Introduction
The application came out → saw a quiet horror → started to write negative reviews → sorted by the shelves → the application was deleted (sent for revision).Hello everyone, in this article, when everything has passed, I want to tell you about the two key stages of the above.What kind of application can be read here .And about the excuses and sending for revision here .Under the cut, we’ll see with you what we saw at the very beginning of the analysis of the application and go over all the interesting points from the code. We’ll enjoy the leaky application and will not accept “look at how long we did it”.Background
It all started for me in the Telegram channel “ IT and COPM ”. I did not immediately see a post with a link to the application in the Play Market and apk's below. Only after about 30 minutes, from the number of posts in this channel, I decided to read. At that time, the guys had already decompiled the application and actively watched where the data was sent. They pulled out some endpoints, hosts, a token, started to post screenshots of pieces of code. Having applied apk's, they asked someone to publish the decompiled code on GitHub - after an hour and a half it was posted . Then I connected ...Main part
Backing
At the very beginning, I want to say that inside the application there was a token for working with the Identix.one face recognition service API . These guys work so that at first they need to load the user database with photos and data, and only then can they send photos for recognition. The token was in the application, working with the API of this service through the client, and not your backend. Thus, any user, having torn out a token, could start uploading any photos of citizens of the Russian Federation and receive information about them. Sounds wonderful. Having looked at the tariffs of this service, I realized that this is generally for CCTV cameras. For each camera you have to pay a good amount and was surprised how much the application developers had to pay for it.Going into the API documentation section it seemed interesting to me to get a loaded user base and other things. So I decided to fulfill the request and check the token. Fortunately or unfortunately, the token was disabled, which I immediately informed the owner of the IT and COPM channel via Twitter .I began my study with a back, because I was planning to find something interesting there ( sql inj , for example). We already had hosts and a link to enter the admin panel. In the admin area and went. Looking at the queries immediately it became clear that this is some kind of Atmosphere Framework. When I saw the wild ass in requests, how it marks which button was pressed, which flag in the form was set, I was depressed. I didn’t want to delve into this and did the maximum I did - I drove “Atmosphere Framework CVE” into Google. Quickly looking at the headlines, I saw nothing interesting except XSS and went further. And then I went to other endpoints we know.These endpoints were pens for starting and ending your work. Which would characterize the range of time spent at work. There was already a code. I opened the project, scrubbed to the right place and began to study the parameters. Among them were deviceEUI , idxid , latitude and longitude. If with the last two it is immediately clear, then with the first - no. Having spent N the number of minutes for the successful completion of the request, I settled on Access denied .Then, to understand the object of study, I decided to download the application myself. I downloaded it, but I couldn’t log in anymore ... By that time they had put the back-up (but I didn’t know about it yet).Having opened the project code not on GitHub , but fully in ideas, I started looking for new endpoints. Found! Name appropriate: / api / covid / Device ...I began to research already in these pens. For a long time I did not understand how authorization goes, where is the header with a token or something else. And then it dawned on me ... She is gone! After making sure of this, having analyzed the processing and generation of requests, I made my conclusion on the backend part and sent it again to Twitter .Conclusion on the backend part : registration takes place by sending information about your device (phone). This includes the address, phone number, name, etc. Immediately after registration, they require a photo from you and upload it to your profile. In fact, in order to indicate whose photo this is, an additional parameter is indicated in the request - IMEI . It is located in the deviceId field of the Device modelthat we sent in the first step of registration. There is no validation that IMEI belongs to you. It is worth sending someone else's - and you successfully complete the request, allegedly from another device. It is noteworthy that among the endpoints there is / api / covid / Device / password , however, the processing of the response is as follows: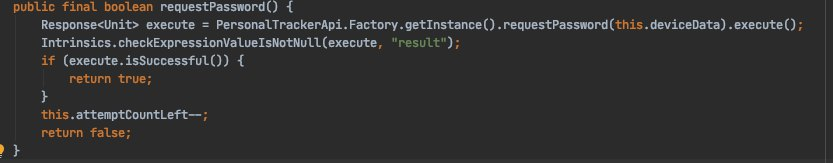 After registering the device, the API returns authCode , but, unfortunately, this code is stored in the object field and lies there, gathering dust. Not involved in the formation of other requests.Thus, without having authentication, any user knowing IMEIa person (or picking up / sorting it out) could send a false geo-location, upload a photo, send status about the beginning of the working day, and so on.I would love to play with such a fun implementation, but, alas, everything was turned off.Since that time, I began to completely run into the code and describe what I see in my Telegram channel. It turned out complete nonsense without any connection between the paragraphs, but after this post I found the strength (it was already 2-3 nights) to rewrite it and make it readable.
After registering the device, the API returns authCode , but, unfortunately, this code is stored in the object field and lies there, gathering dust. Not involved in the formation of other requests.Thus, without having authentication, any user knowing IMEIa person (or picking up / sorting it out) could send a false geo-location, upload a photo, send status about the beginning of the working day, and so on.I would love to play with such a fun implementation, but, alas, everything was turned off.Since that time, I began to completely run into the code and describe what I see in my Telegram channel. It turned out complete nonsense without any connection between the paragraphs, but after this post I found the strength (it was already 2-3 nights) to rewrite it and make it readable.Application parsing
It is immediately worth noting that the application by this time was no longer working. Therefore, I had no idea that it could be visual. He studied everything blindly and by code, which was far from all! We all know what decompilation is, but what happened was enough to draw certain conclusions.The application stores information about your device, name, phone number, address. There are obscure fields, such as comments . And there are interesting ones - a doctor.For identifying faces, the identix service is used (the same parameter from the back part). It allows you to return the age, gender, and other information from the uploaded photo. There is a unique identifier of a person that is used inside the application.Two types of devices are used for navigation: bluetooth, wifi. Both have a name and RSSI (signal quality, talking about the distance to a point).Your geolocation get thanks to Google and GPS module.Among the various types of stored information there is a location. Surprisingly, it has a huge number of fields. Including the battery level, the number of steps (despite the separate model for this) and more.In the settings, you can set the telemetry interval. Both collection and shipping. Not sure about the ability to change these parameters.There are three different types of unique identifiers:- IMEI devices.
- Device ID (not studied).
- MAC address of WiFi.
Thus, what I wrote above about the transfer and selection of IMEI is a simplification , for understanding. This is actually one of three identifiers.Your ID depends on which version of the SDK you have . Simply put, is it possible to get one or another type of unique identifier. Application developers themselves are confused in them and cannot converge in one name.The only place I put the code in the article.if (Build.VERSION.SDK_INT >= 29) {
return getMac(context);
}
return getImei(context);
And inside getImei, here's an if:if (Build.VERSION.SDK_INT >= 26) {
str = telephonyManager.getImei();
} else {
str = telephonyManager.getDeviceId();
}
The application can also get a SIM card number, but only in tricky cases. There is an opportunity - it will.A QR code is generated with the text ID , which can be of three types. This topic, as well as with the face recognition service, has been debated by anyone. I do not focus .An interesting feature of the application are push notifications to you on the device. Developers can send commands remotely and they will be executed by you. One of the teams is called OPEN_CAMERA . Another - SERVER_ADDRESS_KEY - here, most likely, by analogy with Telegram . When it was blocked, it sent out new IPs to all usersaddresses and we continued to use the messenger. In addition, they can remotely set the interval for sending and collecting telemetry. Here about possible push notifications .You can of course still talk about the avatar, how it can be rotated, how they locally save it, how they normalize it. You can talk about the desire to do an auto-update of the application, but you didn’t have time, about the ability to go to the dialer by number, maintaining a list of contacts (the most primitive address book is name and number), about the fact that they interact with the number of active file points around but it's all bored.Conclusion
You know, I won’t say how bad they are, I won’t say how good they are. Everyone will make a conclusion for himself. Critical flaws, vulnerabilities and spy things I have outlined to you. I can only say that, despite the deadlines, in no case should the development of a knowingly vulnerable application be allowed.I cannot but note the cohesion of the people. Everyone began to share their findings, be active, and who could not do this - put 1 in the reviews. 4207 units were recorded by me as much as possible and the absence (in my opinion) of other ratings.The same delusional message with drafts and the original conclusion on the backing are in my Telegram channel, and it is among the links in the profile.The last thing I want to show you is that this is a function of “illegal” getting the MAC address from their code and the same on stackoverflow (thanks ntoskrnl):And as always, thanks for reading right up to here!PS Anyone can make a mistake and I am no exception. Maybe something was wrong, maybe did not quite understand the implementation. Now they will come and say that during registration IP is remembered and it is impossible to execute requests to another person, huh ?! And I’ll answer that it’s nonsense and then the owner himself will lose access when reconnecting to the mobile network ... In general, you understand, the comments are open!