Icloud phishers and where do they live
Attention! Despite the fact that I spent more than a dozen hours working on this article, but you can still participate in it.If your hands itch - try to master this text.The story is more like a comic book, as it contains more than 50 images, so it’s more accurate if you are using a mobile phone. And also - 152-FZ is most likely violated here, so I won’t be surprised if it is deleted, so read faster. This story has no end, but it has a beginning ...And it begins in 2017, when the " Information Danger " channel posted the following content on the post: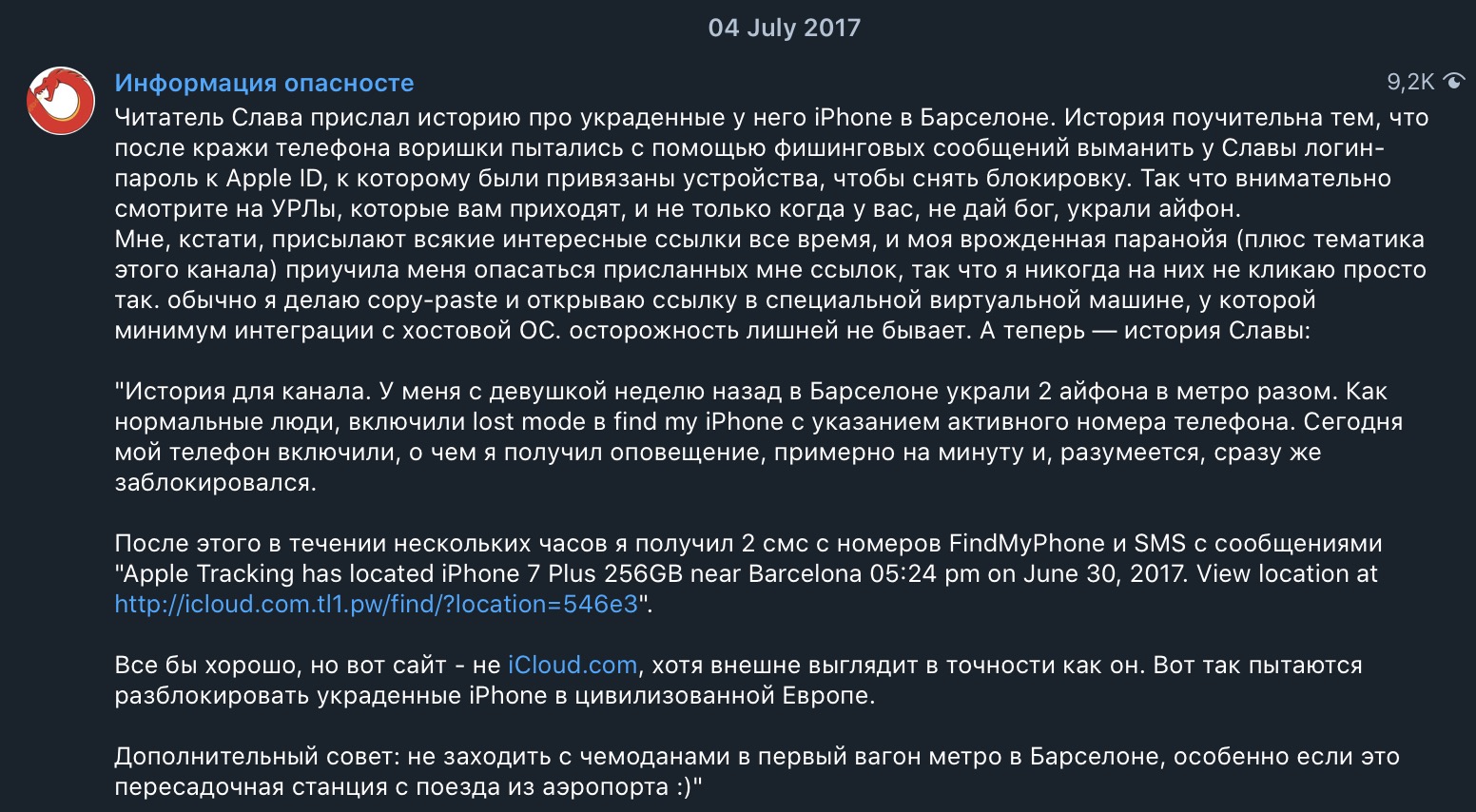 I was curious what kind of fake this is? What kind of engine, how it works and how advanced are phishers (well, you never mind, maybe again php script on free / cheap vps, as in 1732)?It turned out that the truth: scattered php scripts, admin panel, fake templates.Having studied this host, vulnerabilities led me to get the admin panel, and then to execute arbitrary code. As a result - I got access to the database, logs and of course to the source. Oh yes, I do information security (pentests and all that).As it turned out, this gave an impetus to the study of several dozen of the same resources and gave rise to the story that you are reading now.What's happening? The phone is stolen from the victim. If Android, then most often it can immediately be sold as an independent: pulled out a SIM card, rutanul, and already on Avito. But there are some nuances: such as a login password, a bootloader is blocked - but this is a completely different story.But with iPhones it’s already much more complicated, since the inclusion password is the most common condition. And the owner can block the device by leaving a contact number. Like, lost, please return for a reward. Take and flash it will not work, so either for parts (the cost of an iPhone is then lost several times) or suffer.However, with the development of protection technologies, fraud always develops, so the way for thieves was to send phishing to the victim’s contact number. And what? Conveniently. The victim leaves her contacts herself, you just have to introduce yourself as Apple and force the user to enter data from icloud to enter the user.
I was curious what kind of fake this is? What kind of engine, how it works and how advanced are phishers (well, you never mind, maybe again php script on free / cheap vps, as in 1732)?It turned out that the truth: scattered php scripts, admin panel, fake templates.Having studied this host, vulnerabilities led me to get the admin panel, and then to execute arbitrary code. As a result - I got access to the database, logs and of course to the source. Oh yes, I do information security (pentests and all that).As it turned out, this gave an impetus to the study of several dozen of the same resources and gave rise to the story that you are reading now.What's happening? The phone is stolen from the victim. If Android, then most often it can immediately be sold as an independent: pulled out a SIM card, rutanul, and already on Avito. But there are some nuances: such as a login password, a bootloader is blocked - but this is a completely different story.But with iPhones it’s already much more complicated, since the inclusion password is the most common condition. And the owner can block the device by leaving a contact number. Like, lost, please return for a reward. Take and flash it will not work, so either for parts (the cost of an iPhone is then lost several times) or suffer.However, with the development of protection technologies, fraud always develops, so the way for thieves was to send phishing to the victim’s contact number. And what? Conveniently. The victim leaves her contacts herself, you just have to introduce yourself as Apple and force the user to enter data from icloud to enter the user. Despite the fact that the popularity of such phishing grew in 2017, one of the first screenshots of such a service was made back in 2015 .At first they sent it to beautiful domains like lcloud.com (not to be confused with icloud), but when they realized that they were being closed, they started to act easier. On beautiful domains have redirect services that make a short link. It’s more difficult to close such ones - they didn’t post anything illegal. Just a short link service with the name mimicking under apple or icloud.After going through it, you will see an adaptive form of authentication, which loads even faster than icloud.com. Or maybe immediately the card itself, in order to warm up your interest, with a further authentication request.Just don’t say that it’s you who are so smart, and you wouldn’t be led to such a thing. When you lose an expensive thing, and then there is a chance that it was found, you can do stupid things in a state of shock. But here, and how lucky with the domain: maybe the eye will catch on a suspicious place, or maybe it will be indistinguishable from the original, for example, as this dude did using Punycode.“Two-factor authentication,” you say. Well, yes, only phishers have long learned to show the two-factor input form (think, another php script).What do they do after they access icloud? In the best case, they untie the phone. In the worst case, they block all other Apple devices (because you can also leave the laptop somewhere, so this feature is present). Only in this situation, you change sides, on your favorite laptop with a stub will appear the scammer and contacts to unlock. And there is already how to agree :)By the way, one of the employees of Kaspersky Lab in this way “squeezed” the phone. An article story about how this comes from the person of the victim . But if you still did not fall for phishing - you will continue to socialize through a call. But more on that later.
Despite the fact that the popularity of such phishing grew in 2017, one of the first screenshots of such a service was made back in 2015 .At first they sent it to beautiful domains like lcloud.com (not to be confused with icloud), but when they realized that they were being closed, they started to act easier. On beautiful domains have redirect services that make a short link. It’s more difficult to close such ones - they didn’t post anything illegal. Just a short link service with the name mimicking under apple or icloud.After going through it, you will see an adaptive form of authentication, which loads even faster than icloud.com. Or maybe immediately the card itself, in order to warm up your interest, with a further authentication request.Just don’t say that it’s you who are so smart, and you wouldn’t be led to such a thing. When you lose an expensive thing, and then there is a chance that it was found, you can do stupid things in a state of shock. But here, and how lucky with the domain: maybe the eye will catch on a suspicious place, or maybe it will be indistinguishable from the original, for example, as this dude did using Punycode.“Two-factor authentication,” you say. Well, yes, only phishers have long learned to show the two-factor input form (think, another php script).What do they do after they access icloud? In the best case, they untie the phone. In the worst case, they block all other Apple devices (because you can also leave the laptop somewhere, so this feature is present). Only in this situation, you change sides, on your favorite laptop with a stub will appear the scammer and contacts to unlock. And there is already how to agree :)By the way, one of the employees of Kaspersky Lab in this way “squeezed” the phone. An article story about how this comes from the person of the victim . But if you still did not fall for phishing - you will continue to socialize through a call. But more on that later.International SaaS for Thieves
So, what kind of disgust is this.In fact, there are many systems, one was sawn down on the Laravel engine, the others are a group of AppleKit , MagicApp , Phantom , Phoenix , iPanel Pro and more primitive crafts . All of them will be chopped off with their marijuana and fork each other, competing with whom the logo is better. And the funny thing is that inheriting someone else’s code, they inherit other people's vulnerabilities and backdoors.Just in case, taking care that the found bugs can be read in the article and fixed, I will not give examples. There are suspicions that the creators of at least the Phoenix panels accurately understand in Russian.But as a bonus - I'll post the source code. Authors have source codes! And you will see bugs (and backdoors) yourself.Once the dudes realized that the thieves themselves do not rummage in IT, so raising a fake, sending SMS is an impossible task. And since all roads lead to the master by phone (who else can sell spare parts?), He can also help his customers unlock the cell phone or by buying a stolen iPhone at a low price to raise it in price, having worked a bit on it.Earn it all. Renting a service costs $ 150-350 (per month), they give you installation instructions , you buy a domain, drive orders, and the system will do the rest. Then for $ 100-150 you sell this “unlock”.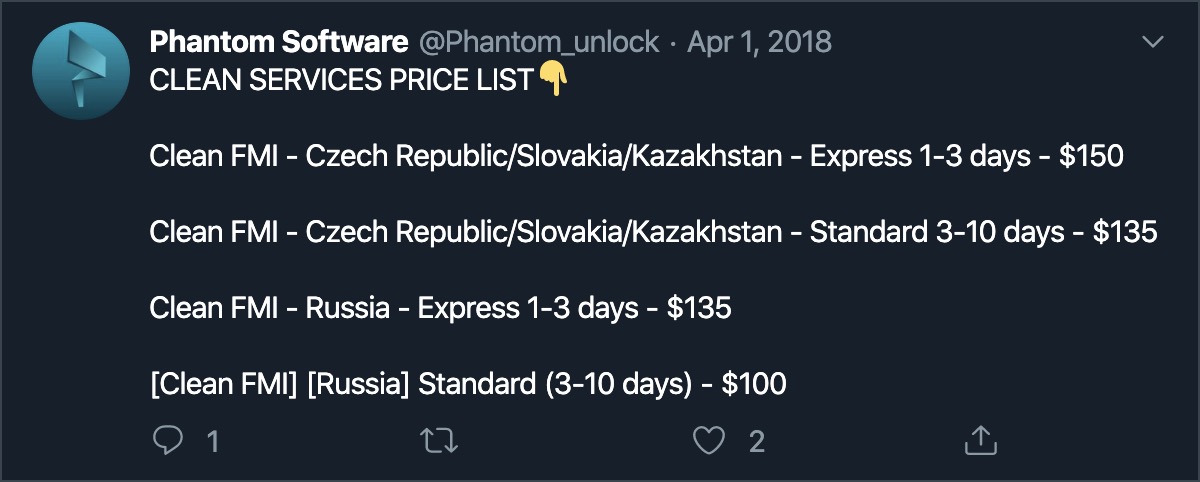 In the west, iPanel is more popular, in the CIS countries - Phoenix.How it looks from the side of the phishing admin: The
In the west, iPanel is more popular, in the CIS countries - Phoenix.How it looks from the side of the phishing admin: The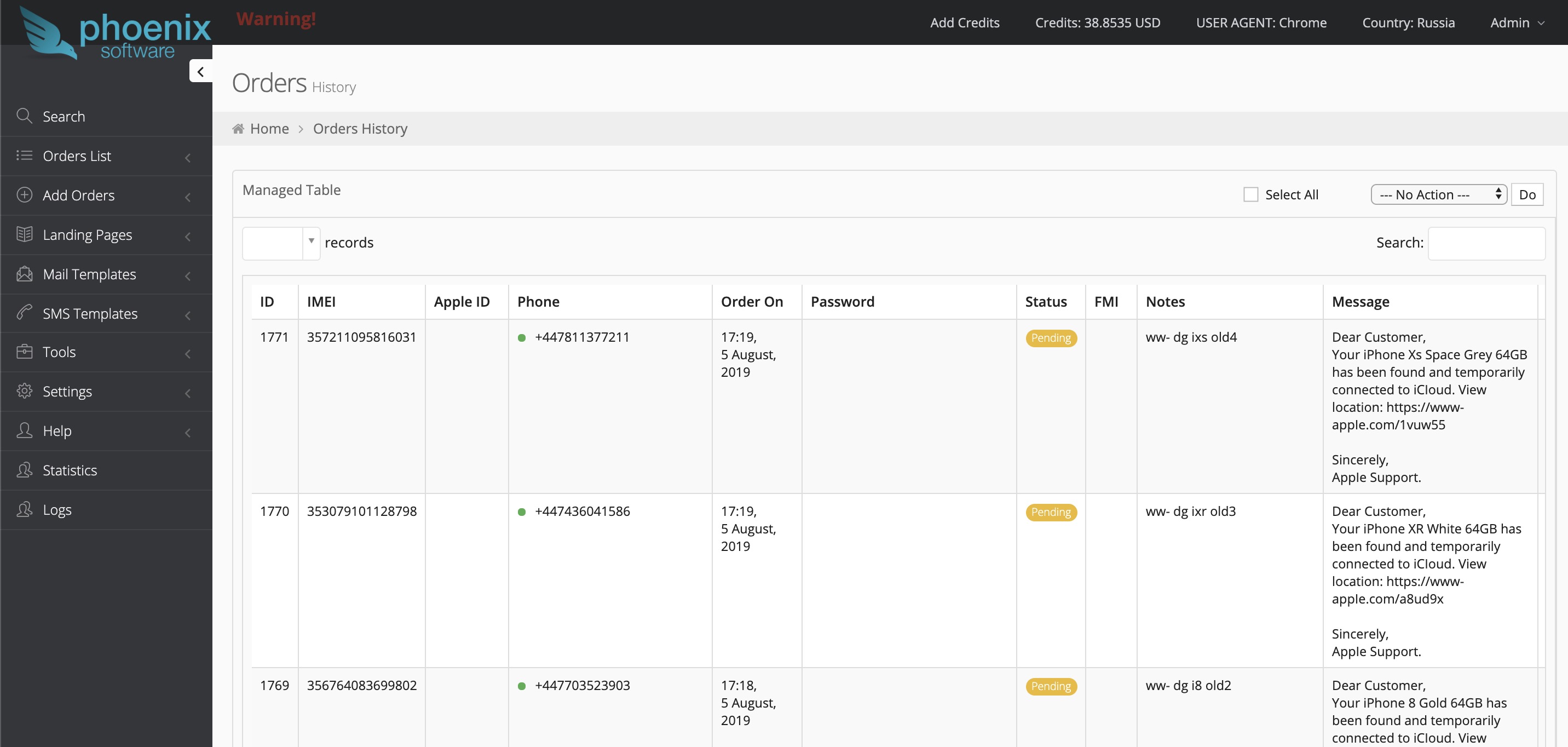 admin can tweak the settings, for example, sending an email after a successful decoupling or notification in Telegram (where without it) and all that stuff.
admin can tweak the settings, for example, sending an email after a successful decoupling or notification in Telegram (where without it) and all that stuff.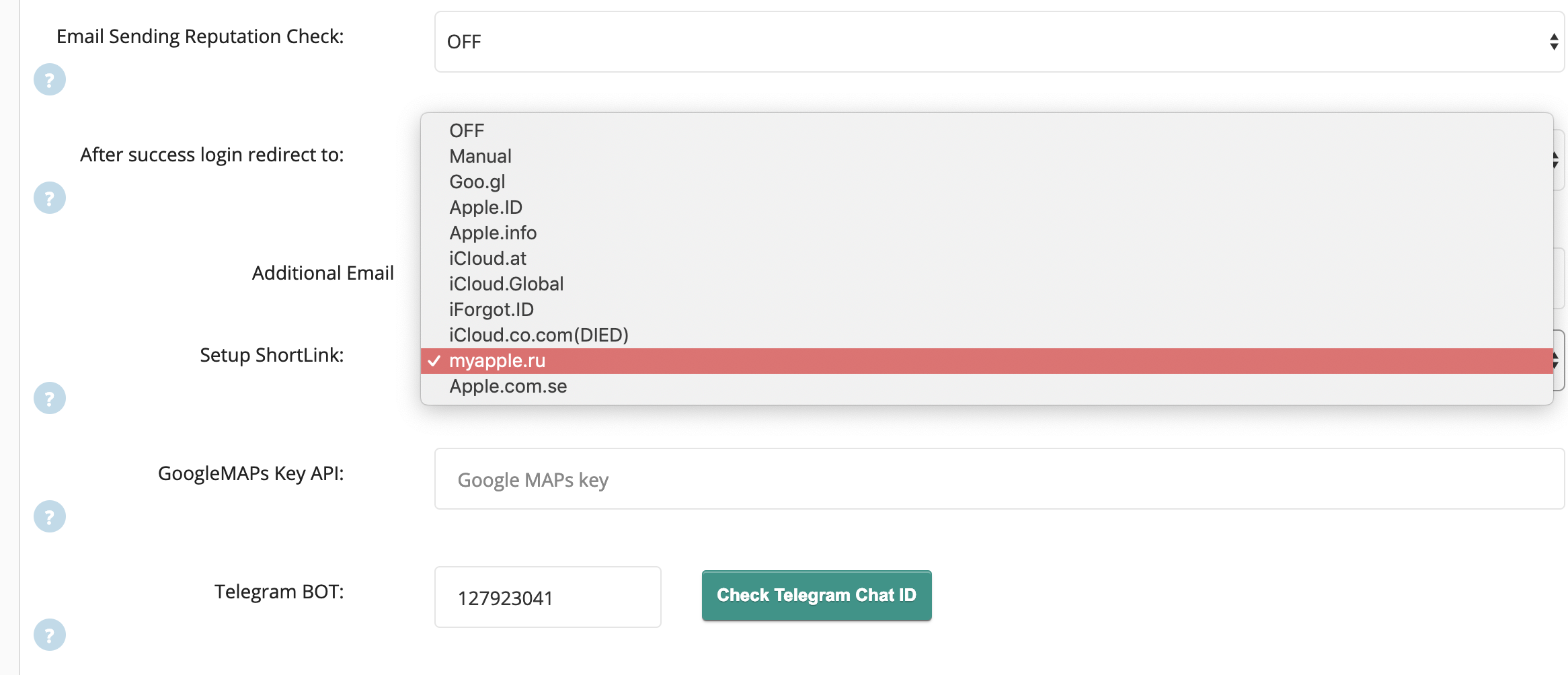 When adding an order, you need to specify which phone and IMEI. Also, he can write a note from whom the order came.
When adding an order, you need to specify which phone and IMEI. Also, he can write a note from whom the order came. Often you can see something like Jack Wazap or Kolya Lysy, which is somewhat amusing. As you know, the physical availability of the phone is not necessary at all, therefore the service is being promoted on the Internet, and you can work with it remotely.
Often you can see something like Jack Wazap or Kolya Lysy, which is somewhat amusing. As you know, the physical availability of the phone is not necessary at all, therefore the service is being promoted on the Internet, and you can work with it remotely. SMS will deliver the language itself.You can also choose the type of phishing design, for example, from the following options:
SMS will deliver the language itself.You can also choose the type of phishing design, for example, from the following options: Everything is quite adaptive and looks good on both phones and desktop. Sometimes the number and type of pages varies, but not significantly.
Everything is quite adaptive and looks good on both phones and desktop. Sometimes the number and type of pages varies, but not significantly. Entrance to the admin panel is different for everyone. But this is a deceptive sensation, since for the most part these are forks of Phoenix or iPanel Pro, and the interface inside is the same, except that logos and, sometimes, colors change.
Entrance to the admin panel is different for everyone. But this is a deceptive sensation, since for the most part these are forks of Phoenix or iPanel Pro, and the interface inside is the same, except that logos and, sometimes, colors change.
Backdoors
Did I say they leave backdoors? Oh yes ...iPanel is generally funny! Check it out. IPanel has an automatic installation. Since the system is intended for installation on hosting with a control panel (such as cpanel), you need to specify a logopas for it. And during installation, you will have a default password for the DBMS:
IPanel has an automatic installation. Since the system is intended for installation on hosting with a control panel (such as cpanel), you need to specify a logopas for it. And during installation, you will have a default password for the DBMS: ipanel@789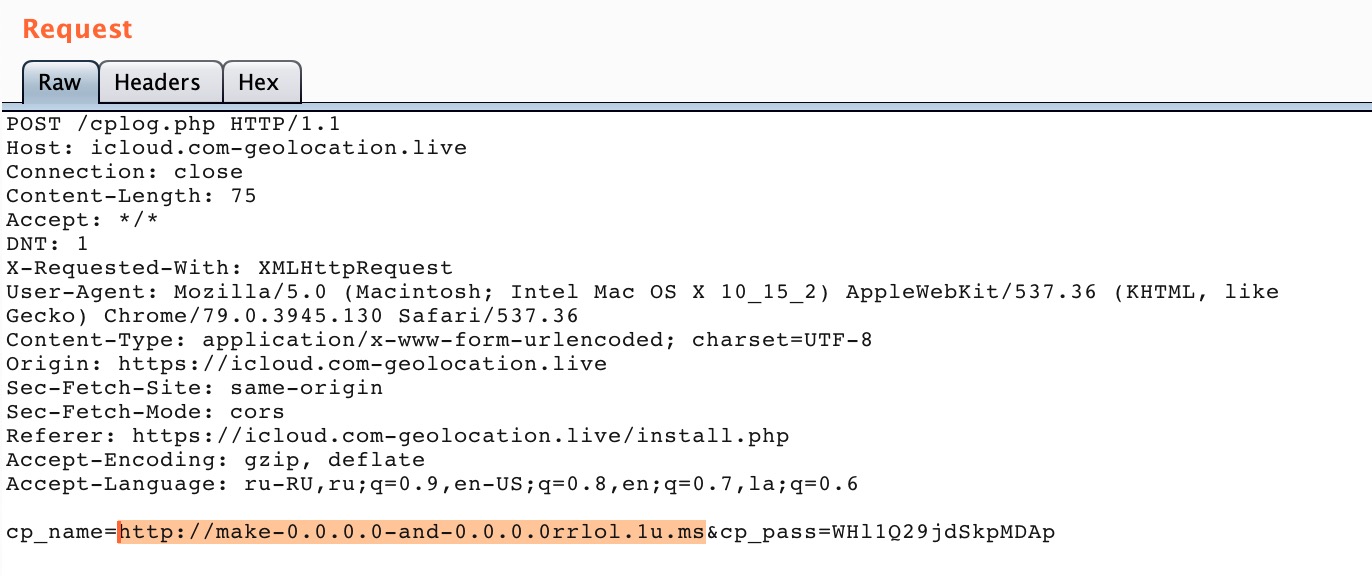 If you send a link as a login or password and listen to the port, we will see how it knocks on us.
If you send a link as a login or password and listen to the port, we will see how it knocks on us.23 Jan [14:35:48] from 149.154.161.4 HTTP: / [] (TelegramBot (like TwitterBot)) euConsent=true; BCPermissionLevel=PERSONAL; BC_GDPR=11111; fhCookieConsent=true; gdpr-source=GB; gdpr_consent=YES; beget=begetokThis indicates that the username and password have flown to someone in carts. But it’s convenient!Another proof of the presence of backdoors can be the logs that leave a trace of errors: Let's see what we have there. Ereg_replace and eval? My friend, you have RCE (but it’s not accurate)!And why no one sees? Code is obfuscated using ioncube. And the panel has a license check, did not pay - litter dude. It turns out that the panel owner gives out his obfuscated code to everyone, they knock on his server (ph-phoenix.com in case of a phoenix), and he can break into it at any time. Well, arrogance)But I wasn’t confused ️️️ and partially cut the code (I spent as much as 10 bucks).Sources were merged, a database dump was made. But all this was forgotten for several years.
Let's see what we have there. Ereg_replace and eval? My friend, you have RCE (but it’s not accurate)!And why no one sees? Code is obfuscated using ioncube. And the panel has a license check, did not pay - litter dude. It turns out that the panel owner gives out his obfuscated code to everyone, they knock on his server (ph-phoenix.com in case of a phoenix), and he can break into it at any time. Well, arrogance)But I wasn’t confused ️️️ and partially cut the code (I spent as much as 10 bucks).Sources were merged, a database dump was made. But all this was forgotten for several years.A year has passed
* the sound of birds singing in the forest *
Two years have passed
The second coming began when my friend, Cyberpunk , had the same story.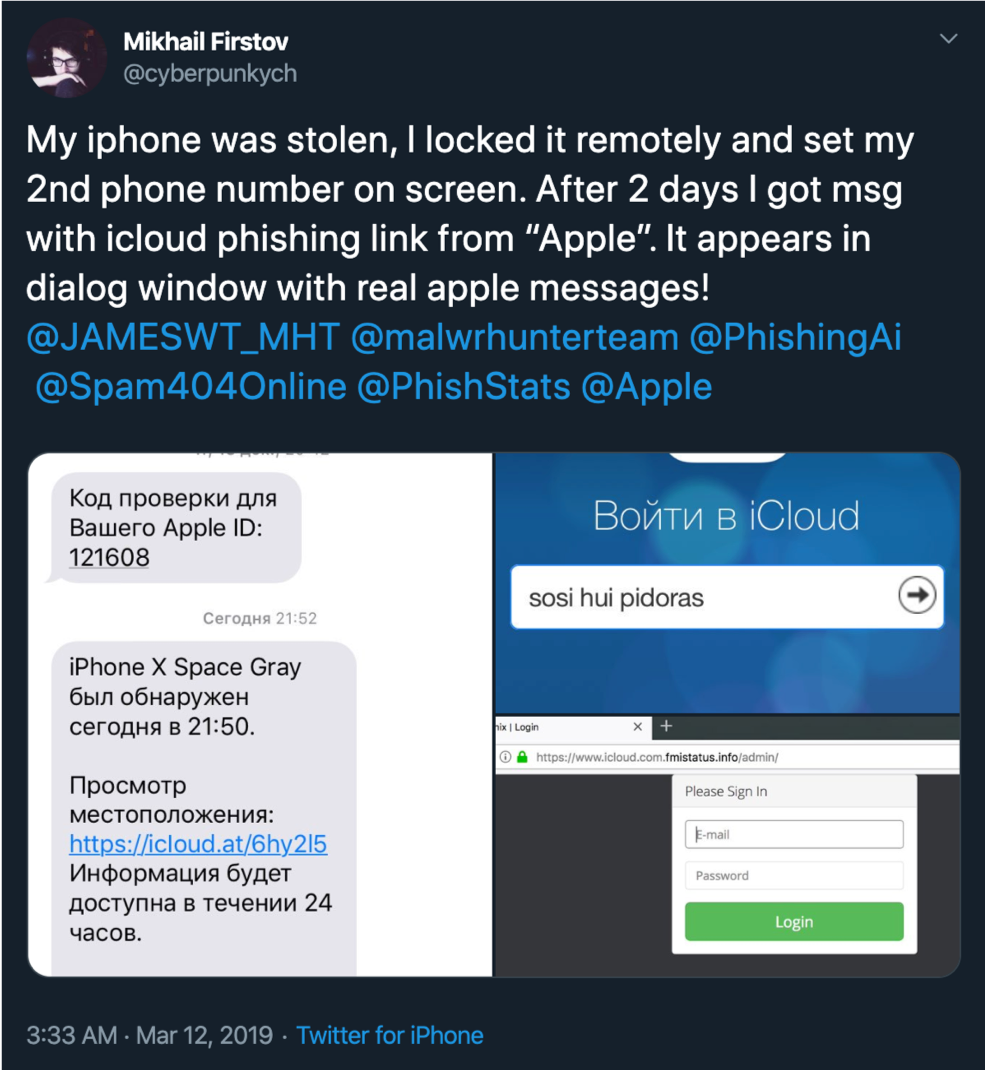 All according to the classical scheme. Theft, blocking, phishing on the domain (this time was icloud.at), which redirects to the panel itself with the domain www.icloud.com.fmistatus.info .
All according to the classical scheme. Theft, blocking, phishing on the domain (this time was icloud.at), which redirects to the panel itself with the domain www.icloud.com.fmistatus.info .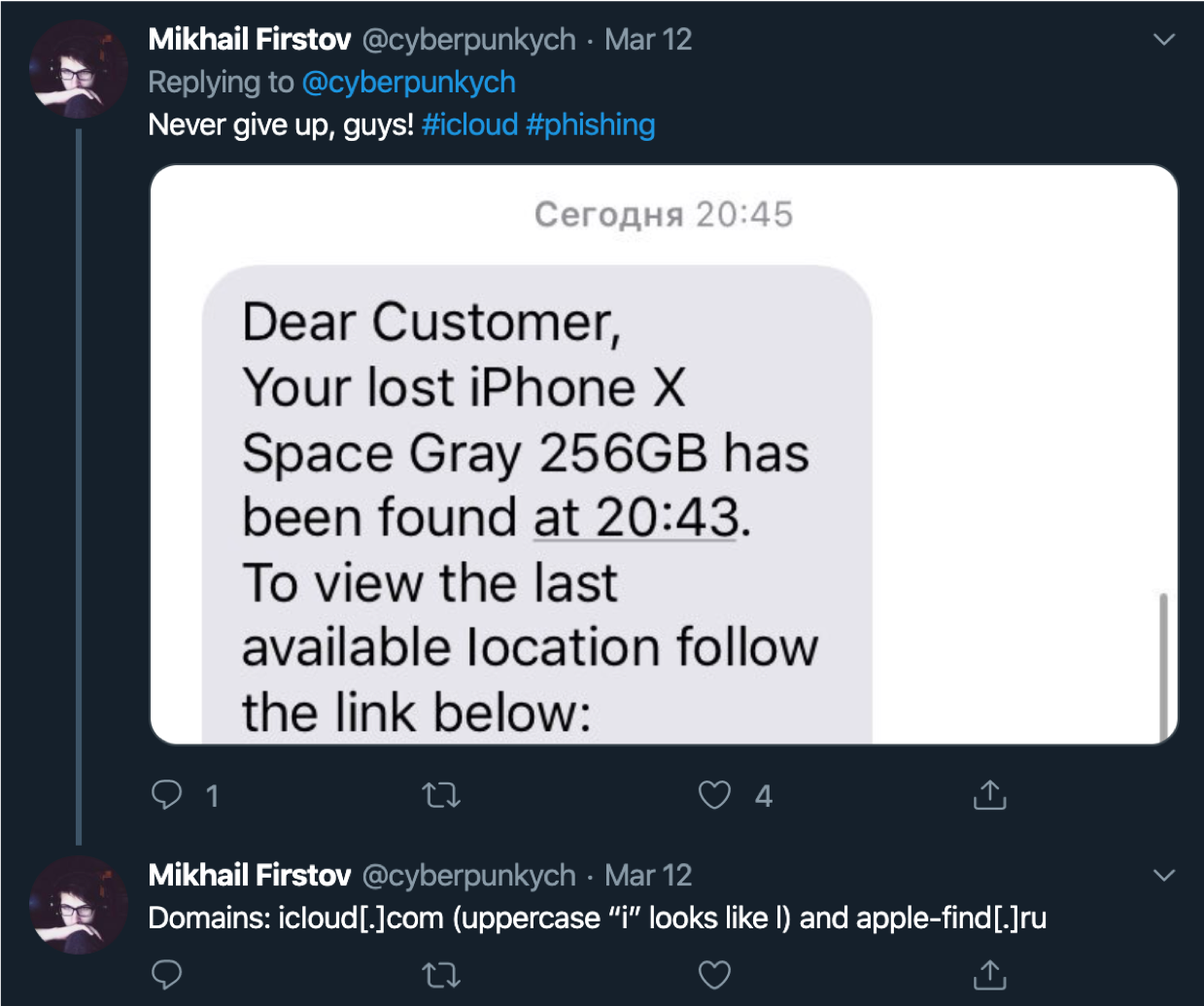 Later that host went blank and an SMS arrived that leads to apple-find.ru.And since the vulnerabilities in this panel were already known to me, phishing was successfully cracked in a short time. His administrator was a certain kolya2017zaza@gmail.com with the password Zaza2015, which, hag, hints that I’m Kolya Zaza, and “my password has not changed since 2015”.But on the Internet there is not a single mention of this account:
Later that host went blank and an SMS arrived that leads to apple-find.ru.And since the vulnerabilities in this panel were already known to me, phishing was successfully cracked in a short time. His administrator was a certain kolya2017zaza@gmail.com with the password Zaza2015, which, hag, hints that I’m Kolya Zaza, and “my password has not changed since 2015”.But on the Internet there is not a single mention of this account:Your search - "kolya2017zaza" - did not match any documents.Sad.We study the base further. We recall the settings; in the database dump, this is the options table.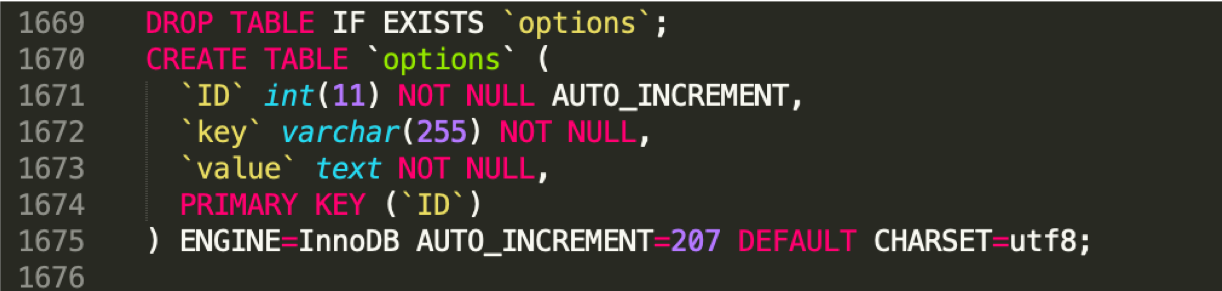 We find there sending notifications from the address ivan89776593244@yandex.ru
We find there sending notifications from the address ivan89776593244@yandex.ru Excellent, then the data is sent from the Yandex server. We go there:
Excellent, then the data is sent from the Yandex server. We go there: I was afraid that the two-factor. But no.Guess what you need to enter in order to get inside?After a successful login, we see that we have alerts from several services. Wow, Vanka is a Muscovite! Interesting indigenous?
I was afraid that the two-factor. But no.Guess what you need to enter in order to get inside?After a successful login, we see that we have alerts from several services. Wow, Vanka is a Muscovite! Interesting indigenous?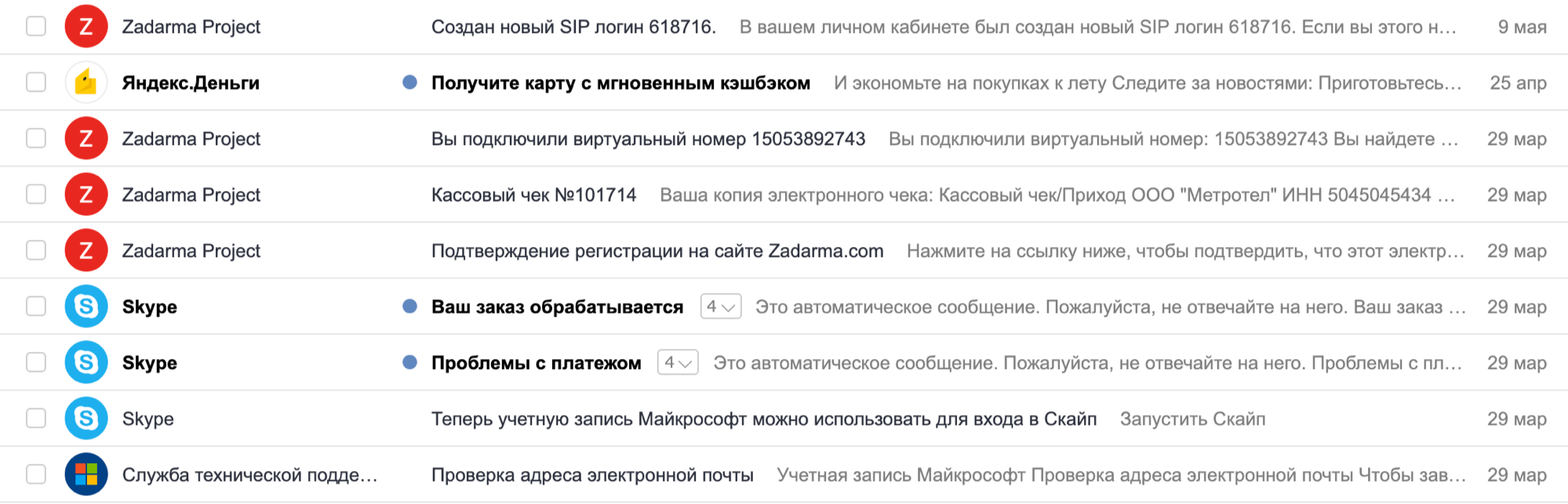 We see one sent letter.
We see one sent letter. By communication, it is clear that the Muscovite is not radical. But not the point.Checking Zadarma (this is a service for renting virtual numbers) - is blocked. Checking Skype - blocked.What are these services for?
By communication, it is clear that the Muscovite is not radical. But not the point.Checking Zadarma (this is a service for renting virtual numbers) - is blocked. Checking Skype - blocked.What are these services for?
If phishing did not work, they call under the guise of a service center employee (or maybe not under the guise). They say that some suspicious type brought a mobile phone, they will need to give it away soon, they are trying to speak their teeth (switch the language to English) and that's all for you to click on the removal of the phone from the loss function.
We go to Yandex Money. We see: the IP address in all operations belongs to Megafon, purchases of Zadarma services, four domains, two phone recharge: Yandex money was replenished through an account in Qiwi. We use the phone “Ivan” and the famous password. He fits here. After all, as you know, stability is a sign of mastery.
We see: the IP address in all operations belongs to Megafon, purchases of Zadarma services, four domains, two phone recharge: Yandex money was replenished through an account in Qiwi. We use the phone “Ivan” and the famous password. He fits here. After all, as you know, stability is a sign of mastery.+7 977 6593244
+7 916 1168710 We find out that the Qiwi wallet was replenished both by using the number +7 977 8667146 (another one-time number) and by using the terminal. In fact, there are more numbers there, I’m just too lazy to look for them in the log (and I saved it, if someone is very interested, kick me).And now I will show a little OSINT trick in QIWI. Each terminal has its own unique identifier. If you go into the payment details and see json, then along with different identifiers there will be an account parameter - this is it!
We find out that the Qiwi wallet was replenished both by using the number +7 977 8667146 (another one-time number) and by using the terminal. In fact, there are more numbers there, I’m just too lazy to look for them in the log (and I saved it, if someone is very interested, kick me).And now I will show a little OSINT trick in QIWI. Each terminal has its own unique identifier. If you go into the payment details and see json, then along with different identifiers there will be an account parameter - this is it! But what to do with it, not to run all over Moscow in search of the terminal number? Qiwi has a nice option for such cases - a terminal map .We walk on the map, look at the arriving identifiers and understand that the terminal is on the Tsaritsyno market.
But what to do with it, not to run all over Moscow in search of the terminal number? Qiwi has a nice option for such cases - a terminal map .We walk on the map, look at the arriving identifiers and understand that the terminal is on the Tsaritsyno market. And also, knowing the terminal number, date and transaction code, you can verify the payment using these data on the check verification page .“And what happened next?” - you ask.And I will answer - nothing.A bunch of left phones, left names, and a market in Tsaritsyno.But so as not to be bored, I decided to continue breaking fakes. But at the same time and see if everything is as neat as KolyaVova, who was trying to steal a friend’s account.
And also, knowing the terminal number, date and transaction code, you can verify the payment using these data on the check verification page .“And what happened next?” - you ask.And I will answer - nothing.A bunch of left phones, left names, and a market in Tsaritsyno.But so as not to be bored, I decided to continue breaking fakes. But at the same time and see if everything is as neat as KolyaVova, who was trying to steal a friend’s account.Man to man is a wolf
Several times I came across email volkbaku@mail.ru on the domains findfindiphone.com and findphonefmi.comI, using the deduction method, suggested that this person was unlikely to be Mexican or Italian.Passwords came across Pass12340 @ and Orxan1313 @.Login is google on the GSM forum, there seems to be no more interesting. And by mail you can see the social network mailru
And by mail you can see the social network mailru Clean icloud unlocking service, he says. But there is no name! Well, keep your secrets.We look at his email in other social networks, for example, from a database leak in vk.And here it is! The contact ID is id105140112, we also find facebook - necefliorxan. Instagram @ orhkan13 is listed on the page.
Clean icloud unlocking service, he says. But there is no name! Well, keep your secrets.We look at his email in other social networks, for example, from a database leak in vk.And here it is! The contact ID is id105140112, we also find facebook - necefliorxan. Instagram @ orhkan13 is listed on the page. The password was the login from instagram, noticed?Dude from Azerbaijan, lives in Moscow. Master in programmer, speaks on facebook.In general, successful success.
The password was the login from instagram, noticed?Dude from Azerbaijan, lives in Moscow. Master in programmer, speaks on facebook.In general, successful success.Passwordman
In another case, the icloud.com-maps-id.com domain came across, the admin account Mail find48store@yandex.ruSearch did not give anything interesting. But the password ... The password is at the admin panel
But the password ... The password is at the admin panel vasif548! Looking at the password is a completely different matter!People forget that a user's fingerprint can be not only some kind of identifier such as login or email. It may be a password!You can have many logins, but if you use one password, you can easily figure it out. And if you use a password from your own login - well, I'm sorry. Could at least copy the login as a password twice, as I do!This dude has logged in to more forums.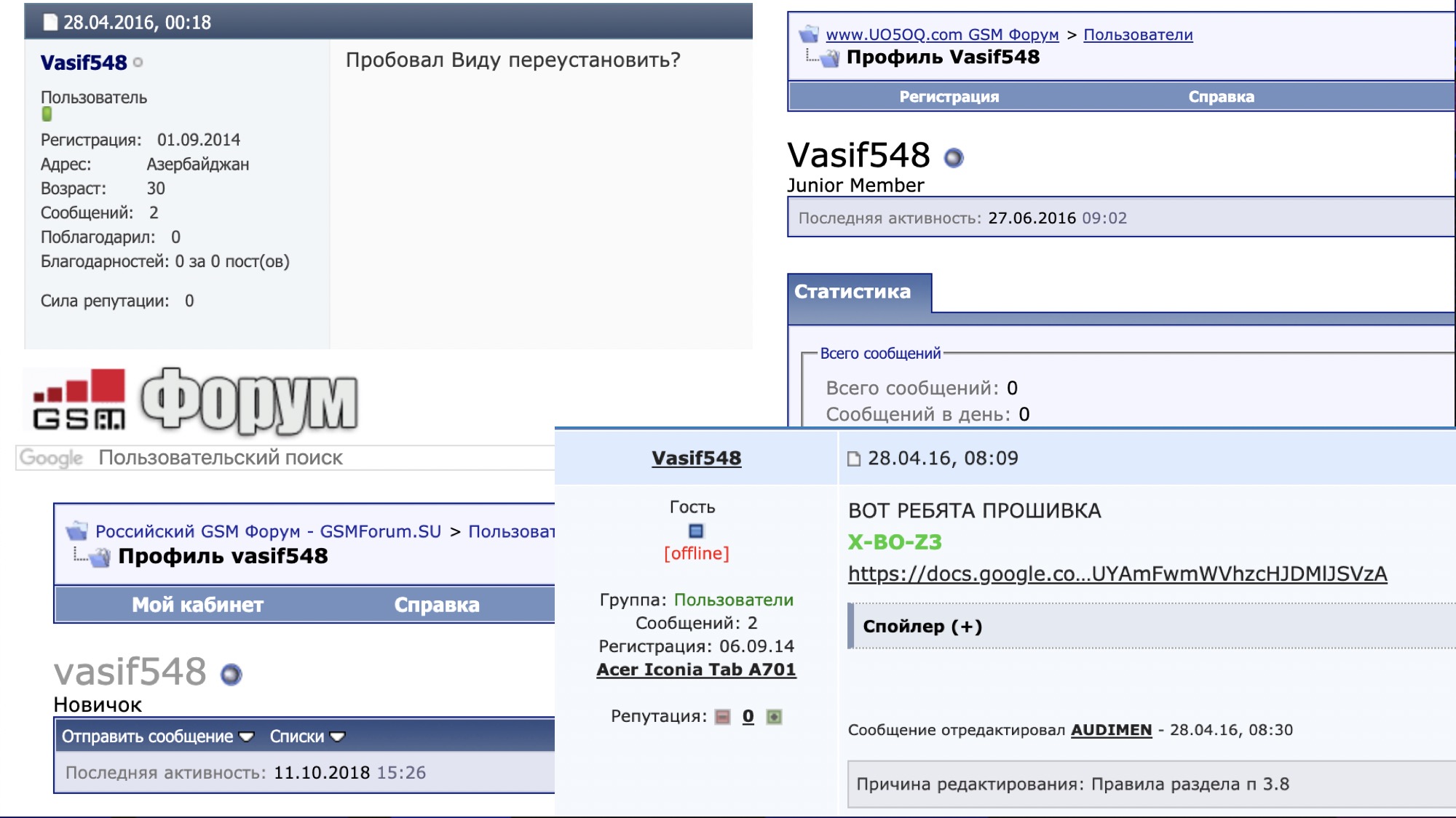 But this is bad luck - I do not see more data. But did you notice that this fisher and the wolf from Baku were sitting on the same forum? We try the wolfs collar and ...
But this is bad luck - I do not see more data. But did you notice that this fisher and the wolf from Baku were sitting on the same forum? We try the wolfs collar and ...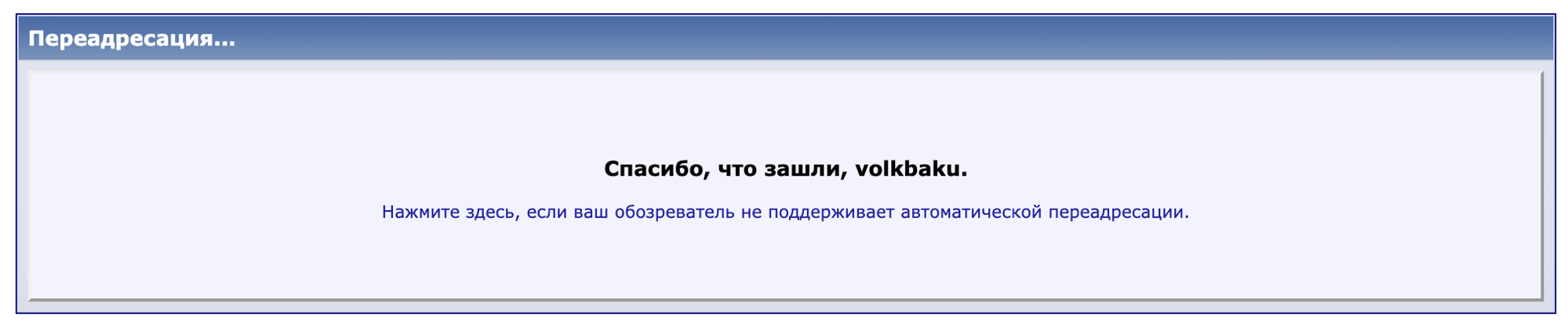 Last activity in 2016, most likely he has vk. Just in case, I studied Wolf’s friends, but nothing.I think, but is it possible to stir up a social little girl? I’ll write, they say, give me your current contact. Suddenly one generally advised the forum to another?We compose a letter:
Last activity in 2016, most likely he has vk. Just in case, I studied Wolf’s friends, but nothing.I think, but is it possible to stir up a social little girl? I’ll write, they say, give me your current contact. Suddenly one generally advised the forum to another?We compose a letter: No, something is wrong. We edit the letter as follows and
No, something is wrong. We edit the letter as follows and send it : We are waiting.A week passes, but there is no answer. And then I realized that I had made an unfortunate mistake. Once again, I began to study the vasif548 profiles and stumbled upon the fact that he had vk listed on w3bsit3-dns.com!
send it : We are waiting.A week passes, but there is no answer. And then I realized that I had made an unfortunate mistake. Once again, I began to study the vasif548 profiles and stumbled upon the fact that he had vk listed on w3bsit3-dns.com! Getting ready to see, open the link vk.com/id277815372
Getting ready to see, open the link vk.com/id277815372 But everything that got on the Internet remains on the Internet. The page with this id was a certain Vasif Bakhyshov, as the vkfaces service says (https://vkfaces.com/vk/user/id402895773)
But everything that got on the Internet remains on the Internet. The page with this id was a certain Vasif Bakhyshov, as the vkfaces service says (https://vkfaces.com/vk/user/id402895773) We look at the specified date of birth, look in other social networks. We find one Vasif in ok.ru (570202078321). In the photos we see announcements about unlocking the phone.Boom! Savelovsky Market, Pavilion 45
We look at the specified date of birth, look in other social networks. We find one Vasif in ok.ru (570202078321). In the photos we see announcements about unlocking the phone.Boom! Savelovsky Market, Pavilion 45
Me and the Fisher Ball
Time passed, the number of fakes did not decrease, someone was hard to find, someone registered to their mail.Dudes with the Laravel framework obviously do not know how to cook it. One could talk about creating an administrator session through the leaked APP_KEY. Or about the execution of arbitrary code using deserialization. But this format is not the same, and the password from the database approached the password from the panel, so this is not the time for extra tricks.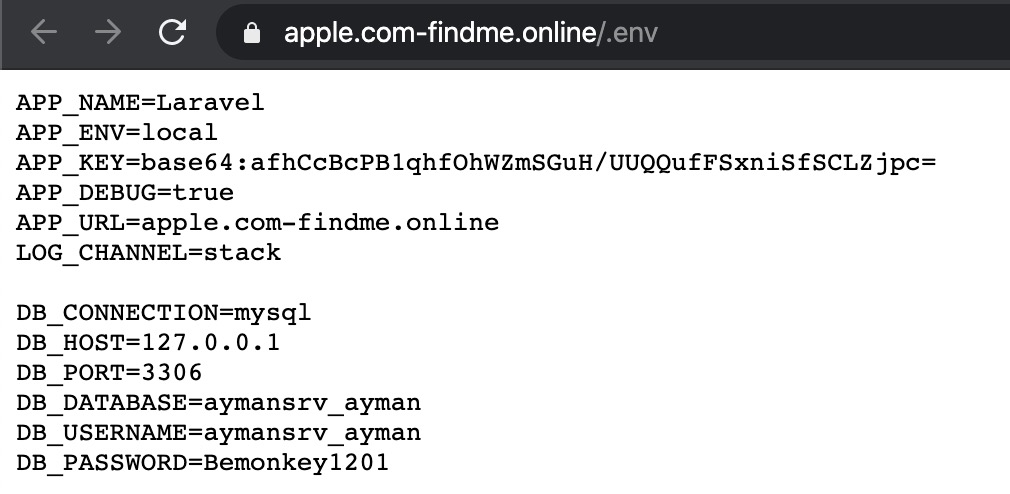 For some, calling an error or gaining access to the logs helped, since the panel administrator often indicated his nickname on the hosting, which was put in the path to the web application (/ var / www / h4cker / icloud /). Others, after installing the panel, clearly tested its performance on itself. Hands have not reached yet to check all the database dumps and see.
For some, calling an error or gaining access to the logs helped, since the panel administrator often indicated his nickname on the hosting, which was put in the path to the web application (/ var / www / h4cker / icloud /). Others, after installing the panel, clearly tested its performance on itself. Hands have not reached yet to check all the database dumps and see. Why do I upload only admin data? Because there is no sense from the victim’s bases, they got it anyway, and then their data will get into the network.About six months have passed since the villain my friend encountered was missed.Let me remind you that KolyaVanya was on a domain.
Why do I upload only admin data? Because there is no sense from the victim’s bases, they got it anyway, and then their data will get into the network.About six months have passed since the villain my friend encountered was missed.Let me remind you that KolyaVanya was on a domain.www.icloud.com.fmips.ruAnd at that moment the following domain caught my eye.www.icloud.com.fmistatus.infoThe first one had an IP address:93.170.123.118The new IP address:93.170.123.102We use deduction, and we understand that this is most likely one hosting. Well, at first I did not find this suspicious, it happens that it is purely by accident that several people use a small and unknown host (in the MAROSNET data center). And more precisely - non-public, which ignores complaints.Admin email is strange: soz112233soz@gmail.comBut the most confused password Qaqa2015.Looks like the previous one Zaza2015?So I thought so.We check mail - it fits! Fine. We study a mailer.Two senders of letters: ExpressVPN and TXTDAT.We look VPN:
Fine. We study a mailer.Two senders of letters: ExpressVPN and TXTDAT.We look VPN: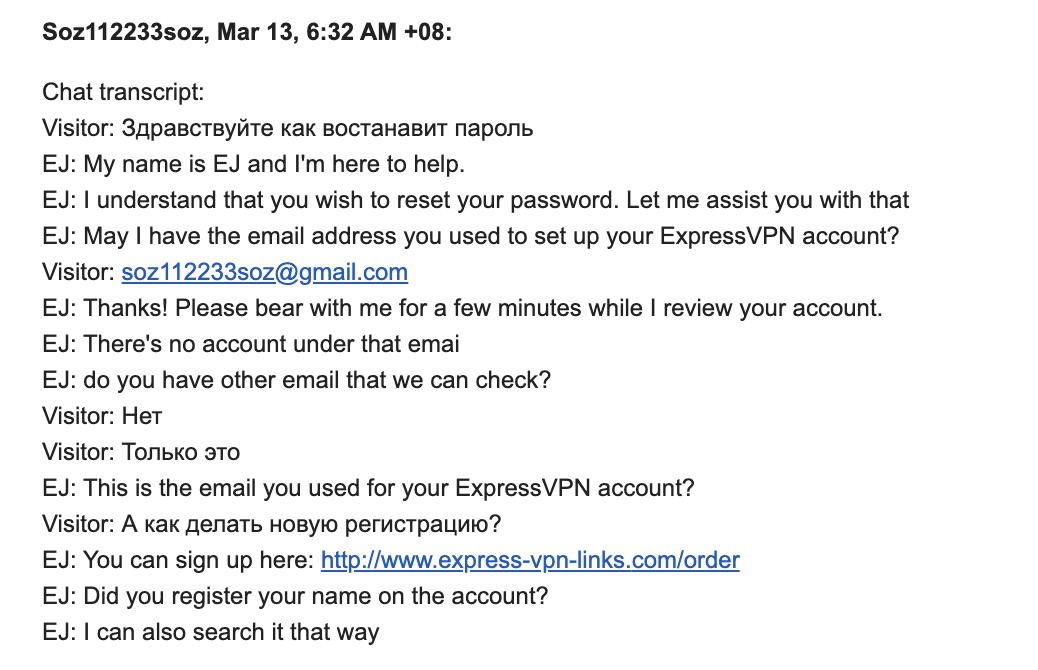 Funny, he lost his access to the VPN. It happens to everyone?Recall that Google stores search history and locations .There are no movements, but the search was saved:
Funny, he lost his access to the VPN. It happens to everyone?Recall that Google stores search history and locations .There are no movements, but the search was saved: Well, we see that he was visiting: Did you use a VPN at that time? We look below: Oh, you little rascal! Forgot to log in? We look at the details, google says that he is from Moscow. The vocabulary is similar to the previous admin, which we missed six months ago. So far, everything is the same.
Well, we see that he was visiting: Did you use a VPN at that time? We look below: Oh, you little rascal! Forgot to log in? We look at the details, google says that he is from Moscow. The vocabulary is similar to the previous admin, which we missed six months ago. So far, everything is the same.iunlocker.net
sms-api.online
 We look in the TXTDAT letter, we see that the specified login: Lostoff.Under this name you can find the service of hacking mail, unlocking iPhones, possibly due to the fact that this is a fairly popular login.We recover the password, go to TXTDAT.A little about it: this is a SMS sending service with a sender spoofing. I tried to register on it, but I need to wait for the confirmation of the administrator. Nobody talks about him on the Internet. Apparently, this is a closed service "only for their own."
We look in the TXTDAT letter, we see that the specified login: Lostoff.Under this name you can find the service of hacking mail, unlocking iPhones, possibly due to the fact that this is a fairly popular login.We recover the password, go to TXTDAT.A little about it: this is a SMS sending service with a sender spoofing. I tried to register on it, but I need to wait for the confirmation of the administrator. Nobody talks about him on the Internet. Apparently, this is a closed service "only for their own."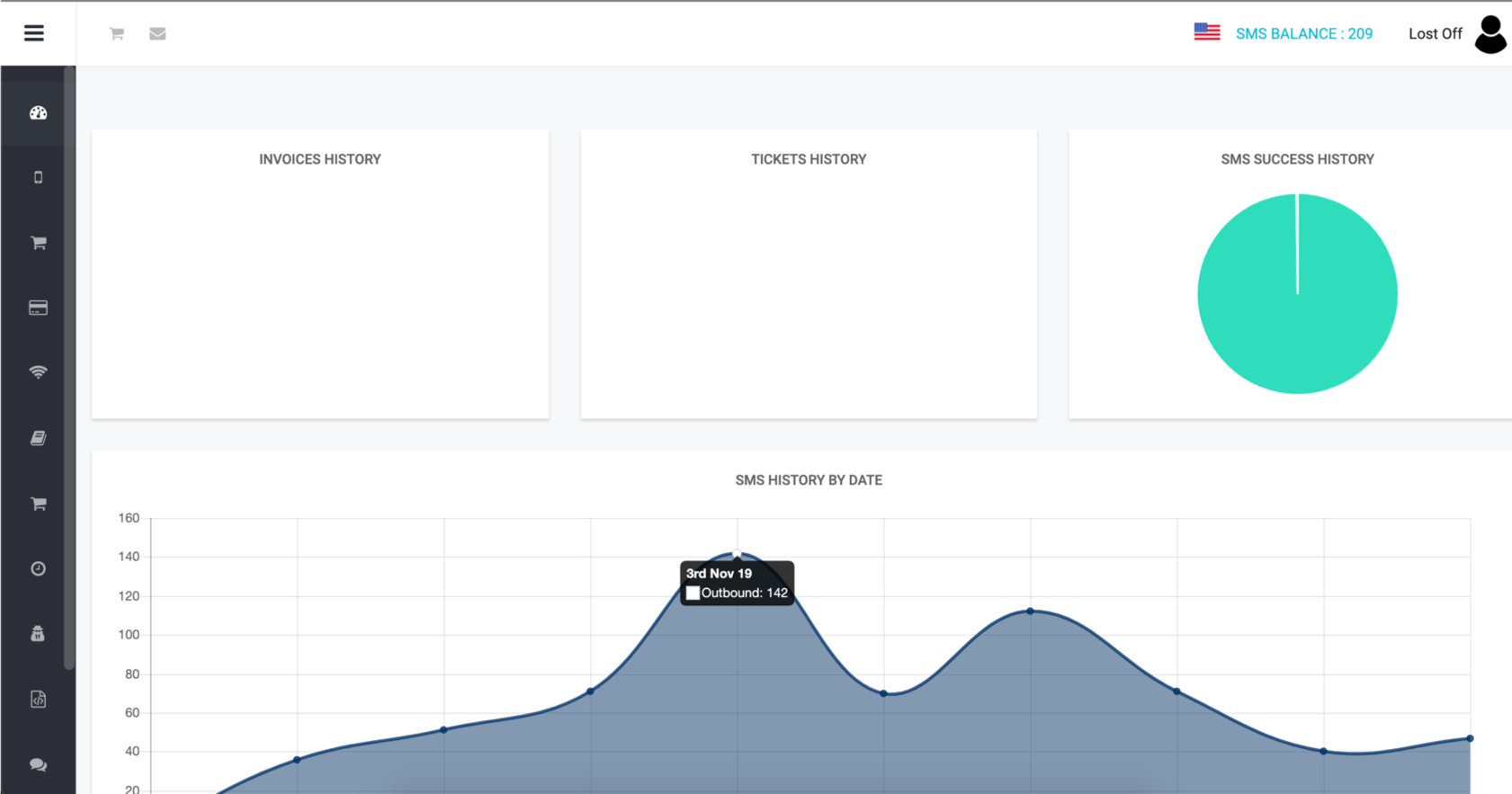 Ofigeev that only one person in the peak can send more than a hundred SMS per day. We go into the account settings, see the number.
Ofigeev that only one person in the peak can send more than a hundred SMS per day. We go into the account settings, see the number. Oh, another one-day room. Or not ...Add to contacts in telegram:
Oh, another one-day room. Or not ...Add to contacts in telegram: Lostoff! I didn’t lie.First, in the telegram bot @get_kontakt_bot and punch the number there.
Lostoff! I didn’t lie.First, in the telegram bot @get_kontakt_bot and punch the number there. Zeynal Mammadov! Known as the “programmer Zeynal”, “Zeynal baba” and “Zeynal Tsaritsino K163”We find by this ad number:
Zeynal Mammadov! Known as the “programmer Zeynal”, “Zeynal baba” and “Zeynal Tsaritsino K163”We find by this ad number:
 We look at the location:
We look at the location: Tsaritsyno , which coincides with the first leads.After breaking the phone through instagram through the nuga.app service, he gave as many as two contacts:@ zeynal.official, with the name Zeynal Mamedov, which has already been deleted.and@ lidermobile38, a department at the Yuzhny radio complex (another radio market?).After this story, a closed initiative group was created at the ZeroNights conference (as many as 66 people at the time of publication) for hacking fakes. Well, as an initiative, we see a fake - we are trying to hack, we send the victims database to the owners of the original site (for changing passwords and other activities). But you yourself can try it.
Tsaritsyno , which coincides with the first leads.After breaking the phone through instagram through the nuga.app service, he gave as many as two contacts:@ zeynal.official, with the name Zeynal Mamedov, which has already been deleted.and@ lidermobile38, a department at the Yuzhny radio complex (another radio market?).After this story, a closed initiative group was created at the ZeroNights conference (as many as 66 people at the time of publication) for hacking fakes. Well, as an initiative, we see a fake - we are trying to hack, we send the victims database to the owners of the original site (for changing passwords and other activities). But you yourself can try it.Where to begin?
How to search for fakes?Unfortunately, domains do not live long, but new ones always appear.I have used several approaches.The first , and the most commonplace, is monitoring social networks.We introduce in social networks different variations of search queries of the form “stole iphone sms”, we get the results from the victims. As with sad stories that they, in addition to the phone, have withdrawn money from the bank, and with simply discontent.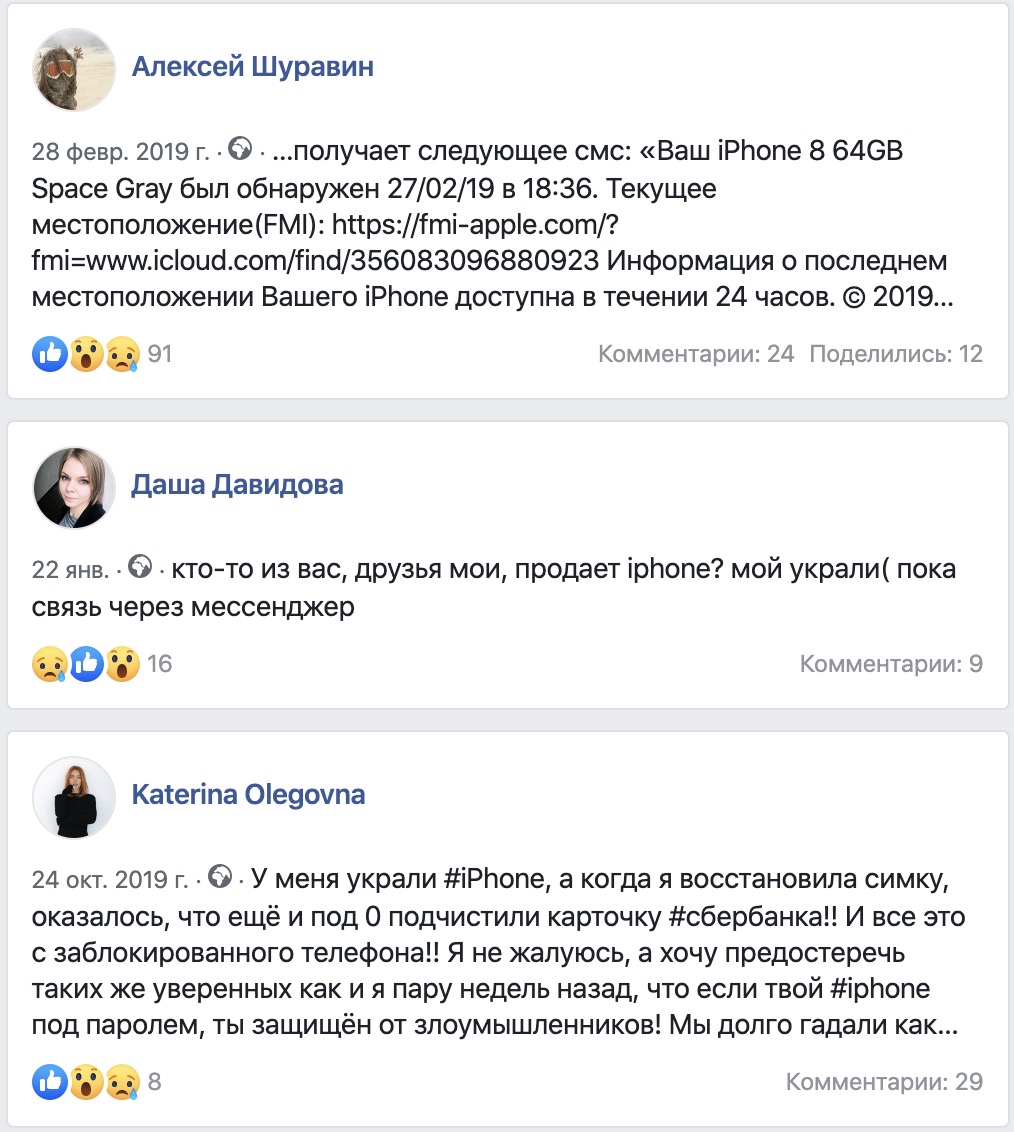 But links are important to us, so we write them off from the screenshots. If you are not shy, you can write to the victims and personally ask for a link.
But links are important to us, so we write them off from the screenshots. If you are not shy, you can write to the victims and personally ask for a link. Way two . If the domain has come into the view of various robots, try to find them.Several services come to the rescue:google.comAwesome site, I always use it myself. It is enough to write intitle: “iCloud cannot find that page” to catch those fakes who have icloud error on the main page 404.You can refine your search on a specific site, for example
Way two . If the domain has come into the view of various robots, try to find them.Several services come to the rescue:google.comAwesome site, I always use it myself. It is enough to write intitle: “iCloud cannot find that page” to catch those fakes who have icloud error on the main page 404.You can refine your search on a specific site, for example site:cutestat.com censys.io / shodan.io / publicwww.com.They allow you to find the hosts on which the same sites were spinning. We use the title of the page, as in the previous version.
censys.io / shodan.io / publicwww.com.They allow you to find the hosts on which the same sites were spinning. We use the title of the page, as in the previous version.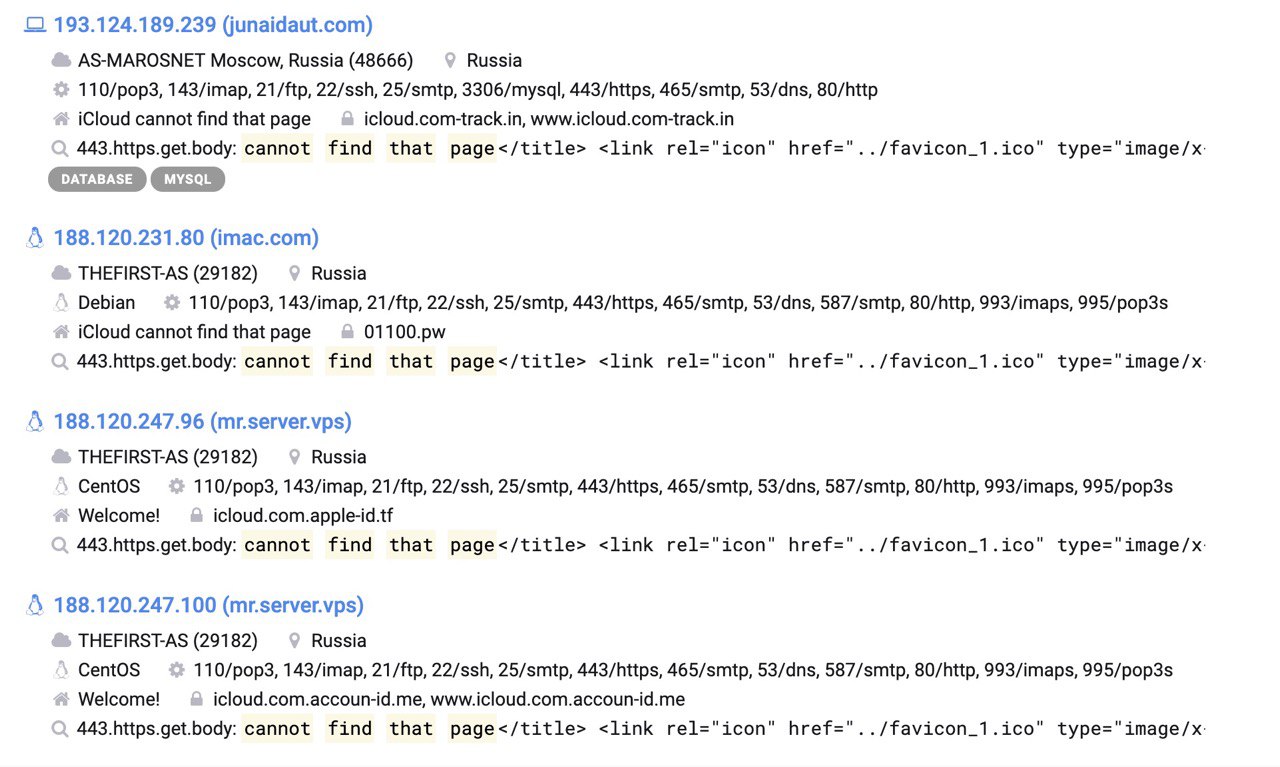 urlscan.io Awesomeservice. It allows you to search, for example, related links . This immediately gives you a lot of fresh domains on the Phoenix engine (or on others).iPanel Pro (and similar ones) will redirect from the main page to the original icloud.com, so you can track redirects .Third way- real-time monitoring.There is a cool script from x0rz: phishing_catcher , it allows you to monitor issued certificates. But since we are only interested in icloud, we look at domains . We select keywords and domain zones.I left only such keywords: Having launched the script, we put it on monitoring, and then we look at the output. That this is a popular market can be judged by the fact that about 10 domains are registered per day. The fourth and last way for today is to search not by certificates, but by registered domains. Dnspedia will help us with this . I think you’ll guess how to search for domains in more than 7 days.
urlscan.io Awesomeservice. It allows you to search, for example, related links . This immediately gives you a lot of fresh domains on the Phoenix engine (or on others).iPanel Pro (and similar ones) will redirect from the main page to the original icloud.com, so you can track redirects .Third way- real-time monitoring.There is a cool script from x0rz: phishing_catcher , it allows you to monitor issued certificates. But since we are only interested in icloud, we look at domains . We select keywords and domain zones.I left only such keywords: Having launched the script, we put it on monitoring, and then we look at the output. That this is a popular market can be judged by the fact that about 10 domains are registered per day. The fourth and last way for today is to search not by certificates, but by registered domains. Dnspedia will help us with this . I think you’ll guess how to search for domains in more than 7 days.# Apple iCloud
'appleid': 70
'icloud': 60
'iforgot': 60
'itunes': 50
'apple': 40
'iphone': 30
'findmy': 30
'findme': 30
'location': 30
'applecare': 30
'fmf': 20
'fmi': 20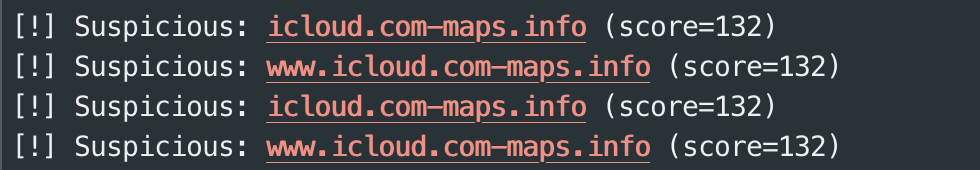
To summarize
- , . , , ( ) — . .
- email .
- ,
- — , email’, VPN, — , . , .
As some smart dude said, it costs a person who defends himself to make a mistake once - they will crack him. But if the cracker is mistaken once, they will find him.I posted the domains, administrator data and source codes on the xss.is forum and will add them if I find more time for this activity. On this my authority is everything.Thanks to kaimi, crlf and other dudes for the help, yarbabin for the cool logo.This, and other blog articles . Source: https://habr.com/ru/post/undefined/
All Articles