[Workshop] DMA attacks in practice. Exploit through direct memory access
 This Saturday, February 1, 2020, a master class on the practical use of DMA attacks will be held in our Hackspace Neuron in Moscow. Together we will hack into a real computer with an encrypted file system that mimics an ATM or payment terminal.Leading workshop ValdikSS and Maxim Goryachy . Behind the bar, Pavel Zhovner .Direct Memory Access (DMA) - a low-level mode of operation of computer devices, involving direct access to the computer's RAM. It is required for PCIe, Thunderbolt, and some other devices to work. Under normal conditions, DMA is used for faster access to memory so as not to occupy the processor.Using a special “evil” device, an attacker can take control of the PCIe bus and gain full read and write access to the memory of a working computer, even if the system is protected from penetration by software.
This Saturday, February 1, 2020, a master class on the practical use of DMA attacks will be held in our Hackspace Neuron in Moscow. Together we will hack into a real computer with an encrypted file system that mimics an ATM or payment terminal.Leading workshop ValdikSS and Maxim Goryachy . Behind the bar, Pavel Zhovner .Direct Memory Access (DMA) - a low-level mode of operation of computer devices, involving direct access to the computer's RAM. It is required for PCIe, Thunderbolt, and some other devices to work. Under normal conditions, DMA is used for faster access to memory so as not to occupy the processor.Using a special “evil” device, an attacker can take control of the PCIe bus and gain full read and write access to the memory of a working computer, even if the system is protected from penetration by software.DMA attacks allow
- Unbeknownst to the operating system and antiviruses, read and modify data in computer memory;
- Inject your code into OS and running programs
- Retrieve any data from running programs: keys, passwords
- Bypass authentication and authorization of the operating system
- .
Part 1 - TheoryFirst, on the fingers we will figure out how the PCIe bus works and memory access, why such attacks are possible and what modern means of protection against such attacks exist. Let's consider what tools exist for conducting DMA attacks and how best to design secure systems.ValdikSS will talk about its experience of using a DMA attack to crack the protection of a Japanese slot machine .Part 2 - practical lessonTo conduct an attack, we will use two computers: the attacker and the victim. A special “evil” device is inserted into the victim’s PCIe port, which implements the physical layer of PCIe and sends commands from the attacker. The attacking computer connects to the "evil" board via USB, and through it sends commands to the victim's PCIe bus.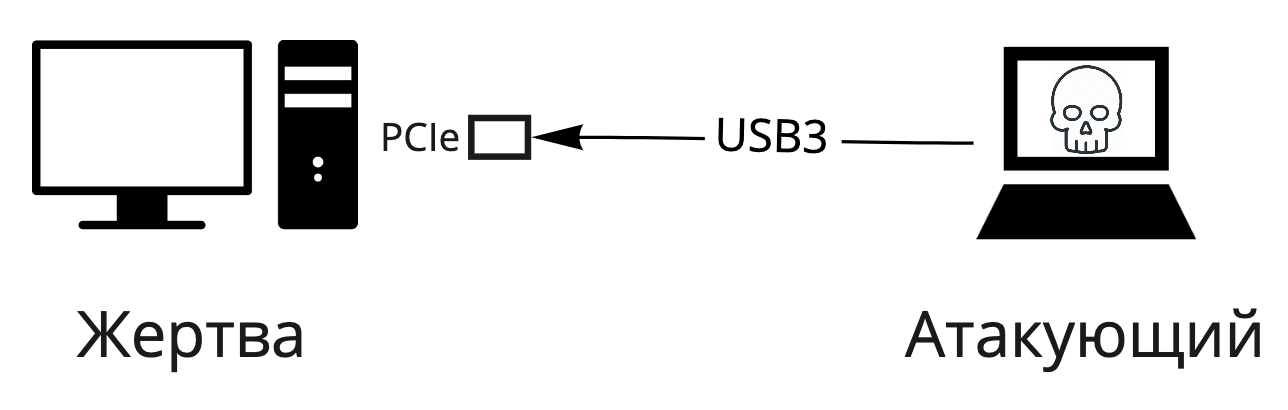 An ordinary X86 computer will act as a victim, and the USB3380 board will act as an “evil” device. The attacker side will use the pcileech framework .Let’s figure out which devices supports pcileech as attackers, and what is better to choose. We’ll set up an attacker’s stand from scratch based on the USB3380 board.
An ordinary X86 computer will act as a victim, and the USB3380 board will act as an “evil” device. The attacker side will use the pcileech framework .Let’s figure out which devices supports pcileech as attackers, and what is better to choose. We’ll set up an attacker’s stand from scratch based on the USB3380 board.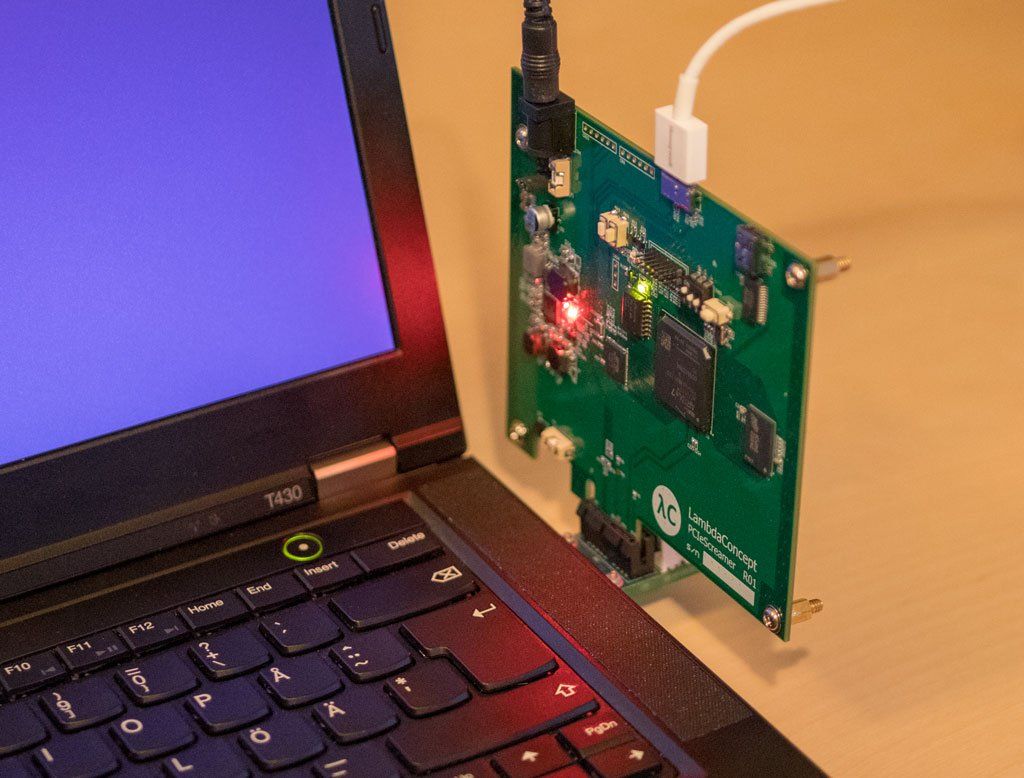 Initially, the victim computer will have a hard disk encrypted with bitlocker and locked to enter the operating system.We will perform the following attacks:
Initially, the victim computer will have a hard disk encrypted with bitlocker and locked to enter the operating system.We will perform the following attacks:- Windows Authentication Bypass - Logging into your account without resetting passwords
- Access to victim files . Despite file system encryption, access to files is still possible from within the OS
- We extract valuable data from memory - keys from a Bitcoin wallet, passwords and typed text
- We install an imitation of a trojan immediately in memory without intermediate files on the disk
For whom is this occupation
The lesson will be useful to developers of embedded systems, those who design terminals, ATMs, machines, game and gambling machines. You will need basic knowledge of computer hardware.The pcileech framework is quite simple and has several convenient plug-ins for typical attacks, so any advanced computer user will be able to learn how to use it.About the authors
 ValdikSS is a security researcher and open source enthusiast. The author of the program for bypassing DPI GoodByeDPI systems , and the services JustVPN and Anti-Ban . He worked at Digital Security . __________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________
ValdikSS is a security researcher and open source enthusiast. The author of the program for bypassing DPI GoodByeDPI systems , and the services JustVPN and Anti-Ban . He worked at Digital Security . __________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________ Maxim Hot- Embedded Developer and Security Researcher at Positive Technologies. He is interested in cryptography, virtualization technologies, reverse engineering and everything related to hardware. He performed at 33C3, 34C3, Black Hat. Together with Mark Ermolov, he found vulnerabilities in Intel ME, Apple MacOS Firmware. _________________________________________________________________________________________________________________________________________________________________________________________
Maxim Hot- Embedded Developer and Security Researcher at Positive Technologies. He is interested in cryptography, virtualization technologies, reverse engineering and everything related to hardware. He performed at 33C3, 34C3, Black Hat. Together with Mark Ermolov, he found vulnerabilities in Intel ME, Apple MacOS Firmware. _________________________________________________________________________________________________________________________________________________________________________________________Venue - Hackspace Neuron
Hackspace Neuron is a community of geeks and techno-enthusiasts in the center of Moscow. Workplaces with professional equipment and a creative atmosphere.
 All the money raised will go towards paying rent and developing Huxspace. If you want to support us additionally, you can embrace and offer your help.Attention: all information presented at the master class is for research purposes only. The test bench for vulnerability analysis is not a real-life system and was created specifically for training purposes. The author does not urge to use the acquired knowledge to commit unlawful acts.
All the money raised will go towards paying rent and developing Huxspace. If you want to support us additionally, you can embrace and offer your help.Attention: all information presented at the master class is for research purposes only. The test bench for vulnerability analysis is not a real-life system and was created specifically for training purposes. The author does not urge to use the acquired knowledge to commit unlawful acts.Source: https://habr.com/ru/post/undefined/
All Articles