Often I read the opinion that keeping the RDP (Remote Desktop Protocol) port open on the Internet is very insecure, and you don’t need to. And you need to give access to RDP either through a VPN, or only from certain "white" IP addresses.
I administer several Windows Server for small companies, in which I was tasked with providing remote access to Windows Server for accountants. Such a modern trend is work from home. Quickly enough, I realized that tormenting VPN accountants is a thankless task, and collecting all the IPs for the whitelist will not work, because the IP addresses of the people are dynamic.
So I went the simplest way - I forwarded the RDP port out. Now, for access, accountants need to run RDP and enter the host name (including port), username and password.
In this article I will share my experience (positive and not so good) and recommendations.
The risks
What are the risks of opening the RDP port?
1) Unauthorized access to sensitive data.
If someone selects a password for RDP, he will be able to get the data that you want to keep private: account status, balances, customer data, ...
2) Data loss, for
example, as a result of the operation of a cryptographic virus.
Or targeted action by an attacker.
3) Loss of the workstation.
Workers need to work, and the system is compromised, you need to reinstall / restore / configure.
4) Compromise of the local network
If an attacker gained access to a Windows computer, then from that computer he will be able to access systems that are not accessible from the outside, from the Internet. For example to file balls, to network printers, etc.
I had a case when Windows Server caught a cryptorC:, NAS . NAS Synology, snapshots, NAS 5 , Windows Server .
Windows Servers Winlogbeat, ElasticSearch. Kibana , .
, .
:
a) RDP -.
RDP 3389, 443 — HTTPS. , , . :
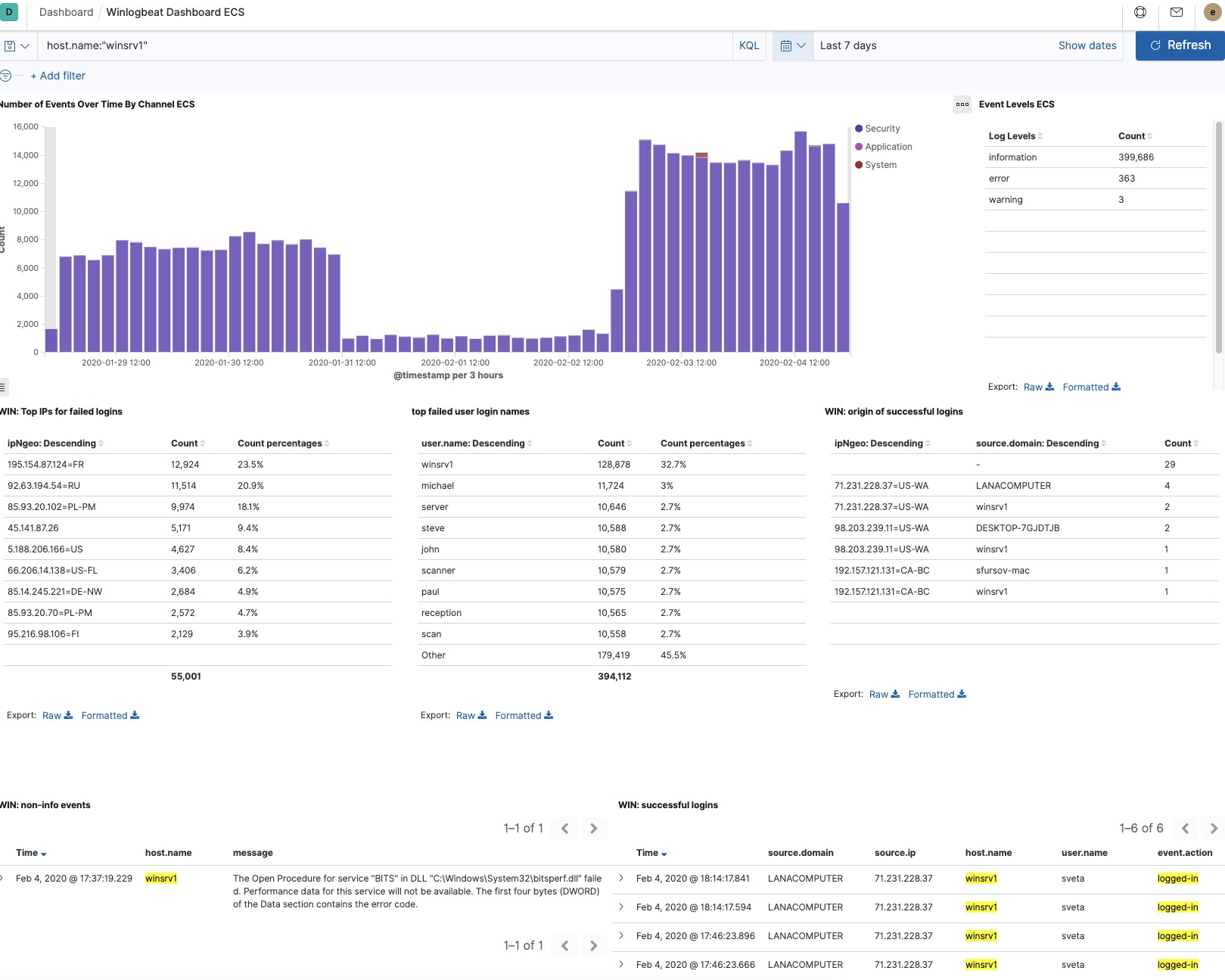
, 400 000 RDP.
, 55 001 IP ( IP ).
, fail2ban,
Update: , 443 — , (32000+), 443 , RDP — .
Update: , :
https://github.com/digitalruby/ipban
IPBan, :

IPBan2020-02-11 00:01:18.2517|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.228,, RDP, 1
2020-02-11 00:01:18.2686|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.228, Administrator, RDP, 2
2020-02-11 00:02:49.7098|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147,, RDP, 3
2020-02-11 00:02:49.7098|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147, Administrator, RDP, 4
2020-02-11 00:04:20.9878|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.184.20,, RDP, 5
2020-02-11 00:04:20.9878|WARN|DigitalRuby.IPBanCore.Logger|Banning ip address: 95.213.184.20, user name:, config black listed: False, count: 5, extra info:
2020-02-11 00:04:20.9878|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.184.20, Administrator, RDP, 5
2020-02-11 00:04:21.0040|WARN|DigitalRuby.IPBanCore.Logger|IP 95.213.184.20, Administrator, RDP ban pending.
2020-02-11 00:04:21.1237|WARN|DigitalRuby.IPBanCore.Logger|Updating firewall with 1 entries…
2020-02-11 00:05:36.6525|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.24,, RDP, 3
2020-02-11 00:05:36.6566|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 31.131.251.24, Administrator, RDP, 4
2020-02-11 00:07:22.4729|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 82.202.249.225, Administrator, RDP, 3
2020-02-11 00:07:22.4894|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 82.202.249.225,, RDP, 4
2020-02-11 00:08:53.1731|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 45.141.86.141,, RDP, 3
2020-02-11 00:08:53.1731|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 45.141.86.141, Administrator, RDP, 4
2020-02-11 00:09:23.4981|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 68.129.202.154,, RDP, 1
2020-02-11 00:09:23.5022|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 68.129.202.154, ADMINISTRATOR, RDP, 2
2020-02-11 00:10:39.0282|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147,, RDP, 5
2020-02-11 00:10:39.0336|WARN|DigitalRuby.IPBanCore.Logger|Banning ip address: 95.213.143.147, user name:, config black listed: False, count: 5, extra info:
2020-02-11 00:10:39.0336|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 95.213.143.147, Administrator, RDP, 5
2020-02-11 00:10:39.0336|WARN|DigitalRuby.IPBanCore.Logger|IP 95.213.143.147, Administrator, RDP ban pending.
2020-02-11 00:10:39.1155|WARN|DigitalRuby.IPBanCore.Logger|Updating firewall with 1 entries…
2020-02-11 00:12:09.6470|WARN|DigitalRuby.IPBanCore.Logger|Login failure: 82.202.249.225,, RDP, 5
2020-02-11 00:12:09.6470|WARN|DigitalRuby.IPBanCore.Logger|Banning ip address: 82.202.249.225, user name:, config black listed: False, count: 5, extra info:
b) username,
, .
: — , . : . , - : DESKTOP-DFTHD7C DFTHD7C:
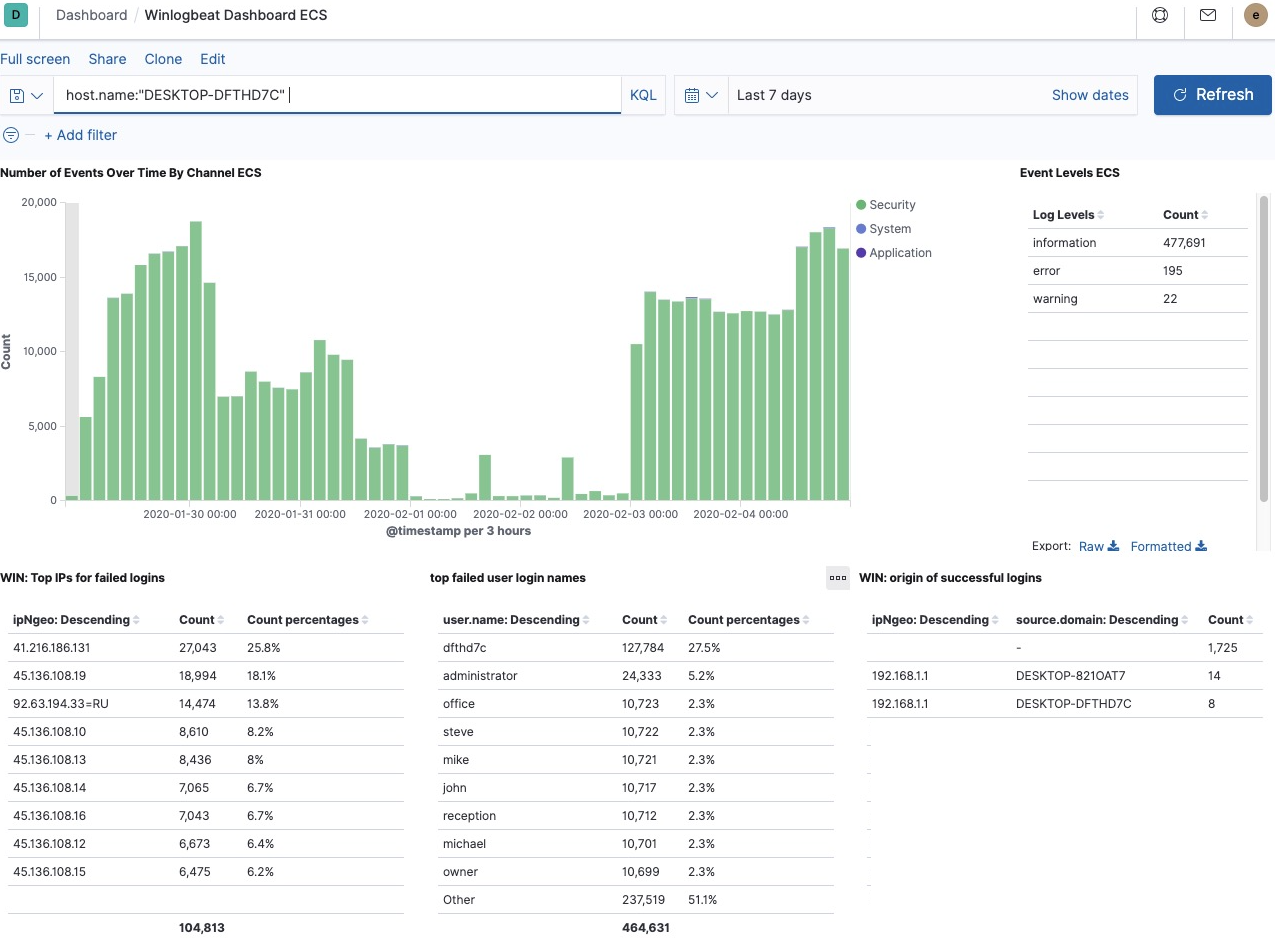
, DESKTOP-MARIA, MARIA.
, : , — "administrator". , Windows, .
- .https://docs.microsoft.com/en-us/windows/security/identity-protection/access-control/local-accounts#administrator-account
Administrator account
The default local Administrator account is a user account for the system administrator. Every computer has an Administrator account (SID S-1-5-domain-500, display name Administrator). The Administrator account is the first account that is created during the Windows installation.
The Administrator account has full control of the files, directories, services, and other resources on the local computer. The Administrator account can create other local users, assign user rights, and assign permissions. The Administrator account can take control of local resources at any time simply by changing the user rights and permissions.
The default Administrator account cannot be deleted or locked out, but it can be renamed or disabled.
: .
, Administrator Murmansk#9. , , , , — .
Administrator , ? !
:
, , Windows Server - - , .
, ?
, RDP, :
— .
, - IP - , IP ( ) PowerShell:
New-NetFirewallRule -Direction Inbound -DisplayName "fail2ban" -Name "fail2ban" -RemoteAddress ("185.143.0.0/16", "185.153.0.0/16", "193.188.0.0/16") -Action Block
Elastic, Winlogbeat Auditbeat, . SIEM (Security Information & Event Management) Kibana. , — Auditbeat Linux , SIEM .
:
- .
- put Security Updates on time
Bonus: a list of 50 users who were most often used for login attempts via RDP