Security Week 06: advertising trackers in mobile applications
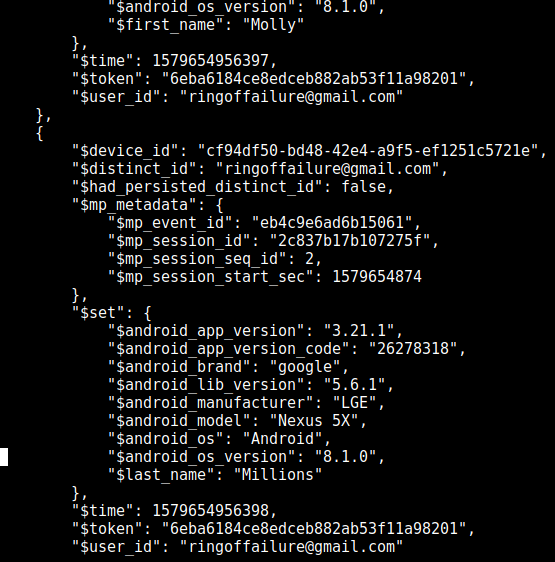
The Amazon Ring smart doorbell mobile application sends detailed user information to three companies at once, collecting information for subsequent advertising targeting, as well as to the Facebook social network. These are the results of a study conducted by the Electronic Frontiers Foundation ( news , original article ). The results of the EFF analysis cannot be called a shocking discovery: the majority of mobile applications supply data to ad networks in one way or another. Of interest is the method of decrypting the data, as well as the type of application under study. Unlike any other scenarios, here we are talking about working with a personal surveillance camera. Such interaction, in theory, should occur with a maximum level of privacy.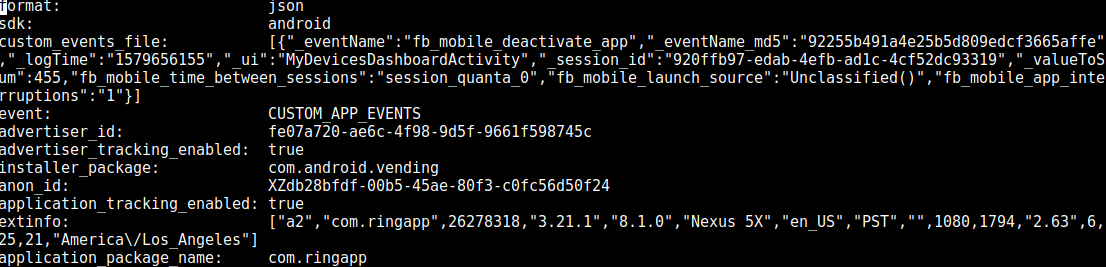
Source: https://habr.com/ru/post/undefined/
All Articles