Hello everyone. In anticipation of the start of the Kali Linux Workshop, we have prepared a translation of an interesting article for you.
Today's guide introduces you to the basics of getting started with aircrack-ng . Of course, it is impossible to provide all the necessary information and cover each scenario. So get ready to do your homework and do your research yourself. There are many additional tutorials and other useful information on the forum and Wiki .Despite the fact that it does not cover all the steps from beginning to end, the Simple WEP Crack manual reveals in more detail how to work with aircrack-ng .Equipment setup, installation of Aircrack-ng
The first step in making aircrack-ng work properly on your Linux system is to patch and install the appropriate driver for your network card. Many cards work with several drivers, some of them provide the necessary functionality for using aircrack-ng , others do not.I think it is unnecessary to say that you need a network card compatible with the aircrack-ng package . That is, the hardware that is fully compatible and can implement packet injection. Using a compatible network card, you can hack into a wireless access point in less than an hour.To determine which category your card belongs to, see the hardware compatibility page .. Read the Tutorial: Is My Wireless Card Compatible? if you don’t know how to handle the table. However, this will not prevent you from reading the manual, which will help you learn something new and make sure of certain properties of your card.To get started, you need to know which chipset is used in your network card and which driver you need for it. You need to determine this using the information in the paragraph above. In the drivers section, you will find out which drivers you need.Aircrack-ng installation
You can obtain the latest version of aircrack-ng by downloading it from the home page , or you can use a penetration testing distribution such as Kali Linux or Pentoo, where the latest version of aircrack-ng is installed .To install aircrack-ng, see the documentation on the installation page .IEEE 802.11 Basics
Well, now that everything is ready, it's time to stop before we take action and learn something about how wireless networks work.The next part is important to understand in order to be able to figure out if something will not work as expected. Understanding how it all works will help you find the problem, or at least describe it correctly so that someone else can help you. Everything is a bit abstruse here, and you might want to skip this part. However, hacking wireless networks requires a little knowledge, and therefore hacking is a little more than just typing one command and letting aircrack do everything for you.How to find a wireless network
This part is a brief introduction to managed networks that work with Access Points (APs). Each access point sends about 10 so-called beacon frames per second. These packages contain the following information:- Network Name (ESSID)
- Is encryption used (and what encryption is used, but note that this information may not be true only because the access point reports it);
- What data rates are supported (in MBit);
- What channel is the network on.
This information is displayed in a tool that connects specifically to this network. It is displayed when you allow the map to scan networks with iwlist <interface> scanNetwork connection
There are several options for connecting to a wireless network. In most cases, Open System Authentication is used. (Optional: if you want to learn more about authentication, read this .)Open System Authentication:- Requests access point authentication;
- The access point answers: OK, you are authenticated.
- Requests access point association;
- The access point answers: OK, you are connected.
This is the simplest case, but problems arise when you do not have access rights, because:- It uses WPA / WPA2 and you need APOL authentication. The access point will refuse in the second step.
- The access point has a list of allowed clients (MAC addresses) and it will not allow anyone else to connect. This is called MAC filtering.
- Shared Key Authentication, WEP-, . (. « ?» )
The first thing to do is find a potential target. The aircrack-ng package has airodump -ng for this , but you can use other programs like Kismet , for example .Before you search for networks, you must transfer your card to the so-called “monitoring mode”. Monitoring mode is a special mode that allows your computer to listen to network packets. This mode also allows injections to be injected. We’ll talk about injections next time.To put the network card in monitoring mode, use airmon-ng :airmon-ng start wlan0
So you create another interface and add “mon” to it . So wlan0 will become wlan0mon . To check if the network card is actually in monitoring mode, do it iwconfigand see for yourself.Then, run airodump-ng to search for networks:airodump-ng wlan0mon
If airodump-ng cannot connect to the WLAN device, you will see something like this: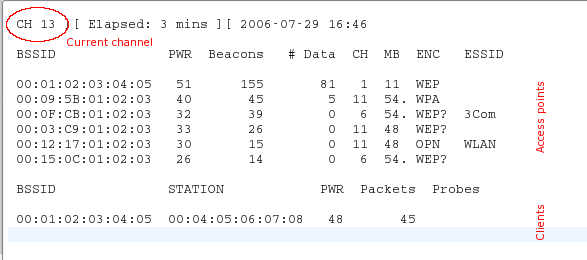 airodump-ng jumps from channel to channel and shows all the access points from which it receives beacons. Channels 1 to 14 are used for 802.11 b and g standards (in the USA it is allowed to use only 1 to 11; in Europe from 1 to 13 with some exceptions; in Japan from 1 to 14). 802.11a operates in the 5 GHz band, and its availability varies in different countries more than in the 2.4 GHz band. In general, well-known channels start from 36 (32 in some countries) to 64 (68 in some countries) and from 96 to 165. On Wikipedia you can find more information about the availability of channels. On Linux, allowing / disabling the transmission of certain channels for your country takes careCentral Regulatory Domain Agent ; however, it must be configured accordingly.The current channel is shown in the upper left.After a while, access points and (hopefully) some related clients will appear.The upper block shows the detected access points:The lower block shows the detected clients:Now you need to monitor the target network. At least one client must be connected to it, since hacking networks without clients is a more complex topic (see How to hack WEP without clients ). She should use WEP encryption and have a good signal. Perhaps you can change the position of the antenna to improve signal reception. Sometimes a few centimeters can be decisive for signal strength.In the example above there is a network 00: 01: 02: 03: 04: 05. It turned out to be the only possible target, since only the client is connected to it. She also has a good signal, so she is a suitable target for practice.
airodump-ng jumps from channel to channel and shows all the access points from which it receives beacons. Channels 1 to 14 are used for 802.11 b and g standards (in the USA it is allowed to use only 1 to 11; in Europe from 1 to 13 with some exceptions; in Japan from 1 to 14). 802.11a operates in the 5 GHz band, and its availability varies in different countries more than in the 2.4 GHz band. In general, well-known channels start from 36 (32 in some countries) to 64 (68 in some countries) and from 96 to 165. On Wikipedia you can find more information about the availability of channels. On Linux, allowing / disabling the transmission of certain channels for your country takes careCentral Regulatory Domain Agent ; however, it must be configured accordingly.The current channel is shown in the upper left.After a while, access points and (hopefully) some related clients will appear.The upper block shows the detected access points:The lower block shows the detected clients:Now you need to monitor the target network. At least one client must be connected to it, since hacking networks without clients is a more complex topic (see How to hack WEP without clients ). She should use WEP encryption and have a good signal. Perhaps you can change the position of the antenna to improve signal reception. Sometimes a few centimeters can be decisive for signal strength.In the example above there is a network 00: 01: 02: 03: 04: 05. It turned out to be the only possible target, since only the client is connected to it. She also has a good signal, so she is a suitable target for practice.Initialization Vector Sniffing
Due to hopping between channels, you will not intercept all packets from the target network. Therefore, we want to listen on only one channel and additionally write all the data to disk, so that later we can use them for hacking:airodump-ng -c 11 --bssid 00:01:02:03:04:05 -w dump wlan0mon
Using the parameter, -you select the channel, and the parameter after -wis the prefix of network dumps written to disk. The flag, –bssidtogether with the MAC address of the access point, limits the receipt of packets to one access point. The flag –bssidis available only in new versions of airodump-ng .Before hacking WEP, you will need between 40,000 and 85,000 different initialization vectors (Initialization Vector, IV). Each data packet contains an initialization vector. They can be reused, so the number of vectors is usually slightly less than the number of packets captured.Thus, you have to wait to intercept from 40k to 85k data packets (from IV). If the network is not busy, it will take a very long time. You can speed up this process using an active attack (or a replay attack). We will talk about them in the next part.Breaking into
Do you already have enough intercepted initialization vectors that are stored in one or more files, you can try to crack the WEP key:aircrack-ng -b 00:01:02:03:04:05 dump-01.cap
The MAC address after the flag -bis the BSSID of the target, and dump-01.capis the file containing the captured packets. You can use several files, just add all the names to the command or use the wildcard, for example dump*.cap.You can learn more about aircrack-ng parameters , output and usage from the manual .The number of initialization vectors required to crack a key is not limited. This is because some vectors are weaker and lose more key information than others. Typically, these initialization vectors are mixed with stronger ones. So, if you're lucky, you can crack a key with just 20,000 initialization vectors. However, often this is not enough,aircrack-ng can work for a long time (a week or more in case of high error), and then tell you that the key cannot be cracked. The more initialization vectors you have, the faster the hacking can happen and usually does in a few minutes or even seconds. Experience has shown that 40,000 to 85,000 vectors are sufficient for hacking.There are more advanced access points that use special algorithms to filter out weak initialization vectors. As a result, you will not be able to get more than N vectors from the access point, or you will need millions of vectors (for example, 5-7 million) to crack the key. You can read on the forum what to do in such cases.Active attacksMost devices do not support injection, at least without patched drivers. Some only support certain attacks. Refer to the compatibility page and look at the aireplay column . Sometimes this table does not provide relevant information, so if you see the word “NO” opposite your driver, do not be discouraged, but rather look at the driver’s home page, in the driver mailing list on our forum . If you were able to successfully replay using a driver that was not included in the supported list, feel free to suggest changes on the compatibility table page and add a link to a quick guide. (To do this, you need to request a wiki account on IRC.)First you need to make sure that packet injection really works with your network card and driver. The easiest way to check is to conduct a test injection attack. Before continuing, make sure that you pass this test. Your card should be able to inject it so you can follow these steps.You will need a BSSID (MAC address of the access point) and an ESSID (network name) of the access point that does not filter by MAC address (for example, your own) and is in the available range.Try connecting to the access point using aireplay-ng :aireplay-ng --fakeauth 0 -e "your network ESSID" -a 00:01:02:03:04:05 wlan0mon
The value after -is the BSSID of your access point.The injection worked if you see something like this:12:14:06 Sending Authentication Request
12:14:06 Authentication successful
12:14:06 Sending Association Request
12:14:07 Association successful :-)
If not:- Recheck the correctness of the ESSID and BSSID;
- Make sure that filtering by MAC address is disabled on your access point;
- Try the same on another access point;
- Make sure your driver is properly configured and supported;
- Instead of "0" try "6000 -o 1 -q 10".
ARP replay
Now that we know that packet injection works, we can do something that greatly accelerates the interception of initialization vectors: an attack injection of ARP requests .main idea
In simple terms, ARP works by transmitting a broadcast request to an IP address, and a device with this IP address sends a response back. Since WEP does not protect against replay, you can sniff a packet and send it again and again while it is valid. Thus, you just need to intercept and play back the ARP request sent to the access point to create traffic (and get initialization vectors).Lazy way
First open a window with airodump-ng , which will sniff traffic (see above). Aireplay-ng and airodump-ng can work simultaneously. Wait for the client to appear on the target network and start the attack:aireplay-ng --arpreplay -b 00:01:02:03:04:05 -h 00:04:05:06:07:08 wlan0mon
-bpoints to the target BSSID, -hto the MAC address of the connected client.Now you need to wait for the ARP packet. Usually you need to wait a few minutes (or read the article further).If you're lucky, you'll see something like this:Saving ARP requests in replay_arp-0627-121526.cap
You must also start airodump to capture replies.
Read 2493 packets (got 1 ARP requests), sent 1305 packets...
If you need to stop playback, then you do not need to wait for the next ARP packet to appear, you can simply use previously intercepted packets using the parameter -r <filename>“--ivs”when executing the command. For aircrack-ng use “aircrack -z <file name>”-x <packets per second>Aggressive way
Most operating systems clear the ARP cache on shutdown. If you need to send the next packet after reconnecting (or just use DHCP), they send an ARP request. As a side effect, you can sniff the ESSID and possibly keystream during reconnection. This is useful if the ESSID of your target is hidden or if it uses shared-key authentication.Let airodump-ng and aireplay-ng work. Open another window and launch a deauthentication attack :Here -ais the BSSID of the access point, the -MAC address of the selected client.Wait a few seconds and ARP replay will work.Most customers try to reconnect automatically. But the risk that someone will recognize this attack, or at least pay attention to what's happening on the WLAN, is higher than with other attacks.You will find more tools and information about them here .Learn more about the course