Is a mobile phone in the work process evil or good? Does a gadget allow an employee to more quickly solve tasks? Or helps the employer to tighten control subordinate? Creates a creative atmosphere? Or annoying at 23:00 messages in the messenger and letters? Contributes to the leakage of corporate secrets or, conversely, provides insurance against surprises? What is corporate mobility, what is its current state and what is the history of this concept, we deal with our partners from the Scientific Testing Institute for Integrated Security Systems ( NII SOKB ). SourceAccording to a study that we conducted a couple of years ago, about 93% of respondents (respondents were quite diverse: office workers, field staff, drivers, and many others) use smartphones for corporate purposes. In addition to fairly predictable calls and text messages, among the most common device usage scenarios included interaction with mail, editing documents, and even connecting to a virtual workstation (VDI).
SourceAccording to a study that we conducted a couple of years ago, about 93% of respondents (respondents were quite diverse: office workers, field staff, drivers, and many others) use smartphones for corporate purposes. In addition to fairly predictable calls and text messages, among the most common device usage scenarios included interaction with mail, editing documents, and even connecting to a virtual workstation (VDI). From all this we can conclude that at present the mobile device in the working environment is not just a “dialer”, but a tool capable of taking on tasks that previously required additional, often specialized, equipment.In this article, we will address the topic of corporate mobility and consider it from various points of view - not only marketing and managerial, but also from the perspective of a “field” employee. To make the story more substantive, we interviewed our colleagues from the Scientific Research Institute of Special Design Bureau , who have extensive experience in similar projects and are ready to share examples, stories and observations from their practice (theory by theory, but in life everything is always more complicated and interesting).NII SOKB specializes in providing comprehensive safety and labor protection, and is also the developer of SafePhone - a solution for the centralized management of mobile devices, applications, content and communications in the organization. We talked with Oleg Assur, chief engineer of the Scientific Research Institute of the SOKB, about what corporate mobility is and what solutions exist in this area.
From all this we can conclude that at present the mobile device in the working environment is not just a “dialer”, but a tool capable of taking on tasks that previously required additional, often specialized, equipment.In this article, we will address the topic of corporate mobility and consider it from various points of view - not only marketing and managerial, but also from the perspective of a “field” employee. To make the story more substantive, we interviewed our colleagues from the Scientific Research Institute of Special Design Bureau , who have extensive experience in similar projects and are ready to share examples, stories and observations from their practice (theory by theory, but in life everything is always more complicated and interesting).NII SOKB specializes in providing comprehensive safety and labor protection, and is also the developer of SafePhone - a solution for the centralized management of mobile devices, applications, content and communications in the organization. We talked with Oleg Assur, chief engineer of the Scientific Research Institute of the SOKB, about what corporate mobility is and what solutions exist in this area.Tell us how mobile devices came into Russian business and how did your views on their application change?
We have been dealing with “mobile” topics for a long time (for more than 10 years - we can say, we were at the forefront), so we participated in the development of this IT area from the very beginning.More or less noticeably, "mobile" began to appear in the "dashing 2000s" (the devices themselves, of course, existed before, but it was a piece of history that did not have a mass character). Then they were used mainly for making calls and sending text messages. They were given out to employees with a comment: “So that you are always in touch, and don’t even think about calling America!” “Smart phones” already existed (the now familiar “smartphone” sounded quite futuristic), but they did not play a big role in the corporate environment, and in most companies employees continued to use their usual computers for their work.The turning point, in my opinion, occurred in the mid-zero, and it is associated with two events: the purchase in 2005 of Google Android, Inc. with the subsequent launch of the platform of the same name and the announcement in 2007 of the first iOS device (then still with the iPhone OS). Both of these platforms immediately offered rich functionality besides calls and SMS and quickly began to supplant classic push-button phones.Naturally, the lucky owners of these devices began to use them in their work: sometimes with the approval of management, sometimes “clandestinely”. This led to a trend in which the device gradually accumulates important corporate information (they connected mail - confidential corporate correspondence appeared, allowed access to CRM - a list of clients was added to the correspondence, etc.). The loss or theft of a gadget is becoming an increasingly significant risk for the company. It is at this moment that the history of centralized corporate mobility management systems begins, including our SafePhone platform .What is the current role of a mobile device in business?
Today, a mobile device is a real food processor that can perform many different functions. On mobile devices, there are full-fledged office suites (and this is probably the main tool for 90% of company employees). Although it is worth noting that such a use case is limited, and PCs still remain the main means of working with documents.  Source: BroadcomIn general, an interesting picture is now observed. Since the inception of IT, it was believed that for full-fledged work, employees need a real, large computer or laptop, but always with a full-fledged x86 processor. Attempts to get this situation off the ground always rested on the reinforced concrete argument from the series: "we have systems that work only under DOS (Windows 95/98, Java 5 - underline what you need), you will break everything for us." It should be understood that the corporate environment is quite conservative ( COBOL programmers are still in demand).The first advances began with the widespread introduction of virtualization and the advent of VDI ( Virtual desktop infrastructure) Suddenly it turned out that you can work with Legacy systems in general from any device, if only there would be a secure network connection. The network, by the way, has long been a deterrent to the development of this technology, but it seems that this restriction will be removed soon. With the advent of the new 5G generation, not least thanks to Samsungthat provide communication at speeds from 1 Gbit / s through a mobile network, you can “drive” virtually any corporate data types (documents, sound, high-resolution video) with a minimum delay. Another consequence of this “acceleration” is also the general trend of abandoning “fat customers”. Most modern business systems have a normal web interface, many in addition to this release a mobile client or a mobile version of the web interface (which can also be "wrapped" in the application using the Progressive Web App ).Thus, it turns out that now, in fact, nothing prevents you from working only on a smartphone or tablet. This, of course, is still a certain prospect (remember conservatism), but its implementation is just around the corner.
Source: BroadcomIn general, an interesting picture is now observed. Since the inception of IT, it was believed that for full-fledged work, employees need a real, large computer or laptop, but always with a full-fledged x86 processor. Attempts to get this situation off the ground always rested on the reinforced concrete argument from the series: "we have systems that work only under DOS (Windows 95/98, Java 5 - underline what you need), you will break everything for us." It should be understood that the corporate environment is quite conservative ( COBOL programmers are still in demand).The first advances began with the widespread introduction of virtualization and the advent of VDI ( Virtual desktop infrastructure) Suddenly it turned out that you can work with Legacy systems in general from any device, if only there would be a secure network connection. The network, by the way, has long been a deterrent to the development of this technology, but it seems that this restriction will be removed soon. With the advent of the new 5G generation, not least thanks to Samsungthat provide communication at speeds from 1 Gbit / s through a mobile network, you can “drive” virtually any corporate data types (documents, sound, high-resolution video) with a minimum delay. Another consequence of this “acceleration” is also the general trend of abandoning “fat customers”. Most modern business systems have a normal web interface, many in addition to this release a mobile client or a mobile version of the web interface (which can also be "wrapped" in the application using the Progressive Web App ).Thus, it turns out that now, in fact, nothing prevents you from working only on a smartphone or tablet. This, of course, is still a certain prospect (remember conservatism), but its implementation is just around the corner.Those. it turns out that in the future mobile devices can replace classic PCs in a corporate environment?
Gradually, the business is moving away from system units towards something more mobile. At first it was quite bulky five-kilogram laptops that worked on the battery for no more than an hour and a half (old-timers will remember the terrible protruding parts of the extended battery, which gave one hour to work and half a kilogram to weight), then we switched to ultraportable laptops weighing 1.5-1.7 a kilogram and a working time of six to seven hours, and now devices less than one kilogram with 12 hours of battery life are already widespread. In parallel with this "miniaturization" of conventional computers, there is an "increase" in smartphones. Today's phone has quite impressive features: the same S20in its top edition, it has 16GB of memory and an eight-core processor on board, which is pretty decent even for full-size laptops.Of course, the most important question is software. Everything is ambiguous here. Many manufacturers have tried to adapt the desktop interface for use in a mobile environment (touch, relatively small screens and other attributes of mobility), but so far there are no ideal solutions: unfortunately, we return to that notorious conservatism; nobody will rewrite the interface on Delphi twenty years ago. At the same time, it’s much easier to add support for “rubber” / drag-and-drop windows to native mobile applications, which, in fact, was done by Google in Android Nougat. If an example of such an approach is interesting, then you can pay attention to the Samsung DeX.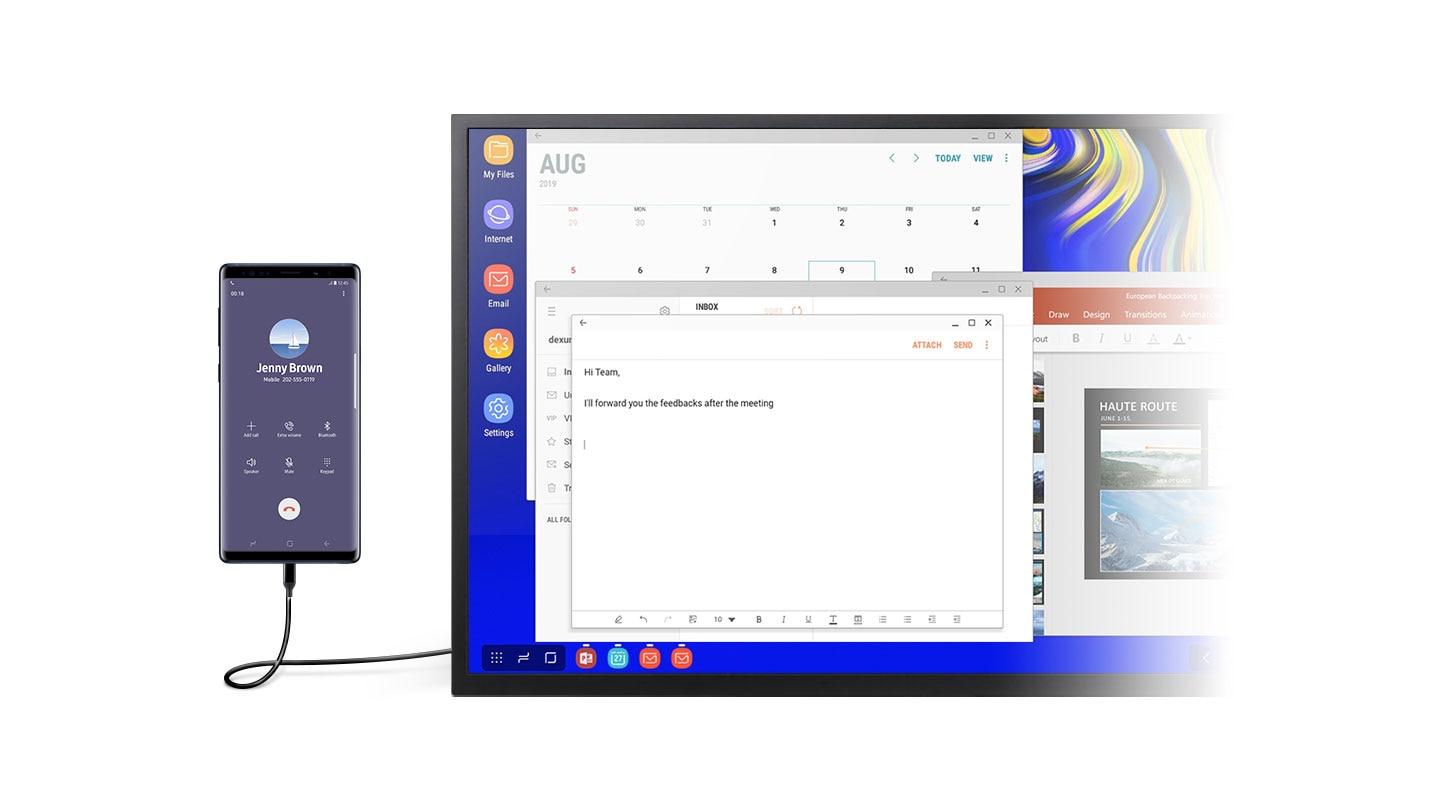 As of today, such an “upward” scenario (turning mobile devices into full-size jobs) seems to us, at least, no less promising than a “downstream” one (using desktops as mobile devices).
As of today, such an “upward” scenario (turning mobile devices into full-size jobs) seems to us, at least, no less promising than a “downstream” one (using desktops as mobile devices).How does the introduction of mobile technology affect the workflow?
Difficult question. Like any technology, mobility can be used in two ways: to make life in a company better or, conversely, worse. Source: Dilbert , our translation.Classically, mobility implies a “work where you feel comfortable” approach (not to be confused with “work constantly”). Conceptually, this means that an employee can fulfill his duties, not necessarily being at the workplace, but also being on a business trip or, for example, at home. And he will do it as effectively as in the office. In addition, internal corporate procedures are simplified: you can order a 2NDFL certificate or agree on a vacation application by pressing a single button on your smartphone.Separately, it is necessary to note the optimization of communication within the company. This is especially true for our country, where in the order of things for the organization to have a head office in Moscow and regional, for example, in Yekaterinburg and Irkutsk. In this case, the interaction turns into a big problem. When colleagues are always in touch with constant access to working tools, it is much easier to coordinate a convenient moment for everyone to call or group chat with general editing of documents.Another incentive for employees can be the provision of a mobile device. In practice, various models are widespread in companies, from providing a corporate gadget with the possibility of personal use of a smartphone (Corporate Owned, Personally Enabled, COPE), to a personal smartphone or tablet with working applications (Bring Your Own Device, BYOD). By the way, BYOD comes from the well-known BYOB abbreviation - bring your own beer - that is, "come with your own alcohol" in the description of the party.
Source: Dilbert , our translation.Classically, mobility implies a “work where you feel comfortable” approach (not to be confused with “work constantly”). Conceptually, this means that an employee can fulfill his duties, not necessarily being at the workplace, but also being on a business trip or, for example, at home. And he will do it as effectively as in the office. In addition, internal corporate procedures are simplified: you can order a 2NDFL certificate or agree on a vacation application by pressing a single button on your smartphone.Separately, it is necessary to note the optimization of communication within the company. This is especially true for our country, where in the order of things for the organization to have a head office in Moscow and regional, for example, in Yekaterinburg and Irkutsk. In this case, the interaction turns into a big problem. When colleagues are always in touch with constant access to working tools, it is much easier to coordinate a convenient moment for everyone to call or group chat with general editing of documents.Another incentive for employees can be the provision of a mobile device. In practice, various models are widespread in companies, from providing a corporate gadget with the possibility of personal use of a smartphone (Corporate Owned, Personally Enabled, COPE), to a personal smartphone or tablet with working applications (Bring Your Own Device, BYOD). By the way, BYOD comes from the well-known BYOB abbreviation - bring your own beer - that is, "come with your own alcohol" in the description of the party. The man who confused BYOD with BYOB. Source: Timo ElliottThere are also some intermediate options in which an employee can choose a working device with partially corporate payment and the prospect of the gadget becoming a property after a while (Choose Your Own Device, CYOD).Summarizing, for employees mobility is the freedom to choose a work format convenient for themselves, while for a company it is cost optimization and a good tool for building well-coordinated processes. Of course, the correct balance and fine-tuning are important: some employees do not have high self-organization, and employers are prone to excessive control.
The man who confused BYOD with BYOB. Source: Timo ElliottThere are also some intermediate options in which an employee can choose a working device with partially corporate payment and the prospect of the gadget becoming a property after a while (Choose Your Own Device, CYOD).Summarizing, for employees mobility is the freedom to choose a work format convenient for themselves, while for a company it is cost optimization and a good tool for building well-coordinated processes. Of course, the correct balance and fine-tuning are important: some employees do not have high self-organization, and employers are prone to excessive control.What is corporate mobility management, and why is it needed?
The main threat: the more a mobile device is involved in corporate life (work correspondence, documents, a messenger for a team, etc.), the more data there is on it, the loss of which can sensitively hit the company. Accordingly, the contents of the device becomes a significant asset of the company that needs to be managed.Here, a contradiction immediately arises: security requires maximum restriction of user freedom and deterministic operation scenarios (access to mail only from the office strictly from 9 to 18), while the whole concept of mobility implies maximum flexibility and variability of use. At the dawn of the industry, the choice has always been made towards limitations. This gave rise to funny situations. As an incentive, the employee was given the opportunity to install corporate mail on his device. This was done with the condition that all the correct security policies were applied and an agent was installed to monitor potential threats. This agent non-alternatively set a 12-digit alphanumeric password (in especially sophisticated cases there was also a dictionary of forbidden combinations and a restriction on password rotation) on the entire device and began to collect all the information available to it. Having suffered like this for a week (each time you try to read SMS you need to enter this same password), the user angrily deleted the mail and forgot about this “encouragement” as a nightmare. Source: Dilbert , our translationNow the situation has changed dramatically. It is good practice when the security system is transparent and as invisible as possible to the user. It should be like a castle from a well-known riddle, which "does not bark, does not bite, but does not let into the house." It should be most convenient for the user to work with the device, all the dirty work is taken over by the mobility management system.
Source: Dilbert , our translationNow the situation has changed dramatically. It is good practice when the security system is transparent and as invisible as possible to the user. It should be like a castle from a well-known riddle, which "does not bark, does not bite, but does not let into the house." It should be most convenient for the user to work with the device, all the dirty work is taken over by the mobility management system.There are a large number of abbreviations for corporate mobility management systems - MDM, EMM, UEM. Tell in a nutshell, what is their difference and how does it fit into a single concept?
Interpretation of terms by different companies can vary greatly. More or less generally accepted are the definitions formulated by Gartner .Mobile Device Management (MDM) - a term that appeared in the late 1990s - early 2000s, means systems that are responsible for managing the life cycle of mobile devices. This usually means the following functionality:- device inventory
- OS settings
- provisioning and deprovisioning
Over time, pure MDM functionality began to be missed, and the following features often began to be added to it:- Mobile Application Management (MAM) - application management.
- Mobile Identity (MI) - Credential and Access Management.
- Mobile Content Management (MCM) - content management.
By the mid-2010s, this set became the standard for the market, and there was no sense in dividing the solutions into separate modules. Then came the term Enterprise Mobility Management (EMM), which denoted a combination of MDM, MAM, MI, and MCM. This change was documented in a Gartner report published in 2014.Then a trend arose, which we spoke about earlier. Mobile devices have become exactly the same workplace as classic desktops and laptops, and it became clear that they need to be managed in a single circuit: there is no longer a division into stationary and mobile. This was the starting point for the emergence of the new term Unified Endpoint Management (UEM). The emergence of UEM was recorded in the 2018 Gartner report .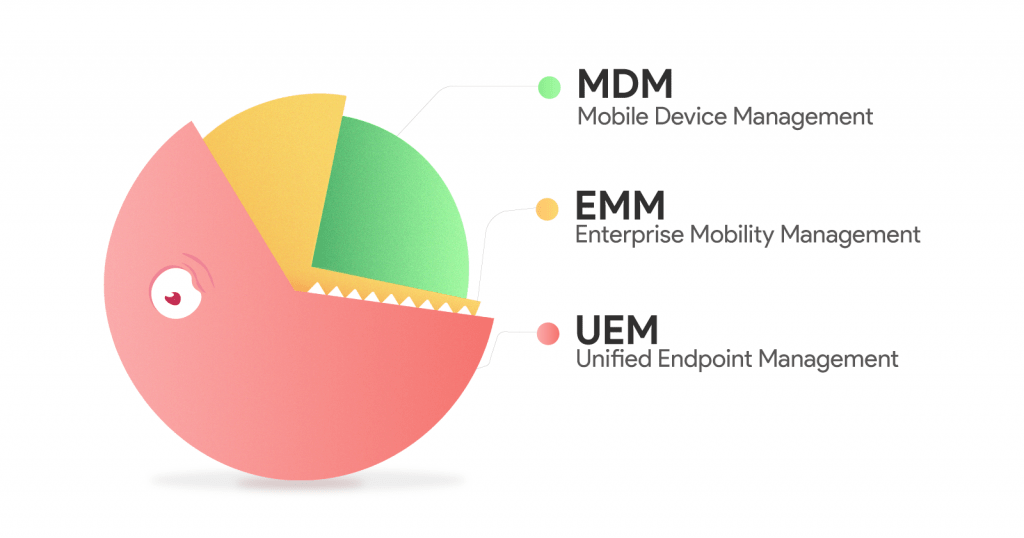 Source: ITSMDailyWe are entering the new decade with the UEM paradigm, and that's what systems are called today, the task of which is to manage mobile and stationary devices in the company.
Source: ITSMDailyWe are entering the new decade with the UEM paradigm, and that's what systems are called today, the task of which is to manage mobile and stationary devices in the company. We discussed history and theory, let's move on to practical issues. How can a mobile workplace now appear in an enterprise? Please share your experience in this area.
Any implementation is always a complex story, and two identical projects do not exist. But let's try to formulate some general points.The implementation initiative often comes from below, from ordinary employees. Now almost everyone has mobile devices, and it is only a matter of time before they will be used for work. There must be a critical mass of people with similar gadgets, after which a request is sent to the IT department for the provision of such a service. Management in this case can choose two strategies: support (the green light is given to the initiative, and the project is initiated) or prohibit. In the latter case, the argument is a big risk of leakage (“lose financial reporting” or “competitors spy on the subway over the shoulder”). As practice shows, this approach is not very constructive. Even if mobile devices are strictly prohibited, employees will still use them “underground”. You can apply administrative measures (reprimands, penalties, sanctions), but this does not always guarantee a 100% result. And even if such restrictions are justified, there will always be an employee who violates all prohibitions, and this one case will have tremendous consequences. The most correct strategy, in our opinion, is the good old principle: “if you can’t win, head.”An even more dangerous controlled environment is many times better than an uncontrolled one.First, this is usually mail (the ability to "pick up" it with a mobile client), then there are documents and various working systems (corporate portal, ERP, CRM, etc.). After the technology is “rooted” (when the tendency becomes clear), the design of internal services is already underway with the expectation of their use on various platforms (including mobile).It is also common that the implementation initiative comes from management. We must not forget that working mobility provides many advantages associated with optimizing costs and increasing the “connectivity” of a business. But here, too, “excesses” are possible. In any heterogeneous environment (and a typical enterprise is just such an environment consisting of very different parts: bookkeeping, warehouse and logistics, office, field staff) there are interests, and not everyone is ready for innovations. A common situation is when part of the team perceives this kind of change “with hostility” (“everything works for us”). In this case, the “carrot” principle has proven itself when the employee receives some bonus when using the implemented system (for example, a telephone as a pass to the office or payment for lunch and booking meeting rooms from a smartphone).These bonuses should encourage the employee to use mobile devices, but not to limit or infringe on him.When implementing complex mobility projects at an enterprise, the following tools are useful:- Conducting an audit and examination of the current state of infrastructure before implementation. This can be monitoring software installed on end devices with the consent of users and collecting statistics on used applications and visited network resources. Maximum openness and correctness in matters of observing the anonymity and privacy of an employee is important. The ultimate goal of this activity is to get a comprehensive picture of the current situation, and not to identify violators. Outreach seminars work well with a clear demonstration of the functionality of monitoring software and the involvement of management in the collection of statistics.
- Feedback. It is important to understand what is happening with the project on the side of the end users. This can provide valuable information about the features of the system and has a positive effect on the attitude of employees. Feedback formats can be different: from face-to-face meetings with a discussion of current problems to a certain questionnaire, possibly anonymous, because not everyone is willing to freely share their impressions.
- Count resources on an iterative development and implementation process. It’s impossible to take everything into account at the start of the project, so you always need to lay additional resources for revision. When implementing this, many people do not take into account, because of which projects break off somewhere in the middle.
Two main questions that are always asked during implementation:- « , / »
, . – (Work Profile). – , — , Samsung. , , , , .
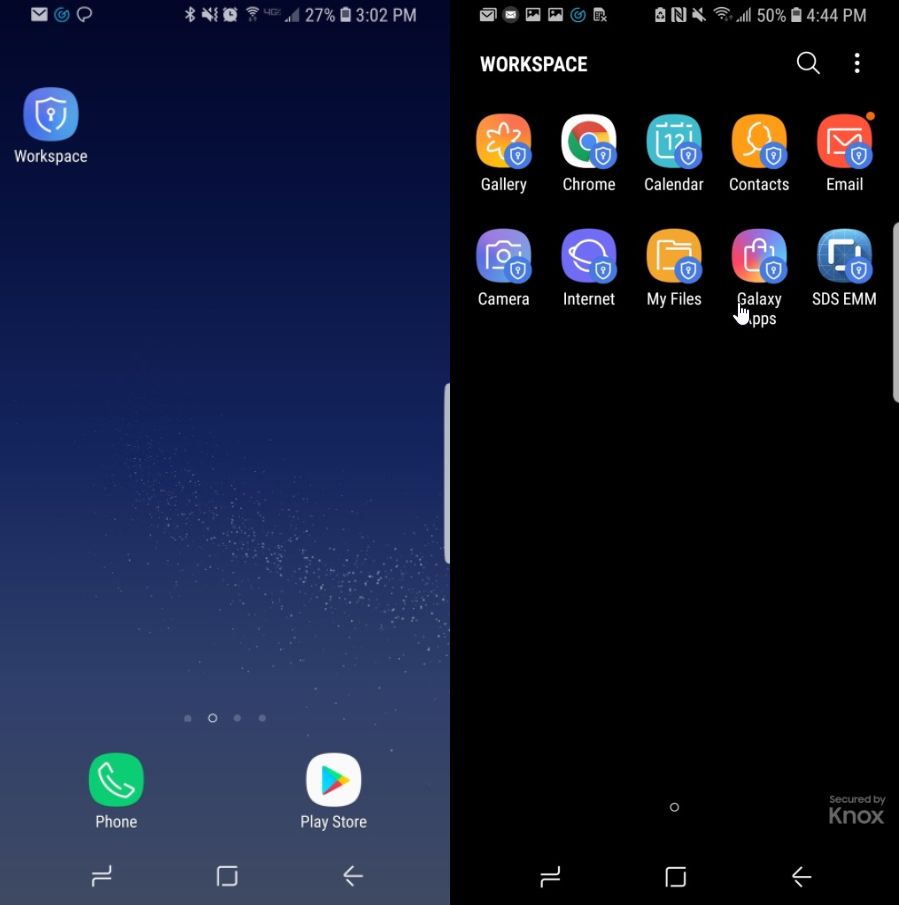
– : , , .
- «- 10 . , 300 , . »
« », (, , ). . Samsung Knox , Knox Mobile Enrollment (KME), « » . . IT . – .
. , Android . . ? ?
This is a stereotype, but it is quite stable. It is especially sad that not only ordinary users, but also some IT and information security workers are affected. No, now the Android OS is quite safe and very common in the corporate segment. This is evidenced by a recent study conducted by IDC. According to it, 78% of mobile devices used in various companies around the world are running the Android OS.Separately, about the security of Samsung devices. According to the latest Gartner rating, the Knox platform received a strong rating of 27 out of a possible 30 positions, which is one of the highest results ( Samsung Note:in more detail about the Knox platform we talked about in this article ).To reasonably talk about security, you must first decide on the types of threats. Classically, data protection is divided into two large segments.- Data-at-rest (storage and work with data). This includes those types of threats that are associated with the “existence” of data on the end device. Examples:
- . , – . . – (, – ). ( ). , .

- /. Android ( ). , , . , , . — .

- Data-in-transit ( ). , . :
- Unprotected traffic. Public Wi-Fi access points are useful during business trips or when you are far from your workplace, but you need to work with a large amount of data. At the same time, unfortunately, it cannot be guaranteed that the channel is safe, and it is not monitored by attackers. To combat this type of threat, a VPN is usually used with automatic activation to launch certain applications.

From a management point of view, the following points are usually indicated:- . ( Samsung: ), : , , . , .
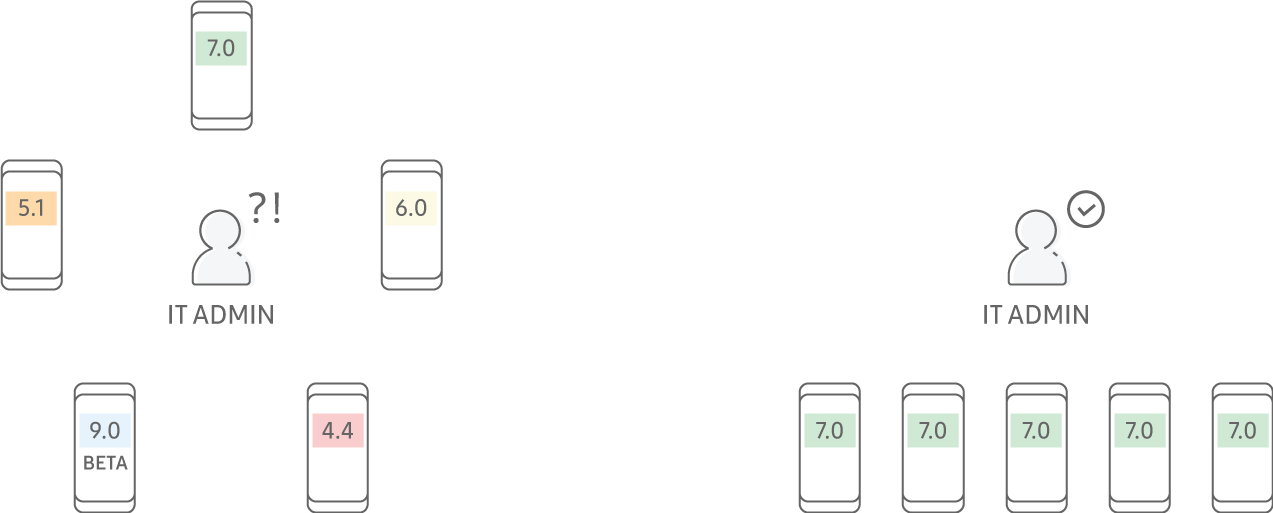
- . , . , , .
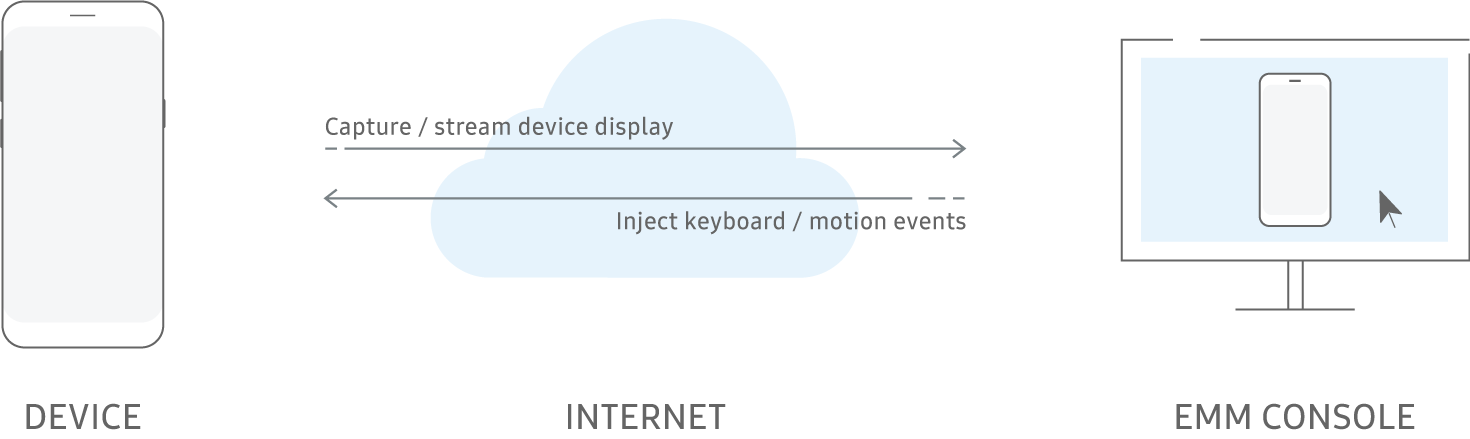
- . , , . , . ( ).
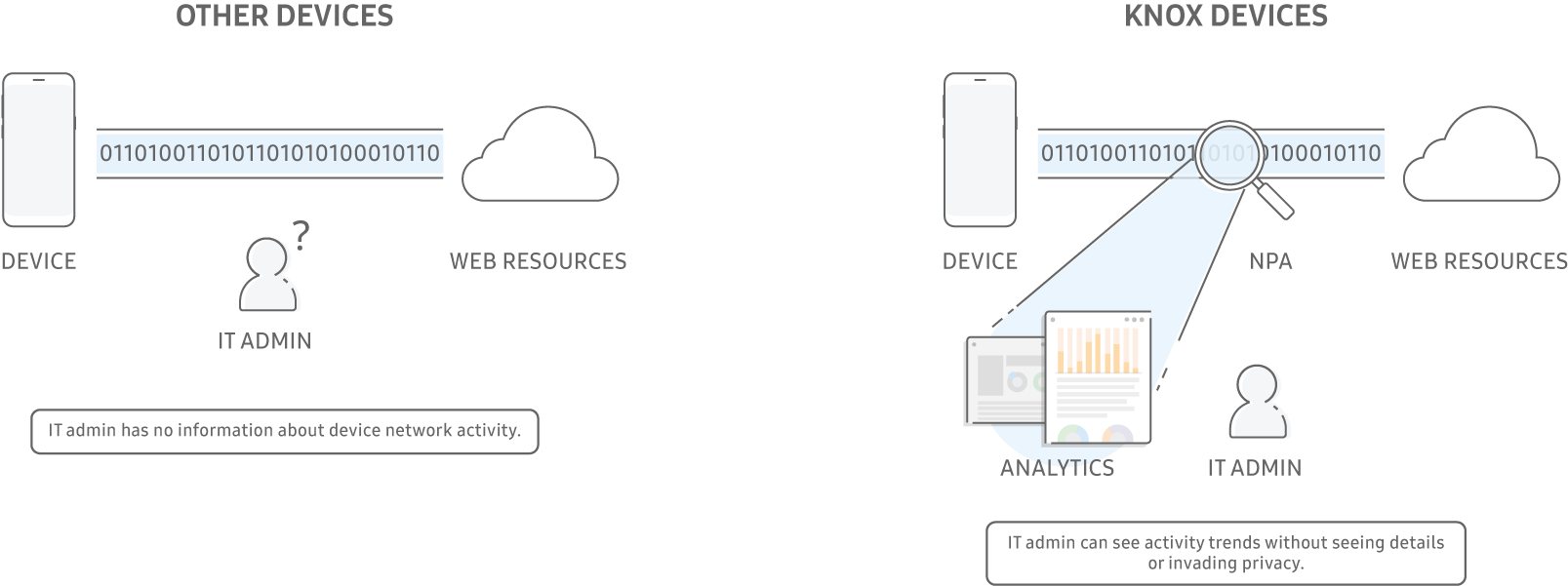
Basically, these are obvious queries. But to realize them is not always possible due to the limited capabilities of different platforms. At one time, Knox Platform For Enterprise , a kind of Knox platform for corporate tasks, helped us a lot in solving these problems. KPfE is a set of tools (SDKs, utilities, web services and device hardware mechanisms) that extends the capabilities of the standard Android OS in terms of management and monitoring. Conveniently, to use the functionality it is not necessary to write a lot of code, there is an option for using Knox Service Plugin , which is configured using OEMConfig (the standard Android for Enterprise mechanism).At the Russian office of Samsung there are specialists who provide assistance in this area, we turn to them with difficult questions. This is a rarity today: more often on development issues you have to communicate with colleagues from India or China, which is quite difficult due to the language barrier and time zone difference.Finally, I would like to talk about the Russian market. Do the projects implemented in our country have any specifics?
The Russian market is slightly behind global trends. Our corporate mobility is in the making. Because of this, generally accepted decisions so far seem alien and inapplicable.The clearest example of such prejudice is the cloud. Often, customers categorically refuse to use this approach, arguing the decision with a lack of confidence in the security and reliability of such systems. This point of view, in our opinion, is no longer relevant today. “Cloudy” does not mean “unreliable” or “unsafe”. This is proved by the experience of many large companies that have entrusted the clouds with a significant part of their business processes - Netflix, Spotify, and a number of others. The fact that the service will be deployed at your site does not guarantee that it will always work. In fact, few can afford to maintain in their server conditions comparable to a certified and certified data center . Software support is a separate line - any system consists of a large number of “invisible” components (OS, database, web server, etc.) that require constant support and regular updates. Summing up: own infrastructure is expensive and troublesome and, unfortunately, not always reliable. The cloud is much cheaper, and all the support and updating work is undertaken by the service provider.Separately, it is worth noting the requirements for certification of decisions made by regulators, for example, for working with personal data. There is an opinion that this is not possible on Android. Our experience shows that in combination with certified security tools, this is possible even in organizations with strict regulations.(from the author) We hope that we have managed to dispel some of the "horror stories", and at least it will now become clear that in life everything is somewhat more complicated than in this comic: Source: Dilbert
Source: Dilbert Asked questions:
Asked questions:
Vladimir Karacharov,
Manager, B2B Pre / Post Sales
Business Development Team
Samsung R&D Institute Russia
 Answered:
Answered:
Oleg Assur,
Chief Engineer,
Research Institute of SOKB