In diesem Artikel möchte ich schrittweise Anweisungen zur schnellen Bereitstellung des skalierbarsten RAS -VPN- Zugriffsschemas basierend auf AnyConnect und Cisco ASA - VPN Load Balancing Cluster geben .
Einführung: Viele Unternehmen auf der ganzen Welt bemühen sich angesichts des aktuellen Umfelds mit COVID-19, ihre Mitarbeiter in den Remote-Modus zu versetzen. Aufgrund des massiven Übergangs zur Remote-Arbeit steigt die Belastung bestehender VPN-Gateways von Unternehmen kritisch an, und es ist eine sehr schnelle Skalierbarkeit erforderlich. Auf der anderen Seite sind viele Unternehmen gezwungen, so etwas wie Fernarbeit von Grund auf neu zu lernen.
Damit Unternehmen so schnell wie möglich einen bequemen, sicheren und skalierbaren VPN-Zugriff für Mitarbeiter implementieren können, stellt Cisco Lizenzen für den AnyConnect-Multifunktions-SSL-VPN-Client für bis zu 13 Wochen zur Verfügung. Sie können ASAv auch von autorisierten Partnern testen lassen (Virtual ASA für VMWare / Hyper-V / KVM-Hypervisoren und AWS / Azure-Cloud-Plattformen) oder sich an Ihren Cisco-Vertreter wenden .
Das AnyConnect COVID-19-Lizenzausstellungsverfahren wird hier beschrieben .
Ich habe schrittweise Anweisungen für eine einfache VPN-Option zum Bereitstellen eines Load-Balancing-Clusters als skalierbarste VPN-Technologie erstellt.
, ( ) .
: VPN Load Balancing Cluster failover , ASA ( ) Remote-Access VPN . C , VPN VPN . VPN .
( ) , , Primary . Load-Balancing , , , . .
VPN Load-Balancing .
VPN Load-Balancing ASA 5512-X .
ASA VPN Load-Balancing , .
:
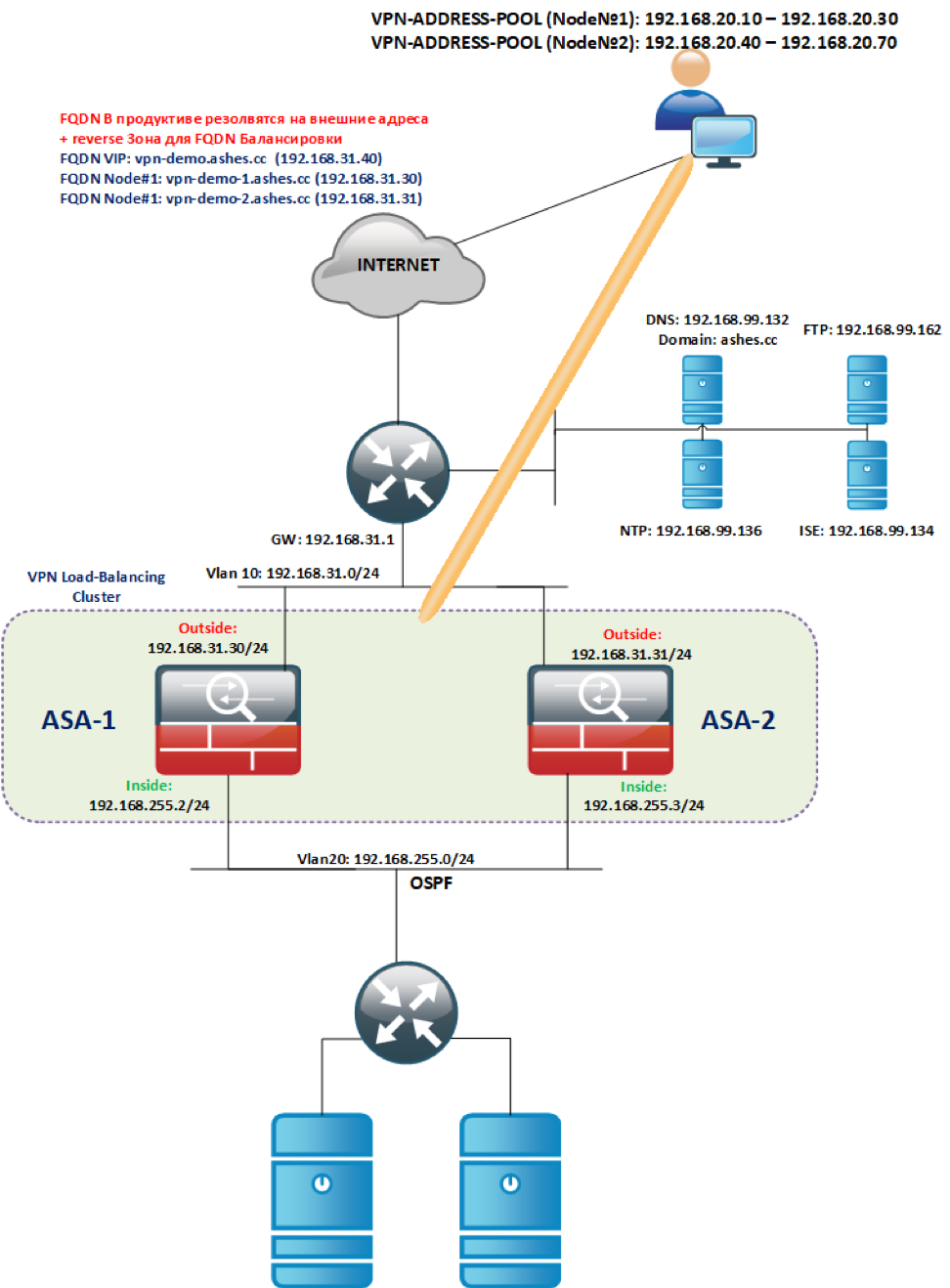
:
ASAv (ASAv5/10/30/50).
INSIDE/OUTSIDE VLAN (Outside VLAN, INSIDE , . ), L2 .
:
!
ciscoasa# conf t
!
ciscoasa(config)# clock set 19:21:00 Mar 18 2020
ciscoasa(config)# clock timezone MSK 3
ciscoasa(config)# ntp server 192.168.99.136
!
ciscoasa(config)# dns domain-lookup outside
ciscoasa(config)# DNS server-group DefaultDNS
ciscoasa(config-dns-server-group)# name-server 192.168.99.132
!
! DNS:
!
ciscoasa(config-dns-server-group)# ping ya.ru
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 87.250.250.242, timeout is 2 seconds:
!!!!!
!
! NTP:
!
ciscoasa(config)# show ntp associations
address ref clock st when poll reach delay offset disp
*~192.168.99.136 91.189.94.4 3 63 64 1 36.7 1.85 17.5
* master (synced), # master (unsynced), + selected, - candidate, ~ configured
!
! ASAv Smart-Licensing ( , 100 )
!
ciscoasa(config)# license smart
ciscoasa(config-smart-lic)# feature tier standard
ciscoasa(config-smart-lic)# throughput level 100M
!
! :
!call-home
! http-proxy ip_address port port
!
! Smart-Account (<token>)
!
ciscoasa(config)# end
ciscoasa# license smart register idtoken <token>
- :
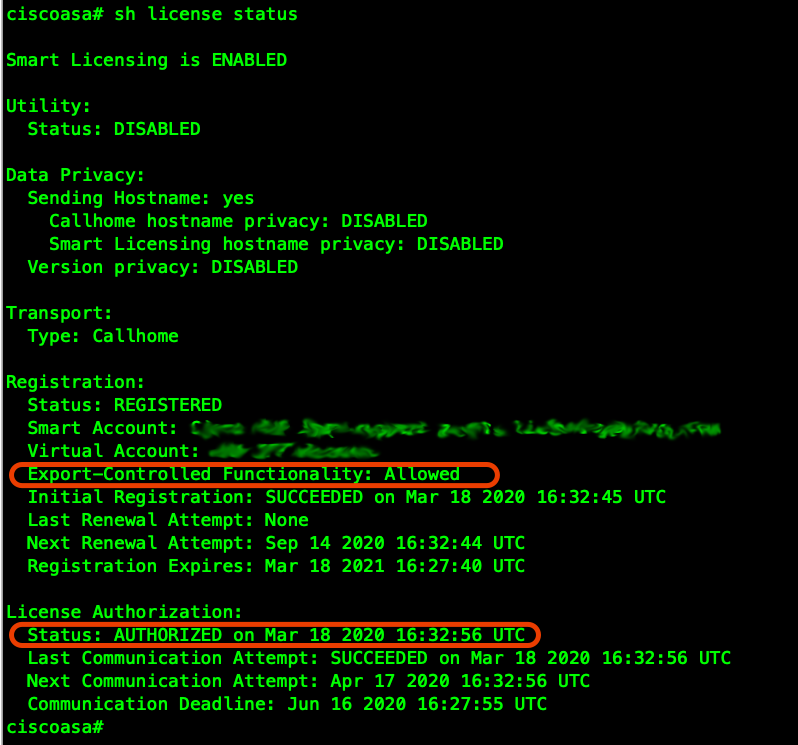
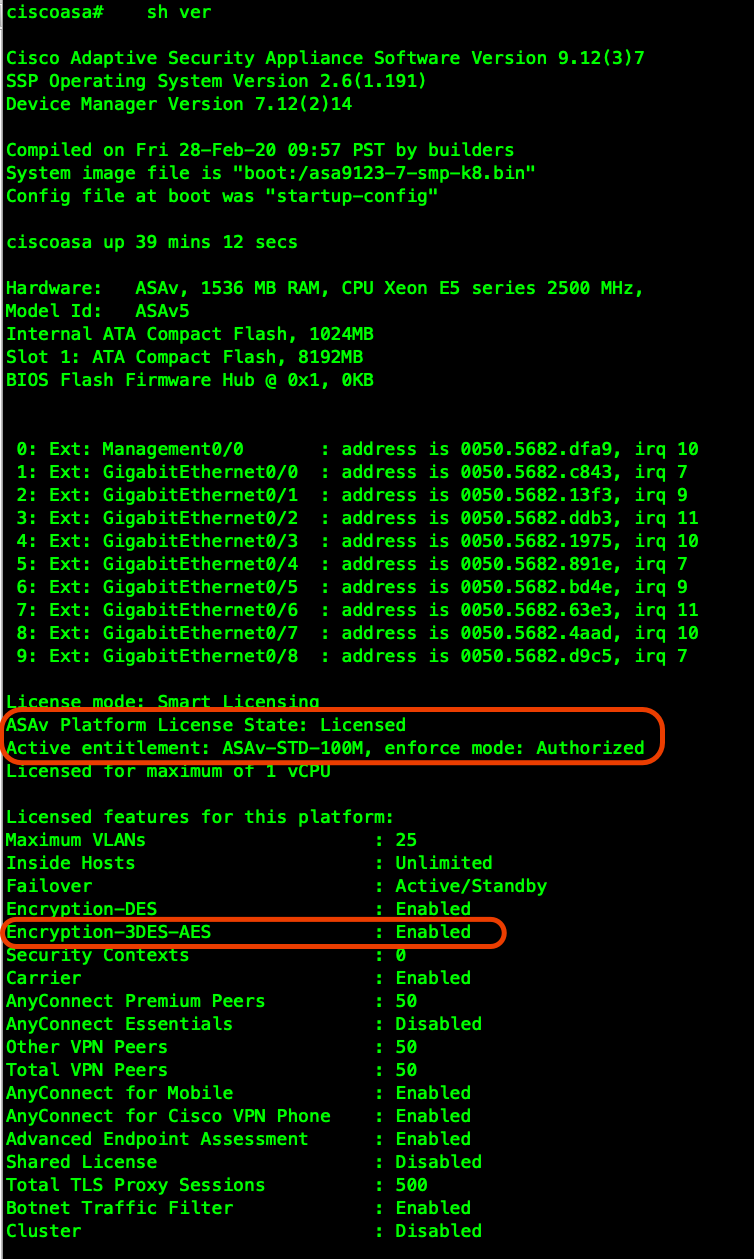
SSL-VPN
SSH ASDM:
!
ciscoasa# conf t
ciscoasa(config)# ssh ver 2
ciscoasa(config)# aaa authentication ssh console LOCAL
ciscoasa(config)# aaa authentication http console LOCAL
ciscoasa(config)# hostname vpn-demo-1
vpn-demo-1(config)# domain-name ashes.cc
vpn-demo-1(config)# cry key gen rsa general-keys modulus 4096
vpn-demo-1(config)# ssh 0 0 inside
vpn-demo-1(config)# http 0 0 inside
!
! HTTPS ASDM 445 SSL-VPN
!
vpn-demo-1(config)# http server enable 445
!
ASDM cisco.com, :
AnyConnect ASA ( Linux/Windows/MAC) Headend Deployment Package :

, , FTP ASA:
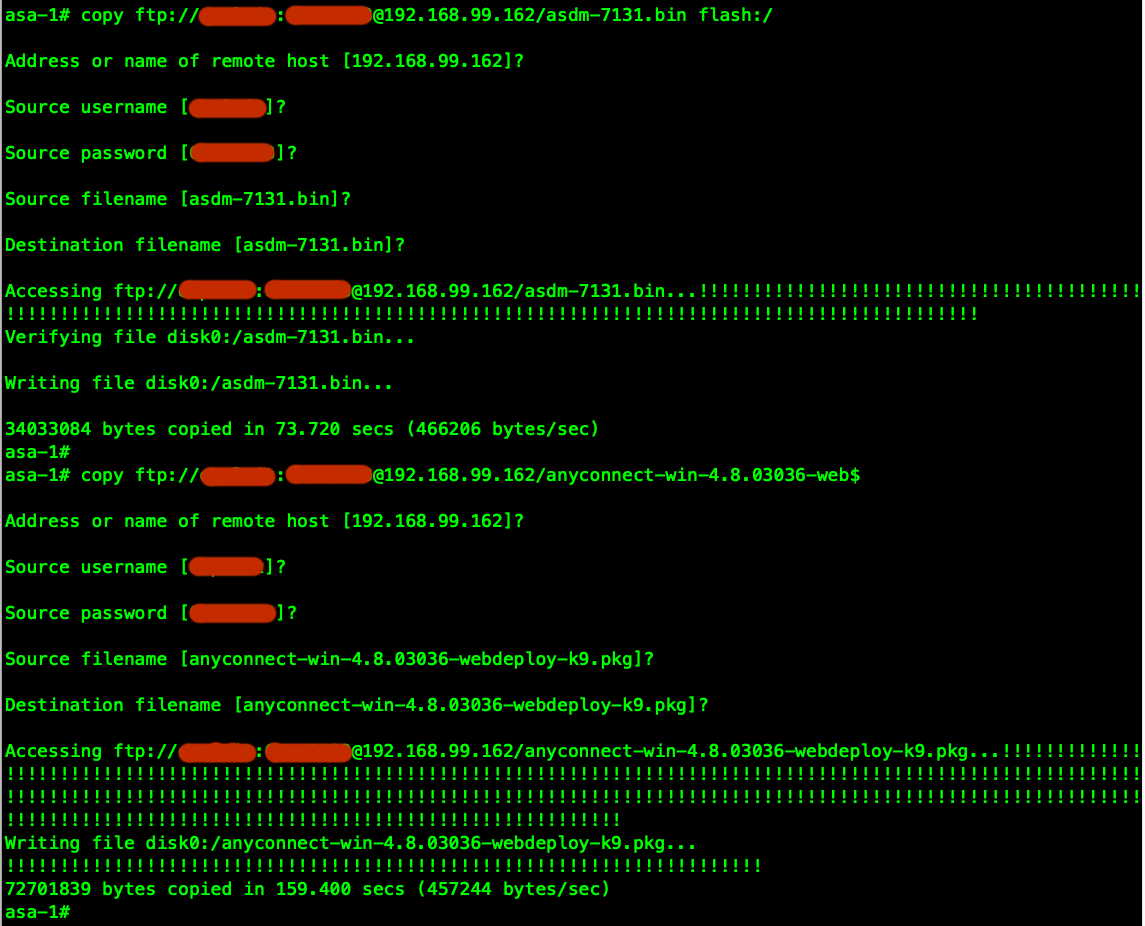
ASDM VPN- SSL-VPN ( ). FQDN (vpn-demo.ashes.cc), FQDN DNS IP OUTSIDE ( mapped , udp/443 (DTLS) tcp/443(TLS)). Certificate Verification .
- Self-Signed ( )
!
vpn-demo-1(config)# asdm image flash:/asdm-7131.bin
!
vpn-demo-1(config)# crypto ca trustpoint SELF
vpn-demo-1(config-ca-trustpoint)# enrollment self
vpn-demo-1(config-ca-trustpoint)# fqdn vpn-demo.ashes.cc
vpn-demo-1(config-ca-trustpoint)# subject-name cn=*.ashes.cc, ou=ashes-lab, o=ashes, c=ru
vpn-demo-1(config-ca-trustpoint)# serial-number
vpn-demo-1(config-ca-trustpoint)# crl configure
vpn-demo-1(config-ca-crl)# cry ca enroll SELF
% The fully-qualified domain name in the certificate will be: vpn-demo.ashes.cc
Generate Self-Signed Certificate? [yes/no]: yes
vpn-demo-1(config)#
vpn-demo-1(config)# ssl trust-point SELF
!
vpn-demo-1(config)# sh cry ca certificates
Certificate
Status: Available
Certificate Serial Number: 4d43725e
Certificate Usage: General Purpose
Public Key Type: RSA (4096 bits)
Signature Algorithm: SHA256 with RSA Encryption
Issuer Name:
serialNumber=9A439T02F95
hostname=vpn-demo.ashes.cc
cn=*.ashes.cc
ou=ashes-lab
o=ashes
c=ru
Subject Name:
serialNumber=9A439T02F95
hostname=vpn-demo.ashes.cc
cn=*.ashes.cc
ou=ashes-lab
o=ashes
c=ru
Validity Date:
start date: 00:16:17 MSK Mar 19 2020
end date: 00:16:17 MSK Mar 17 2030
Storage: config
Associated Trustpoints: SELF
CA Certificate
Status: Available
Certificate Serial Number: 0509
Certificate Usage: General Purpose
Public Key Type: RSA (4096 bits)
Signature Algorithm: SHA1 with RSA Encryption
Issuer Name:
cn=QuoVadis Root CA 2
o=QuoVadis Limited
c=BM
Subject Name:
cn=QuoVadis Root CA 2
o=QuoVadis Limited
c=BM
Validity Date:
start date: 21:27:00 MSK Nov 24 2006
end date: 21:23:33 MSK Nov 24 2031
Storage: config
Associated Trustpoints: _SmartCallHome_ServerCA
- , CA:
- TrustPoint:
!
vpn-demo-1(config)# asdm image flash:/asdm-7131.bin
!
vpn-demo-1# conf t
vpn-demo-1(config)# crypto ca trustpoint ashes-ca
vpn-demo-1(config-ca-trustpoint)# enrollment terminal
vpn-demo-1(config-ca-trustpoint)# fqdn vpn-demo.ashes.cc
vpn-demo-1(config-ca-trustpoint)# subject-name cn=*.ashes.cc, ou=ashes-lab, o$
vpn-demo-1(config-ca-trustpoint)# serial-number
vpn-demo-1(config-ca-trustpoint)# crl configure
!
- Trustpoint, ROOT CA:


- ASA :

- CSR VPN-:

- CA CSR:

- , :

- ASA:

- root-ca:

- SSL TrustPoint:
!
vpn-demo-1(config)# ssl trust-point ashes-ca
!
ASDM , :
:
(): , , . , RADIUS , Cisco Identity Services Engine:
!
vpn-demo-1(config)# aaa-server RADIUS protocol radius
vpn-demo-1(config-aaa-server-group)# dynamic-authorization
vpn-demo-1(config-aaa-server-group)# interim-accounting-update
vpn-demo-1(config-aaa-server-group)# aaa-server RADIUS (outside) host 192.168.99.134
vpn-demo-1(config-aaa-server-host)# key cisco
vpn-demo-1(config-aaa-server-host)# exit
vpn-demo-1(config)# tunnel-group DefaultWEBVPNGroup general-attributes
vpn-demo-1(config-tunnel-general)# authentication-server-group RADIUS
!
AD, AD, .
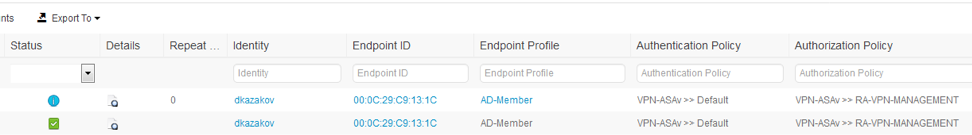
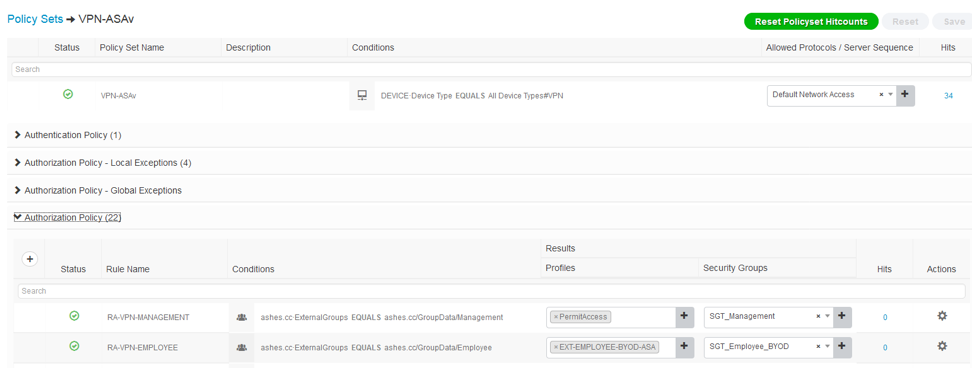
Transparent NAT :
!
vpn-demo-1(config)# object network vpn-users
vpn-demo-1(config-network-object)# subnet 192.168.20.0 255.255.255.0
!
vpn-demo-1(config)# nat (inside,outside) source static any any destination static vpn-users vpn-users no-proxy-arp
(): ASA ( tunnelall ) PAT, OUTSIDE,
!
vpn-demo-1(config-network-object)# nat (outside,outside) source dynamic vpn-users interface
vpn-demo-1(config)# nat (inside,outside) source dynamic any interface
vpn-demo-1(config)# same-security-traffic permit intra-interface
!
ASA , /32 , .
, VPN , FQDN IP.
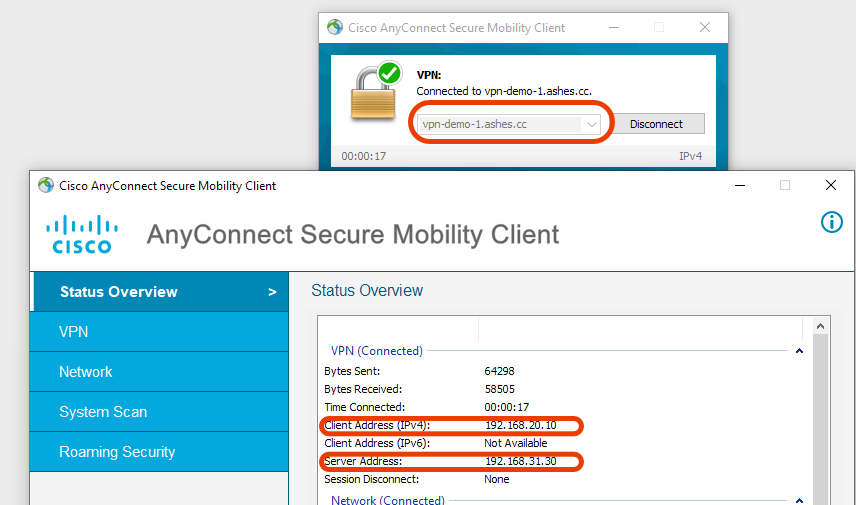
ASA:
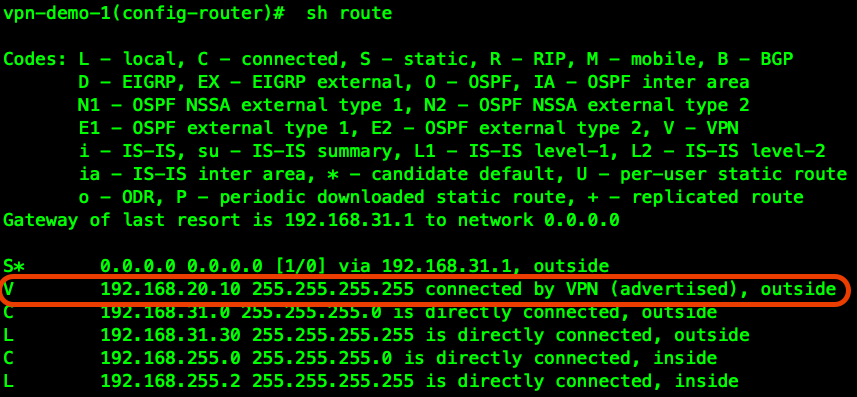
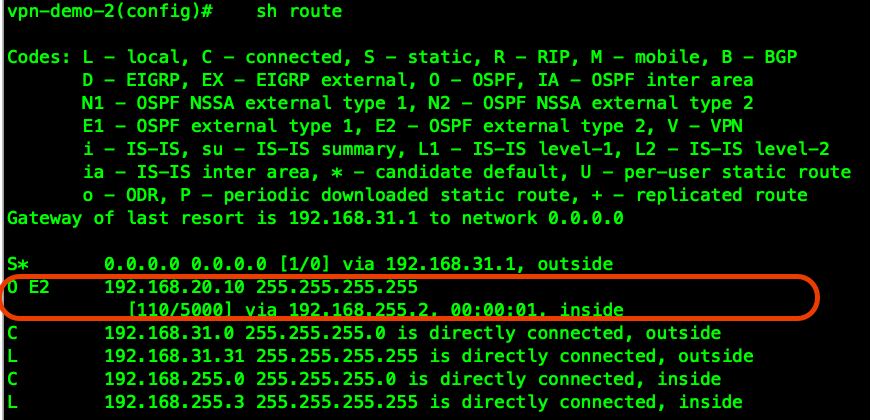
VPN , , OSPF:
!
vpn-demo-1(config)# access-list VPN-REDISTRIBUTE standard permit 192.168.20.0 255.255.255.0
!
vpn-demo-1(config)# route-map RMAP-VPN-REDISTRIBUTE permit 1
vpn-demo-1(config-route-map)# match ip address VPN-REDISTRIBUTE
!
vpn-demo-1(config)# router ospf 1
vpn-demo-1(config-router)# network 192.168.255.0 255.255.255.0 area 0
vpn-demo-1(config-router)# log-adj-changes
vpn-demo-1(config-router)# redistribute static metric 5000 subnets route-map RMAP-VPN-REDISTRIBUTE
ASA-2 , VPN , , , VPN :
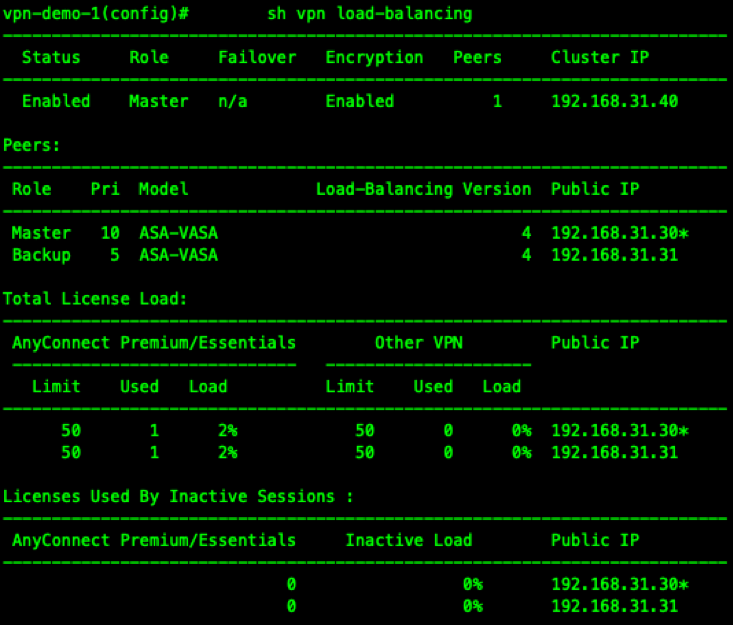
Load-Balancing .
192.168.31.40 Virtual IP ( VIP — VPN ), Master REDIRECT . DNS /FQDN , VIP.
!
vpn-demo-1(config)# crypto ikev1 enable inside
vpn-demo-1(config)# vpn load-balancing
vpn-demo-1(config-load-balancing)# interface lbpublic outside
vpn-demo-1(config-load-balancing)# interface lbprivate inside
vpn-demo-1(config-load-balancing)# priority 10
vpn-demo-1(config-load-balancing)# cluster ip address 192.168.31.40
vpn-demo-1(config-load-balancing)# redirect-fqdn enable
vpn-demo-1(config-load-balancing)# cluster key cisco
vpn-demo-1(config-load-balancing)# cluster encryption
vpn-demo-1(config-load-balancing)# cluster port 9023
vpn-demo-1(config-load-balancing)# participate
vpn-demo-1(config-load-balancing)#
- :
- AnyConnect ASDM.
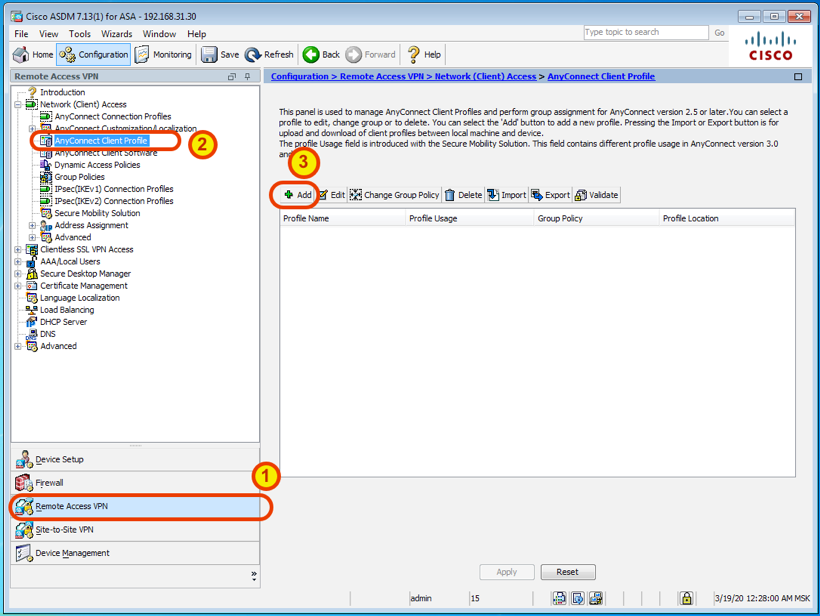
:
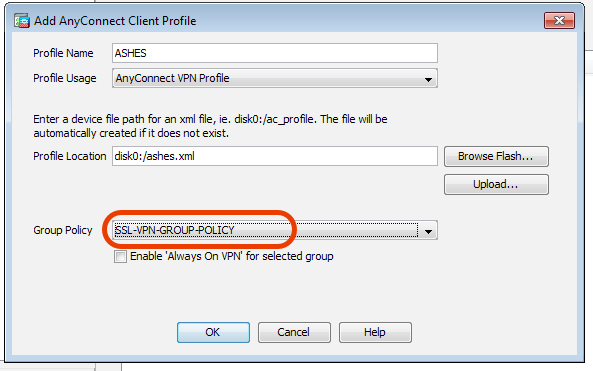
AnyConnect , :
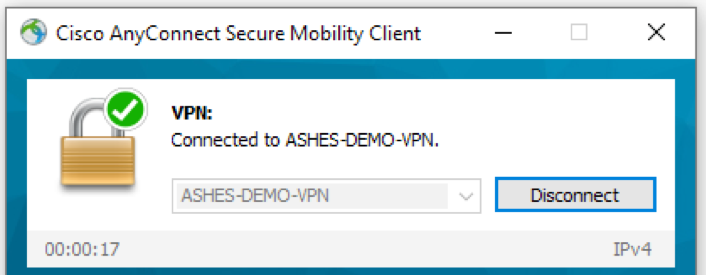
, ASDM ASA, ASA .
: , VPN . , ASAv ASA. AnyConnect Posture ( ), Identity Services Engine.