 Under the cut is a translation of the article " Understanding Hardware-enforced Stack Protection ".
Under the cut is a translation of the article " Understanding Hardware-enforced Stack Protection ".
Authors: Kernel protection team - Jin Lin, Jason Lin, Niraj Majmudar, Greg Colombo
 This is the first (review) publication of a planned series of two translations about the introduction of Intel's Control-flow Enforcement Technology (CET) in Windows 10.
This is the first (review) publication of a planned series of two translations about the introduction of Intel's Control-flow Enforcement Technology (CET) in Windows 10.
We strive to make Windows 10 one of the most secure operating systems for our customers, and for this we invest in many security features. Our philosophy is to create functions that reduce the effectiveness of a wide class of vulnerabilities (ideally, without changing the application code). MSDN has a separate article, “Mitigate threats by using Windows 10 security features,” which aggregates all the security-oriented technologies that we have built into Windows over the years. This article also describes how each of the functions ensures the safety of our customers. There is also a presentation by Matt Miller and David Weston , which can be recommended for reading after the MSDN article. The presentation goes deep into our security philosophy.
We are currently studying hardware-based security features. This will allow us to significantly raise the bar of defense against attacks. Thanks to the deep integration of the Windows kernel with hardware, it will become difficult and costly for attackers to carry out large-scale attacks.
Based on the research ( Evolution of CFI attacks , Joe Bialek), it can be stated that ROP (Return Oriented Programming) attacks have become a very common attacker tool. Consequently, they are the next target for built-in proactive Windows security technologies. In this publication, we describe our efforts to strengthen the integrity of the control flow in Windows 10 using hardware-based stack protection.
Memory Security Vulnerabilities
, , . , (dangling pointers), .
( strcpy). , (: ) , .
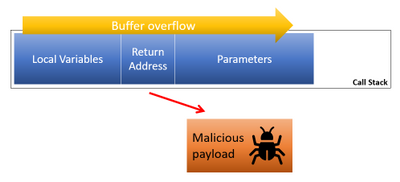
(dangling pointers) , , , , . use-after-free ( ) / , ( , ).
: , . , .
, .
:

Code Integrity Guard (CIG) .
Arbitrary Code Guard (ACG) , , , .
CIG ACG , Call/Jump Oriented Programming (COP/JOP) Return Oriented Programming (ROP).
Control Flow Guard (CFG) Windows 10 ( , forward-edge CFI). (Shadow Stacks) (backward-edge CFI).
ROP
, , . : , Data Execution Prevention (DEP) Address Space Layout Randomization (ASLR). () . , RET ( ), ( ), .
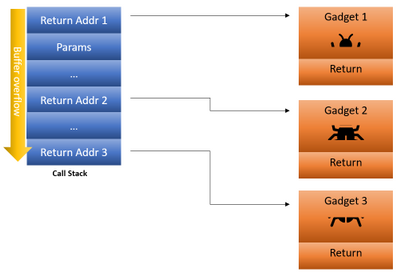
, Intel' Control-flow Enforcement Technology (CET). CET Intel.
Windows 10. , (Shadow Stack). CALL , . RET , , .
, (control protection, #CP). Windows , .
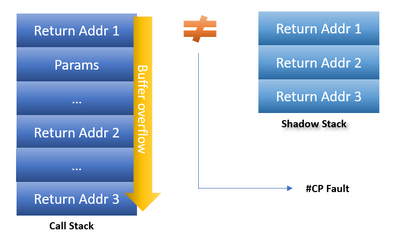
(Shadow Stack) , .
(Shadow Stacks) CET
, , , .
SSP, () . .
:
- INCSSP — SSP ( )
- RDSSP — SSP
- SAVEPREVSSP/RSTORSSP — / (, )
Intel’ CET.
, PE , .
, Windows , . Windows , PE .
(opt-in: ) , .
, Insider preview- Windows 10. , Intel' CET, Insider preview- Windows 10.
ROP , . , Windows , .
, , . , . Windows 10 .
, ( ) . - ( ) ( ) — . … , , :) , .