Diagnosing network connections on a virtual EDGE router
In some cases, there may be problems setting up a virtual router. For example, port forwarding (NAT) and / or a problem in configuring the Firewall rules themselves do not work. Or you just need to get the logs of the router, check the channel, conduct network diagnostics. How this is done, says cloud provider Cloud4Y.Work with a virtual router
First of all, we need to configure access to the virtual router - EDGE. To do this, enter its services and go to the appropriate tab - EDGE Settings. There we enable SSH Status, set a password, and be sure to save the changes.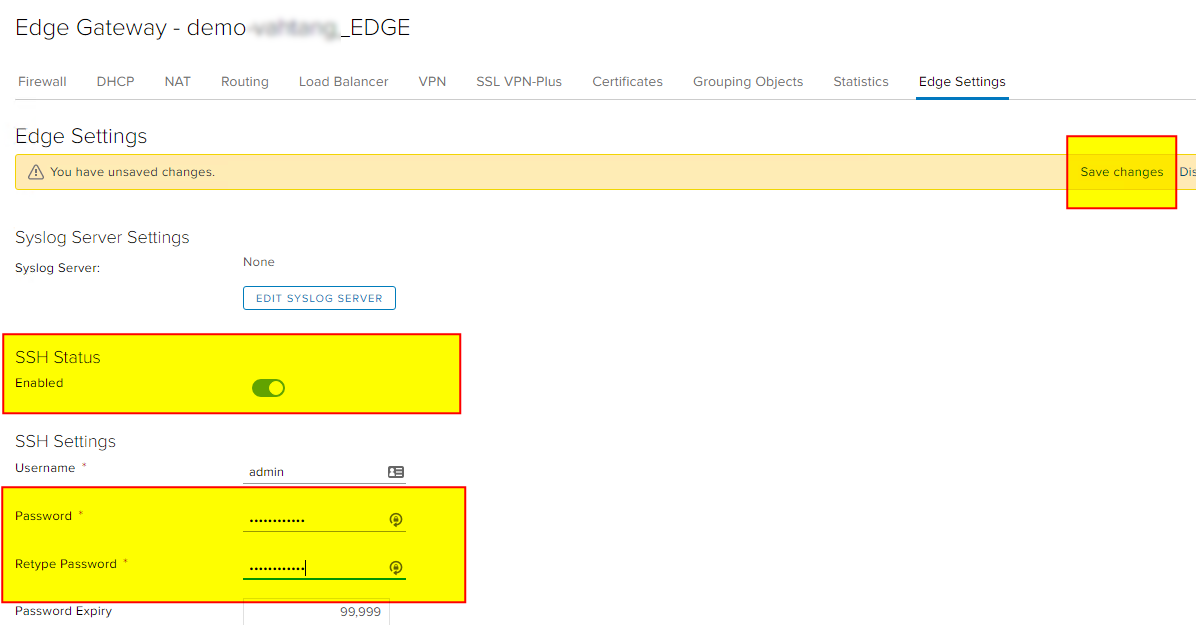 If we use strict Firewall rules, when everything is disabled by default, we add rules that allow connections to the router itself via the SSH port:
If we use strict Firewall rules, when everything is disabled by default, we add rules that allow connections to the router itself via the SSH port: After we connect to any SSH client, for example PuTTY, we get to the console.
After we connect to any SSH client, for example PuTTY, we get to the console. In the console, commands are available to us, a list of which can be seen using:list
In the console, commands are available to us, a list of which can be seen using:list What commands can be useful to us? Here is a list of the most useful:
What commands can be useful to us? Here is a list of the most useful:- show interface - displays the available interfaces and the set IP addresses on them
- show log - show router logs
- show log follow — . , NAT Fierwall, Enable logging, , .
- show flowtable —
1: tcp 6 21599 ESTABLISHED src=9.107.69. dst=178.170.172.XXX sport=59365 dport=22 pkts=293 bytes=22496 src=178.170.172. dst=91.107.69.173 sport=22 dport=59365 pkts=206 bytes=83569 [ASSURED] mark=0 rid=133427 use=1
- show flowtable topN 10 — , 10
- show flowtable topN 10 sort-by pkts —
- show flowtable topN 10 sort-by bytes — bytes
- show flowtable rule-id ID topN 10 - helps to display connections by the desired rule ID
- show flowtable flowspec SPEC - for a more flexible connection selection, where SPEC - sets the necessary filtering rules, for example proto = tcp: srcip = 9X.107.69.XXX: sport = 59365, for selection via TCP protocol and source IP address 9X.107.69.XX from sender port 59365
Example> show flowtable flowspec proto=tcp:srcip=90.107.69.171:sport=59365
1: tcp 6 21599 ESTABLISHED src=9.107.69.XX dst=178.170.172.xxx sport=59365 dport=22 pkts=1659 bytes=135488 src=178.170.172.xxx dst=xx.107.69.xxx sport=22 dport=59365 pkts=1193 bytes=210361 [ASSURED] mark=0 rid=133427 use=1
Total flows: 1
- show packet drops - allows you to see packet statistics

- show firewall flows - shows the firewall packet counters along with the packet flows.

We can also use the main network diagnostic tools directly from the EDGE router:- ping ip WORD

- ping ip WORD size SIZE count COUNT nofrag – , .
- traceroute ip WORD

Firewall Edge
- show firewall usr_rules
- POSTROUTIN DROP. .
:
- IP- — show ipset
- firewall Edge
- — show log follow
- rule_id — show flowtable rule_id
- show flowstats Current Flow Entries (Total Flow Capacity) . VMware NSX Edge. , , .
What else can you read on Cloud4Y's blog→ CRISPR-resistant viruses build shelters to protect genomes from DNA-penetrating enzymes→ How the bank “broke”→ The Great Snowflake Theory→ Internet on balloons→ Pentesters at the forefront of cybersecuritySubscribe to our Telegram - channel, so as not to miss another article! We write no more than twice a week and only on business. We remind you that startups can get 1 million rubles. from Cloud4Y. Terms and conditions for those who wish - on our website: bit.ly/2sj6dPK Source: https://habr.com/ru/post/undefined/
All Articles