 Many already know that Rostelecom, with the support of Mail.ru, has begun the implementation of its advertising banners on sites that are not protected by the HTTPS protocol . You can protect yourself from their appearance on your site by transferring it to HTTPS. But what if you do not have such an opportunity or it is too time-consuming for you? I have done my little research and want to share a simple and yet effective way against this infection.There were already investigations on this subject on Habré and I relied on them:It is known that banners are implemented by replacing the original JavaScript file with malicious one through a redirect. And already he inserts a banner on the website page and uploads the original file. Thus, when checking for viruses, it is impossible to immediately detect how advertising appeared on the site, because the original files are not changed, and the redirect is performed at a certain interval and it is quite difficult to detect it.For research, you need a site that uses the HTTP protocol and contains JS files. As an example, I took the site of the Museum of Kirov . With some periodicity, banners can be observed on it.
Many already know that Rostelecom, with the support of Mail.ru, has begun the implementation of its advertising banners on sites that are not protected by the HTTPS protocol . You can protect yourself from their appearance on your site by transferring it to HTTPS. But what if you do not have such an opportunity or it is too time-consuming for you? I have done my little research and want to share a simple and yet effective way against this infection.There were already investigations on this subject on Habré and I relied on them:It is known that banners are implemented by replacing the original JavaScript file with malicious one through a redirect. And already he inserts a banner on the website page and uploads the original file. Thus, when checking for viruses, it is impossible to immediately detect how advertising appeared on the site, because the original files are not changed, and the redirect is performed at a certain interval and it is quite difficult to detect it.For research, you need a site that uses the HTTP protocol and contains JS files. As an example, I took the site of the Museum of Kirov . With some periodicity, banners can be observed on it. I wrote a special utility. She makes a request at a specific URL at regular intervals and compares the received content with the previous one. If the content of the answer is different, it is saved for study. When analyzing requests for a small script
I wrote a special utility. She makes a request at a specific URL at regular intervals and compares the received content with the previous one. If the content of the answer is different, it is saved for study. When analyzing requests for a small script http://muzey43.ru/js/script-eye.js, it was found that the same content is always returned - there is no redirect.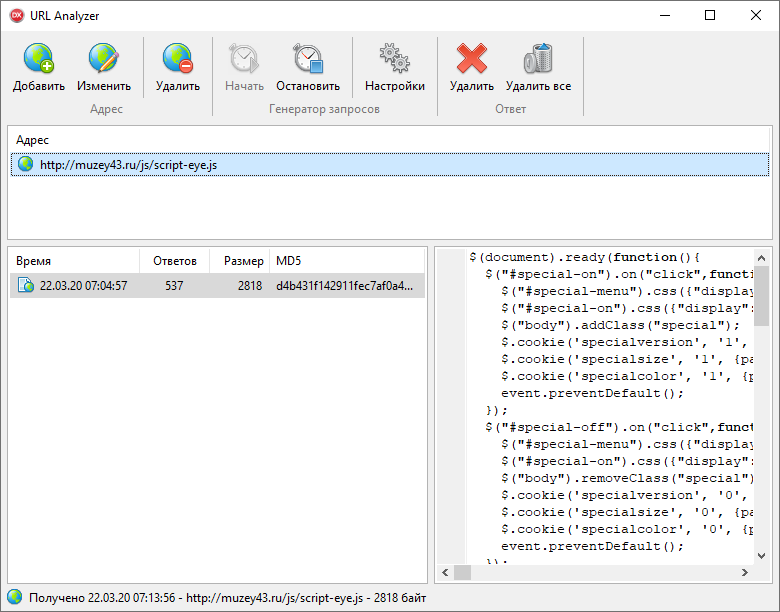 Then how does the banner appear? In the study of the source code of a site was discovered another JS file that is downloaded by HTTP, but with a different host:
Then how does the banner appear? In the study of the source code of a site was discovered another JS file that is downloaded by HTTP, but with a different host: http://ajax.googleapis.com/ajax/libs/jquery/1.7.0/jquery.min.js. When analyzing this request, we periodically observe the receipt of the contents of a malicious file.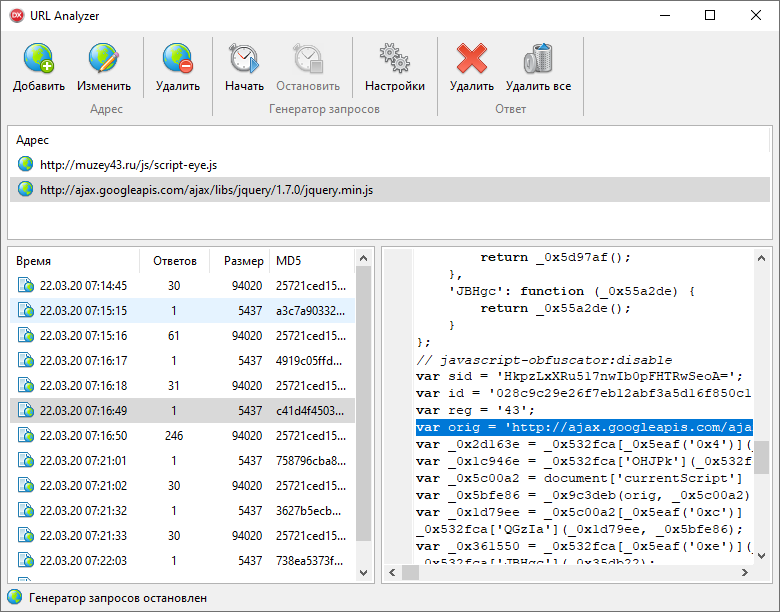 The screenshot shows that malicious content is downloaded approximately twice a minute, but there may be short breaks in the redirect. The contents of the malware each time changes by obfuscating the code and contains a link to the original script.Most likely, there is a certain “white list” of hosts for which the JS redirect is prohibited. For example, the site of the Ministry of Culture of the Kirov region . Despite the fact that it works through the HTTP protocol, banners do not appear on it. But on the Kirov Museums website there is a banner, although there is no redirect for its scripts, but through a redirect of a script from another host a banner is embedded in it. In order to eliminate the vulnerability in this case, most likely, it is enough to request the file using the HTTPS protocol, i.e. just replace the script URL with
The screenshot shows that malicious content is downloaded approximately twice a minute, but there may be short breaks in the redirect. The contents of the malware each time changes by obfuscating the code and contains a link to the original script.Most likely, there is a certain “white list” of hosts for which the JS redirect is prohibited. For example, the site of the Ministry of Culture of the Kirov region . Despite the fact that it works through the HTTP protocol, banners do not appear on it. But on the Kirov Museums website there is a banner, although there is no redirect for its scripts, but through a redirect of a script from another host a banner is embedded in it. In order to eliminate the vulnerability in this case, most likely, it is enough to request the file using the HTTPS protocol, i.e. just replace the script URL withhttps://ajax.googleapis.com/ajax/libs/jquery/1.7.0/jquery.min.js
But what if your site is not in the “white list” and you need to use your own scripts? I found an easy way to avoid JS redirect. It is enough to add an arbitrary parameter to the script URL: https://ajax.googleapis.com/ajax/libs/jquery/1.7.0/jquery.min.js?banner=offand the redirect will not be performed.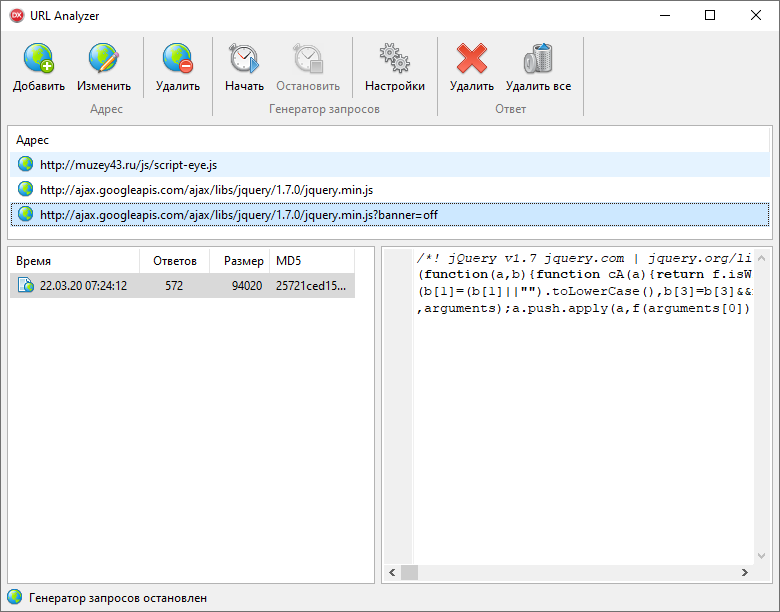 This is probably done so that the redirect does not interfere with the operation of complex dynamic JS sites, or the necessary files are simply identified by the extension
This is probably done so that the redirect does not interfere with the operation of complex dynamic JS sites, or the necessary files are simply identified by the extension .js. But in any case, it’s enough to add random parameters and Rostelecom advertising banners to the URLs of scripts on the pages of your site on it.PSAs the comments correctly indicate, the most appropriate solution for website owners will be switching to HTTPS, especially since now some hosting companies offer installing a free certificate directly from the panel with one button. After all, tomorrow Rostelecom can easily tighten the redirect algorithm and the solution given above will stop working. And just blocking a redirect by a filter on the client, as some suggest, can only solve the client’s problem - there will be no banner, but there will be no substitution of the script that it replaced and the site’s functionality may suffer.