the message again and check the result again. If the problems were related to DNS records, make sure that your changes to the DNS are applied (for example, with the same dig command) before trying again.BUT! The service gives you only 3 free attempts per day, therefore, it is advisable to fix all the errors, and then re-check.
Forgot to mention. There are a couple of important tools online to check your settings.One of the most convenient tools is mail-tester . It's simple:1. Go to the site, copy the mailing address that the service gave you.2. Send a message to this address from your domain from any mailbox. It is desirable that the message is not empty, but contains some kind of text.3. Return to the site, click "Then check the rating."4. Check the result. The portal will check all possible settings, like DNS - the same SPF, DKIM and DMARC records, and will show if your server is blacklisted, etc. He will also give a recommendation if you have errors in the settings.5. If there were errors - correct and then send the message again and check the result again. If the problems were related to DNS records, make sure that your changes to the DNS are applied (for example, with the same dig command) before trying again.BUT! The service gives you only 3 free attempts per day, therefore, it is advisable to fix all the errors, and then re-check. Another tool - mxtoolbox. Here, basically, checking for the presence of DNS records and getting into spam lists. Also on this portal you can find many different tools for checking and there is no such restriction as in mail-tester. Although among the tools there is a check for the presence of a DKIM key, without a message from your domain mxtoolbox will not be able to confirm the correctness of the mail server settings for working with DKIM.
Another tool - mxtoolbox. Here, basically, checking for the presence of DNS records and getting into spam lists. Also on this portal you can find many different tools for checking and there is no such restriction as in mail-tester. Although among the tools there is a check for the presence of a DKIM key, without a message from your domain mxtoolbox will not be able to confirm the correctness of the mail server settings for working with DKIM. If you have configured DKIM and want to make sure that you are correct, you can send a message to the same gmail account, and then open the message in its original form and try to find the line DKIM = pass. Or use the ready-made service - dkimvalidator . The principle of operation is the same as that of mail-tester - send a message to the generated address and see the result.Thus, by setting up these DNS records, messages from your mail servers will not fall into spam (provided that you yourself do not spam), and you will help your recipients to avoid spam and spoofing attacks.Useful links:What is SPFRiddles and Myths SPFWhat Is DKIM?HowTo: DMARC
If you have configured DKIM and want to make sure that you are correct, you can send a message to the same gmail account, and then open the message in its original form and try to find the line DKIM = pass. Or use the ready-made service - dkimvalidator . The principle of operation is the same as that of mail-tester - send a message to the generated address and see the result.Thus, by setting up these DNS records, messages from your mail servers will not fall into spam (provided that you yourself do not spam), and you will help your recipients to avoid spam and spoofing attacks.Useful links:What is SPFRiddles and Myths SPFWhat Is DKIM?HowTo: DMARC