[ Disclaimer: I’m an IB translator, not an IS specialist, so I could have missed. But it seems that they did not write about this attack on Habré, but I liked it - it’s beautiful (+ my XiaoMi-cabinet was in the list of vulnerable ones). For those who like to learn English, I have added terms in brackets].
A new type of attack called “Surfing Attack” can be used against devices with voice assistant.
Voice assistants, which gained their popularity thanks to the Apple Siri, turned out to be very convenient for users - you can play music, call a friend or download a video.
Researchers, however, have demonstrated how indistinguishable to the human ear ultrasonic waves [ultrasonic waves that are not audible to the human hearing] can be used to manage the voice assistants, including Siri, Google Now and Bixby. And this despite the fact that they must recognize the voice of the owner, and not someone else.
You can, of course, implement imitation of [emulation] ( DolphinAttack 2017 ), but there are a couple of conditions for this:
- Between the device and the emitter of ultrasonic waves [ultrasound waves emitter] must be in line of sight [a clear line of sight] .
- The distance between them should be small.
In Surfing Attack, the researchers showed that ultrasonic waves can be sent not only directly, but also through materials of significant thickness, such as a single piece of glass or even a wooden table. They achieved this by fixing a piezoelectric disk under the surface on which the smartphone was located.
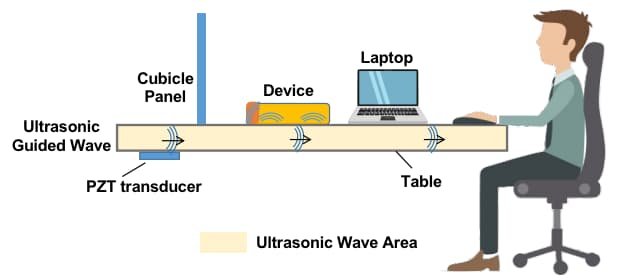
SurfingAttack uses [leverages] directional ultrasonic waves inside the table that generate an ultrasonic emitter hidden beneath the surface.
, , — 17 (~ 43 ), . , , , .
, SurfingAttack , Google . , , ( [2FA]).

17 15 , Apple, Google, Samsung, Motorola, Xiaomi Huawei. – Samsung Galaxy Note 10 Huawei Mate 9. , , , « » [dampened the ultrasonic waves].
, SurfingAttack .
, , , [future device launches].
Of course, the obvious way is to use materials that, as in the cases above, are capable of damping ultrasonic waves, but it is necessary to consider other possible attack vectors, and not just this one separately.
Thank!