1. CheckFlow - fast and free comprehensive audit of internal network traffic using Flowmon
 Welcome to our next mini course. This time we will talk about our new service - CheckFlow . What it is? In fact, this is simply the marketing name for the free audit of network traffic (both internal and external). The audit itself is performed using such a wonderful tool as Flowmon , which can be used by absolutely any company, free of charge, within 30 days. But, I assure you, that after the first hours of testing, you will begin to receive valuable information about your network. Moreover, this information will be valuable both for network administrators and for “security personnel” . Well, let's discuss what this information is and what its value is (At the end of the article, as usual, a video lesson).Immediately, we make a small digression. I’m just sure that many people now have a thought: “How is this different from Check Point Security CheckUP ?”. Our subscribers probably know what it is (we spent a lot of effort on this) :) Do not rush to conclusions, during the lesson everything will fall into place.
Welcome to our next mini course. This time we will talk about our new service - CheckFlow . What it is? In fact, this is simply the marketing name for the free audit of network traffic (both internal and external). The audit itself is performed using such a wonderful tool as Flowmon , which can be used by absolutely any company, free of charge, within 30 days. But, I assure you, that after the first hours of testing, you will begin to receive valuable information about your network. Moreover, this information will be valuable both for network administrators and for “security personnel” . Well, let's discuss what this information is and what its value is (At the end of the article, as usual, a video lesson).Immediately, we make a small digression. I’m just sure that many people now have a thought: “How is this different from Check Point Security CheckUP ?”. Our subscribers probably know what it is (we spent a lot of effort on this) :) Do not rush to conclusions, during the lesson everything will fall into place.What the network administrator can verify with this audit:
- Network traffic analytics - how the channels are loaded, which protocols are used, which servers or users consume the most traffic.
- Network delays and losses - the average response time of your services, the presence of losses on all your channels (the ability to find a bottleneck).
- — . , , .
- — ( , , , ).
- SLA — web- .
- — DNS/DHCP spoofing, , DHCP-, DNS/SMTP .
- — , .
- — - .
:
- — , (0-day) .
- — , .
- — , , , ICMP/DNS . .
- — , brut-force , DoS, DDoS, (MITM).
- — ( ) .
- — ( ).
- — (Bittorent, TeamViewer, VPN, ..).
- Cryptominers and Botnets - scan the network for infected devices connecting to well-known C&C servers.
Reporting
Based on the audit results, you can see all the analytics on Flowmon dashboards, or in PDF reports. Below are a few examples.General traffic analytics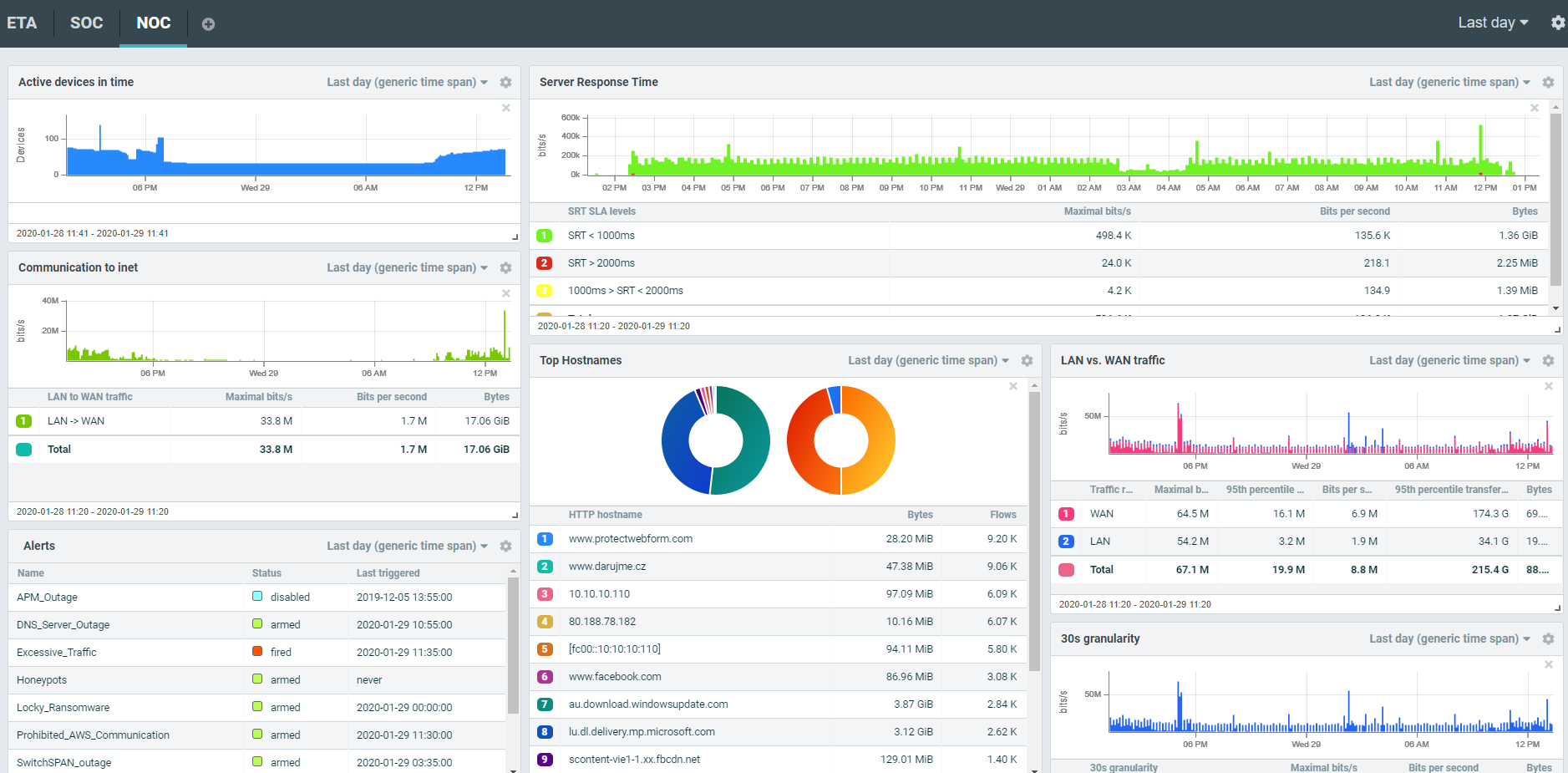 Custom dashboard
Custom dashboard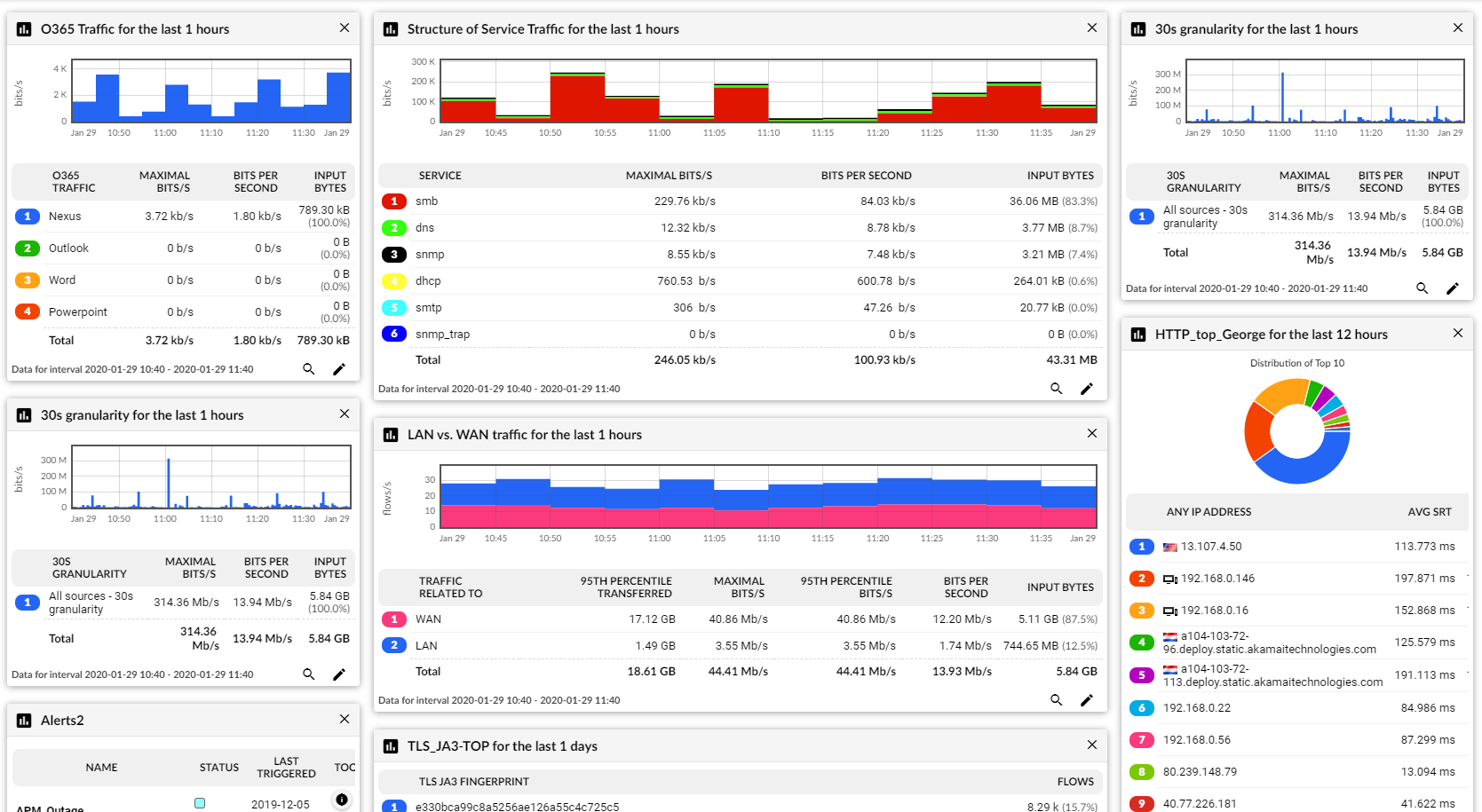 Abnormal activity
Abnormal activity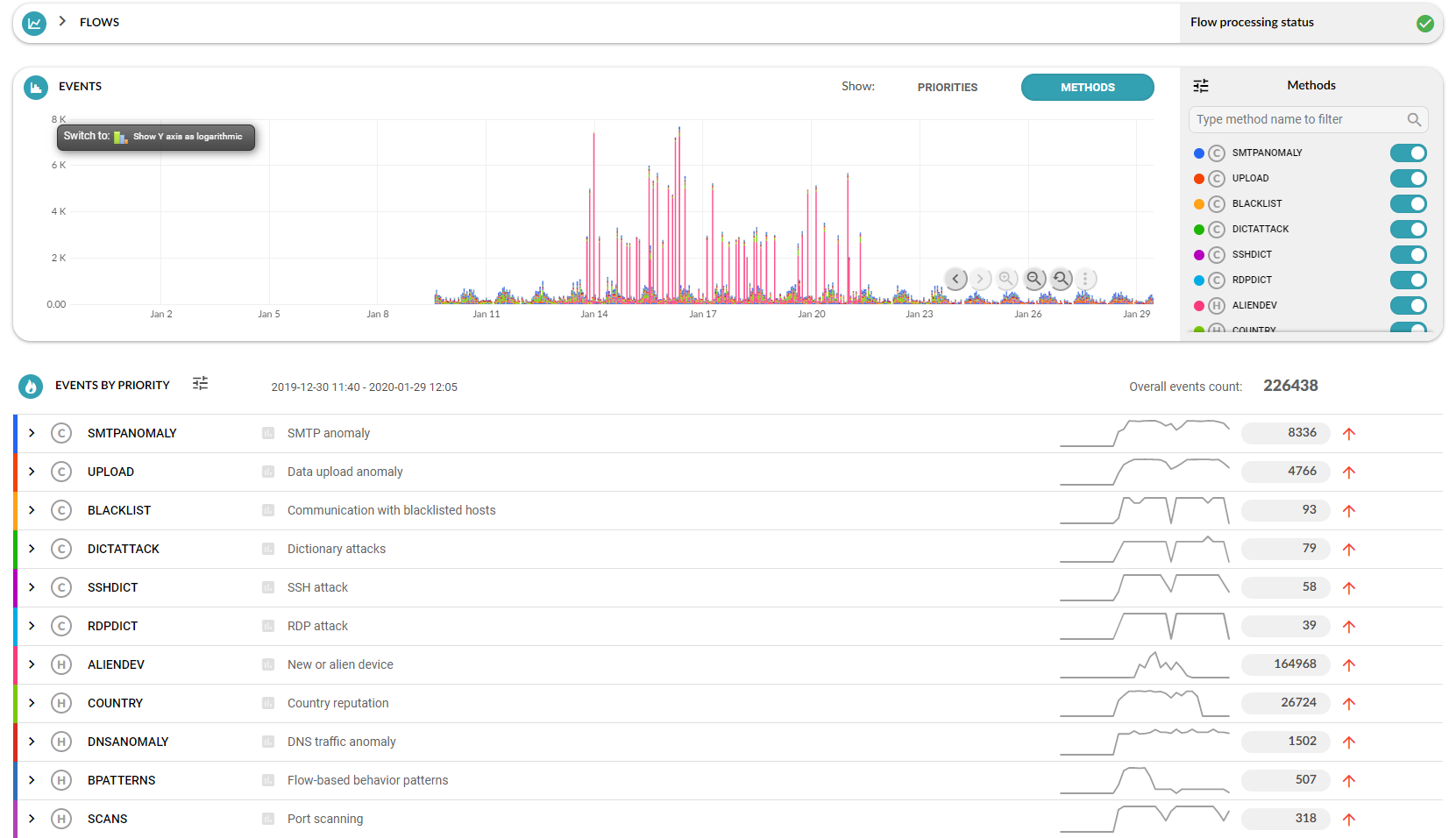 Detected devices
Detected devices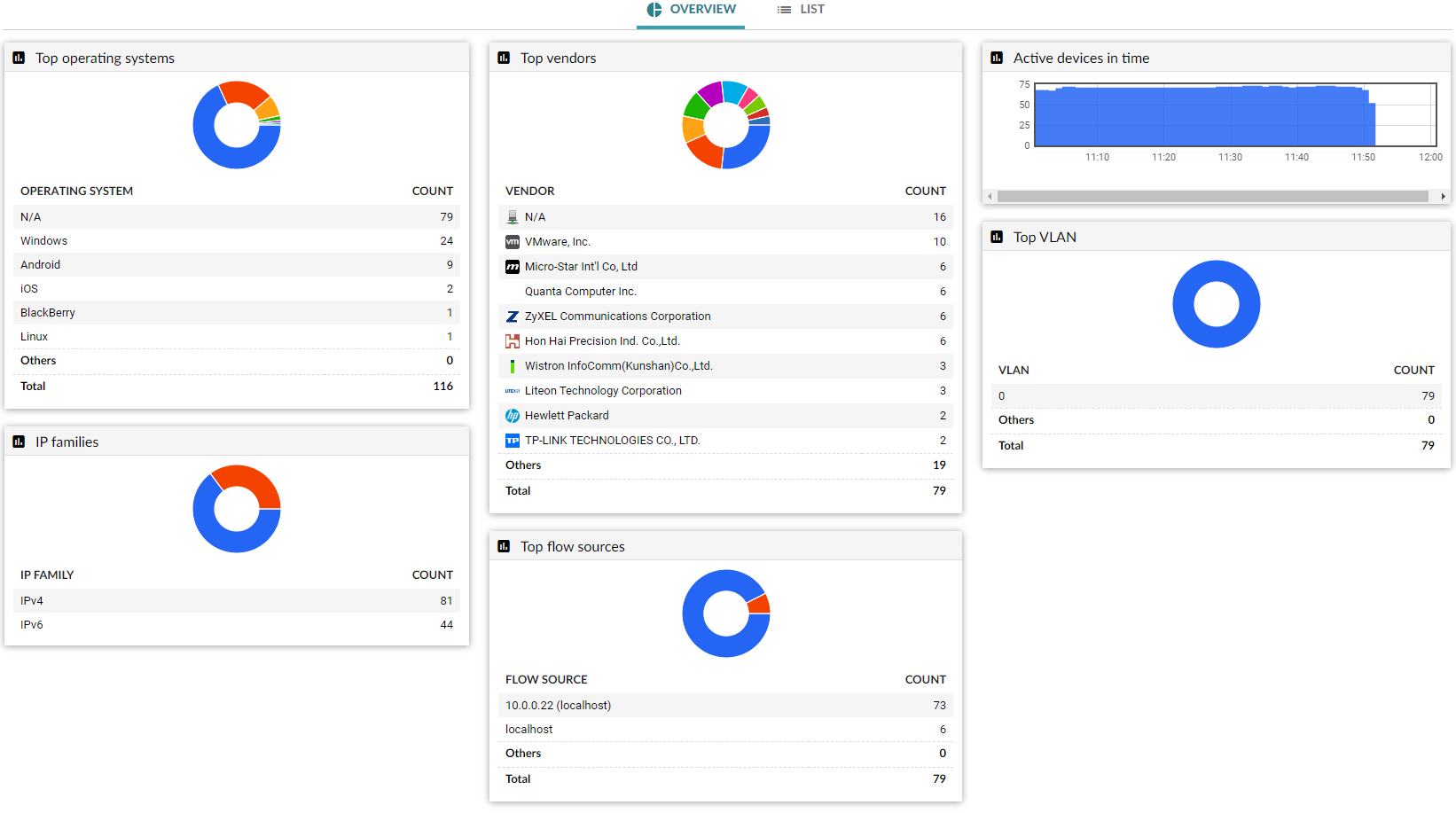
Typical Test Pattern
Scenario No. 1 - one office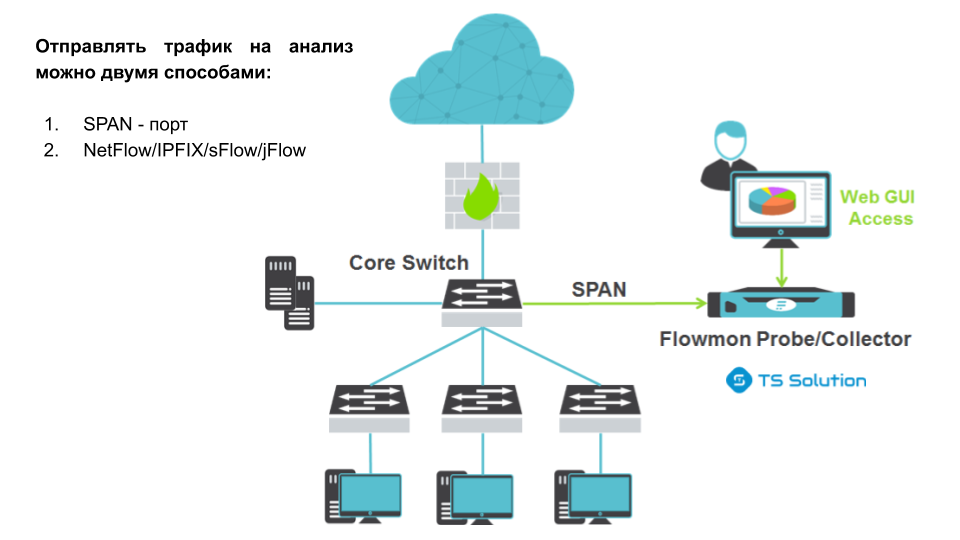 A key feature - you can analyze both external and internal traffic that does not fall under the analysis of network perimeter protection devices (NGFW, IPS, DPI, etc.).Scenario 2 - Multiple Offices
A key feature - you can analyze both external and internal traffic that does not fall under the analysis of network perimeter protection devices (NGFW, IPS, DPI, etc.).Scenario 2 - Multiple Offices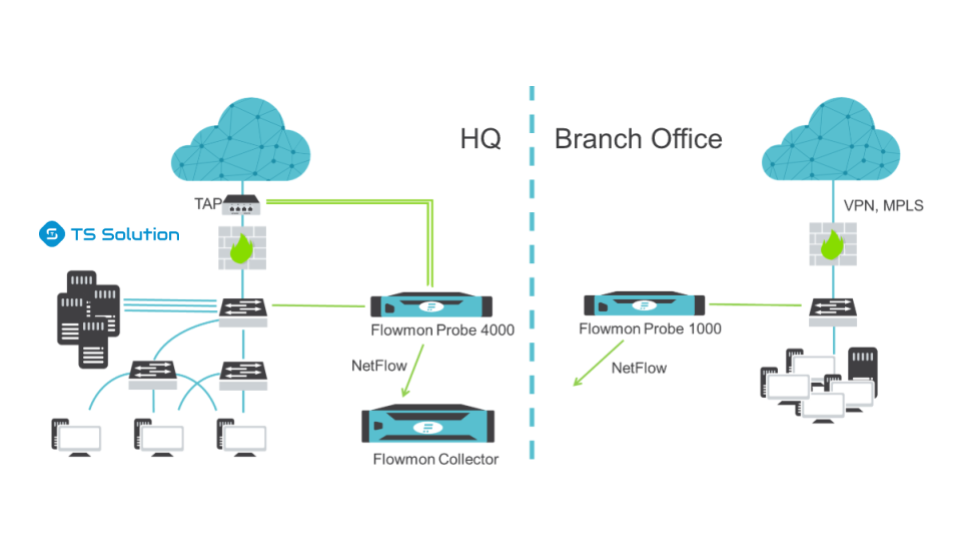
Video tutorial
Summary
Audit CheckFlow is a great opportunity for IT / IB managers:- -;
- ;
- - ( , , ) ;
- -;
- , .
I also recommend reading our previous article - 9 typical network problems that can be detected using NetFlow analysis (using Flowmon as an example) .If you are interested in this topic, then stay tuned ( Telegram , Facebook , VK , TS Solution Blog , Yandex.Zen) .Source: https://habr.com/ru/post/undefined/
All Articles